Full Presentation
... packet switched network will enable the ICT sector to be more innovative. • Currently, many countries started to invest heavily in the ICT sector knowing that it will drive the other entities into massive ...
... packet switched network will enable the ICT sector to be more innovative. • Currently, many countries started to invest heavily in the ICT sector knowing that it will drive the other entities into massive ...
Calculating VLSM Subnets
... address and the broadcast address for each subnet are shown in the corners of each box. Remember that this diagram will differ if you start to calculate the subnets that require the fewest number of hosts first. The best solution is to start with the subnets with the largest number of hosts first, a ...
... address and the broadcast address for each subnet are shown in the corners of each box. Remember that this diagram will differ if you start to calculate the subnets that require the fewest number of hosts first. The best solution is to start with the subnets with the largest number of hosts first, a ...
Slides - Sigmobile
... Ability of XPRESS to exploit multiple paths One flow between extreme nodes XPRESS allowed to use every link available 802.11 uses the shortest ETX path ...
... Ability of XPRESS to exploit multiple paths One flow between extreme nodes XPRESS allowed to use every link available 802.11 uses the shortest ETX path ...
S_V07 - Raadio- ja sidetehnika instituut
... • Ignore sample for segment that has been retransmitted ...
... • Ignore sample for segment that has been retransmitted ...
PAC 530 Output Controller
... Controllers, power supplies, input, output and door controller modules are located in close proximity to the access device. Advantages of this approach includes a reduction of cable quantities required. The door or input/output controller is generally installed in a locked, tamper switched enclosure ...
... Controllers, power supplies, input, output and door controller modules are located in close proximity to the access device. Advantages of this approach includes a reduction of cable quantities required. The door or input/output controller is generally installed in a locked, tamper switched enclosure ...
Networking Components and Devices
... As with a hub, computers connect to a switch via a length of twisted-pair cable. Multiple switches are often interconnected to create larger networks. Despite their similarity in appearance and their identical physical connections to computers, switches offer significant operational advantages over ...
... As with a hub, computers connect to a switch via a length of twisted-pair cable. Multiple switches are often interconnected to create larger networks. Despite their similarity in appearance and their identical physical connections to computers, switches offer significant operational advantages over ...
ppt
... Q: How to provide circuit-like behavior? bandwidth guarantees needed for audio/video apps still an unsolved problem (chapter 6) ...
... Q: How to provide circuit-like behavior? bandwidth guarantees needed for audio/video apps still an unsolved problem (chapter 6) ...
Mobile Number Portability in India
... MNP-STP puts RN before B-party number in IDP message, so that IN can do proper charging on basis of RN. If IN (SCP) responds to MSC (SSF) over CONNECT message same B-number with RN can reach MSC and MSC can route call properly on basis of RN. MSC doesn’t need to do NPDB query again for routing. S ...
... MNP-STP puts RN before B-party number in IDP message, so that IN can do proper charging on basis of RN. If IN (SCP) responds to MSC (SSF) over CONNECT message same B-number with RN can reach MSC and MSC can route call properly on basis of RN. MSC doesn’t need to do NPDB query again for routing. S ...
SAN Consolidation white paper
... disaster recovery plan, organizations mirror storage resources from one data center to another remote data center, where it can serve as a hot standby in the event of an outage. Traditional physical SCSI layers can support links only a few meters in length, which is not enough to ensure continued op ...
... disaster recovery plan, organizations mirror storage resources from one data center to another remote data center, where it can serve as a hot standby in the event of an outage. Traditional physical SCSI layers can support links only a few meters in length, which is not enough to ensure continued op ...
Impact of Sensor Networks on Future InterNetDesign
... • Today, we use a wide range of ad hoc, application specific techniques in the SensorNet patch – Zillion different low-power MACs – Many link-specific, app-specific multihop routing protocols – Epidemic dissemination, directed diffusion, synopsis diffusion, … – All sorts of communication scheduling ...
... • Today, we use a wide range of ad hoc, application specific techniques in the SensorNet patch – Zillion different low-power MACs – Many link-specific, app-specific multihop routing protocols – Epidemic dissemination, directed diffusion, synopsis diffusion, … – All sorts of communication scheduling ...
speed - Rutgers ECE
... Both DIMRO and DIMRO-GS algorithms offer service differentiation, i.e., they provide QoS at the application layer without IP-layer support ...
... Both DIMRO and DIMRO-GS algorithms offer service differentiation, i.e., they provide QoS at the application layer without IP-layer support ...
Cray® XC™ Series Interconnect and Network Technology
... Developing both high-end, performance-optimized supercomputers and commodity-focused cluster computing systems, Cray has depth and breadth of experience when it comes to understanding the benefits of different interconnects and networks for achieving different goals. Rather than focus solely on indi ...
... Developing both high-end, performance-optimized supercomputers and commodity-focused cluster computing systems, Cray has depth and breadth of experience when it comes to understanding the benefits of different interconnects and networks for achieving different goals. Rather than focus solely on indi ...
990111-CANS-DVH~1
... Established in parallel with Internet2 multi-agency research and development (R&D) program to develop, test, and demonstrate advanced networking technologies and applications via testbeds that are 100 to 1,000 times faster end-to-end than today's Internet ...
... Established in parallel with Internet2 multi-agency research and development (R&D) program to develop, test, and demonstrate advanced networking technologies and applications via testbeds that are 100 to 1,000 times faster end-to-end than today's Internet ...
Document
... Link layer can have two types of technologies; • Point to point link like PPP where there are only 2 nodes. • Broadcast link like Ethernet when there are more than 2 nodes. Univ. of Tehran Introduction to computer Network ...
... Link layer can have two types of technologies; • Point to point link like PPP where there are only 2 nodes. • Broadcast link like Ethernet when there are more than 2 nodes. Univ. of Tehran Introduction to computer Network ...
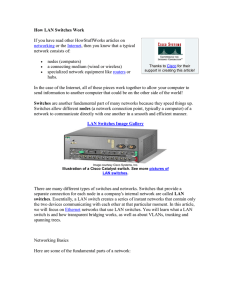
How LAN Switches Work
... Switching allows a network to maintain full-duplex Ethernet. Before switching, Ethernet was half-duplex, which means that data could be transmitted in only one direction at a time. In a fully switched network, each node communicates only with the switch, not directly with other nodes. Information ca ...
... Switching allows a network to maintain full-duplex Ethernet. Before switching, Ethernet was half-duplex, which means that data could be transmitted in only one direction at a time. In a fully switched network, each node communicates only with the switch, not directly with other nodes. Information ca ...
Atom and Molecules
... Finding other agents to buy and sell products • Mark up usually ranges from 20% to ...
... Finding other agents to buy and sell products • Mark up usually ranges from 20% to ...
ch02
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
lecture1424803314
... supporting communication among host computers using the Internet protocols. These protocols include the Internet Protocol (IP), the Internet Control Message Protocol (ICMP), the Internet Group Management Protocol (IGMP), and a variety transport and application protocols that depend upon them. All In ...
... supporting communication among host computers using the Internet protocols. These protocols include the Internet Protocol (IP), the Internet Control Message Protocol (ICMP), the Internet Group Management Protocol (IGMP), and a variety transport and application protocols that depend upon them. All In ...
Part I: Introduction
... Network service model Q: What service model for “channel” transporting packets from sender to receiver? guaranteed bandwidth? preservation of inter-packet ...
... Network service model Q: What service model for “channel” transporting packets from sender to receiver? guaranteed bandwidth? preservation of inter-packet ...
TK6383 Rangkaian Komputer
... LAN technology reducing the cost by reducing number of connection But connected computers have to compete for using shared connection Using principle of locality of reference to acquire computer communication pattern. ...
... LAN technology reducing the cost by reducing number of connection But connected computers have to compete for using shared connection Using principle of locality of reference to acquire computer communication pattern. ...
Partnerships
... Astronomers collect data about a star from many different earth based antennae and send the data to a specialized computer for analysis on a 24x7 basis. VLBI is not as concerned with data loss as they are with long term stability. The end goal is to send data at 1Gb/s from over 20 antennae that are ...
... Astronomers collect data about a star from many different earth based antennae and send the data to a specialized computer for analysis on a 24x7 basis. VLBI is not as concerned with data loss as they are with long term stability. The end goal is to send data at 1Gb/s from over 20 antennae that are ...
The Use of Underwater Wireless Networks in Pisciculture at
... besides that there are a lot of tools for this purpose. The simulation tool used on this research was Network Simulator (NS-2) also used at [12]. NS-2 has a great acceptation level by international scientific community, it is developed in C++ and TCL languages and it has an open source, hence it is ...
... besides that there are a lot of tools for this purpose. The simulation tool used on this research was Network Simulator (NS-2) also used at [12]. NS-2 has a great acceptation level by international scientific community, it is developed in C++ and TCL languages and it has an open source, hence it is ...
show ip route
... •an opportunity to indicate whether you want the router to use this configuration After you approve setup mode entries, the router uses the entries as a running configuration. The router also stores the configuration in NVRAM as a new startup-config, and you can start using the router. For additiona ...
... •an opportunity to indicate whether you want the router to use this configuration After you approve setup mode entries, the router uses the entries as a running configuration. The router also stores the configuration in NVRAM as a new startup-config, and you can start using the router. For additiona ...
WatSan Theme Group Meeting
... SE Data Network: The next meeting on July 2nd will include presentations of the SE data catalogue tool developed to collect and share information on available datasets across the SE, an overview of the mapping issues of the SE, and available assessments which have been registered with the MIMU. ...
... SE Data Network: The next meeting on July 2nd will include presentations of the SE data catalogue tool developed to collect and share information on available datasets across the SE, an overview of the mapping issues of the SE, and available assessments which have been registered with the MIMU. ...