Network Applications for Mobile Computing
... Because information about printers, shared servers, and operating environments for application software is unique to each department’s network, this information must be obtained from the network administrator of the department concerned. Thus, mobile users wishing to remotely access a conventional n ...
... Because information about printers, shared servers, and operating environments for application software is unique to each department’s network, this information must be obtained from the network administrator of the department concerned. Thus, mobile users wishing to remotely access a conventional n ...
SDN and cloud - Networking group
... the Data Centers • B4 is based on a SDN architecture using OpenFlow to control relatively simple switches built from merchant silicon • Google engineered the switches and the SDN architecture ...
... the Data Centers • B4 is based on a SDN architecture using OpenFlow to control relatively simple switches built from merchant silicon • Google engineered the switches and the SDN architecture ...
Bridges
... search forwarding database to see if MAC address is listed for any port except X if address not found, forward to all ports except X if address listed for port Y, check port Y for blocking or forwarding state if not blocked, transmit frame through port Y ...
... search forwarding database to see if MAC address is listed for any port except X if address not found, forward to all ports except X if address listed for port Y, check port Y for blocking or forwarding state if not blocked, transmit frame through port Y ...
GSM
... cell and neighboring cells and passes the information to the BSC. The BSC decides if handover is required, if so, a new traffic channel is allocated to the mobile station and the handover is performed. If handover is not required, the mobile station continues to transmit in the same frequency. ...
... cell and neighboring cells and passes the information to the BSC. The BSC decides if handover is required, if so, a new traffic channel is allocated to the mobile station and the handover is performed. If handover is not required, the mobile station continues to transmit in the same frequency. ...
Chapter 15 - William Stallings, Data and Computer
... hub acts as a repeater limited to about 100 m by UTP properties optical fiber may be used out to 500m physically star, logically bus transmission from a station seen by all others if two stations transmit at the same time have a ...
... hub acts as a repeater limited to about 100 m by UTP properties optical fiber may be used out to 500m physically star, logically bus transmission from a station seen by all others if two stations transmit at the same time have a ...
erbo
... Lightpaths and OPNs - Lightpath: high quality and high capacity optical network connection - Lightpaths provide applications with dedicated bandwidth with fixed characteristics at relatively low costs and with added security - Optical Private Network: system of permanent lightpaths to interconnect ...
... Lightpaths and OPNs - Lightpath: high quality and high capacity optical network connection - Lightpaths provide applications with dedicated bandwidth with fixed characteristics at relatively low costs and with added security - Optical Private Network: system of permanent lightpaths to interconnect ...
SCORE: A Scalable Architecture for Implementing Resource
... IP address is a globally unique or private number associated with a host network interface Every system which will send packets directly out across the Internet must have a unique IP address IP addresses are based on where station is connected IP addresses are controlled by a single organization add ...
... IP address is a globally unique or private number associated with a host network interface Every system which will send packets directly out across the Internet must have a unique IP address IP addresses are based on where station is connected IP addresses are controlled by a single organization add ...
Understanding the Causes and Impact of Network Failures
... it provides information not available from syslog, such as the cause of a failure, but at the same time it is generated by non-deterministic social processes and, thus, only reflects failures that are of a subjectively sufficient magnitude and duration to warrant a broader notice. However, this dual ...
... it provides information not available from syslog, such as the cause of a failure, but at the same time it is generated by non-deterministic social processes and, thus, only reflects failures that are of a subjectively sufficient magnitude and duration to warrant a broader notice. However, this dual ...
California Fault Lines: Understanding the Causes and
... it provides information not available from syslog, such as the cause of a failure, but at the same time it is generated by non-deterministic social processes and, thus, only reflects failures that are of a subjectively sufficient magnitude and duration to warrant a broader notice. However, this dual ...
... it provides information not available from syslog, such as the cause of a failure, but at the same time it is generated by non-deterministic social processes and, thus, only reflects failures that are of a subjectively sufficient magnitude and duration to warrant a broader notice. However, this dual ...
Lab 9.2.7 IP Addressing Basics
... protocol in the world. The Internet or World Wide Web only uses IP addressing. In order for a host to access the Internet, it must have an IP address. In its basic form, the IP address has two parts: ...
... protocol in the world. The Internet or World Wide Web only uses IP addressing. In order for a host to access the Internet, it must have an IP address. In its basic form, the IP address has two parts: ...
Introduction to networking
... An autonomous system is a collection of networks under a common administrative control EIGRP uses a autonomous system number, but calls this a process ID The process ID essentially refers to an instance of the protocol running on a router All the routers running in the same routing domain that are u ...
... An autonomous system is a collection of networks under a common administrative control EIGRP uses a autonomous system number, but calls this a process ID The process ID essentially refers to an instance of the protocol running on a router All the routers running in the same routing domain that are u ...
Powerpoint - People.cs.uchicago.edu
... network. I mean, where exactly does Google live? It lives obviously on Google's bank of servers, but it also lives in a PCbased application. ...
... network. I mean, where exactly does Google live? It lives obviously on Google's bank of servers, but it also lives in a PCbased application. ...
IP Addressing Explored
... A Note on Multicasting • Multicasting delivers a single stream of medial to a router and the receiving end • The router then multiplies and delivers the stream to local clients • As such, only one stream travels along the Internet thus saving bandwidth • In the case of Unicasting, multiple streams ...
... A Note on Multicasting • Multicasting delivers a single stream of medial to a router and the receiving end • The router then multiplies and delivers the stream to local clients • As such, only one stream travels along the Internet thus saving bandwidth • In the case of Unicasting, multiple streams ...
Chapter 7
... aggregation/de-aggregation, and forwarding, among others • Distinct planes suggests that they can operate independently using their own layers and protocols ...
... aggregation/de-aggregation, and forwarding, among others • Distinct planes suggests that they can operate independently using their own layers and protocols ...
Network and Communications
... whole Internet. Networks advertise routes for their own address space to their customers, peers and transit providers using the Border Gateway Protocol. These peers then (selectively) extend the announcement to their own customers, peers and transit providers. This goes around the world. A BGP route ...
... whole Internet. Networks advertise routes for their own address space to their customers, peers and transit providers using the Border Gateway Protocol. These peers then (selectively) extend the announcement to their own customers, peers and transit providers. This goes around the world. A BGP route ...
www.siskiyous.edu
... • Firewall default configuration – Block most common security threats • Preconfigured to accept, deny certain traffic types ...
... • Firewall default configuration – Block most common security threats • Preconfigured to accept, deny certain traffic types ...
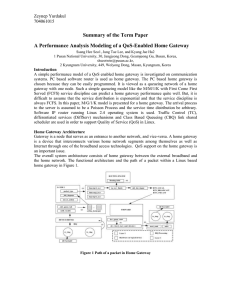
A performance analysis modeling of a QoS
... chosen because they can be easily programmed. It is viewed as a queueing network of a home gateway with one node. Such a simple queueing model like the M/M/1/K with First Come First Served (FCFS) service discipline can predict a home gateway performance quite well. But, it is difficult to assume tha ...
... chosen because they can be easily programmed. It is viewed as a queueing network of a home gateway with one node. Such a simple queueing model like the M/M/1/K with First Come First Served (FCFS) service discipline can predict a home gateway performance quite well. But, it is difficult to assume tha ...
Slide
... with prob. p: randomly selected node with prob. 1-p: copied target from selected ‘prototye node’ 2. Attaching to edges: : after adding new node, instead of selecting target node, select target edges and connect new node to end point of the edges. ...
... with prob. p: randomly selected node with prob. 1-p: copied target from selected ‘prototye node’ 2. Attaching to edges: : after adding new node, instead of selecting target node, select target edges and connect new node to end point of the edges. ...
Algorithmic Mechanism Design
... costs a network is optimal or socially efficient if it minimizes the social cost A graph G=(V,E) is stable (for a value ) if there exists a strategy vector S such that: ...
... costs a network is optimal or socially efficient if it minimizes the social cost A graph G=(V,E) is stable (for a value ) if there exists a strategy vector S such that: ...
M2M Network for Smart Mobility
... When using an M2M network, continuous connection to the network while driving is needed in order to send real-time information such as car location and to receive services based on such information. In addition, as image sensor technology advances, large data files such as images and movies are more ...
... When using an M2M network, continuous connection to the network while driving is needed in order to send real-time information such as car location and to receive services based on such information. In addition, as image sensor technology advances, large data files such as images and movies are more ...
Using the BASrouter with a Spyder Controller
... place. The information in the application note is applicable to each BACnet MS/TP model. BACnet MS/TP data from the Spyder controllers are carried over a two-wire non-isolated twisted-pair network. Spyder controllers auto-baud. They wait until a head-end device — usually a building controller — to s ...
... place. The information in the application note is applicable to each BACnet MS/TP model. BACnet MS/TP data from the Spyder controllers are carried over a two-wire non-isolated twisted-pair network. Spyder controllers auto-baud. They wait until a head-end device — usually a building controller — to s ...
O A RIGINAL RTICLES
... Topology change occurs frequently with every move of the mobile node and hence route may also get changed. It leads to network partitions and most of the times some packets get lost. The data packets are routed through intermediate nodes. Ad-hoc network has such essential functions like packet forwa ...
... Topology change occurs frequently with every move of the mobile node and hence route may also get changed. It leads to network partitions and most of the times some packets get lost. The data packets are routed through intermediate nodes. Ad-hoc network has such essential functions like packet forwa ...
Chapter I: Introduction
... wires) layer and move up to Application (e.g., mail, web browsers) layer explaining how known resources can be used to implement requested services • Top Down : Start with Application layer and move down to Physical layer, explaining how required applications can be implemented ...
... wires) layer and move up to Application (e.g., mail, web browsers) layer explaining how known resources can be used to implement requested services • Top Down : Start with Application layer and move down to Physical layer, explaining how required applications can be implemented ...
Network Access Security – It`s Broke, Now What?
... Client Broker "Middleware" that runs on the client and talks to the Posture Collectors, collecting their data, and passing it down to Network Access Requestor. In product form, this is generally bundled with the Network Access Requestor. ...
... Client Broker "Middleware" that runs on the client and talks to the Posture Collectors, collecting their data, and passing it down to Network Access Requestor. In product form, this is generally bundled with the Network Access Requestor. ...