Switches part 1 File
... does not support it, the Catalyst switch defaults the switch port to half-duplex mode. • Half-duplex on one end and full-duplex on the other causes late collision errors at the half-duplex end. • To avoid this, manually set the duplex parameters of the switch to match the attached device. CCNA3-10 ...
... does not support it, the Catalyst switch defaults the switch port to half-duplex mode. • Half-duplex on one end and full-duplex on the other causes late collision errors at the half-duplex end. • To avoid this, manually set the duplex parameters of the switch to match the attached device. CCNA3-10 ...
GENIConnections
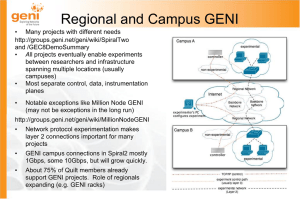
... Regional and Campus GENI • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentat ...
... Regional and Campus GENI • Many projects with different needs http://groups.geni.net/geni/wiki/SpiralTwo and /GEC8DemoSummary • All projects eventually enable experiments between researchers and infrastructure spanning multiple locations (usually campuses) • Most separate control, data, instrumentat ...
cPacket Networks - Semantic Scholar
... sources and underlying trade-offs, to facilitate effective measurement and analysis, and to support development of a consistent latency monitoring and improvement strategy. The L-word buzz has been increasing with the proliferation of network applications with end-to-end latency requirements. Tradit ...
... sources and underlying trade-offs, to facilitate effective measurement and analysis, and to support development of a consistent latency monitoring and improvement strategy. The L-word buzz has been increasing with the proliferation of network applications with end-to-end latency requirements. Tradit ...
ppt
... • Focus on network to application layer • We will deal with: • Protocol rules and algorithms • Investigate protocol trade-offs • Why this way and not another? ...
... • Focus on network to application layer • We will deal with: • Protocol rules and algorithms • Investigate protocol trade-offs • Why this way and not another? ...
Lecture 12 - USC`s Center for Computer Systems Security
... • Fundamentally differs from existing Intrusion Detection System (IDS) approaches – IDS protects local hosts within its perimeter (LAN) – An enumerator would identify both local as well as remote infections ...
... • Fundamentally differs from existing Intrusion Detection System (IDS) approaches – IDS protects local hosts within its perimeter (LAN) – An enumerator would identify both local as well as remote infections ...
Note
... inet_aton() converts the Internet host address cp from the standard numbers-and-dots notation into binary data and stores it in the structure that inp points to. inet_aton() returns non-zero if the address is valid, zero if not. The inet_addr() function converts the Internet host address cp from num ...
... inet_aton() converts the Internet host address cp from the standard numbers-and-dots notation into binary data and stores it in the structure that inp points to. inet_aton() returns non-zero if the address is valid, zero if not. The inet_addr() function converts the Internet host address cp from num ...
paper
... decoding buffer and processed by a decoder, which runs Gauss elimination over the received packets. In the decoding buffer, a virtual output queue (VOQ) is generated for each generation. The decoder is a batch processor [2] which checks all VOQs for complete generations with the decoding interval δt ...
... decoding buffer and processed by a decoder, which runs Gauss elimination over the received packets. In the decoding buffer, a virtual output queue (VOQ) is generated for each generation. The decoder is a batch processor [2] which checks all VOQs for complete generations with the decoding interval δt ...
Fiber Optic Network Solutions
... In the broadband communication, the fiber optic network deployment is increasingly applied to today’s cloud applications and high-demanding multimedia streaming service. The fiber optic transmission has large advantages over the existing copper wire as the optic fiber cable carries much lower attenu ...
... In the broadband communication, the fiber optic network deployment is increasingly applied to today’s cloud applications and high-demanding multimedia streaming service. The fiber optic transmission has large advantages over the existing copper wire as the optic fiber cable carries much lower attenu ...
Brocade 6510 Switch Data Sheet
... Administrators can configure the entire fabric (or multiple fabrics) at one time using common rules and policies, or customize policies for specific ports or switch elements. Monitoring: Leverages pre-defined MAPS policies to automatically detect and alert administrators to different latency severit ...
... Administrators can configure the entire fabric (or multiple fabrics) at one time using common rules and policies, or customize policies for specific ports or switch elements. Monitoring: Leverages pre-defined MAPS policies to automatically detect and alert administrators to different latency severit ...
On Demand Network-wide VPN Deployment in GPRS
... of the original packet is visible, or may be changed as it moves through a network. Even though there is some criticism on IPsec, it is commonly admitted that it is the best IP security protocol available today [8]. It facilitates the authentication of the communicating entities, and the transparent ...
... of the original packet is visible, or may be changed as it moves through a network. Even though there is some criticism on IPsec, it is commonly admitted that it is the best IP security protocol available today [8]. It facilitates the authentication of the communicating entities, and the transparent ...
Centrality Measures
... • IntuiHon: how many pairs of individuals would have to go through you in order to reach one another in the minimum number of hops? • who has higher betweenness, X or Y? Y ...
... • IntuiHon: how many pairs of individuals would have to go through you in order to reach one another in the minimum number of hops? • who has higher betweenness, X or Y? Y ...
Deploying F5 with Nagios Open Source Network
... Adding a BIG-IP LTM host to the Nagios monitored environment The Nagios platform provides methods to monitor particular devices or services. Service monitors (HTTP, FTP, and so on) can quickly be established using the plug-ins available with the distribution. Plug-ins for Nagios are Perl or other si ...
... Adding a BIG-IP LTM host to the Nagios monitored environment The Nagios platform provides methods to monitor particular devices or services. Service monitors (HTTP, FTP, and so on) can quickly be established using the plug-ins available with the distribution. Plug-ins for Nagios are Perl or other si ...
Network Training 2008-05-25
... RG-58 (Thin-Net). Most of the time, if a simple problem occurred at only one node, the entire network would stop working. ...
... RG-58 (Thin-Net). Most of the time, if a simple problem occurred at only one node, the entire network would stop working. ...
BlueField™ Multicore System on Chip
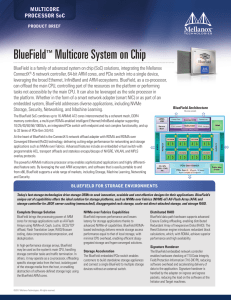
... BlueField enables the attachment of multiple GPUs through its integrated PCIe switch. BlueField PCIe 4.0 support is futureproof for nextgeneration GPU devices. Mellanox PeerDirect™ Mellanox PeerDirect is an accelerated communication architecture that supports peer-to-peer ...
... BlueField enables the attachment of multiple GPUs through its integrated PCIe switch. BlueField PCIe 4.0 support is futureproof for nextgeneration GPU devices. Mellanox PeerDirect™ Mellanox PeerDirect is an accelerated communication architecture that supports peer-to-peer ...
Measuring BGP - Geoff Huston
... Route views in prefix-length-filtered parts of the net do not show the same recent reduction in the size of the routing table. It is likely that the reduction in routes seen by AS1221 appears to be in the prefix-length filtered ranges ...
... Route views in prefix-length-filtered parts of the net do not show the same recent reduction in the size of the routing table. It is likely that the reduction in routes seen by AS1221 appears to be in the prefix-length filtered ranges ...
Application Note: How to Evaluate Network and Device Performance
... 1.1.5 Measuring time to recover from a lost mote One of the reasons a mesh is important is the robustness to path failures. In star and tree structures, a single RF path can represent a single point of failure for one or many devices data. In evaluating the mesh, many observers will want to see the ...
... 1.1.5 Measuring time to recover from a lost mote One of the reasons a mesh is important is the robustness to path failures. In star and tree structures, a single RF path can represent a single point of failure for one or many devices data. In evaluating the mesh, many observers will want to see the ...
Fastpass: A Centralized “Zero-Queue” Datacenter Network
... utilization, and (3) the network is able to support multiple resource allocation objectives between flows, applications, or users? Such a network would be useful in many contexts, but especially in datacenters where queueing dominates end-to-end latencies, link rates are at technology’s bleeding edg ...
... utilization, and (3) the network is able to support multiple resource allocation objectives between flows, applications, or users? Such a network would be useful in many contexts, but especially in datacenters where queueing dominates end-to-end latencies, link rates are at technology’s bleeding edg ...
Disks
... Partitions and MBRs – PC only allows for 4 partitions. – To overcome limit, create a logical partition which ...
... Partitions and MBRs – PC only allows for 4 partitions. – To overcome limit, create a logical partition which ...
- Z-Wave Products
... Behavior within the Z-Wave network On factory default the device does not belong to any Z-Wave network. The device needs to join an existing wireless network to communicate with the devices of this network. This process is called Inclusion. Devices can also leave a network. This process is called Ex ...
... Behavior within the Z-Wave network On factory default the device does not belong to any Z-Wave network. The device needs to join an existing wireless network to communicate with the devices of this network. This process is called Inclusion. Devices can also leave a network. This process is called Ex ...
Managed Switch Quick Start Guide
... supplies are not being used, then a jumper can be used between these terminals to prevent a fault (indicated by solid red LED). Also connect the 0 V common (#3 or #4 on Rail and #2°2 on MICE) and optionally, the fault contact (normally-closed for indication of alarm such as lost power supply, redund ...
... supplies are not being used, then a jumper can be used between these terminals to prevent a fault (indicated by solid red LED). Also connect the 0 V common (#3 or #4 on Rail and #2°2 on MICE) and optionally, the fault contact (normally-closed for indication of alarm such as lost power supply, redund ...
CMT-TS-CAG Meeting - Grupo de Redes de Computadores
... Chunks of the net are unable to reach nodes in nearby regions Small Effective Network Diameter A path may cease to exist almost as quickly as it was discovered (reactive routing) Limited Redundancy The redundancy in MANETs is critical to providing additional bandwidth In VANETs the redundanc ...
... Chunks of the net are unable to reach nodes in nearby regions Small Effective Network Diameter A path may cease to exist almost as quickly as it was discovered (reactive routing) Limited Redundancy The redundancy in MANETs is critical to providing additional bandwidth In VANETs the redundanc ...
Expl_Sw_chapter_02_Switches_Part_I
... does not support it, the Catalyst switch defaults the switch port to half-duplex mode. • Half-duplex on one end and full-duplex on the other causes late collision errors at the half-duplex end. • To avoid this, manually set the duplex parameters of the switch to match the attached device. CCNA3-9 ...
... does not support it, the Catalyst switch defaults the switch port to half-duplex mode. • Half-duplex on one end and full-duplex on the other causes late collision errors at the half-duplex end. • To avoid this, manually set the duplex parameters of the switch to match the attached device. CCNA3-9 ...
IEEE 802.11 Wireless LAN Security Performance Using Multiple
... which uses an Ethernet-style contention algorithm that provides access to all traffic. Ordinary asynchronous traffic uses this coordination function (see Section 2.2.4). The upper MAC sublayer is the point coordination function (PCF), a centralised MAC algorithm that provides contention-free service ...
... which uses an Ethernet-style contention algorithm that provides access to all traffic. Ordinary asynchronous traffic uses this coordination function (see Section 2.2.4). The upper MAC sublayer is the point coordination function (PCF), a centralised MAC algorithm that provides contention-free service ...