Detecting Flood-based Denial-of-Service Attacks with SNMP/RMON Abstract
... Denial of service (DoS) attacks continue to threaten networks and computers connected to the Internet. As reported in the CSI/FBI Computer Crime and Security Survey of 2003[1], 42% of respondents indicated DoS attacks were a major problem for them. Financial setbacks due to DoS attacks alone were th ...
... Denial of service (DoS) attacks continue to threaten networks and computers connected to the Internet. As reported in the CSI/FBI Computer Crime and Security Survey of 2003[1], 42% of respondents indicated DoS attacks were a major problem for them. Financial setbacks due to DoS attacks alone were th ...
Paper
... (FCoE), Small Computer System Interface over IP (iSCSI), and network-attached storage (NAS) traffic. This solution allows reduction in the number of devices managed and maintained, reduced cabling requirements, and more efficient resource utilization, leading to lower power and cooling costs. ...
... (FCoE), Small Computer System Interface over IP (iSCSI), and network-attached storage (NAS) traffic. This solution allows reduction in the number of devices managed and maintained, reduced cabling requirements, and more efficient resource utilization, leading to lower power and cooling costs. ...
Goal of VPN
... • The goal of a Virtual Private Network (VPN) is to provide private communications within the public Internet Infrastructure • VPNs apply various networking technologies to achieve the goal • The basic concepts: – Build a virtual overlay network that is run on top of the infrastructure of the Intern ...
... • The goal of a Virtual Private Network (VPN) is to provide private communications within the public Internet Infrastructure • VPNs apply various networking technologies to achieve the goal • The basic concepts: – Build a virtual overlay network that is run on top of the infrastructure of the Intern ...
Chapter 4
... • In addition to straightforward network adapters, several types of cards deliver specialized capabilities – They include interfaces for wireless networks, as well as a feature for so-called diskless workstations (“thin clients”), which must access the network to load an OS when they boot • These c ...
... • In addition to straightforward network adapters, several types of cards deliver specialized capabilities – They include interfaces for wireless networks, as well as a feature for so-called diskless workstations (“thin clients”), which must access the network to load an OS when they boot • These c ...
Forensic Analysis Reveals Data Leaks in HIPAA
... server hosting the database. Although the server hosting the database had been compromised by the attackers, Kivu determined the attackers had not managed to access the contents of the ERM application database itself8. Kivu was therefore able to focus the initial searching on data elements outside t ...
... server hosting the database. Although the server hosting the database had been compromised by the attackers, Kivu determined the attackers had not managed to access the contents of the ERM application database itself8. Kivu was therefore able to focus the initial searching on data elements outside t ...
Chapter 1
... machine to establish sessions between them. •Sessions offer various services: •Dialog control (keeping track of whose turn it is to transmit); •Token management (preventing two parties from attempting the same critical operation at the same time); •Synchronization (check pointing long transmissions ...
... machine to establish sessions between them. •Sessions offer various services: •Dialog control (keeping track of whose turn it is to transmit); •Token management (preventing two parties from attempting the same critical operation at the same time); •Synchronization (check pointing long transmissions ...
ppt
... • Another way is to define elementary fragment size that can pass through every network. • When packet fragmented, all pieces equal to elementary fragment size, except last one (may be smaller). • Packet may contain several fragments. ...
... • Another way is to define elementary fragment size that can pass through every network. • When packet fragmented, all pieces equal to elementary fragment size, except last one (may be smaller). • Packet may contain several fragments. ...
Campground and RV Park Wi-Fi Planning
... device to be carried by the data cables rather than power cords. The result is lower cost, less downtime, easier maintenance, and greater installation flexibility than with traditional wiring. Bandwidth5 - In computer networks, bandwidth is synonymous with data transfer rate, the amount of data that ...
... device to be carried by the data cables rather than power cords. The result is lower cost, less downtime, easier maintenance, and greater installation flexibility than with traditional wiring. Bandwidth5 - In computer networks, bandwidth is synonymous with data transfer rate, the amount of data that ...
Copy area
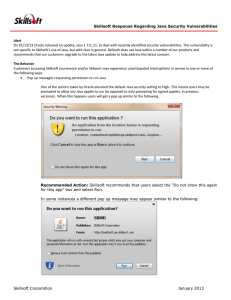
... Skillsoft Response Regarding Java Security Vulnerabilities Recommended Action: If the Publisher is identified as “Skillsoft Corporation” then Skillsoft recommends users select the “Always trust content from this Publisher” and select Run. ...
... Skillsoft Response Regarding Java Security Vulnerabilities Recommended Action: If the Publisher is identified as “Skillsoft Corporation” then Skillsoft recommends users select the “Always trust content from this Publisher” and select Run. ...
Safe & Secure Environment for Students
... – Ensure students, teachers and administrators make the most of its computing technology – while receiving only appropriate Internet content – Previous filtering solution provided inadequate integration with user directories, ...
... – Ensure students, teachers and administrators make the most of its computing technology – while receiving only appropriate Internet content – Previous filtering solution provided inadequate integration with user directories, ...
Chapter 1 Security Problems in Computing
... Ans: C1 = 50h * H = 0101 0000 * H = 38 + 171 = 209. C2 = 45h * H = 0100 0101 * H = 38 + 40 + 123 = 201. C3 = 41h * H = 0100 0001 * H = 38 + 123 = 161. C4 = 43h * H = 0100 0011 * H = 38 + 118 + 123 = 279. ...
... Ans: C1 = 50h * H = 0101 0000 * H = 38 + 171 = 209. C2 = 45h * H = 0100 0101 * H = 38 + 40 + 123 = 201. C3 = 41h * H = 0100 0001 * H = 38 + 123 = 161. C4 = 43h * H = 0100 0011 * H = 38 + 118 + 123 = 279. ...
On PRY-layer Security of Cognitive Radio: Collaborative Sensing
... layer security attacks. Existing research on the PHYlayer security of the CR networks is very limited. In [3], a general analysis of threats to different types of CRs along with a rough sketch of mitigation techniques is provided. In [4], the denial-of-service vulnerabilities of CR networks are exam ...
... layer security attacks. Existing research on the PHYlayer security of the CR networks is very limited. In [3], a general analysis of threats to different types of CRs along with a rough sketch of mitigation techniques is provided. In [4], the denial-of-service vulnerabilities of CR networks are exam ...
A Study on Effective Hash Routing in MANET
... The NN received the H(RREQ) message obtains the H(RREQi) which is applied to the MD5 in order to verification digital signatures and calculates log2n and then creates n bit string g value after adding to the H(RREQi) by calculating 0 number of bit strings of message. It should check that j-th bit st ...
... The NN received the H(RREQ) message obtains the H(RREQi) which is applied to the MD5 in order to verification digital signatures and calculates log2n and then creates n bit string g value after adding to the H(RREQi) by calculating 0 number of bit strings of message. It should check that j-th bit st ...
Introduction to Peer-to
... ▴ connected overlay (i.e., no partitions), low average path length ▴ data objects accessible from anywhere in the network ...
... ▴ connected overlay (i.e., no partitions), low average path length ▴ data objects accessible from anywhere in the network ...
Malicious Threats - The University of Texas at Dallas
... Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
... Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
... exercises a network or host is the target of attack. Web based attacks focus on an application itself and functions on Application Layer of the OSI. Most of all attacks occur at the application layer. One approach for dealing with HTTP-based attacks is to identify malicious code in incoming HTTP req ...
Malicious Threats - The University of Texas at Dallas
... Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
... Sanjay Goel, School of Business/Center for Information Forensics and Assurance University at Albany Proprietary Information ...
Application Security within Java 2, Standard Edition (J2SE)
... is loaded, the system uses a class called the SecureClassLoader (java.security.SecureClassLoader) to load the class. First the class is loaded from the specified URL and then the digital signature of the class is checked to make sure that the class is correct and intact. A CodeSource object is deriv ...
... is loaded, the system uses a class called the SecureClassLoader (java.security.SecureClassLoader) to load the class. First the class is loaded from the specified URL and then the digital signature of the class is checked to make sure that the class is correct and intact. A CodeSource object is deriv ...
Cisco AON Secure File Transfer Extension Module
... business applications directly from within the network, offloading the task of developing and managing these functions on the dozens or hundreds of application infrastructure servers and application endpoints within your business and throughout your trading community. The Cisco AON module or applian ...
... business applications directly from within the network, offloading the task of developing and managing these functions on the dozens or hundreds of application infrastructure servers and application endpoints within your business and throughout your trading community. The Cisco AON module or applian ...
The FTC: What you need to know about one of the most relentless
... regardless of the cybersecurity representations made by the company. However, other than precedents established through previous enforcement activity and what has been determined to be “unreasonable” in its prior consent decrees, the FTC’s guidance on these standards is minimal. This lack of guidanc ...
... regardless of the cybersecurity representations made by the company. However, other than precedents established through previous enforcement activity and what has been determined to be “unreasonable” in its prior consent decrees, the FTC’s guidance on these standards is minimal. This lack of guidanc ...
IEEE 802.11 Wireless LAN Security Performance Using Multiple
... mobility. Unlike a traditional wired network, which requires a wire to connect a computer to the network, wireless technology enables the users to access information from anywhere without any restriction. Wireless networks are frequently categorised into three groups based on their coverage range [3 ...
... mobility. Unlike a traditional wired network, which requires a wire to connect a computer to the network, wireless technology enables the users to access information from anywhere without any restriction. Wireless networks are frequently categorised into three groups based on their coverage range [3 ...
Download
... Admission control: 802.1x based topology independent authentication and authorization for end-points and network devices. Confidentiality and integrity: Link-layer 802.1AE authenticated cryptography provides data privacy and guarantees its reliability while allowing the insertion of network services ...
... Admission control: 802.1x based topology independent authentication and authorization for end-points and network devices. Confidentiality and integrity: Link-layer 802.1AE authenticated cryptography provides data privacy and guarantees its reliability while allowing the insertion of network services ...