Rate Scaling Laws in Multicell Networks under
... achieved when path loss is accounted for. II. N ETWORK AND SIGNAL MODELS We consider a wireless network featuring a number N of transmit-receive active pairs, which are simultaneously selected for transmission by the scheduling protocol at any considered instant of time, others remaining silent. All ...
... achieved when path loss is accounted for. II. N ETWORK AND SIGNAL MODELS We consider a wireless network featuring a number N of transmit-receive active pairs, which are simultaneously selected for transmission by the scheduling protocol at any considered instant of time, others remaining silent. All ...
Computer Networks
... companies and for individuals. For companies, networks of personal computers using shared servers often provide access to corporate information. Typically they follow the client-server model, with client workstations on employee desktops accessing powerful servers in the machine room. For individual ...
... companies and for individuals. For companies, networks of personal computers using shared servers often provide access to corporate information. Typically they follow the client-server model, with client workstations on employee desktops accessing powerful servers in the machine room. For individual ...
PDF
... ● The transition to IPv6 is expected to lead to a long period of coexistence between IPv4 and IPv6. There are multiple different ways of making the transition to IPv6 but it is commonly believed that the use of 6PE and 6VPE for IPv6 VPNs presents the least amount of risk to existing networks without ...
... ● The transition to IPv6 is expected to lead to a long period of coexistence between IPv4 and IPv6. There are multiple different ways of making the transition to IPv6 but it is commonly believed that the use of 6PE and 6VPE for IPv6 VPNs presents the least amount of risk to existing networks without ...
Routing Table Lookup
... – H: route is to a host, I.e., destination address is the complete host address; if flag is not set, route is to a network and destination address is netID or subnetID – D: route created by redirect – M: route modified by redirect • Refcnt: reference count: number of active uses of each route; for e ...
... – H: route is to a host, I.e., destination address is the complete host address; if flag is not set, route is to a network and destination address is netID or subnetID – D: route created by redirect – M: route modified by redirect • Refcnt: reference count: number of active uses of each route; for e ...
Viewing Network Element Properties
... navigation pane, the information displayed in the content pane is updated. The branches in the navigation pane can be expanded and collapsed to display and hide information as needed. The window heading and the highest level in the navigation pane display the name of the VNE given to the device as d ...
... navigation pane, the information displayed in the content pane is updated. The branches in the navigation pane can be expanded and collapsed to display and hide information as needed. The window heading and the highest level in the navigation pane display the name of the VNE given to the device as d ...
High Performance Networks for High Performance
... High-Performance Businesses View the Network as Critical to Success High-Performance Businesses Profile ...
... High-Performance Businesses View the Network as Critical to Success High-Performance Businesses Profile ...
The Tenet Architecture for Tiered Sensor Networks
... and unexpected failure modes, are particularly important for the challenging environments in which sensor networks are deployed. Manageability implies, for example, that tools in the task library must provide useful insight into network problems—such as why a particular sensor or group of sensors is ...
... and unexpected failure modes, are particularly important for the challenging environments in which sensor networks are deployed. Manageability implies, for example, that tools in the task library must provide useful insight into network problems—such as why a particular sensor or group of sensors is ...
02_TCPIP
... This is where DoD M&S network standards live. There have been several over the years: • Ad hoc: Created as needed for proprietary systems; elder days to present • Distributed Interactive Simulation (DIS): 1993-> present • High Level Architecture (HLA): circa 1998-present • TENA: Circa 2000-present • ...
... This is where DoD M&S network standards live. There have been several over the years: • Ad hoc: Created as needed for proprietary systems; elder days to present • Distributed Interactive Simulation (DIS): 1993-> present • High Level Architecture (HLA): circa 1998-present • TENA: Circa 2000-present • ...
ASI5308, ASI5316, ASI6316
... TMS320C6713 VLIW floating point DSP connected to a highspeed bus-master PCI Express interface. AudioScience MRX technology allows up to 8 (ASI5308) or 16 (ASI5316/ASI6316) streams of different formats and sample rates to be played, recorded, and mixed over CobraNet. For the ASI5308/ASI5416, a choice ...
... TMS320C6713 VLIW floating point DSP connected to a highspeed bus-master PCI Express interface. AudioScience MRX technology allows up to 8 (ASI5308) or 16 (ASI5316/ASI6316) streams of different formats and sample rates to be played, recorded, and mixed over CobraNet. For the ASI5308/ASI5416, a choice ...
Document
... Intra/inter-gigaPoP connectivity can be optimized and separate bandwidth allocated to other or special purpose requirements. Primary gigaPoP service is provided by the IP Routing Elements. They are fed directly from external SONET/PPP or high speed synchronous circuits via PVC/SVC links. All QoS sup ...
... Intra/inter-gigaPoP connectivity can be optimized and separate bandwidth allocated to other or special purpose requirements. Primary gigaPoP service is provided by the IP Routing Elements. They are fed directly from external SONET/PPP or high speed synchronous circuits via PVC/SVC links. All QoS sup ...
User Guide
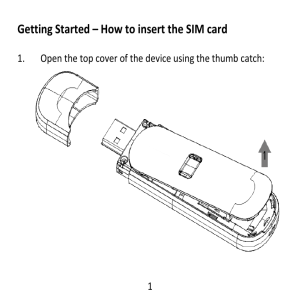
... a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to be used as a handheld or body worn device but SAR tests have been successfully completed in accordance with the Australian regulatory requirements. ...
... a clear space around the device to allow the transmit and receive signals to propagate. It is not intended to be used as a handheld or body worn device but SAR tests have been successfully completed in accordance with the Australian regulatory requirements. ...
Overview Discovery & Exploration
... Example – CCNA Discovery Skills Development Networking for Home Working at a Small-toor Small Businesses Medium Business or ISP ...
... Example – CCNA Discovery Skills Development Networking for Home Working at a Small-toor Small Businesses Medium Business or ISP ...
Slide 1
... Interoperability between IP-PBX and Service Provider Quality of Service (QoS) Security ...
... Interoperability between IP-PBX and Service Provider Quality of Service (QoS) Security ...
Topic 16: Routing in IP over ATM networks
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
... The packet encapsulation has been defined in RFC1483 ([9], now obsoleted by [10]), which also takes into account the saving of virtual connections by multiplexing different protocols into a single VC. The LLC/SNAP encapsulation defined in RFC1483 is the most common encapsulation in IP over ATM netwo ...
STA-UI-A0037s (BlueW_2310 USB version) User`s Manual
... and one or more Wireless USB dongle. This type of network provides a coverage area sufficient to satisfy the network requirements for many homes and small businesses. The Access Point connects your network computers to an existing network. Once this “infrastructure” is in place, you can easily add c ...
... and one or more Wireless USB dongle. This type of network provides a coverage area sufficient to satisfy the network requirements for many homes and small businesses. The Access Point connects your network computers to an existing network. Once this “infrastructure” is in place, you can easily add c ...
Dell SonicWALL NSA Series
... the appliance, NSA appliance also have access to the Dell SonicWALL CloudAV Service, which extends the onboard signature intelligence with more than twelve million signatures. This CloudAV database is accessed via a proprietary light-weight protocol by the firewall to augment the inspection done on ...
... the appliance, NSA appliance also have access to the Dell SonicWALL CloudAV Service, which extends the onboard signature intelligence with more than twelve million signatures. This CloudAV database is accessed via a proprietary light-weight protocol by the firewall to augment the inspection done on ...
Orf467F10Networks
... buckets and The contents of bucket k are content(k). Whenever we update the distance label of node i from d1 to d2 we move node i from contents (d1) to contents(d2). This can be done with a doubly-linked list (each cell has two links, one to the preceding cell and the other to the succeeding cell. E ...
... buckets and The contents of bucket k are content(k). Whenever we update the distance label of node i from d1 to d2 we move node i from contents (d1) to contents(d2). This can be done with a doubly-linked list (each cell has two links, one to the preceding cell and the other to the succeeding cell. E ...
Technical Report DSL Forum TR-059
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
PDF
... devices require location information. Dynamic updates of location information are required to support mobility of the endpoints (wired or wireless). For example, if a wired phone is provisioned for Cube B6-1, Floor 3, Building 19, and if the person whose phone this is moves to Cube C5-2, Floor 2, Bu ...
... devices require location information. Dynamic updates of location information are required to support mobility of the endpoints (wired or wireless). For example, if a wired phone is provisioned for Cube B6-1, Floor 3, Building 19, and if the person whose phone this is moves to Cube C5-2, Floor 2, Bu ...
Secure Network Infrastructure
... The connection is private. Encryption is used after an initial handshake to define a secret key. Symmetric cryptography is used for data encryption (for example, DES and RC4). The peer’s identity can be authenticated using asymmetric, or public key, cryptography (for example, RSA and DSS). The ...
... The connection is private. Encryption is used after an initial handshake to define a secret key. Symmetric cryptography is used for data encryption (for example, DES and RC4). The peer’s identity can be authenticated using asymmetric, or public key, cryptography (for example, RSA and DSS). The ...
A Multi-Radio Unification Protocol for IEEE 802.11
... significant decrease in performance. Also, it is possible that the node misses an RTS/CTS exchange on one channel when listening on another, causing the hidden terminal problem to re-surface. For all these reasons, to the best of our knowledge, systems built over the IEEE 802.11 standard operate usi ...
... significant decrease in performance. Also, it is possible that the node misses an RTS/CTS exchange on one channel when listening on another, causing the hidden terminal problem to re-surface. For all these reasons, to the best of our knowledge, systems built over the IEEE 802.11 standard operate usi ...
Wavenis Ecosystem - Integrator catalog
... key goal of this research was to achieve low energy consumption for the overall system and its communications, which is why Wavenis® wireless technology was chosen as the data link between the wireless sensor devices. Event-driven and asynchronous protocols were proposed for self-configuration, self ...
... key goal of this research was to achieve low energy consumption for the overall system and its communications, which is why Wavenis® wireless technology was chosen as the data link between the wireless sensor devices. Event-driven and asynchronous protocols were proposed for self-configuration, self ...
Serial and Asynchronous High-Speed WAN Interface Cards for
... Synchronous serial ports are typically used in the following networking solutions: ...
... Synchronous serial ports are typically used in the following networking solutions: ...
FASP Technology Datasheet
... Comprehensive configuration of server software from a web browser, a desktop GUI or command line. Complete server-side policy management: enforce all Aspera transfer properties including authorization (allowed direction, allowed IP, and secure token lifetime), bandwidth controls, encryption settings, ...
... Comprehensive configuration of server software from a web browser, a desktop GUI or command line. Complete server-side policy management: enforce all Aspera transfer properties including authorization (allowed direction, allowed IP, and secure token lifetime), bandwidth controls, encryption settings, ...