The Internet is a global communication network which acts as a
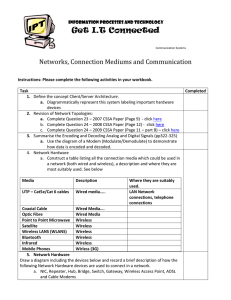
... a. Use the diagram of a Modem (Modulate/Demodulate) to demonstrate how data is encoded and decoded. 4. Network Hardware a. Construct a table listing all the connection media which could be used in a network (both wired and wireless), a description and where they are most suitably used. See below Med ...
... a. Use the diagram of a Modem (Modulate/Demodulate) to demonstrate how data is encoded and decoded. 4. Network Hardware a. Construct a table listing all the connection media which could be used in a network (both wired and wireless), a description and where they are most suitably used. See below Med ...
Broadband Voice IAD
... The SpeedTouch 706WL/780WL also support powerful wireless security mechanisms, such as Wi-Fi Protected AccessTM (WPA), Wired Equivalent Privacy (WEP) encryption, and a physical registration button, which allows users to communicate and access data with efficient link quality and the highest level of ...
... The SpeedTouch 706WL/780WL also support powerful wireless security mechanisms, such as Wi-Fi Protected AccessTM (WPA), Wired Equivalent Privacy (WEP) encryption, and a physical registration button, which allows users to communicate and access data with efficient link quality and the highest level of ...
Quantenna develops first 802.11ac 10G Wave 3 Wi-Fi product
... Quantenna’s 10G Wave 3 platform delivers the maximum capacity within the minimum spectrum so that more streams can be simultaneously transmitted with improved range and reliability. This means that 802.11 Wi-Fi access points or gateways using Quantenna’s 10G Wave 3 product family can support more cl ...
... Quantenna’s 10G Wave 3 platform delivers the maximum capacity within the minimum spectrum so that more streams can be simultaneously transmitted with improved range and reliability. This means that 802.11 Wi-Fi access points or gateways using Quantenna’s 10G Wave 3 product family can support more cl ...
Networking Components
... Firewall is used to provide a first line of defense against data integrity and attacks, and we use the server provides additional data protection and stability. ...
... Firewall is used to provide a first line of defense against data integrity and attacks, and we use the server provides additional data protection and stability. ...
3 - network - Web Design John Cabot University
... 5 Wi-Fi Setup Enter an SSID for the network Activate WEP, WPA, or PSK and create an encryption key Set up the wireless workstations Connect an Internet access device ...
... 5 Wi-Fi Setup Enter an SSID for the network Activate WEP, WPA, or PSK and create an encryption key Set up the wireless workstations Connect an Internet access device ...
BigPond ElitE™ WiRElESS
... 300kbps to 1Mbps in other coverage areas. Actual speeds vary due to factors such as distance from the cell, local conditions, user numbers, hardware software and other factors. Speeds vary due to factors such as distance from the cell, local conditions, number of users, download source, associated c ...
... 300kbps to 1Mbps in other coverage areas. Actual speeds vary due to factors such as distance from the cell, local conditions, user numbers, hardware software and other factors. Speeds vary due to factors such as distance from the cell, local conditions, number of users, download source, associated c ...
tr-5a series - Baltic Networks
... maximum application bandwidth at the lowest total cost of ownership. The EN404 is a wireless mesh router specifically designed for outdoor applications. The dual-radio EN404 serves as a WiFi access point with a dedicated 802.11b/g radio, an intra-network repeater and router with a dedicated 802.11a ...
... maximum application bandwidth at the lowest total cost of ownership. The EN404 is a wireless mesh router specifically designed for outdoor applications. The dual-radio EN404 serves as a WiFi access point with a dedicated 802.11b/g radio, an intra-network repeater and router with a dedicated 802.11a ...
Data Link Layer & Wireless Networking
... 802.11n: multiple antennae 802.11g 2.4-5 GHz range 2.4-5 GHz range up to 200 Mbps up to 54 Mbps ...
... 802.11n: multiple antennae 802.11g 2.4-5 GHz range 2.4-5 GHz range up to 200 Mbps up to 54 Mbps ...
MPLS Based Web Switching
... Integrated WLAN and GPRS cards allow High-speed access indoors (802.11a supports 54Mbps) Wide-area connectivity via emerging wide-area data services (GPRS / 3G) Ongoing research on seamless roaming between LAN/WAN ...
... Integrated WLAN and GPRS cards allow High-speed access indoors (802.11a supports 54Mbps) Wide-area connectivity via emerging wide-area data services (GPRS / 3G) Ongoing research on seamless roaming between LAN/WAN ...
IOSR Journal of Computer Engineering (IOSR-JCE)
... collectively known as Wi-Fi technologies. Additionally, Bluetooth and various other non Wi-Fi technologies also exist, each also designed for specific networking applications. ...
... collectively known as Wi-Fi technologies. Additionally, Bluetooth and various other non Wi-Fi technologies also exist, each also designed for specific networking applications. ...
Slide 1
... Wi-Fi WLANs - inside the office, wireless phones that use the office WLAN VoWLAN – Combination of IP PBX and WLAN to have an in-office portable phone (also called Voice Over Wi-Fi) Wireline networks - Use wires and cables to connect customers’ premises to central offices maintained by telecommunicat ...
... Wi-Fi WLANs - inside the office, wireless phones that use the office WLAN VoWLAN – Combination of IP PBX and WLAN to have an in-office portable phone (also called Voice Over Wi-Fi) Wireline networks - Use wires and cables to connect customers’ premises to central offices maintained by telecommunicat ...
man-in-the-middle - Personal.kent.edu
... • IV reuse(24 bits)=>16.7 million variations • Same shared key in both directions • Encryption is vulnerable to collision-based attacks. ...
... • IV reuse(24 bits)=>16.7 million variations • Same shared key in both directions • Encryption is vulnerable to collision-based attacks. ...
COMP10023 - UWS Mahara
... Compare among generic mobile ad hoc networks, typical wireless sensor networks, and hybrid wireless mesh networks. The following aspects may be taken into account in the comparison: advantages and disadvantages compared with infrastructure networks, typical network topology, network protocols, main ...
... Compare among generic mobile ad hoc networks, typical wireless sensor networks, and hybrid wireless mesh networks. The following aspects may be taken into account in the comparison: advantages and disadvantages compared with infrastructure networks, typical network topology, network protocols, main ...
5 10 Wired Network Basics - Web Design John Cabot University
... 5 Wi-Fi Setup Enter an SSID for the network Activate WEP, WPA, or PSK and create an encryption key Set up the wireless workstations Connect an Internet access device ...
... 5 Wi-Fi Setup Enter an SSID for the network Activate WEP, WPA, or PSK and create an encryption key Set up the wireless workstations Connect an Internet access device ...
Start a wireless network with up to 4X the range and 12X
... from the access point, volume of network traffic, building materials and construction, operating system used, mix of wireless products used, interference and other adverse conditions. Check the product package and contents for specific features supported. Specifications are subject to change without ...
... from the access point, volume of network traffic, building materials and construction, operating system used, mix of wireless products used, interference and other adverse conditions. Check the product package and contents for specific features supported. Specifications are subject to change without ...
354603Specification
... The Dual Band Repeater is Mainly used for providing free WiFi service in big area such as factory, community, street or etc. For example, the normal enhancer can expend distance up to 300 meters away. If there are more repeaters or more bigger power repeater, the range will extended further; the Rep ...
... The Dual Band Repeater is Mainly used for providing free WiFi service in big area such as factory, community, street or etc. For example, the normal enhancer can expend distance up to 300 meters away. If there are more repeaters or more bigger power repeater, the range will extended further; the Rep ...
CHAPTER 6
... 1. A computer’s wireless network adaptor translates data into a radio signal and transmits it. 2. The access point has an antenna that receives the signal and decodes it. It sends the information to the Internet using a cabled connection. 3. As a rule of thumb, the range is about 150 ft (indoors) an ...
... 1. A computer’s wireless network adaptor translates data into a radio signal and transmits it. 2. The access point has an antenna that receives the signal and decodes it. It sends the information to the Internet using a cabled connection. 3. As a rule of thumb, the range is about 150 ft (indoors) an ...
Home Network Basics
... port and only sends it out the port that is connected to the device that is suppose to get the message. It can send information between two different networks, such as, your home network and the Internet. • Most routers have ports to plug in Ethernet cables and wireless for Wi-Fi. ...
... port and only sends it out the port that is connected to the device that is suppose to get the message. It can send information between two different networks, such as, your home network and the Internet. • Most routers have ports to plug in Ethernet cables and wireless for Wi-Fi. ...
Network Forensics Tracking Hackers Through Cyberspace.
... 1. Gather station descriptors, such as MAC addresses, which can help provide a physical description so that you know what to look for 2. For clients, identify the WAP that the station is associated with (by SSID) 3. Leverage commercial enterprise wireless mapping software ...
... 1. Gather station descriptors, such as MAC addresses, which can help provide a physical description so that you know what to look for 2. For clients, identify the WAP that the station is associated with (by SSID) 3. Leverage commercial enterprise wireless mapping software ...
Dual Radio Outdoor Wireless Mesh Router
... The EN500: the most cost-effective solution for delivering broadband wireless applications in outdoor environments. The EN500 combines 802.11a mesh networking with 802.11b/g access points for maximum range and interoperability with WiFi enabled devices. Enabled by Tranzeo’s WirelessFabric™ network s ...
... The EN500: the most cost-effective solution for delivering broadband wireless applications in outdoor environments. The EN500 combines 802.11a mesh networking with 802.11b/g access points for maximum range and interoperability with WiFi enabled devices. Enabled by Tranzeo’s WirelessFabric™ network s ...
Wi-Fi
Wi-Fi (or WiFi) is a local area wireless computer networking technology that allows electronic devices to network, mainly using the 2.4 gigahertz (12 cm) UHF and 5 gigahertz (6 cm) SHF ISM radio bands.The Wi-Fi Alliance defines Wi-Fi as any ""wireless local area network"" (WLAN) product based on the Institute of Electrical and Electronics Engineers' (IEEE) 802.11 standards. However, the term ""Wi-Fi"" is used in general English as a synonym for ""WLAN"" since most modern WLANs are based on these standards. ""Wi-Fi"" is a trademark of the Wi-Fi Alliance. The ""Wi-Fi Certified"" trademark can only be used by Wi-Fi products that successfully complete Wi-Fi Alliance interoperability certification testing.Many devices can use Wi-Fi, e.g. personal computers, video-game consoles, smartphones, digital cameras, tablet computers and digital audio players. These can connect to a network resource such as the Internet via a wireless network access point. Such an access point (or hotspot) has a range of about 20 meters (66 feet) indoors and a greater range outdoors. Hotspot coverage can be as small as a single room with walls that block radio waves, or as large as many square kilometres achieved by using multiple overlapping access points. Wi-Fi can be less secure than wired connections, such as Ethernet, precisely because an intruder does not need a physical connection. Web pages that use TLS are secure, but unencrypted internet access can easily be detected by intruders. Because of this, Wi-Fi has adopted various encryption technologies. The early encryption WEP proved easy to break. Higher quality protocols (WPA, WPA2) were added later. An optional feature added in 2007, called Wi-Fi Protected Setup (WPS), had a serious flaw that allowed an attacker to recover the router's password. The Wi-Fi Alliance has since updated its test plan and certification program to ensure all newly certified devices resist attacks.