.pdf
... during a run. Especially multimedia content analysis applications have to process huge amounts of image and video data [27]. For example, the Netherlands Forensic Institute (NFI) urgently needs to detect objects and people in video streams of surveillance cameras. Identifying materials or land-cover ...
... during a run. Especially multimedia content analysis applications have to process huge amounts of image and video data [27]. For example, the Netherlands Forensic Institute (NFI) urgently needs to detect objects and people in video streams of surveillance cameras. Identifying materials or land-cover ...
COMP680E by M. Hamdi
... • To receive performance guarantee from the network, resource reservation must be set up before the application can start transmitting packets. • Sender starts the setup of a reservation by sending characteristics and resource requirement of the flow. • The network can accept the new application flo ...
... • To receive performance guarantee from the network, resource reservation must be set up before the application can start transmitting packets. • Sender starts the setup of a reservation by sending characteristics and resource requirement of the flow. • The network can accept the new application flo ...
Quantitative examination of stimulus
... delivered to a single site in almost all experiments; only when it is mentioned explicitly were stimuli delivered to two sites simultaneously. Monophasic, negative voltage pulses of 0.4-ms width and 0.5– 0.7 V amplitude were used to minimize oxidation of TiN electrodes, which would increase their im ...
... delivered to a single site in almost all experiments; only when it is mentioned explicitly were stimuli delivered to two sites simultaneously. Monophasic, negative voltage pulses of 0.4-ms width and 0.5– 0.7 V amplitude were used to minimize oxidation of TiN electrodes, which would increase their im ...
The QoSbox: A PC-Router for Quantitative Service Differentiation in IP Networks ∗
... sending rates at the sources. Consequently, the backlog at bottleneck links is generally highly variable. A static configuration of the worst-case, as in CBQ, therefore results in under-utilizing network resources such as bandwidth [30], and it is desirable to use instead an architecture dynamically ...
... sending rates at the sources. Consequently, the backlog at bottleneck links is generally highly variable. A static configuration of the worst-case, as in CBQ, therefore results in under-utilizing network resources such as bandwidth [30], and it is desirable to use instead an architecture dynamically ...
The evolutionary origins of modularity References
... evolves not because it conveys evolvability, but as a byproduct from selection to reduce connection costs in a network (figure 1) [9,16]. Such costs include manufacturing connections, maintaining them, the energy to transmit along them and signal delays, all of which increase as a function of connec ...
... evolves not because it conveys evolvability, but as a byproduct from selection to reduce connection costs in a network (figure 1) [9,16]. Such costs include manufacturing connections, maintaining them, the energy to transmit along them and signal delays, all of which increase as a function of connec ...
IPv6
... Existing applications and networking protocols do not work with changing IP addresses Applications do not “reconnect” when a new IP address appears • TCP drops session when IP address changes • IPSEC hashes across IP addresses, changing address breaks the Security Association ...
... Existing applications and networking protocols do not work with changing IP addresses Applications do not “reconnect” when a new IP address appears • TCP drops session when IP address changes • IPSEC hashes across IP addresses, changing address breaks the Security Association ...
View
... x.y.z.t defines one of the addresses and the /n defines the mask The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost 32 − n bits to 1s. ...
... x.y.z.t defines one of the addresses and the /n defines the mask The first address in the block can be found by setting the rightmost 32 − n bits to 0s The last address in the block can be found by setting the rightmost 32 − n bits to 1s. ...
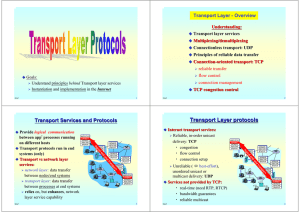
Transport Layer protocols
... between app’ processes running application transport network data link on different hosts physical Transport protocols run in end ...
... between app’ processes running application transport network data link on different hosts physical Transport protocols run in end ...
CCNA 1: Chapter 11 Exam Answer v4.0 100%
... The connection between routers B and C has been successfully tested. However, after rebooting router C, the administrator noticed the response time between networks 10.10.3.0 and 10.10.4.0 is slower. Ping between the two routers is successful. A trace route indicates three hops from router B to rout ...
... The connection between routers B and C has been successfully tested. However, after rebooting router C, the administrator noticed the response time between networks 10.10.3.0 and 10.10.4.0 is slower. Ping between the two routers is successful. A trace route indicates three hops from router B to rout ...
20100810-OSG-NPW-Diagnostics
... about performance to another, get as much information as possible • Is the problem un-directional? Bi-directional? • Does the problem occur all the time, frequently, or rarely? • Does the problem occur for only a specific application, many applications, or only some applications? • Is the problem re ...
... about performance to another, get as much information as possible • Is the problem un-directional? Bi-directional? • Does the problem occur all the time, frequently, or rarely? • Does the problem occur for only a specific application, many applications, or only some applications? • Is the problem re ...
PRP - Seamless redundancy for Industrial Ethernet scheme
... - the sender inserts the same sequence counter into both frames of a pair, and increments it by one for each frame sent. - the receiver keeps track of the sequence counter for each for each source MAC address it receives frames from. Frames with the same source and counter value coming from differen ...
... - the sender inserts the same sequence counter into both frames of a pair, and increments it by one for each frame sent. - the receiver keeps track of the sequence counter for each for each source MAC address it receives frames from. Frames with the same source and counter value coming from differen ...
Final Presentation - High Speed Digital Systems Laboratory
... Linux kernel sources – must be used to compile the kernel module Microsoft Visual studio – developing Packet Generator GUI and COM serial communicator Ethereal Network sniffer – great (and free) tool for receiving and checking the packet streams Putty – free program for serial communication ...
... Linux kernel sources – must be used to compile the kernel module Microsoft Visual studio – developing Packet Generator GUI and COM serial communicator Ethereal Network sniffer – great (and free) tool for receiving and checking the packet streams Putty – free program for serial communication ...
IP-PBX - Ingate Systems
... Prior to SIPconnect, the state of standards for connecting an IP PBX with a VoIP service provider were largely undefined and predictable interoperability did not exist. “SIP” alone does not mean compatibility. “SIP” is comprised of 45+ RFCs, 25+ related RFCs (e.g. SDP), and numerous Internet Drafts. ...
... Prior to SIPconnect, the state of standards for connecting an IP PBX with a VoIP service provider were largely undefined and predictable interoperability did not exist. “SIP” alone does not mean compatibility. “SIP” is comprised of 45+ RFCs, 25+ related RFCs (e.g. SDP), and numerous Internet Drafts. ...
Network Infrastructure for EtherNet/IP
... Note from the Publisher The application of Ethernet and Internet technologies is permeating every aspect of manufacturing automation today—control, safety, configuration and diagnostics, synchronization and motion, and information. To realize the benefits of these technologies, the network infrastru ...
... Note from the Publisher The application of Ethernet and Internet technologies is permeating every aspect of manufacturing automation today—control, safety, configuration and diagnostics, synchronization and motion, and information. To realize the benefits of these technologies, the network infrastru ...
01_FC_and_Host_Supported_Configurations_v1
... devices that need to communicate with each other are located on the same switch or segment, then these two devices are said to have high locality. If these same devices are located on different switches or segments of a fabric and these two devices need to communicate with each other, then these dev ...
... devices that need to communicate with each other are located on the same switch or segment, then these two devices are said to have high locality. If these same devices are located on different switches or segments of a fabric and these two devices need to communicate with each other, then these dev ...
Finite State Automata that Recurrent Cascade
... cannot oscillate with a period greater than 2, which is exactly what was proven in Section 5. This proves that the automaton of Figure lc) (among others) cannot be implemented by RCC. In addition to unifying both the results of Giles et. al. and Section 5, the theorem of Section 6 also accounts for ...
... cannot oscillate with a period greater than 2, which is exactly what was proven in Section 5. This proves that the automaton of Figure lc) (among others) cannot be implemented by RCC. In addition to unifying both the results of Giles et. al. and Section 5, the theorem of Section 6 also accounts for ...
ROBUSTNESS AGAINST LARGE-SCALE FAILURES IN COMMUNICATIONS NETWORKS Juan SEGOVIA SILVERO Dipòsit legal: GI-251-2012
... networks for business and leisure and there is high expectation on their availability and performance. Communications networks (or a part thereof) can experience failures, for example due to cables cuts or node breakdowns, but such isolated failures usually go unnoticed by users thanks to effective ...
... networks for business and leisure and there is high expectation on their availability and performance. Communications networks (or a part thereof) can experience failures, for example due to cables cuts or node breakdowns, but such isolated failures usually go unnoticed by users thanks to effective ...
Steps to Troubleshoot Database Replication
... The Hosts files are mismatched: There is a possibility of an incorrect activity when an IP address changes or updates to the Hostname on the server. Refer to this link in order to change IP address to the Hostname for the CUCM. IP Address and Hostname Changes Restart the following services from the ...
... The Hosts files are mismatched: There is a possibility of an incorrect activity when an IP address changes or updates to the Hostname on the server. Refer to this link in order to change IP address to the Hostname for the CUCM. IP Address and Hostname Changes Restart the following services from the ...
Chapter5_24_Nov_2010_v2
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! random access MAC protocols efficient at low load: single node can fully uti ...
... “Taking Turns” MAC protocols channel partitioning MAC protocols: share channel efficiently and fairly at high load inefficient at low load: delay in channel access, 1/N bandwidth allocated even if only 1 active node! random access MAC protocols efficient at low load: single node can fully uti ...
Chapter 8: Networking and Digital Communication
... All of the following are advantages of using a computer network EXCEPT that it: A. reduces costs when hardware is shared. B. promotes independence so users have exclusive control over their own data and applications. C. saves money when software is shared. D. enables data sharing, increasing efficie ...
... All of the following are advantages of using a computer network EXCEPT that it: A. reduces costs when hardware is shared. B. promotes independence so users have exclusive control over their own data and applications. C. saves money when software is shared. D. enables data sharing, increasing efficie ...
The Internet and Its Uses - Mt. Hood Community College
... mode when they are set to 10 or 100 Mb/s, but when set to 1,000 Mb/s, they operate only in full-duplex mode Note: Autonegotiation can produce unpredictable results. –By default, when autonegotiation fails, the Catalyst switch sets the corresponding switch port to half-duplex mode. •This type of fa ...
... mode when they are set to 10 or 100 Mb/s, but when set to 1,000 Mb/s, they operate only in full-duplex mode Note: Autonegotiation can produce unpredictable results. –By default, when autonegotiation fails, the Catalyst switch sets the corresponding switch port to half-duplex mode. •This type of fa ...
Document
... to control the exact route – in this case, the actual Rx is listed in the routing table and the desired next hop is listed • Default Routing – instead of listing all of the various networks in the Internet, Tx host would use one entry called the Default (network address 0.0.0.0) ...
... to control the exact route – in this case, the actual Rx is listed in the routing table and the desired next hop is listed • Default Routing – instead of listing all of the various networks in the Internet, Tx host would use one entry called the Default (network address 0.0.0.0) ...
Dell presentation template Standard 4:3 layout
... Beyond Firewall – Benefits for customers Firewall appliances “Platform” “It is not a box” it the heart of your security network ...
... Beyond Firewall – Benefits for customers Firewall appliances “Platform” “It is not a box” it the heart of your security network ...