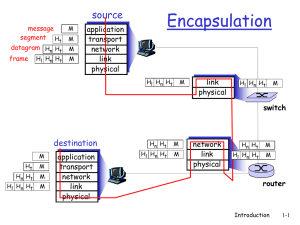
What is a Network?
... The Token Ring protocol was developed by IBM in the mid-1980s. The access method used involves tokenpassing. In Token Ring, the computers are connected so that the signal travels around the network from one computer to another in a logical ring. A single electronic token moves around the ring from o ...
... The Token Ring protocol was developed by IBM in the mid-1980s. The access method used involves tokenpassing. In Token Ring, the computers are connected so that the signal travels around the network from one computer to another in a logical ring. A single electronic token moves around the ring from o ...
Layer Number Layer Designation Function Responsibility Page
... electrical, mechanical, procedural, and functional requirements for activating, maintaining, and deactivating a physical link between end systems ...
... electrical, mechanical, procedural, and functional requirements for activating, maintaining, and deactivating a physical link between end systems ...
ch2
... if adapter receives frame with matching destination address, or with broadcast address (eg ARP packet), it passes data in frame to net-layer protocol otherwise, adapter discards frame ...
... if adapter receives frame with matching destination address, or with broadcast address (eg ARP packet), it passes data in frame to net-layer protocol otherwise, adapter discards frame ...
Network Management
... Switches may operate at one or more OSI layers, including physical, data link, network, or transport (i.e., end-to-end). A device that operates simultaneously at more than one of these layers is called a multilayer switch, although use of the term is diminishing.[citation needed] In switches inten ...
... Switches may operate at one or more OSI layers, including physical, data link, network, or transport (i.e., end-to-end). A device that operates simultaneously at more than one of these layers is called a multilayer switch, although use of the term is diminishing.[citation needed] In switches inten ...
NetworkPurposeTypesPackets
... A packet is a formatted unit of data carried by a packet mode computer network. Computer communications links that do not support packets, such as traditional point-to-point telecommunications links, simply transmit data as a series of bytes, characters, or bits alone. When data is formatted into pa ...
... A packet is a formatted unit of data carried by a packet mode computer network. Computer communications links that do not support packets, such as traditional point-to-point telecommunications links, simply transmit data as a series of bytes, characters, or bits alone. When data is formatted into pa ...
The network convergence: A Reality?
... The Network Convergence: A Reality? Emmanuel DUJARDIN, Orange – France Telecom Group ...
... The Network Convergence: A Reality? Emmanuel DUJARDIN, Orange – France Telecom Group ...
View File
... A site that wants to transmit information must wait until the token arrives When the site completes its round of message passing, it retransmits the token A token-passing scheme is used by some IBM and HP/Apollo ...
... A site that wants to transmit information must wait until the token arrives When the site completes its round of message passing, it retransmits the token A token-passing scheme is used by some IBM and HP/Apollo ...
Home Network Management
... my dad to configure it. People will demand the functionality that home networks can provide, but problems will ensue due to this complexity – mis-operation will be blamed on the network operator! Network operators need to be able to take proactive role in helping people to configure, manage and ...
... my dad to configure it. People will demand the functionality that home networks can provide, but problems will ensue due to this complexity – mis-operation will be blamed on the network operator! Network operators need to be able to take proactive role in helping people to configure, manage and ...
Defense - Northwestern Networks Group
... – Allows host attached to same switch to route only through switch – Allows inter-pod traffic to stay within pod – unused.PodNumber.switchnumber.Endhost ...
... – Allows host attached to same switch to route only through switch – Allows inter-pod traffic to stay within pod – unused.PodNumber.switchnumber.Endhost ...
Chapter 1 Data Communications and Networks Overview
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. —Application layer —Host to host or transport layer —Internet layer —Network access layer —Physical layer ...
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. —Application layer —Host to host or transport layer —Internet layer —Network access layer —Physical layer ...
Chapter 1 Data Communications and Networks Overview
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. —Application layer —Host to host or transport layer —Internet layer —Network access layer —Physical layer ...
... Research Project Agency (DARPA) for its packet switched network (ARPANET) • Used by the global Internet • No official model but a working one. —Application layer —Host to host or transport layer —Internet layer —Network access layer —Physical layer ...
Categories of Networks
... • packet switching systems have large overheads to compensate for errors • modern systems are more reliable • errors can be caught in end system • Frame Relay provides higher speeds • with most error control overhead ...
... • packet switching systems have large overheads to compensate for errors • modern systems are more reliable • errors can be caught in end system • Frame Relay provides higher speeds • with most error control overhead ...
Viasat Linkstar Modem
... Quality of Service (QoS) and TCP acceleration features, makes LinkStar more efficient and faster than other TDMA systems. The combination automatically increases the speed of the return channel to give you the throughput you need. ViaSat is always working to bring you the highest return channel data ...
... Quality of Service (QoS) and TCP acceleration features, makes LinkStar more efficient and faster than other TDMA systems. The combination automatically increases the speed of the return channel to give you the throughput you need. ViaSat is always working to bring you the highest return channel data ...
5.2 Sub Tactical Radio Network
... full access to the CB radio frequencies. Therefore some courtesy and patience may need to be made for other users of the system. Experience will determine the best means of dealing with such instances, eg moving to another channel or requesting other public users to do so. ...
... full access to the CB radio frequencies. Therefore some courtesy and patience may need to be made for other users of the system. Experience will determine the best means of dealing with such instances, eg moving to another channel or requesting other public users to do so. ...
pptx
... How to Compare Two Network Models? • We are interested in the relative behavior of • If we plot ...
... How to Compare Two Network Models? • We are interested in the relative behavior of • If we plot ...
What Advantages Does an Agile Network Bring (Issue
... Different services place different requirements on network quality. For example, the packet loss ratio of voice service should be smaller than 10-2 and that of High Definition (HD) video service should be smaller than 10-6. That is, voice quality degrades if one packet is lost among 100 packets, and ...
... Different services place different requirements on network quality. For example, the packet loss ratio of voice service should be smaller than 10-2 and that of High Definition (HD) video service should be smaller than 10-6. That is, voice quality degrades if one packet is lost among 100 packets, and ...
例外(exception)とは何か
... - Agreement about communication * formats of messages (syntax) * meanings of messages (semantics) * rules for data exchange and connection establishment/termination * procedures for handling problems Set of Protocols - A network includes a set of protocols to work together, called protocol suite/fam ...
... - Agreement about communication * formats of messages (syntax) * meanings of messages (semantics) * rules for data exchange and connection establishment/termination * procedures for handling problems Set of Protocols - A network includes a set of protocols to work together, called protocol suite/fam ...
PASS4TEST
... employees at all 37 branches. He wants to check the various security concerns for ensuring that business traffic is secured. He is also in under pressure to make this new feature a winning strategy for a company. Mark wants the employees to be free to troubleshoot their own wireless connections befo ...
... employees at all 37 branches. He wants to check the various security concerns for ensuring that business traffic is secured. He is also in under pressure to make this new feature a winning strategy for a company. Mark wants the employees to be free to troubleshoot their own wireless connections befo ...
Presentation - UWC Computer Science
... The database design structure uses the view-processor logical architecture [5] Database Server: ‘Network’ ‘Node’ Net-setting ...
... The database design structure uses the view-processor logical architecture [5] Database Server: ‘Network’ ‘Node’ Net-setting ...
anti bullying policy - Boskenwyn Primary School
... Do not introduce floppy disks, CDs, DVDs or ‘pen drives’ into the network without having them checked for viruses. Do not attempt to visit websites that might be considered inappropriate. (Such sites would include those relating to illegal activity. All sites visited leave evidence in the county net ...
... Do not introduce floppy disks, CDs, DVDs or ‘pen drives’ into the network without having them checked for viruses. Do not attempt to visit websites that might be considered inappropriate. (Such sites would include those relating to illegal activity. All sites visited leave evidence in the county net ...
TE Solutions
... – Enough resources are allocated to keep the risk of burstlevel overload at the output multiplexer within tolerable limits – Both short- and long-term correlations are important 28 ...
... – Enough resources are allocated to keep the risk of burstlevel overload at the output multiplexer within tolerable limits – Both short- and long-term correlations are important 28 ...
Security - Risk Assessment
... Evaluate vendor’s proposals and decide technology for pilots Pilot sites will be Gates/Computer Science and five sites within ITSS Perform a physical inventory of the closets for each pilot site Evaluate and upgrade the network backbone and core infrastructure Provide tools and training for voice an ...
... Evaluate vendor’s proposals and decide technology for pilots Pilot sites will be Gates/Computer Science and five sites within ITSS Perform a physical inventory of the closets for each pilot site Evaluate and upgrade the network backbone and core infrastructure Provide tools and training for voice an ...