SAN Consolidation white paper
... Traditional Direct-Attach Storage (DAS) methods persist in many data centers due to low off-the-shelf hardware costs. However, enterprise applications are currently driving the adoption of more centralized networking environments such as Storage Area Networks (SAN) or Network Attached Storage (NAS) ...
... Traditional Direct-Attach Storage (DAS) methods persist in many data centers due to low off-the-shelf hardware costs. However, enterprise applications are currently driving the adoption of more centralized networking environments such as Storage Area Networks (SAN) or Network Attached Storage (NAS) ...
CECS470
... data or information. – Main cause of transmission errors. – Given as the signal to noise ratio S/N and measured in decibels (dB). • Channel Bandwidth: The size of the range of frequencies that can be transmitted through a channel. Measured in Hertz (Hz). Affected by: – Type and physical characterist ...
... data or information. – Main cause of transmission errors. – Given as the signal to noise ratio S/N and measured in decibels (dB). • Channel Bandwidth: The size of the range of frequencies that can be transmitted through a channel. Measured in Hertz (Hz). Affected by: – Type and physical characterist ...
Document
... know T’s existence The LAN does not have its own netid; the hosts in the LAN are assigned unused addresses in the WAN T sends packets from the WAN to the appropriate host in the LAN T accepts packets from the LAN and routes them across WAN to the destination ...
... know T’s existence The LAN does not have its own netid; the hosts in the LAN are assigned unused addresses in the WAN T sends packets from the WAN to the appropriate host in the LAN T accepts packets from the LAN and routes them across WAN to the destination ...
"Anonymous Gossip: Improving Multicast Reliability in Mobile Ad-Hoc Networks"
... a very high probability and with distant nodes occasionally. Our AG protocol is augmented to achieve this optimization. Here, we assume some familiarity with MAODV, because the constraint of brevity prevents us from explaining MAODV in detail, and yet our algorithm builds upon it. We require each no ...
... a very high probability and with distant nodes occasionally. Our AG protocol is augmented to achieve this optimization. Here, we assume some familiarity with MAODV, because the constraint of brevity prevents us from explaining MAODV in detail, and yet our algorithm builds upon it. We require each no ...
BayStack Access Node and Access Node Hub Data Sheet
... In all BayStack AN and ANH configurations, the serial interfaces provide remote office network design flexibility. For mission-critical applications, they facilitate Dial Backup and Bandwidth-on-Demand support. In addition, Dial-onDemand functionality enables a BayStack AN to extend network availabi ...
... In all BayStack AN and ANH configurations, the serial interfaces provide remote office network design flexibility. For mission-critical applications, they facilitate Dial Backup and Bandwidth-on-Demand support. In addition, Dial-onDemand functionality enables a BayStack AN to extend network availabi ...
Lecture04: Network Layer Security
... Most commonly used to obfuscate passwords Vulnerable to brute-force and rainbow table attacks ...
... Most commonly used to obfuscate passwords Vulnerable to brute-force and rainbow table attacks ...
IDES: An Internet Distance Estimation Service for
... Jonathan M. Smith is currently on leave from Penn at DARPA. Approved for Public Release, Distribution Unlimited. 1 Network distance is traditionally known as the round trip time (RTT) between two hosts. However, in this paper, unless specified otherwise, the definition is generalized to any type of ...
... Jonathan M. Smith is currently on leave from Penn at DARPA. Approved for Public Release, Distribution Unlimited. 1 Network distance is traditionally known as the round trip time (RTT) between two hosts. However, in this paper, unless specified otherwise, the definition is generalized to any type of ...
PDF
... Protecting a network begins with securing connectivity. For example, ACLs can be used to restrict access to sensitive portions of the network. To defend against network threats such as Dynamic Host Configuration Protocol (DHCP) spoofing, DHCP snooping can be used to allow only DHCP requests (but not ...
... Protecting a network begins with securing connectivity. For example, ACLs can be used to restrict access to sensitive portions of the network. To defend against network threats such as Dynamic Host Configuration Protocol (DHCP) spoofing, DHCP snooping can be used to allow only DHCP requests (but not ...
CSCI 312 – Data Communication and Computer Networks
... • We have learned that the Internet provides “best effort service.” What is meant by a “best effort” ...
... • We have learned that the Internet provides “best effort service.” What is meant by a “best effort” ...
Powerpoint - Purdue University
... Packet, e.g., scheduling, packet discard Performance concerns become on-line High speed = propagation delay much higher than packet transmission time Number of packets in the “pipe” is high Open loop Router-based Reservation Backpressure Sonia Fahmy ...
... Packet, e.g., scheduling, packet discard Performance concerns become on-line High speed = propagation delay much higher than packet transmission time Number of packets in the “pipe” is high Open loop Router-based Reservation Backpressure Sonia Fahmy ...
network - Victoria College
... • Bits that are not part of the network or subnetwork portions of the address are the range of host address • Use the 2h – 2 formula (where h is the number of host bits) to calculate available host addresses; all 0s in host portion is the subnet identifier address, all 1s in host portion is the subn ...
... • Bits that are not part of the network or subnetwork portions of the address are the range of host address • Use the 2h – 2 formula (where h is the number of host bits) to calculate available host addresses; all 0s in host portion is the subnet identifier address, all 1s in host portion is the subn ...
LoadBalancing - Indico
... A device/driver monitors network traffic flow and makes packet forwarding decisions Example: Microsoft Windows 2003 Server NLB Disadvantages: Not applications aware Simple network topology only Proprietary ...
... A device/driver monitors network traffic flow and makes packet forwarding decisions Example: Microsoft Windows 2003 Server NLB Disadvantages: Not applications aware Simple network topology only Proprietary ...
METHODOLOGY Network Firewall - Data Center V1.0
... System (NFS)) and long-‐lived TCP connections (such as you would see in an iSCSI Storage Area Network (SAN), or a backup application) are common in many data center networks. These types of applications ...
... System (NFS)) and long-‐lived TCP connections (such as you would see in an iSCSI Storage Area Network (SAN), or a backup application) are common in many data center networks. These types of applications ...
Tornado and VxWorks
... Dynamic routing occurs when routers talk to adjacent routers, informing each other of what network each router is connected to Entries in the routing tables change dynamically as routes change over time The Routing Information Protocol (RIP) is provided with VxWorks • This is intended for small to m ...
... Dynamic routing occurs when routers talk to adjacent routers, informing each other of what network each router is connected to Entries in the routing tables change dynamically as routes change over time The Routing Information Protocol (RIP) is provided with VxWorks • This is intended for small to m ...
Chapter 10 Protocols for QoS Support
... — Source/destination IP address or network IP address — Port numbers — IP protocol id — Differentiated services codepoint — IPv6 flow label • Forwarding is simple lookup in predefined table — Map label to next hop • Can define PHB(per hop behaviour) at an LSR for given FEC • Packets between same end ...
... — Source/destination IP address or network IP address — Port numbers — IP protocol id — Differentiated services codepoint — IPv6 flow label • Forwarding is simple lookup in predefined table — Map label to next hop • Can define PHB(per hop behaviour) at an LSR for given FEC • Packets between same end ...
module11-ospf
... • Currently in version 4 • Note: In the context of BGP, a gateway is nothing else but an IP router that connects autonomous systems. • Interdomain routing protocol for routing between autonomous systems • Uses TCP to send routing messages • BGP is neither a link state, nor a distance vector protocol ...
... • Currently in version 4 • Note: In the context of BGP, a gateway is nothing else but an IP router that connects autonomous systems. • Interdomain routing protocol for routing between autonomous systems • Uses TCP to send routing messages • BGP is neither a link state, nor a distance vector protocol ...
Switched LAN Architecture
... the switch console port. Step 2. Set the line speed on the emulation software to 9600 baud. Step 3. Power off the switch. Reconnect the power cord to the switch and within 15 seconds, press the Mode button while the System LED is still flashing green. Continue pressing the Mode button until the Syst ...
... the switch console port. Step 2. Set the line speed on the emulation software to 9600 baud. Step 3. Power off the switch. Reconnect the power cord to the switch and within 15 seconds, press the Mode button while the System LED is still flashing green. Continue pressing the Mode button until the Syst ...
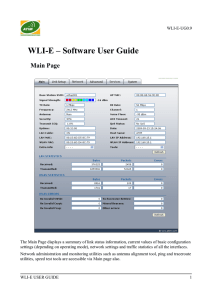
WLI-E – Software User Guide
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
... Transmit CCQ: This is an index of which evaluates the wireless Client Connection Quality. It takes into account transmit errors, latency, and throughput while evaluating the ratio of successfully transmitted packets against the re-transmitted ones and taking into account current rate ratio against t ...
IP connectivity access network
... In 2G mobile networks the visited service control is in use when a user is roaming, an entity (visited mobile service switching centre) in the visited network provides services and controls the traffic for the user In the early days of Release 5 both visited and home service control models wer ...
... In 2G mobile networks the visited service control is in use when a user is roaming, an entity (visited mobile service switching centre) in the visited network provides services and controls the traffic for the user In the early days of Release 5 both visited and home service control models wer ...
press release 01/2015_e - Deutschmann Automation
... The series is based on the established Protocol converter UNIGATE CL. In addition to RS232, RS485 and RS422 standard interfaces, a Fast Ethernet interface is also provided. After entering the network-specific data, such as IP address, the device is immediately ready for use for communication via TCP ...
... The series is based on the established Protocol converter UNIGATE CL. In addition to RS232, RS485 and RS422 standard interfaces, a Fast Ethernet interface is also provided. After entering the network-specific data, such as IP address, the device is immediately ready for use for communication via TCP ...
Recursive InterNetwork Architecture (RINA)

The Recursive InterNetwork Architecture (RINA) is a computer network architecture that unifies distributed computing and telecommunications. RINA's fundamental principle is that computer networking is just Inter-Process Communication or IPC. RINA reconstructs the overall structure of the Internet, forming a model that comprises a single repeating layer, the DIF (Distributed IPC Facility), which is the minimal set of components required to allow distributed IPC between application processes. RINA inherently supports mobility, multi-homing and Quality of Service without the need for extra mechanisms, provides a secure and programmable environment, motivates for a more competitive marketplace, and allows for a seamless adoption.