AtlasTier3Virtualization - Indico
... • Design a system to be flexible and simple to setup (1 person < 1 week) • Simple to operate - < 0.25 FTE to maintain • Scalable with Data volumes • Fast - Process 1 TB of data over night • Relatively inexpensive • Run only the needed services/process • Devote most resources to CPU’s and Disk ...
... • Design a system to be flexible and simple to setup (1 person < 1 week) • Simple to operate - < 0.25 FTE to maintain • Scalable with Data volumes • Fast - Process 1 TB of data over night • Relatively inexpensive • Run only the needed services/process • Devote most resources to CPU’s and Disk ...
Shoregear Data Sheet
... ShoreGear-E1 provides an E1 interface using Euro-ISDN PRI signaling for international applications. All the ShoreGear switches include two LAN ports for redundant network connections. ...
... ShoreGear-E1 provides an E1 interface using Euro-ISDN PRI signaling for international applications. All the ShoreGear switches include two LAN ports for redundant network connections. ...
Introduction to Queue theory
... Packet length, P, is the length of a packet in bits. Link length, L, is the length of a link in meters. Data rate, R, is the rate at which bits can be sent, in bits/second, or b/s.1 Propagation delay, PROP, is the time for one bit to travel along a link of length, L. PROP = L/c. Transmission time, T ...
... Packet length, P, is the length of a packet in bits. Link length, L, is the length of a link in meters. Data rate, R, is the rate at which bits can be sent, in bits/second, or b/s.1 Propagation delay, PROP, is the time for one bit to travel along a link of length, L. PROP = L/c. Transmission time, T ...
Designing Converged Networks
... • VLANs provide security and traffic segmentation and are supported by Network Cards, switches, wireless access points, routers and security appliances • Use VLANs to segment network in logical groups or business functions • VLANs can be mapped to IP Subnets and are terminated by routers/Layer 3 swi ...
... • VLANs provide security and traffic segmentation and are supported by Network Cards, switches, wireless access points, routers and security appliances • Use VLANs to segment network in logical groups or business functions • VLANs can be mapped to IP Subnets and are terminated by routers/Layer 3 swi ...
network layer model
... frequencies to transmit information between individual computers. The individual computers do not communicate directly with each other, but instead through a wireless network hub or router. Wi-Fi (wireless fidelity), also called IEEE 802.11b standard, the current popular standard for wireless ne ...
... frequencies to transmit information between individual computers. The individual computers do not communicate directly with each other, but instead through a wireless network hub or router. Wi-Fi (wireless fidelity), also called IEEE 802.11b standard, the current popular standard for wireless ne ...
File: IIB ACCEPTABLE USE POLICY for Internet/Online
... Intellectual Freedom. The HCCA Network must be a free and open forum for expression, including viewpoints that are strange, unorthodox, or unpopular. The network administrators will place no official sanctions upon the expression of personal opinion on the network. However, the poster of an opinion ...
... Intellectual Freedom. The HCCA Network must be a free and open forum for expression, including viewpoints that are strange, unorthodox, or unpopular. The network administrators will place no official sanctions upon the expression of personal opinion on the network. However, the poster of an opinion ...
Presentation16
... operating normally & the establishment and management of open channels is managed separately by a further protocol (known as CSMA/CD - more on this later) all channels are “open” for communication packets are numbered, so they can be correctly assembled at the receiving end ...
... operating normally & the establishment and management of open channels is managed separately by a further protocol (known as CSMA/CD - more on this later) all channels are “open” for communication packets are numbered, so they can be correctly assembled at the receiving end ...
Network Devices - courses.psu.edu
... MAC address is known now. Hand packet down to Data Link Layer. A frame is generated. The frame is handed down to the Physical Layer to be put on the medium. Every device on the collision domain receives the bits. They run CRC and check FCS field. The interface E0 matches the FCS field. Look what typ ...
... MAC address is known now. Hand packet down to Data Link Layer. A frame is generated. The frame is handed down to the Physical Layer to be put on the medium. Every device on the collision domain receives the bits. They run CRC and check FCS field. The interface E0 matches the FCS field. Look what typ ...
Evaluating a coherent method for source location reconstruction on
... The MonteCarlo We have used BNS signals, with m1 = m2 = 1.45 M ! , and a fmin = 30Hz. With this choice, the signal duration is about 52 s. For each sky location, signals are injected every 100s, at a distance of 1Mpc, with polarization randomly distributed in [" ! , ! ] , and inclination i uniforml ...
... The MonteCarlo We have used BNS signals, with m1 = m2 = 1.45 M ! , and a fmin = 30Hz. With this choice, the signal duration is about 52 s. For each sky location, signals are injected every 100s, at a distance of 1Mpc, with polarization randomly distributed in [" ! , ! ] , and inclination i uniforml ...
Network protocols
... – Server operating system: When the OS installed on a computer is designed mainly to share network resources and provide other network services – Server computer: When a computer’s primary role in the network is to give client computers access to network resources and services – Server software: Res ...
... – Server operating system: When the OS installed on a computer is designed mainly to share network resources and provide other network services – Server computer: When a computer’s primary role in the network is to give client computers access to network resources and services – Server software: Res ...
WDRM, 2nd edition - Falcon Electronics
... that enables cordless data transfer between Bluetooth equipped devices at short range. bounded medium A term used to describe cabling or waveguide. Contrast with unbounded medium. bridge 1. A Layer 2 networking device used to connect separate local area network (LAN) collision domains (or network se ...
... that enables cordless data transfer between Bluetooth equipped devices at short range. bounded medium A term used to describe cabling or waveguide. Contrast with unbounded medium. bridge 1. A Layer 2 networking device used to connect separate local area network (LAN) collision domains (or network se ...
Controller
... Any tunnel encap or rewrites needed? Any other external software/DBs to use (radius, directory)? ...
... Any tunnel encap or rewrites needed? Any other external software/DBs to use (radius, directory)? ...
HWBA54G Manual
... If you select invisible, this AP can not be detected by wireless sniffers; which means all the wireless clients can not associated to this AP unless they know/use the SSID. You can select different wireless networking hardware (PHY) to meet your wireless environment or for optimal performance. You c ...
... If you select invisible, this AP can not be detected by wireless sniffers; which means all the wireless clients can not associated to this AP unless they know/use the SSID. You can select different wireless networking hardware (PHY) to meet your wireless environment or for optimal performance. You c ...
last draft
... reserved media bandwidth, and guaranteed required QoS. Most IP flows depend on TCP, a protocol to provide reliable, ordered, and error-checked delivery of a stream of octets between applications running on hosts. TCP is resilient against packet loss through retransmission of unacknowledged packets, ...
... reserved media bandwidth, and guaranteed required QoS. Most IP flows depend on TCP, a protocol to provide reliable, ordered, and error-checked delivery of a stream of octets between applications running on hosts. TCP is resilient against packet loss through retransmission of unacknowledged packets, ...
pptx - Department of Computer Science
... host, However,Switch, HyperFlow can handle far larger number of for thousands link changes events. of hosts During spikes inconsistency window is not bounded. ...
... host, However,Switch, HyperFlow can handle far larger number of for thousands link changes events. of hosts During spikes inconsistency window is not bounded. ...
NetEnforcer® AC-3000 Series
... Allot Communications Ltd. (NASDAQ: ALLT) is a leading provider of intelligent IP service optimization solutions for fixed and mobile broadband operators and large enterprises. Allot’s rich portfolio of solutions leverages dynamic actionable recognition technology (DART) to transform broadband pipes i ...
... Allot Communications Ltd. (NASDAQ: ALLT) is a leading provider of intelligent IP service optimization solutions for fixed and mobile broadband operators and large enterprises. Allot’s rich portfolio of solutions leverages dynamic actionable recognition technology (DART) to transform broadband pipes i ...
Wireless Expands M D to More of the Plant
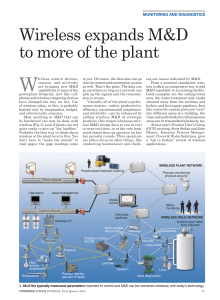
... and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an antenna which transmits a signal through an industrial-grade point accessing ...
... and the solutions, or what you actually do with the monitored points. The links and infrastructure (Fig 2) are industrial, ruggedized versions of similar equipment you use at home or in the office. Each field device has an antenna which transmits a signal through an industrial-grade point accessing ...
Unit 2–Computer Network Fundamentals
... Ethernet operates at the Network Access layer in the TCP/IP model. It uses the star networking topology, which has proved more robust than either the bus or ring topologies. At the physical layer, Ethernet uses unshielded twisted pair cabling primarily. The current standard for UTP is Category 5 Enh ...
... Ethernet operates at the Network Access layer in the TCP/IP model. It uses the star networking topology, which has proved more robust than either the bus or ring topologies. At the physical layer, Ethernet uses unshielded twisted pair cabling primarily. The current standard for UTP is Category 5 Enh ...
ppt - Computer Science & Engineering
... anticipated that each of 12 separate stations will have a camera installed by the end of the year. These cameras currently are set to transmit images of pre-set views once per hour over a 10Mbps field IP network. The utility of these cameras could also be leveraged by implementing software control s ...
... anticipated that each of 12 separate stations will have a camera installed by the end of the year. These cameras currently are set to transmit images of pre-set views once per hour over a 10Mbps field IP network. The utility of these cameras could also be leveraged by implementing software control s ...
Chapter 2 Networking Standards and the OSI Model
... • Data Link layer protocols organize data they receive from the Network layer into frames that contain error checking routines and can then be transmitted by the Physical layer • Physical layer protocols generate and detect voltage to transmit and receive signals carrying data over a network medium ...
... • Data Link layer protocols organize data they receive from the Network layer into frames that contain error checking routines and can then be transmitted by the Physical layer • Physical layer protocols generate and detect voltage to transmit and receive signals carrying data over a network medium ...
ppt for Chapters 1-5 - Computer and Information Sciences
... ►” An (almost) arbitrary number of Ethernets can be connected together with bridges” ►”A set of bridged segments acts like a single Ethernet” (“transparent”) ► “Most bridges . . . Make intelligent decisions about which frames to forward” -- No “runts” ► Special case when bridge first powered up -- ...
... ►” An (almost) arbitrary number of Ethernets can be connected together with bridges” ►”A set of bridged segments acts like a single Ethernet” (“transparent”) ► “Most bridges . . . Make intelligent decisions about which frames to forward” -- No “runts” ► Special case when bridge first powered up -- ...
City of Southlake
... Embedded web and SNMP-based network management agents make it easy to monitor BridgeWave’s radios from a standard management console, eliminating the need for additional software, servers and training. With phase one completed, planning started for the next stage of the rollout. Phase two is focused ...
... Embedded web and SNMP-based network management agents make it easy to monitor BridgeWave’s radios from a standard management console, eliminating the need for additional software, servers and training. With phase one completed, planning started for the next stage of the rollout. Phase two is focused ...