3rd Edition, Chapter 5
... carry network layer data of any network layer protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address ...
... carry network layer data of any network layer protocol (not just IP) at same time ability to demultiplex upwards bit transparency: must carry any bit pattern in the data field error detection (no correction) connection liveness: detect, signal link failure to network layer network layer address ...
Switched LAN Architecture
... application needs, and requires access to different data resources available through the network. For example, when selecting switches for the wiring closets of the HR and Finance departments, you would choose a switch that had enough ports to meet the department needs and was powerful enough to acc ...
... application needs, and requires access to different data resources available through the network. For example, when selecting switches for the wiring closets of the HR and Finance departments, you would choose a switch that had enough ports to meet the department needs and was powerful enough to acc ...
XCAST6_WhiteBoard
... 1. XCAST works on routers with existing Unicast routing information. There is no need for additional routing protocol like Multicast which can lead to a delivery time overhead. 2. Participants are unique and identified clearly by individual IP addresses, therefore individual access lists, policies a ...
... 1. XCAST works on routers with existing Unicast routing information. There is no need for additional routing protocol like Multicast which can lead to a delivery time overhead. 2. Participants are unique and identified clearly by individual IP addresses, therefore individual access lists, policies a ...
SEMESTER_2_Chapter_4KEY
... 3. If an update with a better metric for that network is received from any neighboring router during the holddown period, the network is reinstated and the holddown timer is removed. 4. If an update from any other neighbor is received during the holddown period with the same or worse metric for that ...
... 3. If an update with a better metric for that network is received from any neighboring router during the holddown period, the network is reinstated and the holddown timer is removed. 4. If an update from any other neighbor is received during the holddown period with the same or worse metric for that ...
COVERPAGE
... tcptrace software tool [27] was used to summarize tcpdump data set. Tcptrace can produce several different types of output containing information on each connection seen, such as elapsed time, bytes and segments sent and received, retransmissions, round trip times, window advertisements and throughp ...
... tcptrace software tool [27] was used to summarize tcpdump data set. Tcptrace can produce several different types of output containing information on each connection seen, such as elapsed time, bytes and segments sent and received, retransmissions, round trip times, window advertisements and throughp ...
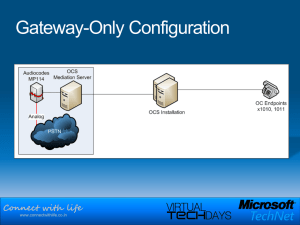
Voice over IP (VoIP)
... communications services. Voice over IP has now been proven feasible; the race is on to adopt standards, design terminals and gateways, and begin the roll-out of services on a global scale. Needless to say, the technical difficulties of transporting voice and the complexities of building commercial p ...
... communications services. Voice over IP has now been proven feasible; the race is on to adopt standards, design terminals and gateways, and begin the roll-out of services on a global scale. Needless to say, the technical difficulties of transporting voice and the complexities of building commercial p ...
docx 152851_networking
... 1. Ensure that you have set both the console and the Command Line access passwords – this should allow one to control the authorisations and also at the same time limit those who can make changes to the settings of the switch. 2. The next step requires securing the command line, disabling the telnet ...
... 1. Ensure that you have set both the console and the Command Line access passwords – this should allow one to control the authorisations and also at the same time limit those who can make changes to the settings of the switch. 2. The next step requires securing the command line, disabling the telnet ...
DeviceNet Overview
... 500 m @ 125Kb, 100 m @ 500Kb. 8 byte network length, fragmentation application. Linear trunk / drop line. Power & signal on same cable. 24Vdc @ 8A Peer to Peer or Master/Slave. Remove & replace under power. Hazardous area classification is Class 1 Div 2 Open standard administered by ODVA. ...
... 500 m @ 125Kb, 100 m @ 500Kb. 8 byte network length, fragmentation application. Linear trunk / drop line. Power & signal on same cable. 24Vdc @ 8A Peer to Peer or Master/Slave. Remove & replace under power. Hazardous area classification is Class 1 Div 2 Open standard administered by ODVA. ...
Module 8
... improper protocol configuration down interfaces incorrect routing information packet fragmentation is required ...
... improper protocol configuration down interfaces incorrect routing information packet fragmentation is required ...
No Slide Title
... The interaction between layers in the OSI model • The OSI model is composed of seven ordered layers. • Within a single machine each layer calls upon the services of the layer just below it. • Layer 3 uses the services of layer 2 and provide services to layer 4 • Between machines, layer x on the mac ...
... The interaction between layers in the OSI model • The OSI model is composed of seven ordered layers. • Within a single machine each layer calls upon the services of the layer just below it. • Layer 3 uses the services of layer 2 and provide services to layer 4 • Between machines, layer x on the mac ...
Get your computer ready for Chestnut
... Every computer needs an IP address in order to communicate with other devices on the network as well as accessing the Internet. At Chestnut Residence, our network server will assign an IP address for each connected computer. Your main task is to connect your computer properly using the provided equi ...
... Every computer needs an IP address in order to communicate with other devices on the network as well as accessing the Internet. At Chestnut Residence, our network server will assign an IP address for each connected computer. Your main task is to connect your computer properly using the provided equi ...
Cloud Computing and Security
... standard Ethernet switching networks. Cost-effective layer-2 switching provides an assured forwarding performance within a metropolitan area domain (where exact routing path is not significant since delay and loss characteristics are comparable) Logical Separation: Implemented through the use of: • ...
... standard Ethernet switching networks. Cost-effective layer-2 switching provides an assured forwarding performance within a metropolitan area domain (where exact routing path is not significant since delay and loss characteristics are comparable) Logical Separation: Implemented through the use of: • ...
2.1 Chapter 2 Network Models
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
... processes at this time with port addresses a, b, and c. The receiving computer is running two processes at this time with port addresses j and k. Process a in the sending computer needs to communicate with process j in the receiving computer. Note that although physical addresses change from hop to ...
Consultation Paper On The Review of the Licensing
... only the actual holders of particular technology based Network and/or Service Licenses may operate certain networks and/or provide very specific services. For example, only the holders of either Network or Service Voice (whether fixed or mobile) Licenses can make available and accessible voice servi ...
... only the actual holders of particular technology based Network and/or Service Licenses may operate certain networks and/or provide very specific services. For example, only the holders of either Network or Service Voice (whether fixed or mobile) Licenses can make available and accessible voice servi ...
What is WIMAX ? - Yola
... The phrase is therefore often used by the telecommunications and cable television industries. The actual distance of this leg may be considerably more than a mile, especially in rural areas. ...
... The phrase is therefore often used by the telecommunications and cable television industries. The actual distance of this leg may be considerably more than a mile, especially in rural areas. ...
Introduction to BACnet Routers
... another on a local bus involving no routers, the NPCI collapses to only two bytes. However, if a message is being sent to a remote device (a device on another network), the NPCI expands since the network layer must specify the destination network in the NPCI. When a router relays this same remote me ...
... another on a local bus involving no routers, the NPCI collapses to only two bytes. However, if a message is being sent to a remote device (a device on another network), the NPCI expands since the network layer must specify the destination network in the NPCI. When a router relays this same remote me ...
Bayesian Method for Groundwater Quality Monitoring Network
... contaminant distribution, and accordingly to estimate the expected value of sample information. Disability adjusted life years approach of the global burden of disease is used for quantifying the health risk consequences. This is demonstrated through a case study application to nitrate contamination ...
... contaminant distribution, and accordingly to estimate the expected value of sample information. Disability adjusted life years approach of the global burden of disease is used for quantifying the health risk consequences. This is demonstrated through a case study application to nitrate contamination ...
Datasheet - EnOcean Alliance
... performance intensive computing onto the client platform while remaining completely platform independent. The application is built with respect to standard conformity and is therefore supported by most AJAX-capable Browsers including Internet Explorer 7, Firefox3, Safari3, Opera9, Google Chrome and ...
... performance intensive computing onto the client platform while remaining completely platform independent. The application is built with respect to standard conformity and is therefore supported by most AJAX-capable Browsers including Internet Explorer 7, Firefox3, Safari3, Opera9, Google Chrome and ...
APES 110 Network Firm amendment - Final
... The determination of whether the professional resources shared are significant, and therefore the firms are network firms, should be made based on the relevant facts and circumstances. Where the shared resources are limited to common audit methodology or audit manuals, with no exchange of personnel ...
... The determination of whether the professional resources shared are significant, and therefore the firms are network firms, should be made based on the relevant facts and circumstances. Where the shared resources are limited to common audit methodology or audit manuals, with no exchange of personnel ...
ppt - Texas A&M University
... – E.g., IPsec makes content of the traffic inaccessible. – 85% of the IP traffic will be encrypted in the near future. (VPN, SSL, etc.) An encrypted email message between a customer service center and its ordinary user is not under suspicion, however, the one between an employee of a defense contr ...
... – E.g., IPsec makes content of the traffic inaccessible. – 85% of the IP traffic will be encrypted in the near future. (VPN, SSL, etc.) An encrypted email message between a customer service center and its ordinary user is not under suspicion, however, the one between an employee of a defense contr ...
Enabling Service with MoCA
... MAC throughput including 175 Mb/s (MoCA v1.1) Flexible spectrum usage – 50 MHz coexisting with Cable or Satellite Support for 16 nodes (MoCA v1.1) PHY is Bitloaded OFDM – optimizes PHY rate for any channel • Pre-equalization allows simple Reed Solomon FEC ...
... MAC throughput including 175 Mb/s (MoCA v1.1) Flexible spectrum usage – 50 MHz coexisting with Cable or Satellite Support for 16 nodes (MoCA v1.1) PHY is Bitloaded OFDM – optimizes PHY rate for any channel • Pre-equalization allows simple Reed Solomon FEC ...
Basic Network Configuration
... To track down the cause of disappearing packets, first run traceroute (covered next) to discover the route that packets are taking to the target host. Then ping the intermediate gateways in sequence to discover which link is dropping packets. To pin down the problem, you need to send a fair number o ...
... To track down the cause of disappearing packets, first run traceroute (covered next) to discover the route that packets are taking to the target host. Then ping the intermediate gateways in sequence to discover which link is dropping packets. To pin down the problem, you need to send a fair number o ...
Chuong 1 - Gio Thieu Quan Tri Mang
... interconnect a set of BSSs and an integrated LAN to form an ESS. The DS is used for the transfer of communications between the APs in the ESS. The DS is composed of two parts: the Distribution System Medium and the Distribution System Services. The DSM is the medium used for communications among APs ...
... interconnect a set of BSSs and an integrated LAN to form an ESS. The DS is used for the transfer of communications between the APs in the ESS. The DS is composed of two parts: the Distribution System Medium and the Distribution System Services. The DSM is the medium used for communications among APs ...