Contents Technical support
... The Alpha® Gateway Interface allows for the exchange of data between a PLC and Alpha® sign(s) to show messages and real-time data on a system. The AGI is connected to Alpha® signs via a multi-drop (RS485) network which will support up to 32 drops before requiring a repeater. Alpha® signs can be assi ...
... The Alpha® Gateway Interface allows for the exchange of data between a PLC and Alpha® sign(s) to show messages and real-time data on a system. The AGI is connected to Alpha® signs via a multi-drop (RS485) network which will support up to 32 drops before requiring a repeater. Alpha® signs can be assi ...
Firewall - theodoros christophides site
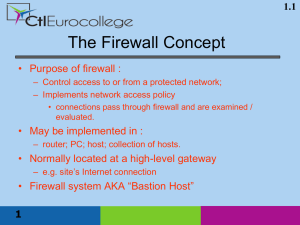
... – firewall designed to prevent outsiders from accessing sensitive data – many attacks would not need to use the firewall ...
... – firewall designed to prevent outsiders from accessing sensitive data – many attacks would not need to use the firewall ...
Network Addressing - Cisco Networking Academy
... network can communicate with hosts on different networks. Each interface on a router is connected to a separate network. The IP address assigned to the router interface identifies which local network is connected directly to it. Every host on a network must use the router as a gateway to other netwo ...
... network can communicate with hosts on different networks. Each interface on a router is connected to a separate network. The IP address assigned to the router interface identifies which local network is connected directly to it. Every host on a network must use the router as a gateway to other netwo ...
Transport of Signaling over IP
... SS7 MTP3-User Adaptation Layer (M3UA)Management Information Base using SMIv2 (129205 bytes) V5.2-User Adaption Layer (V5UA) (41441 bytes) DPNSS/DASS 2 extensions to the IUA protocol (21903 bytes) ...
... SS7 MTP3-User Adaptation Layer (M3UA)Management Information Base using SMIv2 (129205 bytes) V5.2-User Adaption Layer (V5UA) (41441 bytes) DPNSS/DASS 2 extensions to the IUA protocol (21903 bytes) ...
Wireless Electronic Notice Board
... ZigBee has a defined rate of 250 kbit/s, best suited for periodic or intermittent data or a single signal transmission from a sensor or input device. Applications include wireless light switches, electrical meters with inhome-displays, traffic management systems, and other consumer and industrial eq ...
... ZigBee has a defined rate of 250 kbit/s, best suited for periodic or intermittent data or a single signal transmission from a sensor or input device. Applications include wireless light switches, electrical meters with inhome-displays, traffic management systems, and other consumer and industrial eq ...
Enterprise Mac Test Plan Introduction The purpose of this effort is to
... The ability of the system to cache user account information for use when the system is off the network and/or no longer in touch with campus infrastructure resources. 2.4. Access Controls The ability to control system access locally at the console and remotely via network protocols. 2.5. Group Polic ...
... The ability of the system to cache user account information for use when the system is off the network and/or no longer in touch with campus infrastructure resources. 2.4. Access Controls The ability to control system access locally at the console and remotely via network protocols. 2.5. Group Polic ...
Y-Comm: A new architecture for heterogeneous networking
... Proactive Policy Management ◦ The mobile node can know or estimate the network state at a given point before it arrives at that point ◦ Proactive Policies allow us to maximize the use of available channels provided you know the amount of time a channel will be available. ◦ That time is known as: T ...
... Proactive Policy Management ◦ The mobile node can know or estimate the network state at a given point before it arrives at that point ◦ Proactive Policies allow us to maximize the use of available channels provided you know the amount of time a channel will be available. ◦ That time is known as: T ...
Protocols and the tcp/ip suite
... INTERNETWORKING TERMS • End System (ES) – device used to support end-user applications or services • Intermediate System (IS) – device used to connect two networks • Bridge – an IS used to connect two LANs that use similar LAN protocols • Router - an IS used to connect two networks that may or may ...
... INTERNETWORKING TERMS • End System (ES) – device used to support end-user applications or services • Intermediate System (IS) – device used to connect two networks • Bridge – an IS used to connect two LANs that use similar LAN protocols • Router - an IS used to connect two networks that may or may ...
Introductory Guide to Z
... of devices that are not within direct range of the primary controller. The image below represents an ideal installation using NWI. The key is nodes 1-4 must support NWI in order to pass the inclusion message on to the primary controller during the inclusion process. As depicted by the following figu ...
... of devices that are not within direct range of the primary controller. The image below represents an ideal installation using NWI. The key is nodes 1-4 must support NWI in order to pass the inclusion message on to the primary controller during the inclusion process. As depicted by the following figu ...
Chap 18 - The University of Tulsa
... As an example of hierarchical routing, let us consider Figure 18.36. A regional ISP is granted 16,384 addresses starting from 120.14.64.0. The regional ISP has decided to divide this block into 4 subblocks, each with 4096 addresses. Three of these sub-blocks are assigned to three local ISPs, the sec ...
... As an example of hierarchical routing, let us consider Figure 18.36. A regional ISP is granted 16,384 addresses starting from 120.14.64.0. The regional ISP has decided to divide this block into 4 subblocks, each with 4096 addresses. Three of these sub-blocks are assigned to three local ISPs, the sec ...
LevelOne
... secures function of the device in rough environments (WAB-1000H). The devices comply with IEEE 802.11b/g standard with a data transmission rate of up to 54Mbps and work in AP-, Repeater- and Bridging mode at the same time. Security functions like 64/128bit WEP and AES/3DES encoding, Wi-FI protected ...
... secures function of the device in rough environments (WAB-1000H). The devices comply with IEEE 802.11b/g standard with a data transmission rate of up to 54Mbps and work in AP-, Repeater- and Bridging mode at the same time. Security functions like 64/128bit WEP and AES/3DES encoding, Wi-FI protected ...
VINE - UiO
... ”QoS is the measure of how good a service is, as presented to the user. It is expressed in user understandable language and manifests itself in a number of parameters, all of which have either subjective or objective values.” ...
... ”QoS is the measure of how good a service is, as presented to the user. It is expressed in user understandable language and manifests itself in a number of parameters, all of which have either subjective or objective values.” ...
Networking-101026
... A router will be used for wireless printer sharing and all the following steps are recommended to configure and secure a wireless router when used with an AARP Tax-Aide network for printer sharing: 1. Infrastructure network configuration will be used. Ad-Hoc networks are not permitted. 2. The wirele ...
... A router will be used for wireless printer sharing and all the following steps are recommended to configure and secure a wireless router when used with an AARP Tax-Aide network for printer sharing: 1. Infrastructure network configuration will be used. Ad-Hoc networks are not permitted. 2. The wirele ...
Avaya Network Operating System 6.0
... • Stealth Topology – End-to-end virtual network segments are completely ...
... • Stealth Topology – End-to-end virtual network segments are completely ...
AREN - ASC
... Introduction to Computer Networking (OSI) Review of Common Components (show and tell) Ethernet ins and outs (theory and hands-on) Intro to TCP/IP addressing (don’t worry!) ...
... Introduction to Computer Networking (OSI) Review of Common Components (show and tell) Ethernet ins and outs (theory and hands-on) Intro to TCP/IP addressing (don’t worry!) ...
P2P final
... When a new user joins the Gnutella Network, he broadcasts a message called a "ping request" to the network, announcing his presence on the network. Nodes which receive this ping, send a “Pong” back to the pinging user to acknowledge that they have received this message. ...
... When a new user joins the Gnutella Network, he broadcasts a message called a "ping request" to the network, announcing his presence on the network. Nodes which receive this ping, send a “Pong” back to the pinging user to acknowledge that they have received this message. ...
authors(v7) - IDA.LiU.se
... run applications may be stationary (nonmobile) or mobile • wireless does not always mean mobility ...
... run applications may be stationary (nonmobile) or mobile • wireless does not always mean mobility ...
Lecture03
... Power management for local processing, e.g., how accurately can we predict energy consumption? What is the energy tradeoff between local processing of data vs. sending the data to do remote processing? Running a CPU, a sensor device, or a communication device in sleep mode can save energy considerab ...
... Power management for local processing, e.g., how accurately can we predict energy consumption? What is the energy tradeoff between local processing of data vs. sending the data to do remote processing? Running a CPU, a sensor device, or a communication device in sleep mode can save energy considerab ...
tina-thesis - CSE
... A player's position in virtual environment drives its preferences on entity updates ...
... A player's position in virtual environment drives its preferences on entity updates ...
Demystifying Multimedia Conferencing Over the Internet
... secure access to the conference using various authentication mechanisms. Q.931 and H.245 messages can be routed through the gatekeeper, and statistical information about the calls in progress can be collected. Gatekeepers may also perform telephony service operations such as call forwarding and call ...
... secure access to the conference using various authentication mechanisms. Q.931 and H.245 messages can be routed through the gatekeeper, and statistical information about the calls in progress can be collected. Gatekeepers may also perform telephony service operations such as call forwarding and call ...
Module 3 - IT, Sligo
... DUAL guarantees loop-free operation at every instant throughout a route computation allowing all routers involved in a topology change to synchronize at the same time ...
... DUAL guarantees loop-free operation at every instant throughout a route computation allowing all routers involved in a topology change to synchronize at the same time ...
Research on Routing in Mobile/Wireless Ad
... system cannot forward packets to its new locations. ...
... system cannot forward packets to its new locations. ...