Language Support for Concurrency
... – Must coordinate multiple copies of shared state information (using only a network) – What would be easy in a centralized system becomes a lot more difficult ...
... – Must coordinate multiple copies of shared state information (using only a network) – What would be easy in a centralized system becomes a lot more difficult ...
Introduction to HTML - Department of Computing and Software
... computer in the network called Domain Server. These names are approved by the Internet Naming Authority to ensure that they are unique. The software that translates the names into IP addresses is called Domain Name Service (DNS) World Wide Web (www): is another means of communication between compute ...
... computer in the network called Domain Server. These names are approved by the Internet Naming Authority to ensure that they are unique. The software that translates the names into IP addresses is called Domain Name Service (DNS) World Wide Web (www): is another means of communication between compute ...
Data Communications for Business Students
... individual computers (made when needed and terminated when transmission is completed). – Data packets are encrypted for security. ...
... individual computers (made when needed and terminated when transmission is completed). – Data packets are encrypted for security. ...
Computer Terminology …
... MSN Messenger item for a user on Computer B Computer A: What "number"/designation is Computer B on these days? Don't know- let's look in The Directory. Computer A: Aha, the directory says that Computer B is on number (e.g 169.145.72.9) at the moment! Computer A: I'm sending a request to Computer B o ...
... MSN Messenger item for a user on Computer B Computer A: What "number"/designation is Computer B on these days? Don't know- let's look in The Directory. Computer A: Aha, the directory says that Computer B is on number (e.g 169.145.72.9) at the moment! Computer A: I'm sending a request to Computer B o ...
The Triple-A approach to network security
... system works and they perceive it as getting in the way of productivity, they will not use it. The business value of the system then disappears, not to mention the network security. With mobility, for example, BYOD is one of the most common ways in which employees can make their organisation vulnera ...
... system works and they perceive it as getting in the way of productivity, they will not use it. The business value of the system then disappears, not to mention the network security. With mobility, for example, BYOD is one of the most common ways in which employees can make their organisation vulnera ...
Introduction to Information Security
... In general, security is “the quality or state of being secure—to be free from danger.” It means to be protected from adversaries—from those who would do harm, intentionally or otherwise. A successful organization should have the following multiple layers of security in place for the protection of it ...
... In general, security is “the quality or state of being secure—to be free from danger.” It means to be protected from adversaries—from those who would do harm, intentionally or otherwise. A successful organization should have the following multiple layers of security in place for the protection of it ...
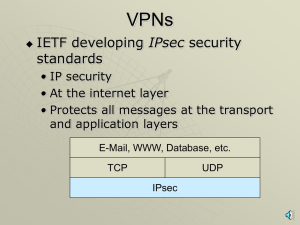
VPNs, PKIs, ISSs, SSLs with narration
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
... Another Security System for VPNs is the Point-to-Point Tunneling Protocol (PPTP) ...
view presentation
... SDLC is the process of developing information systems through investigation, analysis, design, implementation and maintenance. SDLC is also known as information systems development or application development. SDLC is a systems approach to problem solving and is made up of several phases, each compri ...
... SDLC is the process of developing information systems through investigation, analysis, design, implementation and maintenance. SDLC is also known as information systems development or application development. SDLC is a systems approach to problem solving and is made up of several phases, each compri ...
Document
... Using Web search bots to infect other computers Causing other people’s computers to become “zombie” PCs following a master computer Infecting corporate servers with “zombie” Trojan horses that allow undetected access through a back door ...
... Using Web search bots to infect other computers Causing other people’s computers to become “zombie” PCs following a master computer Infecting corporate servers with “zombie” Trojan horses that allow undetected access through a back door ...
Chapter 1
... Developed by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
... Developed by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
Dependable Cyber Physical Systems
... In a Cloud or IoT scenario, equipment or data will not the physically protected as today, thus privacy solutions will be a key element to protect business information from 3rd party. ...
... In a Cloud or IoT scenario, equipment or data will not the physically protected as today, thus privacy solutions will be a key element to protect business information from 3rd party. ...
Local area Network
... single VLAN, they can share resources and bandwidth as if they were connected to the same segment. The resources of other departments can be invisible to the marketing VLAN members, accessible to all, or accessible only to specified individuals, at the IT manager's discretion. ...
... single VLAN, they can share resources and bandwidth as if they were connected to the same segment. The resources of other departments can be invisible to the marketing VLAN members, accessible to all, or accessible only to specified individuals, at the IT manager's discretion. ...
ModuleONEandTWO
... Testing Connectivity To test connectivity, use the PING command in a DOS prompt. A PING is simply this: One user sends packets to another user requesting a reply for each to confirm the two users are connected. Pinging a URL can be used to test a computer’s internet connection. PING uses In ...
... Testing Connectivity To test connectivity, use the PING command in a DOS prompt. A PING is simply this: One user sends packets to another user requesting a reply for each to confirm the two users are connected. Pinging a URL can be used to test a computer’s internet connection. PING uses In ...
Security - NYU Stern School of Business
... • Public system design – It creates a false illusion if you think nobody knows you architecture ...
... • Public system design – It creates a false illusion if you think nobody knows you architecture ...
William Stallings Data and Computer Communications
... Developed by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
... Developed by the US Defense Advanced Research Project Agency (DARPA) for its packet switched network (ARPANET) Used by the global Internet No official model but a working one. Application layer Host to host or transport layer Internet layer Network access layer Physical layer ...
COEN 252 Computer Forensics
... Robust implementation of TCP/IP. SSH for remote access. Simple to disable services. Simple to run local firewall. ...
... Robust implementation of TCP/IP. SSH for remote access. Simple to disable services. Simple to run local firewall. ...
Security Issues in Mobile Ad
... [2] Secure Ad Hoc Networking, Panagiotis Papadimitratos, Virginia Polytechnic Institute and State University, ...
... [2] Secure Ad Hoc Networking, Panagiotis Papadimitratos, Virginia Polytechnic Institute and State University, ...
Organized, sophisticated supply chains (PII, financial
... Full packet capture at strategic network locations Network segmentation Team trained and focused on APT activity ...
... Full packet capture at strategic network locations Network segmentation Team trained and focused on APT activity ...
Throughput Scaling in Wideband Sensory Relay Networks
... - Often times disparate methods are used for cyber systems and physical systems, e.g., differential equations for power systems whereas graph models for communication networks - Interdependence is asymmetric and depends on local properties, e.g., different components of power grids have different Qo ...
... - Often times disparate methods are used for cyber systems and physical systems, e.g., differential equations for power systems whereas graph models for communication networks - Interdependence is asymmetric and depends on local properties, e.g., different components of power grids have different Qo ...
Introduction to Networking
... Servers- powerful computers dedicated to controlling all of the systems on the network. All networked computers are connected to the server in some way Printers- One of the reasons networks were developed was to make a single printer accessible by many different computers Computers- individual machi ...
... Servers- powerful computers dedicated to controlling all of the systems on the network. All networked computers are connected to the server in some way Printers- One of the reasons networks were developed was to make a single printer accessible by many different computers Computers- individual machi ...
61765 Computer Networks I
... Internet – an introduction: protocols, components and services, access methods, delays, layer model. Application layer: DNS, HTTP, SMTP, POP3, P2P protocols Transport layer: services and principles, UDP, flow and congestion control, TCP implementation. Network layer: introduction to routing, link st ...
... Internet – an introduction: protocols, components and services, access methods, delays, layer model. Application layer: DNS, HTTP, SMTP, POP3, P2P protocols Transport layer: services and principles, UDP, flow and congestion control, TCP implementation. Network layer: introduction to routing, link st ...
Overview of Knowledge Discovery in Databases Process and Data
... of early warning and response mechanisms and instruments for preventing violence, war, and state collapse, violent conflict. There is a need to develop many others and improve the existing ones for detecting important economic and social risks including hungers, epidemics, crimes, child abuses and u ...
... of early warning and response mechanisms and instruments for preventing violence, war, and state collapse, violent conflict. There is a need to develop many others and improve the existing ones for detecting important economic and social risks including hungers, epidemics, crimes, child abuses and u ...
Final bits of OS - Department of Computer Science
... • Result: a transport allowing hosts to send IP event notification messages to syslog servers – provides a very general message format – allowing processes and applications to use suitable conventions for ...
... • Result: a transport allowing hosts to send IP event notification messages to syslog servers – provides a very general message format – allowing processes and applications to use suitable conventions for ...