Solving the Wireless Mesh Multi-Hop Dilemma
... easy for their network backhaul bandwidth to become affected by radio interference from neighboring devices that operate in the same band. Radio interference can also cause transmission errors. These errors can compound. Furthermore, it is important to note that interference may vary in different pa ...
... easy for their network backhaul bandwidth to become affected by radio interference from neighboring devices that operate in the same band. Radio interference can also cause transmission errors. These errors can compound. Furthermore, it is important to note that interference may vary in different pa ...
Week_Eleven_ppt
... Factors affecting the convergence time include the following: • Routing protocol used • Distance of the router, or the number of hops from the point of change • Number of routers in the network that use dynamic routing protocols • Bandwidth and traffic load on communications links • Load on the rout ...
... Factors affecting the convergence time include the following: • Routing protocol used • Distance of the router, or the number of hops from the point of change • Number of routers in the network that use dynamic routing protocols • Bandwidth and traffic load on communications links • Load on the rout ...
There has been much talk about the holy grail of optical networking
... Many in the scientific research community are of the opinion that today’s production, experimental and research networks do not have the capabilities to meet the needs of some of the existing e-science and grid applications. Many of these applications have requirements of one or more of these constr ...
... Many in the scientific research community are of the opinion that today’s production, experimental and research networks do not have the capabilities to meet the needs of some of the existing e-science and grid applications. Many of these applications have requirements of one or more of these constr ...
Pass4sure 640
... Thousands of IT Professionals before you have already passed their 640-802 certification exams using the Cisco 640-802 Practice Exam from ipass4sure.com. Once you start using our 640-802 exam questions you simply can't stop! You are guaranteed to pass your Cisco 640-802 test with ease and in your fi ...
... Thousands of IT Professionals before you have already passed their 640-802 certification exams using the Cisco 640-802 Practice Exam from ipass4sure.com. Once you start using our 640-802 exam questions you simply can't stop! You are guaranteed to pass your Cisco 640-802 test with ease and in your fi ...
Mobile IP and Wireless Application Protocol
... Forth phase – completes the setting up of a secure connection ...
... Forth phase – completes the setting up of a secure connection ...
3rd Edition: Chapter 4
... . . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair incoming datagrams: replace (NAT IP address, new port #) in dest fields of every ...
... . . . remote clients/servers will respond using (NAT IP address, new port #) as destination addr remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair incoming datagrams: replace (NAT IP address, new port #) in dest fields of every ...
EdgeRouter Lite
... All specifications in this document are subject to change without notice. Ubiquiti products are sold with a limited warranty described at: www.ubnt.com/support/warranty ©2012-2014 Ubiquiti Networks, Inc. All rights reserved. Ubiquiti, Ubiquiti Networks, the Ubiquiti U logo, the Ubiquiti beam logo, E ...
... All specifications in this document are subject to change without notice. Ubiquiti products are sold with a limited warranty described at: www.ubnt.com/support/warranty ©2012-2014 Ubiquiti Networks, Inc. All rights reserved. Ubiquiti, Ubiquiti Networks, the Ubiquiti U logo, the Ubiquiti beam logo, E ...
Follow this link to lec1d handout
... Among the key issues dealt with are: Routing packets from source to destination through the network (or multiple networks) using static or dynamic routing algorithms Controlling congestion in the network Accounting functions (for billing) Translating between protocols across heterogeneous ne ...
... Among the key issues dealt with are: Routing packets from source to destination through the network (or multiple networks) using static or dynamic routing algorithms Controlling congestion in the network Accounting functions (for billing) Translating between protocols across heterogeneous ne ...
chapter5
... The 2m node IDs arranged in ascending order in a circle (m=160 in current implementation) Node ID name space = key name space (name both NS e.g. NS = {0, …, 2m –1}) Since n << 2m the node ID space includes (many) IDs without actual nodes assigned to them. Define the total function successor: NS NS ...
... The 2m node IDs arranged in ascending order in a circle (m=160 in current implementation) Node ID name space = key name space (name both NS e.g. NS = {0, …, 2m –1}) Since n << 2m the node ID space includes (many) IDs without actual nodes assigned to them. Define the total function successor: NS NS ...
Turn over
... b) Companies that have offices in several countries around the globe need to create a private corporate network that is able to connect these sites together and transport traffic of different types between them. An increasingly popular way of providing such a network is to use Multiprotocol Label Sw ...
... b) Companies that have offices in several countries around the globe need to create a private corporate network that is able to connect these sites together and transport traffic of different types between them. An increasingly popular way of providing such a network is to use Multiprotocol Label Sw ...
Clean Slate Design for the Internet
... Feature lists as long as your arm Routers with >10M lines of source code, datapath with 100M gates & 1Gbyte RAM. ...
... Feature lists as long as your arm Routers with >10M lines of source code, datapath with 100M gates & 1Gbyte RAM. ...
HC1318
... largely asymmetric with the long latency of data delivery. In disconnection, most cases it is impossible to have an end-to-end path. Hence, disconnection is more usual than connection. Normally, the disconnection may be mainly caused by network partition as well as unexpected fault. In DTNs, the que ...
... largely asymmetric with the long latency of data delivery. In disconnection, most cases it is impossible to have an end-to-end path. Hence, disconnection is more usual than connection. Normally, the disconnection may be mainly caused by network partition as well as unexpected fault. In DTNs, the que ...
Chapter 4 Lecture Presentation
... Fast call setup delay: if 1-sec call setup delay, holding time should be at least n times this number, e.g., n=10. Call handling throughput should be high e.g., 160Gbps switching capacity; per-call rate: 300Mbps; number of concurrent calls = 533 if call holding time = 10 sec, switch controller s ...
... Fast call setup delay: if 1-sec call setup delay, holding time should be at least n times this number, e.g., n=10. Call handling throughput should be high e.g., 160Gbps switching capacity; per-call rate: 300Mbps; number of concurrent calls = 533 if call holding time = 10 sec, switch controller s ...
An intro to Software Defined Networking
... • Framework for concurrent and consistent policy composition in distributed SDN • Transactional interface to manipulate the network as though there is no concurrency – Policies compose or conflict (and abort) ...
... • Framework for concurrent and consistent policy composition in distributed SDN • Transactional interface to manipulate the network as though there is no concurrency – Policies compose or conflict (and abort) ...
- Cisco EMEAR Network
... IP addresses needed to identify all user devices in a global network. The protocol makes it possible to supply every end user with a range of unique static addresses as well as assign a whole subnet large enough to support various devices: PCs, sensors, security appliances, video surveillance tools, ...
... IP addresses needed to identify all user devices in a global network. The protocol makes it possible to supply every end user with a range of unique static addresses as well as assign a whole subnet large enough to support various devices: PCs, sensors, security appliances, video surveillance tools, ...
7.4 Node-Level Simulators
... There are two types of components in nesC, depending on how they are implemented: modules and configurations. Modules are implemented by application code (written in a C-like syntax). Configurations are implemented by connecting interfaces of existing components. The implementation part of a module ...
... There are two types of components in nesC, depending on how they are implemented: modules and configurations. Modules are implemented by application code (written in a C-like syntax). Configurations are implemented by connecting interfaces of existing components. The implementation part of a module ...
The Petabit Routing Company - Home Page
... Hyperchip is unique in building carrier class core routers with extreme performance and scalability • Founded in 1997 • $150M investment funding to date ...
... Hyperchip is unique in building carrier class core routers with extreme performance and scalability • Founded in 1997 • $150M investment funding to date ...
Intelligence Finding MAPs for belief networks is NP-hard
... size of the representation. If our model has n random variables, then representing the complete distribution might require space exponential in n. By using the structuring (and independence assumptions) available in the graphical representation, and a very sparse graph, space linear in n is frequent ...
... size of the representation. If our model has n random variables, then representing the complete distribution might require space exponential in n. By using the structuring (and independence assumptions) available in the graphical representation, and a very sparse graph, space linear in n is frequent ...
GSM/UMTS Network
... Flexible architecture that is possible to use for any connectivity (ATM, IP, STM) Keep the N-ISDN/GSM service paradigm. Use MAP, ISUP, etc. All devices needed for user plane manipulation are moved to the Media Gateway (echo cancellers, codecs, etc.) Possible to place infrequently used equipment in c ...
... Flexible architecture that is possible to use for any connectivity (ATM, IP, STM) Keep the N-ISDN/GSM service paradigm. Use MAP, ISUP, etc. All devices needed for user plane manipulation are moved to the Media Gateway (echo cancellers, codecs, etc.) Possible to place infrequently used equipment in c ...
IM2_2_Frederiks
... ABGPS data used in Aerotriangulation adjustment to reduce the amount of ground control ...
... ABGPS data used in Aerotriangulation adjustment to reduce the amount of ground control ...
No - Trinity College Dublin
... An activation rule for combining the inputs impinging on a unit with the current state of that unit to produce a new level of activation for the unit A learning rule whereby patterns of connectivity are modified by experience An environment within which the system must operate ...
... An activation rule for combining the inputs impinging on a unit with the current state of that unit to produce a new level of activation for the unit A learning rule whereby patterns of connectivity are modified by experience An environment within which the system must operate ...
To View PowerPoint Presentation
... What are the State Standards = LISD Standards TEKS and Technology Plan Instructional Training Program Understanding the Network ...
... What are the State Standards = LISD Standards TEKS and Technology Plan Instructional Training Program Understanding the Network ...
Document
... • The Infected node (K, or I) reports the discovered suspicious neighbors (J, or F) to the M‐server, and forwards the checksum to the reported suspicious neighbors (J, or F). ...
... • The Infected node (K, or I) reports the discovered suspicious neighbors (J, or F) to the M‐server, and forwards the checksum to the reported suspicious neighbors (J, or F). ...
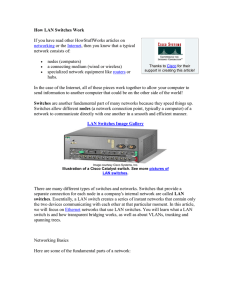
How LAN Switches Work
... pass. A router works like this. Without the specific address of another device, it will not let the data packet through. This is a good thing for keeping networks separate from each other, but not so good when you want to talk between different parts of the same network. This is where switches come ...
... pass. A router works like this. Without the specific address of another device, it will not let the data packet through. This is a good thing for keeping networks separate from each other, but not so good when you want to talk between different parts of the same network. This is where switches come ...