information
... A node should add the routing information contained in each packet’s header it overhears A hacker can easily broadcast a message with a spoofed IP address such as the other nodes add this new route to reach a special node S It’s the malicious node which will receive the packets intended to S. ...
... A node should add the routing information contained in each packet’s header it overhears A hacker can easily broadcast a message with a spoofed IP address such as the other nodes add this new route to reach a special node S It’s the malicious node which will receive the packets intended to S. ...
IP CIP compared to other NonStop TCP/IP products – Technical
... Both TCP/IPv6 and CIP are system-wide subsystems and allow many more interfaces, so there is no need to split single network connectivity because of throughput concerns. If you are connected to multiple independent networks or need to confine applications, you can create partitions that act like sep ...
... Both TCP/IPv6 and CIP are system-wide subsystems and allow many more interfaces, so there is no need to split single network connectivity because of throughput concerns. If you are connected to multiple independent networks or need to confine applications, you can create partitions that act like sep ...
Using Your Wi-Fi® card by palmOne (English)
... Insert the card into the expansion slot with the palmOne logo label facing the front of the handheld. ...
... Insert the card into the expansion slot with the palmOne logo label facing the front of the handheld. ...
Vodafone PowerPoint template
... original design was intended to provide a direct equivalent to a WiFi access point, but for mobile cellular (UMTS, CDMA-2000 or WiMAX). The unit contained all the core network elements and did not require a cellular core network, requiring only a data connection to the Internet or WiFi core network. ...
... original design was intended to provide a direct equivalent to a WiFi access point, but for mobile cellular (UMTS, CDMA-2000 or WiMAX). The unit contained all the core network elements and did not require a cellular core network, requiring only a data connection to the Internet or WiFi core network. ...
Investigating Network Performance – A Case Study
... • High sensitivity requires large bandwidths as well as large collecting area e.g Lovell, GBT, Effelsberg, Camb. 32-m • Aperture synthesis needs signals from individual antennas to be correlated together at a central site • Need for interconnection data rates of many Gbit/sec ...
... • High sensitivity requires large bandwidths as well as large collecting area e.g Lovell, GBT, Effelsberg, Camb. 32-m • Aperture synthesis needs signals from individual antennas to be correlated together at a central site • Need for interconnection data rates of many Gbit/sec ...
third edition
... and to see the big picture of networking. It is our experience that both students and professionals learning about networks for the first time often have the impression that network protocols are some sort of edict handed down from on high, and that their job is to learn as many TLAs (three-letter a ...
... and to see the big picture of networking. It is our experience that both students and professionals learning about networks for the first time often have the impression that network protocols are some sort of edict handed down from on high, and that their job is to learn as many TLAs (three-letter a ...
Understanding Simple Network Management Protocol
... the “SNMP Community Strings and Users” section on page 15-5. In Cisco Unified Serviceability, you configure SNMP v3 support in the V3 Configuration window. ...
... the “SNMP Community Strings and Users” section on page 15-5. In Cisco Unified Serviceability, you configure SNMP v3 support in the V3 Configuration window. ...
Lecture 3 TCP/IP model
... A: It depends on the application. TCP provides a connection-oriented, reliable, byte stream service (lots of overhead). UDP offers minimal datagram delivery service (as little overhead as possible). ...
... A: It depends on the application. TCP provides a connection-oriented, reliable, byte stream service (lots of overhead). UDP offers minimal datagram delivery service (as little overhead as possible). ...
NFV - Oasis
... necessarily be infringed by implementations of this OASIS Committee Specification or OASIS Standard, to notify OASIS TC Administrator and provide an indication of its willingness to grant patent licenses to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee ...
... necessarily be infringed by implementations of this OASIS Committee Specification or OASIS Standard, to notify OASIS TC Administrator and provide an indication of its willingness to grant patent licenses to such patent claims in a manner consistent with the IPR Mode of the OASIS Technical Committee ...
paper
... security concerns, rendering King narrowly applicable. Conversely, we show that Ting can be used to infer with direct measurements the end-to-end latencies among any pair of active Tor nodes. In other words, as Tor’s user base increases, so too does Ting’s applicability. We show that Tor’s current u ...
... security concerns, rendering King narrowly applicable. Conversely, we show that Ting can be used to infer with direct measurements the end-to-end latencies among any pair of active Tor nodes. In other words, as Tor’s user base increases, so too does Ting’s applicability. We show that Tor’s current u ...
Framework
... Inspect TCP, UDP, IP headers to make filtering decisions Do stateful filtering by checking the firewall’s state table for relation of packets to packets already filtered If packet does not match existing connect, ruleset (static filt.) is used If packet matches existing connection, it is allowed to ...
... Inspect TCP, UDP, IP headers to make filtering decisions Do stateful filtering by checking the firewall’s state table for relation of packets to packets already filtered If packet does not match existing connect, ruleset (static filt.) is used If packet matches existing connection, it is allowed to ...
Using Switches with a PS Series Group
... separate network switches, but with fewer physical switches and less management overhead. Because VLANs use logical rather than physical connections, they are flexible to operate. Note: PS Series storage arrays do not support VLAN tagging. Typically, VLANs are separate subnets in TCP/IP networks, so ...
... separate network switches, but with fewer physical switches and less management overhead. Because VLANs use logical rather than physical connections, they are flexible to operate. Note: PS Series storage arrays do not support VLAN tagging. Typically, VLANs are separate subnets in TCP/IP networks, so ...
PDF
... http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html CCDE, CCENT, Cisco Eos, Cisco Lumin, Cisco Nexus, Cisco StadiumVision, Cisco TelePresence, the Cisco logo, DCE, and Welcome to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn and Cisco Store are service ...
... http://www.cisco.com/en/US/docs/general/whatsnew/whatsnew.html CCDE, CCENT, Cisco Eos, Cisco Lumin, Cisco Nexus, Cisco StadiumVision, Cisco TelePresence, the Cisco logo, DCE, and Welcome to the Human Network are trademarks; Changing the Way We Work, Live, Play, and Learn and Cisco Store are service ...
New Scheduling Algorithm for Providing Proportional Jitter in Differentiated Service Network
... quality of service here is explained as end-to-end delay, because whether we implement a model of PDD or PJD in terms of delay or delay jitter in a network, which we hope is always receiving better end-to-end quality of service, and in this case, a better end-to-end delay, which is the sum of networ ...
... quality of service here is explained as end-to-end delay, because whether we implement a model of PDD or PJD in terms of delay or delay jitter in a network, which we hope is always receiving better end-to-end quality of service, and in this case, a better end-to-end delay, which is the sum of networ ...
High Availability WLANs Based on Software-Defined
... Recently, the software defined networking (SDN) has attracted a lot of interest. The main characteristics of SDN is to decouple the control and data planes of a network and provide the freedom of programmability to development more efficient network applications [1]. Furthermore, the SDN also result ...
... Recently, the software defined networking (SDN) has attracted a lot of interest. The main characteristics of SDN is to decouple the control and data planes of a network and provide the freedom of programmability to development more efficient network applications [1]. Furthermore, the SDN also result ...
PDF
... address. The wizard also adds configuration options for automated attendant, business schedules, localization, inbound and outbound dial plans, users and phones, and call blast and hunt groups. The Video Monitoring wizard provides trouble-free setup for streaming video from a Cisco WVC2300 or PVC230 ...
... address. The wizard also adds configuration options for automated attendant, business schedules, localization, inbound and outbound dial plans, users and phones, and call blast and hunt groups. The Video Monitoring wizard provides trouble-free setup for streaming video from a Cisco WVC2300 or PVC230 ...
Broadband Router with built-in ADSL Modem
... User-definable application sensing tunnel supports applications requiring multiple connections. ...
... User-definable application sensing tunnel supports applications requiring multiple connections. ...
LAB1-Overview
... Use the ping command to verify that the local host can communicate across the internetwork to a given remote host. ...
... Use the ping command to verify that the local host can communicate across the internetwork to a given remote host. ...
Chapter 6 - Network Layer
... Itself - This is a special IP address of 127.0.0.1 which is referred to as the loopback interface. Local host - This is a host on the same network as the sending host. The hosts share the same network address. Remote host - This is a host on a remote network. The hosts do not share the same network ...
... Itself - This is a special IP address of 127.0.0.1 which is referred to as the loopback interface. Local host - This is a host on the same network as the sending host. The hosts share the same network address. Remote host - This is a host on a remote network. The hosts do not share the same network ...
Lecture Note 6 - Computing Science
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet Satellite 802.11 wireless LAN Or lecture room ...
... Two types of “links”: point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet Satellite 802.11 wireless LAN Or lecture room ...
Review, Performance Metrics, Cont…
... —Well suited for non-real-time, bursty traffic —2 types of packet switching, connectionless and connection oriented: ...
... —Well suited for non-real-time, bursty traffic —2 types of packet switching, connectionless and connection oriented: ...
22101-660
... Technical Specification Group Services and System Aspects Service aspects; Service principles (Release 6) ...
... Technical Specification Group Services and System Aspects Service aspects; Service principles (Release 6) ...
User Manual
... be first disconnected from the 245U-E module during these adjustments. Equipment should carry clear markings to indicate remote or automatic operation. For example, “This equipment is remotely controlled and may start without warning. Isolate at the switchboard before attempting adjustments.” 5. Th ...
... be first disconnected from the 245U-E module during these adjustments. Equipment should carry clear markings to indicate remote or automatic operation. For example, “This equipment is remotely controlled and may start without warning. Isolate at the switchboard before attempting adjustments.” 5. Th ...
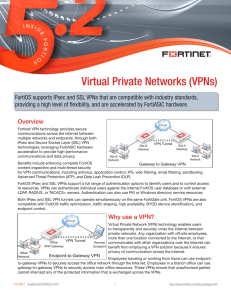
Virtual Private Networks (VPNs)
... VPN is the only workaround in this situation, since the HTTPS protocol used for SSL VPN is a standard Internet protocol required for many applications and is almost never blocked. SSL VPN is the best solution for endpoint-to-gateway VPNs. Remote users can securely log into the SSL VPN web portal fro ...
... VPN is the only workaround in this situation, since the HTTPS protocol used for SSL VPN is a standard Internet protocol required for many applications and is almost never blocked. SSL VPN is the best solution for endpoint-to-gateway VPNs. Remote users can securely log into the SSL VPN web portal fro ...