William Stallings Data and Computer Communications
... Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
... Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
Network Management Protocols
... Because of these two problems and many user requests to enhance features of MRTG, a new version of MRTG was released in January 1997 (MRTG-2.0). This new release became even more popular by users because it was much faster and more user-friendly than the previous release. For example, Version 2.0 ha ...
... Because of these two problems and many user requests to enhance features of MRTG, a new version of MRTG was released in January 1997 (MRTG-2.0). This new release became even more popular by users because it was much faster and more user-friendly than the previous release. For example, Version 2.0 ha ...
Pretest Answers
... b. They are recommended for networks with fewer than 10 users in the same physical area. c. They require a powerful central server. d. Users are typically located in a large geographical area. 36. Which one of the following best describes a bus topology network? a. It needs significantly more cablin ...
... b. They are recommended for networks with fewer than 10 users in the same physical area. c. They require a powerful central server. d. Users are typically located in a large geographical area. 36. Which one of the following best describes a bus topology network? a. It needs significantly more cablin ...
CIS339
... You should consider the following design options: i. 802.11b Wireless LAN. ii. 10Base-T Ethernet using unshielded twisted pair wiring. iii. 10Base-F Ethernet using fibre optic cable. ...
... You should consider the following design options: i. 802.11b Wireless LAN. ii. 10Base-T Ethernet using unshielded twisted pair wiring. iii. 10Base-F Ethernet using fibre optic cable. ...
Enterprise Network Analyzer and OmniEngine Console
... segment, including 10GbE, Gigabit, WAN, and wireless segments, as well as any network segment configured with an OmniEngine • Analyze and troubleshoot both data and media traffic using one single product • Monitor networks with high-level network views, or “Dashboards,” and instantly drill down to ...
... segment, including 10GbE, Gigabit, WAN, and wireless segments, as well as any network segment configured with an OmniEngine • Analyze and troubleshoot both data and media traffic using one single product • Monitor networks with high-level network views, or “Dashboards,” and instantly drill down to ...
Blue Gene/L system architecture
... dispatch, out of order execution and out of order completion, etc ...
... dispatch, out of order execution and out of order completion, etc ...
Video-surveillance Citizen Network
... The professional point-to-multipoint ARBA Pro solution by Albentia Systems was selected because it has been specially designed for video-surveillance and security applications. It is a solution with extraordinary spectral efficiency, QoS and powerful security mechanisms which, combined with the robu ...
... The professional point-to-multipoint ARBA Pro solution by Albentia Systems was selected because it has been specially designed for video-surveillance and security applications. It is a solution with extraordinary spectral efficiency, QoS and powerful security mechanisms which, combined with the robu ...
COMBO Introduction
... • In the past, fixed and mobile access networks have been optimized and evolved ...
... • In the past, fixed and mobile access networks have been optimized and evolved ...
Adam Arvay IGVA 1 Opening the black box of connectionist nets
... different varieties of sentences that contain the word laughed. No matter how you set up the vectors you would end up with that solution surface which cannot be separated. ...
... different varieties of sentences that contain the word laughed. No matter how you set up the vectors you would end up with that solution surface which cannot be separated. ...
benefits of a connected world
... IEEE 802.11y-2008 extended operation of 802.11a to the licensed 3.7 GHz band. Increased power limits allow a range up to 5,000 m. As of 2009[update], it is only being licensed in the United States by the FCC. Assumes short guard interval (SGI) enabled otherwise reduces each data rate by 10%. ...
... IEEE 802.11y-2008 extended operation of 802.11a to the licensed 3.7 GHz band. Increased power limits allow a range up to 5,000 m. As of 2009[update], it is only being licensed in the United States by the FCC. Assumes short guard interval (SGI) enabled otherwise reduces each data rate by 10%. ...
GigaVUE-420 // Data Sheet
... • A flexible range of SFP and SFP+ transceivers including direct attach copper and active fiber cables, SR, LR, ER, and LRM ...
... • A flexible range of SFP and SFP+ transceivers including direct attach copper and active fiber cables, SR, LR, ER, and LRM ...
INTERNET CONNECTIONS How does data get from point A to point
... Data Communication can be established using analog or digital signal. Analog signal is a continuous wave pattern. The telephone system uses analog signals Digital signal consists of a series of 1s and 0s. HDTV uses digital signals. – Signal can be of any kind: Electric current, electromagnetic waves ...
... Data Communication can be established using analog or digital signal. Analog signal is a continuous wave pattern. The telephone system uses analog signals Digital signal consists of a series of 1s and 0s. HDTV uses digital signals. – Signal can be of any kind: Electric current, electromagnetic waves ...
Chapter 1 - William Stallings, Data and Computer Communications
... providing the required capacity, with acceptable reliability, at minimum cost ...
... providing the required capacity, with acceptable reliability, at minimum cost ...
Unit E - Home - KSU Faculty Member websites
... or a file broken into small, equal size pieces Contains ...
... or a file broken into small, equal size pieces Contains ...
Security and Privacy in Sensor Networks: Research Challenges
... We must secure entire networked system, not just an individual component Solutions must be robust/adapt to new threats as much as possible ...
... We must secure entire networked system, not just an individual component Solutions must be robust/adapt to new threats as much as possible ...
SCRAMNet+ - Curtiss-Wright Defense Solutions
... To utilize the replicated shared-memory concept, distributed processes map their global data structures into the dualport memory located on each SCRAMNet+ node. Any time an application process updates a data structure located in its local SCRAMNet+ memory, the address and data are immediately (and a ...
... To utilize the replicated shared-memory concept, distributed processes map their global data structures into the dualport memory located on each SCRAMNet+ node. Any time an application process updates a data structure located in its local SCRAMNet+ memory, the address and data are immediately (and a ...
r03-arpa - Computer Engineering
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
... • Implementing a functionality at a lower level should have minimum performance impact on the applications that do not use the functionality ...
PDF
... quality of service. (The solution of this general problem automatically solves the more restricted problem of supporting continuous-media applications in an integrated services network.) Providing users with a consistent and reliable quality of service has usually been studied from the perspectives ...
... quality of service. (The solution of this general problem automatically solves the more restricted problem of supporting continuous-media applications in an integrated services network.) Providing users with a consistent and reliable quality of service has usually been studied from the perspectives ...
1 - Oxford Schools | PowerSchool Learning
... 8. Which of the following terms describes the address used at the Network layer? A. Physical B. Logical C. MAC D. Host E. Hexadecimal 9. Which of the following is the binary representation of the decimal number 110? A. 10000011 B. 01101110 C. 01111101 D. 11110111 E. 11101101 10. How is data packaged ...
... 8. Which of the following terms describes the address used at the Network layer? A. Physical B. Logical C. MAC D. Host E. Hexadecimal 9. Which of the following is the binary representation of the decimal number 110? A. 10000011 B. 01101110 C. 01111101 D. 11110111 E. 11101101 10. How is data packaged ...
Introduction to Networks
... • On-demand time-division • Schedule link on a per-packet (limited-size block of data) basis • Packets from different sources interleaved on link • Buffer packets that are contending for the link • Buffer (queue) overflow is called congestion • FIFO or round-robin to make flow in a fair maner ...
... • On-demand time-division • Schedule link on a per-packet (limited-size block of data) basis • Packets from different sources interleaved on link • Buffer packets that are contending for the link • Buffer (queue) overflow is called congestion • FIFO or round-robin to make flow in a fair maner ...
Chapter 1 Introduction 1.1
... The term telecommunication means communication at a distance. The word data refers to information presented in whatever form is agreed upon by the parties creating and using the data. Data communications are the exchange of data between two devices via some form of transmission medium such as a wire ...
... The term telecommunication means communication at a distance. The word data refers to information presented in whatever form is agreed upon by the parties creating and using the data. Data communications are the exchange of data between two devices via some form of transmission medium such as a wire ...
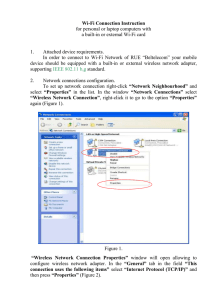
инструкция
... PLEASE NOTE: Should you choose connection to the wireless network “byfly WIFI” and the message “No or limited connectivity” is displayed in the window containing the list of available wireless network connections, or the authorization page fails to download when entering the necessary address in th ...
... PLEASE NOTE: Should you choose connection to the wireless network “byfly WIFI” and the message “No or limited connectivity” is displayed in the window containing the list of available wireless network connections, or the authorization page fails to download when entering the necessary address in th ...