BiPAC 8200M BiPAC 8200N
... 1. None of the LEDs are on when you turn on the router. Check the connection between the adaptor and the router. If the error persists, you may have a hardware problem. In this case you should contact technical support. 2. Can’t ping any PCs on the LAN. Check the Ethernet LEDs on the front panel. Th ...
... 1. None of the LEDs are on when you turn on the router. Check the connection between the adaptor and the router. If the error persists, you may have a hardware problem. In this case you should contact technical support. 2. Can’t ping any PCs on the LAN. Check the Ethernet LEDs on the front panel. Th ...
Network
... connected to a central hub. Easy to lay out and modify. Most costly (cabling). Failure of hub can cause network failure. Ring: Messages move in one ...
... connected to a central hub. Easy to lay out and modify. Most costly (cabling). Failure of hub can cause network failure. Ring: Messages move in one ...
Protocols and Interaction Models for Web Services
... Sender’s window size can’t exceed this or receiver will have buffer overflow and packets will be lost Network congestion causes some packets to be dropped at some router or to not be ack’d before a timeout occurs Sender then reduces window size to Wc , which reduces its transmission rate and atte ...
... Sender’s window size can’t exceed this or receiver will have buffer overflow and packets will be lost Network congestion causes some packets to be dropped at some router or to not be ack’d before a timeout occurs Sender then reduces window size to Wc , which reduces its transmission rate and atte ...
www.cs.hofstra.edu
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
Chapter 15 Local Area Network Overview
... • Now many types of devices for interconnecting LANs • Beyond bridges and routers • Layer 2 switches • Layer 3 switches ...
... • Now many types of devices for interconnecting LANs • Beyond bridges and routers • Layer 2 switches • Layer 3 switches ...
answer-sheet-031_heather-mclellan_isf-7765
... 802.11b - IEEE expanded on the original 802.11 to 802.11b. This supports bandwidth up 10 11mbps, comparable to Ethernet. It still uses the frequency of 2.4GHz. This standard can be interfered from microwaves, ovens, cordless phones and other applications using the same GHz. 802.11a- IEEE created a s ...
... 802.11b - IEEE expanded on the original 802.11 to 802.11b. This supports bandwidth up 10 11mbps, comparable to Ethernet. It still uses the frequency of 2.4GHz. This standard can be interfered from microwaves, ovens, cordless phones and other applications using the same GHz. 802.11a- IEEE created a s ...
(CCNA) 7.Data Link Layer
... Duration/ID field - Depending on the type of frame, represents either the time, in microseconds, required to transmit the frame or an association identity (AID) for the station that transmitted the frame Destination Address (DA) field - MAC address of the final destination node in the network ...
... Duration/ID field - Depending on the type of frame, represents either the time, in microseconds, required to transmit the frame or an association identity (AID) for the station that transmitted the frame Destination Address (DA) field - MAC address of the final destination node in the network ...
William Stallings Data and Computer Communications 7
... • Now many types of devices for interconnecting LANs • Beyond bridges and routers • Layer 2 switches • Layer 3 switches ...
... • Now many types of devices for interconnecting LANs • Beyond bridges and routers • Layer 2 switches • Layer 3 switches ...
No - Trinity College Dublin
... Demonstrates that any logical function can be implemented by some network of neurons. •There are rules governing the excitatory and inhibitory pathways. •All computations are carried out in discrete time intervals. •Each neuron obeys a simple form of a linear threshold law: Neuron fires whenever at ...
... Demonstrates that any logical function can be implemented by some network of neurons. •There are rules governing the excitatory and inhibitory pathways. •All computations are carried out in discrete time intervals. •Each neuron obeys a simple form of a linear threshold law: Neuron fires whenever at ...
OPTICAL ACCESS NETWORK
... • 3. The Media Gateway handles the voice media data payload (the digitized samples of speech during conversation). In the future, video data will also need to be supported. In the current model, the Media Gateway must support connectivity to a TDM bus carrying voice media data to the Telco switch si ...
... • 3. The Media Gateway handles the voice media data payload (the digitized samples of speech during conversation). In the future, video data will also need to be supported. In the current model, the Media Gateway must support connectivity to a TDM bus carrying voice media data to the Telco switch si ...
Document
... cost to each directly attached neighbor v of x: c(x,v) the distance vector containing the estimate of the cost to all destinations, y, in N: Dx = [Dx(y): y є N ] the distance vector of each neighbor v of x: Dv = ...
... cost to each directly attached neighbor v of x: c(x,v) the distance vector containing the estimate of the cost to all destinations, y, in N: Dx = [Dx(y): y є N ] the distance vector of each neighbor v of x: Dv = ...
Ch11
... • When initialized, router determines link cost on each interface • Router advertises these costs to all other routers in topology • Router monitors its costs — When changes occurs, costs are re-advertised ...
... • When initialized, router determines link cost on each interface • Router advertises these costs to all other routers in topology • Router monitors its costs — When changes occurs, costs are re-advertised ...
PowerPoint
... Networks – super- and subnetting Inversely, if two networks can be “joined” together under the same netmask, which encompasses both networks, then we are supernetting. ...
... Networks – super- and subnetting Inversely, if two networks can be “joined” together under the same netmask, which encompasses both networks, then we are supernetting. ...
Network Layer (4) - FSU Computer Science Department
... Virtual Circuit • Circuit means a path between the source and the destination. • Real circuit switching has a physical path set up between the source and the destination, like telephone network – When you dial, a request is sent to the network, network finds if there are free links on the path and ...
... Virtual Circuit • Circuit means a path between the source and the destination. • Real circuit switching has a physical path set up between the source and the destination, like telephone network – When you dial, a request is sent to the network, network finds if there are free links on the path and ...
Business to Business Wireless E
... M-Commerce has to have several key components in order to work. One must have a device, capable of sending information. This can be as simple as a modern cell phone, or a PDA such as a Palm Pilot, or the BlackBerry device. It can be as advanced as a laptop with a wireless modem attached to it, or a ...
... M-Commerce has to have several key components in order to work. One must have a device, capable of sending information. This can be as simple as a modern cell phone, or a PDA such as a Palm Pilot, or the BlackBerry device. It can be as advanced as a laptop with a wireless modem attached to it, or a ...
M6 Lecture1
... frames between devices. Is responsible for flow regulation, error detection and correction, framing of bits for transmission. The network frame is made up of checksum, destination MAC address, source address, and the data. The largest frame size is the maximum transmission Unit (MTU). Consists of tw ...
... frames between devices. Is responsible for flow regulation, error detection and correction, framing of bits for transmission. The network frame is made up of checksum, destination MAC address, source address, and the data. The largest frame size is the maximum transmission Unit (MTU). Consists of tw ...
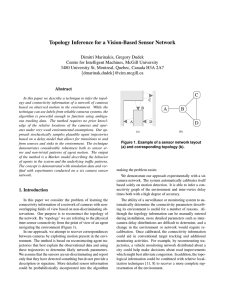
Topology Inference for a Vision-Based Sensor Network
... Motion in the environment can be exploited to calibrate a network of cameras. Most efforts using this technique have focused on sensor self-localization. Stein [13], for example, considered recovering a rough planar alignment of the location and orientation of the individual cameras. Using a least-m ...
... Motion in the environment can be exploited to calibrate a network of cameras. Most efforts using this technique have focused on sensor self-localization. Stein [13], for example, considered recovering a rough planar alignment of the location and orientation of the individual cameras. Using a least-m ...
Stream Over P2P Network
... opposed to all clients accessing the same central server, so as to avoid bottleneck near that server. Content types include web objects, download-able objects (media files, software, documents), applications, real time media streams, and other components of internet delivery (DNS, routes, and databa ...
... opposed to all clients accessing the same central server, so as to avoid bottleneck near that server. Content types include web objects, download-able objects (media files, software, documents), applications, real time media streams, and other components of internet delivery (DNS, routes, and databa ...
Introduction to Computer Networks
... Sequence of A & B packets does not have fixed pattern, shared on demand statistical multiplexing. TDM: each host gets same slot in revolving TDM frame. Introduction ...
... Sequence of A & B packets does not have fixed pattern, shared on demand statistical multiplexing. TDM: each host gets same slot in revolving TDM frame. Introduction ...
INPUT DOCUMENT: Response to Report of the 6th FGNGN meeting
... 7.1 Isolation Legacy networks, such as the Internet, enable users to exploit multiple network services over a shared physical infrastructure, so a service may be affected by other coexisting network services. As a consequence, this can cause security problems. Network virtualization guarantees indep ...
... 7.1 Isolation Legacy networks, such as the Internet, enable users to exploit multiple network services over a shared physical infrastructure, so a service may be affected by other coexisting network services. As a consequence, this can cause security problems. Network virtualization guarantees indep ...
Lesson 6-2: History of Internetworking
... industry and communications satellites began to transfer telephone and television signals between continents. New technologies and products allowed mainframes to perform unrelated tasks for users from multiple terminals. A terminal looks like a personal computer, but it can not do anything unless it ...
... industry and communications satellites began to transfer telephone and television signals between continents. New technologies and products allowed mainframes to perform unrelated tasks for users from multiple terminals. A terminal looks like a personal computer, but it can not do anything unless it ...
Network Scavenger Hunt
... look at far left column). Routers connect many networks together. Example: Temple Network which consists of many LANS (Local Area Networks) like the LAN at which you are currently doing this lab. ____________________________________________________________________________ 2.. When an asterisk (*) ap ...
... look at far left column). Routers connect many networks together. Example: Temple Network which consists of many LANS (Local Area Networks) like the LAN at which you are currently doing this lab. ____________________________________________________________________________ 2.. When an asterisk (*) ap ...
FPGA Research Design Platform Fuels Network Advances
... blocks of IP that may each use varied types of communication interfaces (streaming, byte-addressable and so on), with varied bandwidth and latency requirements. In its essence, OpenCPI is a highly configurable framework that provides the critical communication “glue” between IP that is needed to rea ...
... blocks of IP that may each use varied types of communication interfaces (streaming, byte-addressable and so on), with varied bandwidth and latency requirements. In its essence, OpenCPI is a highly configurable framework that provides the critical communication “glue” between IP that is needed to rea ...
Document
... • Devices connected to or installed in network nodes • Enable nodes to communicate with each other and access the network • Desktop and notebook computers sold today contain network adaptors – Network interface card (NIC) ...
... • Devices connected to or installed in network nodes • Enable nodes to communicate with each other and access the network • Desktop and notebook computers sold today contain network adaptors – Network interface card (NIC) ...