Hidden cost of Chromebook deployments: Up to 40 times longer to
... the system as a notebook during our tests. The Chromebook we used in our testing was the Acer C720 running Chrome OS™ (33.0.1750.152) and featuring a 1.4GHz Intel Celeron® Processor 2955U and 2 GB of RAM. Because Chromebook users primarily store files on the cloud, only 16 GB of local solid-state st ...
... the system as a notebook during our tests. The Chromebook we used in our testing was the Acer C720 running Chrome OS™ (33.0.1750.152) and featuring a 1.4GHz Intel Celeron® Processor 2955U and 2 GB of RAM. Because Chromebook users primarily store files on the cloud, only 16 GB of local solid-state st ...
Deploying IPv6, now
... Existing applications and networking protocols do not work with changing IP addresses Applications do not “reconnect” when a new IP address appears • TCP drops session when IP address changes • IPSEC hashes across IP addresses, changing address breaks the Security Association ...
... Existing applications and networking protocols do not work with changing IP addresses Applications do not “reconnect” when a new IP address appears • TCP drops session when IP address changes • IPSEC hashes across IP addresses, changing address breaks the Security Association ...
Network Service and Applications
... Excessive congestion: packet delay and loss - protocols needed for reliable data transfer, congestion control Q: How to provide circuit-like behavior? - bandwidth guarantees needed for audio/video apps - still an unsolved problem - Overprovisioning often used Mao W07 ...
... Excessive congestion: packet delay and loss - protocols needed for reliable data transfer, congestion control Q: How to provide circuit-like behavior? - bandwidth guarantees needed for audio/video apps - still an unsolved problem - Overprovisioning often used Mao W07 ...
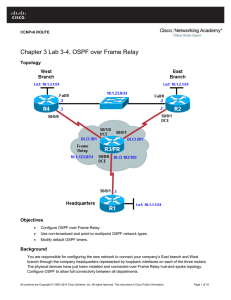
Chapter 3 Lab 3-4, OSPF over Frame Relay
... Use non-broadcast and point-to-multipoint OSPF network types. ...
... Use non-broadcast and point-to-multipoint OSPF network types. ...
Inferring Subnets in Router-level Topology Collection Studies
... Based on this observation, we use an iterative approach to identify candidate subnets. We first form all candidate /x subnets from the data set by combining the IP addresses whose first x bits match. Next, we recursively form smaller subnets (e.g., /x, /(x+1), . . ., /31 subnets). At this point, we ...
... Based on this observation, we use an iterative approach to identify candidate subnets. We first form all candidate /x subnets from the data set by combining the IP addresses whose first x bits match. Next, we recursively form smaller subnets (e.g., /x, /(x+1), . . ., /31 subnets). At this point, we ...
Routing protocols for wireless networks
... 2. Sender S broadcasts a RREQ to all its neighbors, each node receiving RREQ forwards RREQ to its neighbors. *Sequence numbers help to avoid the possibility of forwarding the same packet more than once. 3. An intermediate node (not the destination) may also send a RouteReply (RREP) packet provided t ...
... 2. Sender S broadcasts a RREQ to all its neighbors, each node receiving RREQ forwards RREQ to its neighbors. *Sequence numbers help to avoid the possibility of forwarding the same packet more than once. 3. An intermediate node (not the destination) may also send a RouteReply (RREP) packet provided t ...
Routers and Routing Basics CCNA 2
... Routers Route Packets Routers are network devices that deliver packets (more precisely – frames) from the source to destination. Routers have two major mechanisms that allow them not only to deliver packets with a required reliability and quality, but also to find the best available path for de ...
... Routers Route Packets Routers are network devices that deliver packets (more precisely – frames) from the source to destination. Routers have two major mechanisms that allow them not only to deliver packets with a required reliability and quality, but also to find the best available path for de ...
User Manual PowerLine AV500 Wireless N Mini Extender Starter Kit
... your home - the electrical wiring. Share Internet connections and experience smooth file transfers, streaming multimedia, online gaming and more. The Powerline AV500 Wireless N Mini Extender features easy plug-and-play installation and can be connected to any Ethernet-enabled device. The PowerLine P ...
... your home - the electrical wiring. Share Internet connections and experience smooth file transfers, streaming multimedia, online gaming and more. The Powerline AV500 Wireless N Mini Extender features easy plug-and-play installation and can be connected to any Ethernet-enabled device. The PowerLine P ...
Tips for Using This Template
... For more information on Qualcomm, visit us at: www.qualcomm.com or www.qualcomm.com/blog ...
... For more information on Qualcomm, visit us at: www.qualcomm.com or www.qualcomm.com/blog ...
Chapter14 (Unicast Routing Protocols)
... RIP and OSPF are popular intradomain routing protocols used to update routing tables in an AS. RIP is based on distance vector routing, in which each router shares, at regular intervals, its knowledge about the entire AS with its neighbors. A RIP routing table entry consists of a destination n ...
... RIP and OSPF are popular intradomain routing protocols used to update routing tables in an AS. RIP is based on distance vector routing, in which each router shares, at regular intervals, its knowledge about the entire AS with its neighbors. A RIP routing table entry consists of a destination n ...
T O P
... Board of ‘Support’ menu in WIZnet website (www.wiznet.co.kr). WIZnet Engineer will give an answer as soon as possible. ...
... Board of ‘Support’ menu in WIZnet website (www.wiznet.co.kr). WIZnet Engineer will give an answer as soon as possible. ...
Migration of Gsm to Gprs
... performs security functions and access control. Detects and registers new GPRS mobile stations located in its service area Participates into routing, as well as mobility management functions. Nishith Ranjan Sahoo ...
... performs security functions and access control. Detects and registers new GPRS mobile stations located in its service area Participates into routing, as well as mobility management functions. Nishith Ranjan Sahoo ...
User Manual Powerline AV 500 Wireless N Mini Extender DHP-W310AV
... the most pervasive medium in your home - the electrical wiring. Share Internet connections and experience smooth file transfers, streaming multimedia, online gaming and more. The Powerline AV Wireless N Mini Extender features easy plug-and-play installation and can be connected to any Ethernet-enabl ...
... the most pervasive medium in your home - the electrical wiring. Share Internet connections and experience smooth file transfers, streaming multimedia, online gaming and more. The Powerline AV Wireless N Mini Extender features easy plug-and-play installation and can be connected to any Ethernet-enabl ...
Manual D-Link AirPlus Xtreme G DWL-G810
... and public areas such as airports, coffee shops and universities. Innovative ways to utilize WLAN technology are helping people to work and communicate more efficiently. Increased mobility and the absence of cabling and other fixed infrastructure have proven to be beneficial for many users. Wireless ...
... and public areas such as airports, coffee shops and universities. Innovative ways to utilize WLAN technology are helping people to work and communicate more efficiently. Increased mobility and the absence of cabling and other fixed infrastructure have proven to be beneficial for many users. Wireless ...
COEN 252 Computer Forensics - Santa Clara University's
... MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack. ...
... MAC, a Linux laptop that has been compromised and is used for a Denial of Service attack. ...
DCV General Info
... in conjunction with one or more DCV Data Managers. Additionally the functionality of each DCV on the network can be further restricted to allow specific actions such as: capture workstation only; view workstation only; and data correction workstation. DCV Data Manager is the main data server compone ...
... in conjunction with one or more DCV Data Managers. Additionally the functionality of each DCV on the network can be further restricted to allow specific actions such as: capture workstation only; view workstation only; and data correction workstation. DCV Data Manager is the main data server compone ...
Network Layer Pt 1
... • Routers – understand packets and calculating best path for packets • Routing = process perform by routers : receive packets, analyzing dest add info, select a path and forwarding packets to the next router • Each route to next device = hop ...
... • Routers – understand packets and calculating best path for packets • Routing = process perform by routers : receive packets, analyzing dest add info, select a path and forwarding packets to the next router • Each route to next device = hop ...
ppt
... For the following questions, assume that these are always coupled with a FIFO scheduling policy. The full queue problem occurs if routers’ queues are often full. The lockout problem refers to a situation where a small number of flows monopolize the available queue space on a router. •Drop-tail solv ...
... For the following questions, assume that these are always coupled with a FIFO scheduling policy. The full queue problem occurs if routers’ queues are often full. The lockout problem refers to a situation where a small number of flows monopolize the available queue space on a router. •Drop-tail solv ...
pptx
... Hep-Th database: papers and authors in theoretical high-energy physics, from the arXiv archive, linked if at least two papers together. Enron dataset: from a corpus of email sent to and from managers at Enron Corporation -- Two individuals connected if they corresponded at least 5 times. Net-trace d ...
... Hep-Th database: papers and authors in theoretical high-energy physics, from the arXiv archive, linked if at least two papers together. Enron dataset: from a corpus of email sent to and from managers at Enron Corporation -- Two individuals connected if they corresponded at least 5 times. Net-trace d ...
Chapter 10 Protocols for QoS Support
... different domain. Note that if an LSR has a neighboring host that is not running MPLS, then that LSR is an MPLS edge node. ...
... different domain. Note that if an LSR has a neighboring host that is not running MPLS, then that LSR is an MPLS edge node. ...
Juniper Networks VPN Decision Guide
... In addition, corporate business partners and customers increasingly need real-time access to corporate resources and applications. In the early 1990s, there were only limited options to extend the availability of the enterprise’s network beyond the boundaries of the corporate central site, which com ...
... In addition, corporate business partners and customers increasingly need real-time access to corporate resources and applications. In the early 1990s, there were only limited options to extend the availability of the enterprise’s network beyond the boundaries of the corporate central site, which com ...
Layer 2 Fundamentals
... slaves wether they have to transmit data or not) • is concerned with physical naming (addressing); defines MAC addressing; • The NIC uses the MAC address to assess whether the message is destined for that host and therefore should be passed onto the upper layers of the OSI model. • The NIC makes thi ...
... slaves wether they have to transmit data or not) • is concerned with physical naming (addressing); defines MAC addressing; • The NIC uses the MAC address to assess whether the message is destined for that host and therefore should be passed onto the upper layers of the OSI model. • The NIC makes thi ...