Chapter 5
... Fragments from different datagrams can arrive out of order and still be sorted out by : matching them using the IDENT field values; recognizing the last fragment from the bit set in its header; and recognizing when all fragments in an original datagram have been received. ...
... Fragments from different datagrams can arrive out of order and still be sorted out by : matching them using the IDENT field values; recognizing the last fragment from the bit set in its header; and recognizing when all fragments in an original datagram have been received. ...
ATM
... AAL3 used by connection-oriented packet services (e.g. X.25) AAL4 used by connectionless services (e.g. IP) ...
... AAL3 used by connection-oriented packet services (e.g. X.25) AAL4 used by connectionless services (e.g. IP) ...
socks - OpenLoop.com
... Allows client-server applications to transparently use the services of a network firewall without requiring direct IPrechability ...
... Allows client-server applications to transparently use the services of a network firewall without requiring direct IPrechability ...
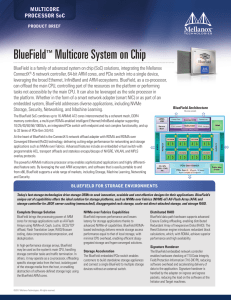
BlueField™ Multicore System on Chip
... Using a combination of advanced offloads and ARM compute capabilities, BlueField terminates network and security protocols inline. BlueField Smart NIC As a network adapter, BlueField offers the flexibility to fully or partially implement the data and control planes. As such, BlueField unlocks more e ...
... Using a combination of advanced offloads and ARM compute capabilities, BlueField terminates network and security protocols inline. BlueField Smart NIC As a network adapter, BlueField offers the flexibility to fully or partially implement the data and control planes. As such, BlueField unlocks more e ...
Connecting computers - Cambridge Regional College
... Port addresses Transport layer protocols use port addresses Each services listens on a port Port numbers 0 to 1024 are reserved Combination of IP address and port number is a socket ...
... Port addresses Transport layer protocols use port addresses Each services listens on a port Port numbers 0 to 1024 are reserved Combination of IP address and port number is a socket ...
physical address.
... Each one defines what information and services must provide for layer above it. Well-defined interfaces and layer functions provide modularity to a network ( could modified or replace without affect surrounding ) ...
... Each one defines what information and services must provide for layer above it. Well-defined interfaces and layer functions provide modularity to a network ( could modified or replace without affect surrounding ) ...
Security and Access Control Lists (ACLs)
... • Manage router security • Secure remote access • Logging router activity • Secure vulnerable router services and interfaces • Secure routing protocols • Control and filter network traffic • SDM can be used to configure security features on Cisco IOS based routers Version 2002-1 ...
... • Manage router security • Secure remote access • Logging router activity • Secure vulnerable router services and interfaces • Secure routing protocols • Control and filter network traffic • SDM can be used to configure security features on Cisco IOS based routers Version 2002-1 ...
Computer Networking Tutorial - ECE, Rutgers
... reliably. This distance, known as transmission range, is decided arbitrarily, depending on what is considered acceptable bit error rate. For example, we can define the transmission range as the sender-receiver distance for which the packet error rate is less than 10 %. In addition to thermal noise, ...
... reliably. This distance, known as transmission range, is decided arbitrarily, depending on what is considered acceptable bit error rate. For example, we can define the transmission range as the sender-receiver distance for which the packet error rate is less than 10 %. In addition to thermal noise, ...
CCNA2 Module 6
... A routing protocol is the communication used between routers. A routing protocol allows one router to share information with other routers regarding the networks it knows about as well as its proximity to other routers. The information a router gets from another router, using a routing protocol, is ...
... A routing protocol is the communication used between routers. A routing protocol allows one router to share information with other routers regarding the networks it knows about as well as its proximity to other routers. The information a router gets from another router, using a routing protocol, is ...
Document
... Support multiple topologies or virtualized network services e.g., support for multiple virtual networks multiple vid spaces may be constructed e.g., by defining different types of “physical” neighbors ...
... Support multiple topologies or virtualized network services e.g., support for multiple virtual networks multiple vid spaces may be constructed e.g., by defining different types of “physical” neighbors ...
Simplifying Manageability, Scalability and Host Mobility in Large-Scale Enterprise Networks using VEIL-click
... Shortest path routing using link state routing protocol on Ethernet switches ID Location separation for better mobility Seattle uses DHT style lookup, VL2 uses a directory service for flooding free lookup No flooding on data plane However, control plane still uses flooding! DHT style routing for sca ...
... Shortest path routing using link state routing protocol on Ethernet switches ID Location separation for better mobility Seattle uses DHT style lookup, VL2 uses a directory service for flooding free lookup No flooding on data plane However, control plane still uses flooding! DHT style routing for sca ...
Ruh_Cisco_EA_2006_04_24
... new 1RU, 2RU devices but 2,500 “application services”) • Management headache, high operations/ people costs • Exponential growth in application message traffic ...
... new 1RU, 2RU devices but 2,500 “application services”) • Management headache, high operations/ people costs • Exponential growth in application message traffic ...
SNMP Plus a Lightweight API for SNAP Handling
... and stretched resources provide two important requirements for network management solutions: (1) the response to network problems should be fast, and (2) the amount of traffic generated by the system itself should be kept to a minimum. Most of today’s networks rely on SNMP (Simple Network Management ...
... and stretched resources provide two important requirements for network management solutions: (1) the response to network problems should be fast, and (2) the amount of traffic generated by the system itself should be kept to a minimum. Most of today’s networks rely on SNMP (Simple Network Management ...
How Network Address Translation Works
... So what does the size of the Internet have to do with NAT? Everything! For a computer to communicate with other computers and Web servers on the Internet, it must have an IP address. An IP address (IP stands for Internet Protocol) is a unique 32-bit number that identifies the location of your comput ...
... So what does the size of the Internet have to do with NAT? Everything! For a computer to communicate with other computers and Web servers on the Internet, it must have an IP address. An IP address (IP stands for Internet Protocol) is a unique 32-bit number that identifies the location of your comput ...
irewall Presentation F Mike Shinn Casey Priester
... • At Defcon 19 (Dec 2011), Palo Alto firewall demonstrated to have fatal design flaw 1. Pescatore, J. & Young, G. (2009, October 19). Defining the Next-Generation Firewall. Gartner RAS Core Research Group. Retrieved from: http://img1.custompublish.com/getfile.php/1434855.1861.sqqycbrdwq/Defining+the ...
... • At Defcon 19 (Dec 2011), Palo Alto firewall demonstrated to have fatal design flaw 1. Pescatore, J. & Young, G. (2009, October 19). Defining the Next-Generation Firewall. Gartner RAS Core Research Group. Retrieved from: http://img1.custompublish.com/getfile.php/1434855.1861.sqqycbrdwq/Defining+the ...
15. Interior Routing Protocols
... Slow convergence may cause: All link costs 1 B has distance to network 5 as 2, next hop D A & C have distance 3 and next hop B ...
... Slow convergence may cause: All link costs 1 B has distance to network 5 as 2, next hop D A & C have distance 3 and next hop B ...
H.225 Call Signaling
... providing multimedia communication over packet-based networks H.323 can be applied in a variety of mechanisms audio only (IP telephony); audio and video … H.323 provides myriad services and, therefore, can be applied in a wide variety of areas consumer, business, and entertainment applications. ...
... providing multimedia communication over packet-based networks H.323 can be applied in a variety of mechanisms audio only (IP telephony); audio and video … H.323 provides myriad services and, therefore, can be applied in a wide variety of areas consumer, business, and entertainment applications. ...
Slide 1
... Network of nodes and few powerful base stations ● 102 – 106 sensor nodes ● particular nodes deployed randomly, e.g., from plane ...
... Network of nodes and few powerful base stations ● 102 – 106 sensor nodes ● particular nodes deployed randomly, e.g., from plane ...
ppt
... Is the network regarded as flat or hierarchical? – Compare topology control, traditional routing Which data is used to identify nodes? – An arbitrary identifier? – The position of a node? • Can be used to assist in geographic routing protocols because choice of next hop neighbor can be computed ba ...
... Is the network regarded as flat or hierarchical? – Compare topology control, traditional routing Which data is used to identify nodes? – An arbitrary identifier? – The position of a node? • Can be used to assist in geographic routing protocols because choice of next hop neighbor can be computed ba ...
Decentralised Service Composition using Potential Fields in Internet
... denotes the set of wireless links among nodes which can communicate directly. We consider ܸ ൌ ܸ ܸ ௌ , where ܸ represents the set of all high level devices (e.g. tablets, smartphones, RFID readers), and ܸ ௌ represents the set of low level devices (e.g. RFIDs, sensors). Services run on high le ...
... denotes the set of wireless links among nodes which can communicate directly. We consider ܸ ൌ ܸ ܸ ௌ , where ܸ represents the set of all high level devices (e.g. tablets, smartphones, RFID readers), and ܸ ௌ represents the set of low level devices (e.g. RFIDs, sensors). Services run on high le ...
History of Data Compression
... Acknowledged mode is similar to modem operation using V.42 error correction procedures in that packets are partitioned, as necessary, into segments that are transmitted to the peer over a reliable link and acknowledged by the peer. If the peer does not correctly receive a segment, it is re-transmitt ...
... Acknowledged mode is similar to modem operation using V.42 error correction procedures in that packets are partitioned, as necessary, into segments that are transmitted to the peer over a reliable link and acknowledged by the peer. If the peer does not correctly receive a segment, it is re-transmitt ...
Introduction - Communications
... Different Views of Networking • Different Layers of the protocol stack have a different view of the network. This is HTTP’s and TCP’s view of the network. ...
... Different Views of Networking • Different Layers of the protocol stack have a different view of the network. This is HTTP’s and TCP’s view of the network. ...
Network+ Guide to Networks, Fourth Edition
... Twisted pair cables support a wide variety of fast, modern network standards. Twisted pair cabling is composed of the following components: • Two wires that carry the data signals (one conductor carries a positive signal; one carries a negative signal). They are made of 22 or 24 gauge copper wiring. ...
... Twisted pair cables support a wide variety of fast, modern network standards. Twisted pair cabling is composed of the following components: • Two wires that carry the data signals (one conductor carries a positive signal; one carries a negative signal). They are made of 22 or 24 gauge copper wiring. ...
module02-reviewV2
... Different Views of Networking • Different Layers of the protocol stack have a different view of the network. This is HTTP’s and TCP’s view of the network. ...
... Different Views of Networking • Different Layers of the protocol stack have a different view of the network. This is HTTP’s and TCP’s view of the network. ...