PDF (Updated 1/18)
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
... Protocols at this level transmit data in a network representation that is independent of the representations used in individual computers, which may differ. Encryption is also performed in this layer, if required. At this level reliability and adaptation are performed, such as detection of failures ...
Week_Three_Network_ppt - Computing Sciences
... - Observe the acknowledgment (ACK) and frame retries after a missing ACK. ACK is called a control frame. Clients and access points use them to implement a retransmission mechanism ...
... - Observe the acknowledgment (ACK) and frame retries after a missing ACK. ACK is called a control frame. Clients and access points use them to implement a retransmission mechanism ...
Reverse Power Flow
... Low Carbon Network Fund Tier 2 Projects 2011 • FALCON (Western Power Distribution East Midlands) • Facilitate the installation of low carbon technologies by avoiding traditional reinforcement • Use of real time network data in inform network decisions • Development of a scenario investment model us ...
... Low Carbon Network Fund Tier 2 Projects 2011 • FALCON (Western Power Distribution East Midlands) • Facilitate the installation of low carbon technologies by avoiding traditional reinforcement • Use of real time network data in inform network decisions • Development of a scenario investment model us ...
Towards Wireless Overlay Network Architectures
... Encourage more interactive discussion, fewer and/or shorter talks Provide more context, clearly define terms, review related work Place read-ahead material on the Web before retreat Organize sessions according to topic and/or research area ...
... Encourage more interactive discussion, fewer and/or shorter talks Provide more context, clearly define terms, review related work Place read-ahead material on the Web before retreat Organize sessions according to topic and/or research area ...
Automotive, Jaspar contribution to tutorial
... Member companies from JASPAR will contribute the standardization works ...
... Member companies from JASPAR will contribute the standardization works ...
Port Scanning: Is it illegal
... can attack the computer via the port and exploit any vulnerabilities. A common tool used to port scan is “Nmap.” Nmap can hit ports with a full “three-way” handshake which are often logged, SYN scans (sends only a SYN packet and waits to receive an ACK packet), ...
... can attack the computer via the port and exploit any vulnerabilities. A common tool used to port scan is “Nmap.” Nmap can hit ports with a full “three-way” handshake which are often logged, SYN scans (sends only a SYN packet and waits to receive an ACK packet), ...
Bishop: Chapter 26 Network Security
... Router establishes connection to client When connected establish with server If the client never sends the ACK (before timing out), then the initial SYN packet is part of an attack handshake. The target never sees the illegitimate SYN packets. The router uses short time-outs to protect itself. ...
... Router establishes connection to client When connected establish with server If the client never sends the ACK (before timing out), then the initial SYN packet is part of an attack handshake. The target never sees the illegitimate SYN packets. The router uses short time-outs to protect itself. ...
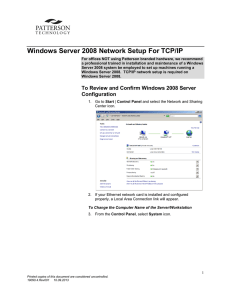
Windows Server 2008 Network Setup For TCP/IP
... 8. Select OK. You will be prompted to restart your computer. 9. Once you have restarted your computer, you can check your network connection by going to Network and Sharing Center and opening up the network. Any and all other computers in the same workgroup will be listed. ...
... 8. Select OK. You will be prompted to restart your computer. 9. Once you have restarted your computer, you can check your network connection by going to Network and Sharing Center and opening up the network. Any and all other computers in the same workgroup will be listed. ...
Designing Technomadic Systems
... option—RS-232 or RS-485 console ports. The latter, with software-controlled line driver, is optimized for building a multidrop network in which the Hub always transmits to all nodes on one pair, with only one node at a time allowed to transmit on the other. There are various ways to go about this — ...
... option—RS-232 or RS-485 console ports. The latter, with software-controlled line driver, is optimized for building a multidrop network in which the Hub always transmits to all nodes on one pair, with only one node at a time allowed to transmit on the other. There are various ways to go about this — ...
Distributed Systems
... currently being transmitted over that link. If two or more sites begin transmitting at exactly the same time, then they will register a CD and will stop transmitting When the system is very busy, many collisions may occur, and thus performance may be degraded ...
... currently being transmitted over that link. If two or more sites begin transmitting at exactly the same time, then they will register a CD and will stop transmitting When the system is very busy, many collisions may occur, and thus performance may be degraded ...
Lec_1: Syllabus
... Error detection: Errors caused by signal attenuation, noise. Receiver detects presence of errors: • Signals sender for retransmission or drops frame ...
... Error detection: Errors caused by signal attenuation, noise. Receiver detects presence of errors: • Signals sender for retransmission or drops frame ...
The Future of Computing: Challenges and Opportunities
... CS 450/650 Fundamentals of Integrated Computer Security ...
... CS 450/650 Fundamentals of Integrated Computer Security ...
4.new-mj-hawaii
... Production use for cases where shared IP service is not acceptable but also dedicated 10G waves not needed ...
... Production use for cases where shared IP service is not acceptable but also dedicated 10G waves not needed ...
slides - network systems lab @ sfu
... Reliable data transfer: principles rdt_send(): called from above, (e.g., by app.). Passed data to deliver to receiver upper layer ...
... Reliable data transfer: principles rdt_send(): called from above, (e.g., by app.). Passed data to deliver to receiver upper layer ...
Self-Organizing Hierarchical Neural Network
... •This work attempts to build a self-organized hierarchical structure with correlation based sparse connectivity. •Self-organizing networks, hierarchical or otherwise, have been researched for many years, and have applications in such areas as: surveillance, traffic monitoring, flight control, rescue ...
... •This work attempts to build a self-organized hierarchical structure with correlation based sparse connectivity. •Self-organizing networks, hierarchical or otherwise, have been researched for many years, and have applications in such areas as: surveillance, traffic monitoring, flight control, rescue ...
Urban Area Securtity Initiative
... overlay additions to the current RF infrastructure: IP network backbone, IP network components and Mobile Communication Units Allows interoperability between disparate radio system technologies Provides flexibility and scalability Achieves functionality in most areas of state population with fixed c ...
... overlay additions to the current RF infrastructure: IP network backbone, IP network components and Mobile Communication Units Allows interoperability between disparate radio system technologies Provides flexibility and scalability Achieves functionality in most areas of state population with fixed c ...
Chapter 3 - Network Protocols
... format of how data frames will be sent over the physical medium, so that two network cards of the same network type will actually be able to communicate. These frames are sent to physical level to be turned into the electronic signals that are sent over a specific network. (layer 2 uses the services ...
... format of how data frames will be sent over the physical medium, so that two network cards of the same network type will actually be able to communicate. These frames are sent to physical level to be turned into the electronic signals that are sent over a specific network. (layer 2 uses the services ...
man-in-the-middle - Personal.kent.edu
... Linear Checksum • Encrypted CRC-32 used as integrity check • Fine for random errors, but not deliberate ones • CRC is linear • Can maliciously flip bits in the packet • Can replay modified packets! ...
... Linear Checksum • Encrypted CRC-32 used as integrity check • Fine for random errors, but not deliberate ones • CRC is linear • Can maliciously flip bits in the packet • Can replay modified packets! ...
Ch 9 Ques
... 28. SONET: A) is a standard for optical transmission that currently operates at Terabit per second speeds B) is very similar to the ITU-T standard, synchronous digital hierarchy C) uses inverse multiplexing above the OC-1 level D) refers to Sprint Overall Network E) is not currently available, even ...
... 28. SONET: A) is a standard for optical transmission that currently operates at Terabit per second speeds B) is very similar to the ITU-T standard, synchronous digital hierarchy C) uses inverse multiplexing above the OC-1 level D) refers to Sprint Overall Network E) is not currently available, even ...
Part I: Introduction
... Special network components responsible for “moving” packets across the network from source to destination. Network hosts, workstations, etc. they generally represent the source and sink (destination) of data traffic (packets) We can recursively build large networks by ...
... Special network components responsible for “moving” packets across the network from source to destination. Network hosts, workstations, etc. they generally represent the source and sink (destination) of data traffic (packets) We can recursively build large networks by ...
CACHEBOX enables Mexican firm to switch to low-cost
... sites would now directly connect to the internet, and no longer pass through the cache at our HQ. We were at risk of losing control of a critical aspect of network administration,” explained IT Infrastructure Manager at Grupo Alcione, Juan Hernandez. “We knew we had to maintain that control. Among o ...
... sites would now directly connect to the internet, and no longer pass through the cache at our HQ. We were at risk of losing control of a critical aspect of network administration,” explained IT Infrastructure Manager at Grupo Alcione, Juan Hernandez. “We knew we had to maintain that control. Among o ...
1648 Discovery 4 - Designing and Supporting Computer Network
... equipment and protocol needs, and creating a network topology which addresses the needs of the customer. Areas of study include network design concepts, gathering network requirements, characterizing the existing network, identifying application impacts on network designs, creating the network desig ...
... equipment and protocol needs, and creating a network topology which addresses the needs of the customer. Areas of study include network design concepts, gathering network requirements, characterizing the existing network, identifying application impacts on network designs, creating the network desig ...
Installing Chart Templates
... (such as speedtest.net) that measure TCP throughput on a long-running flow, and round-trip latency on an unloaded ...
... (such as speedtest.net) that measure TCP throughput on a long-running flow, and round-trip latency on an unloaded ...
PPTX
... "The function in question can completely and correctly be implemented only with the knowledge and help of the application standing at the end points of the communication system. Therefore, providing that questioned function as a feature of the communication system itself is not possible. (Sometimes ...
... "The function in question can completely and correctly be implemented only with the knowledge and help of the application standing at the end points of the communication system. Therefore, providing that questioned function as a feature of the communication system itself is not possible. (Sometimes ...
Edco FAS-TEL and FAS-31XT
... The Edco FAS-TEL and Edco FAS-31XT are single pair telephone or data line protectors that implement advanced two-stage hybrid design. These units address over-voltage transients with silicon breakover devices, while sneak and fault currents are mitigated with PTC technology which consists of solid s ...
... The Edco FAS-TEL and Edco FAS-31XT are single pair telephone or data line protectors that implement advanced two-stage hybrid design. These units address over-voltage transients with silicon breakover devices, while sneak and fault currents are mitigated with PTC technology which consists of solid s ...