Availability Confidentiality Integrity
... compared to an attacker misusing the system – The stakeholders must be aware of this from the beginning Copyright © 2013-2016 – Curt Hill ...
... compared to an attacker misusing the system – The stakeholders must be aware of this from the beginning Copyright © 2013-2016 – Curt Hill ...
The AIG netAdvantage Suite® Coverage Highlights
... Punitive, Exemplary and Multiple Damages: Coverage provided where permissible by law. ...
... Punitive, Exemplary and Multiple Damages: Coverage provided where permissible by law. ...
Glossary of Terms, Abbreviations, and Acronyms
... unauthorized access. A firewall permits or denies computer traffic between networks with different security levels based upon a set of rules and other criteria. ...
... unauthorized access. A firewall permits or denies computer traffic between networks with different security levels based upon a set of rules and other criteria. ...
6 - University of South Florida St. Petersburg
... Installing Internetwork connections requires leased lines or other data channels; these connections are usually secured under requirements of formal service agreement When individuals seek to connect to organization’s network, more flexible option must be provided Options such as virtual priva ...
... Installing Internetwork connections requires leased lines or other data channels; these connections are usually secured under requirements of formal service agreement When individuals seek to connect to organization’s network, more flexible option must be provided Options such as virtual priva ...
Catholic University College of Ghana Fiapre
... of hardware and software devices as an interface to make these connections. • A bridge is a hardware and software combination used to connect the same types of networks • A router is a special computer that directs communicating messages when several networks are connected together. • A gateway is a ...
... of hardware and software devices as an interface to make these connections. • A bridge is a hardware and software combination used to connect the same types of networks • A router is a special computer that directs communicating messages when several networks are connected together. • A gateway is a ...
pptx - cse.sc.edu
... exact HTTP attack code, the target variable, the attackload used, the query sent to the database, etc. Allied to the high detection rate of the IDS, there is also a high false ...
... exact HTTP attack code, the target variable, the attackload used, the query sent to the database, etc. Allied to the high detection rate of the IDS, there is also a high false ...
CORE IMPACT
... connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all messages going between the two vic ...
... connections with the victims and relays messages between them, making them believe that they are talking directly to each other over a private connection, when in fact the entire conversation is controlled by the attacker. The attacker must be able to intercept all messages going between the two vic ...
Managing security risks and vulnerabilities
... review security device configuration data and detect configuration errors—all from a single location. It features an automated policy engine that can quantify the risk of exploits by calculating attack paths to vulnerable assets and evaluate actual and potential network traffic for compliance with p ...
... review security device configuration data and detect configuration errors—all from a single location. It features an automated policy engine that can quantify the risk of exploits by calculating attack paths to vulnerable assets and evaluate actual and potential network traffic for compliance with p ...
Whitepaper
... across virtually any business process, including: insider threat management; IP& trade secret protection; PII/PCI & PHI compliance, advanced cyber defense, export control restrictions, et al. HOW VERDASYS MSIP WORKS The Verdasys hosted service is built on Digital Guardian, the industry’s most proven ...
... across virtually any business process, including: insider threat management; IP& trade secret protection; PII/PCI & PHI compliance, advanced cyber defense, export control restrictions, et al. HOW VERDASYS MSIP WORKS The Verdasys hosted service is built on Digital Guardian, the industry’s most proven ...
IPSEC Presentation
... • A collection of protocols for securing Internet Protocol (IP) communications by encrypting and authenticating all IP packets1 • Progressive standard • Defined in RFC 2401 thru 2409 • Purpose: – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
... • A collection of protocols for securing Internet Protocol (IP) communications by encrypting and authenticating all IP packets1 • Progressive standard • Defined in RFC 2401 thru 2409 • Purpose: – To protect IP packets – To provide defense against network attacks 1: From wikipedia.org ...
W ADVICE FOR HEALTHCARE ORGANIZATIONS SEEKING TO FierceMarkets
... Despite the advent of the electronic medical record (EMR), clinical and non-clinical staff in most organizations continue to struggle with scattered patient data stored across legacy platforms. Depending on which patient data they need to access, this requires staff to log onto multiple systems, cre ...
... Despite the advent of the electronic medical record (EMR), clinical and non-clinical staff in most organizations continue to struggle with scattered patient data stored across legacy platforms. Depending on which patient data they need to access, this requires staff to log onto multiple systems, cre ...
Lazy Garbage Collection of Recovery State for Fault – Tolerant
... such as an array or a pointer in C Buffer overflow occurs when a program or process tries to store more data in a buffer than it was intended to hold Buffer overflows are exploited to change the flow of a program in execution Buffer overflows are by far the most commonly exploited bug on the linux/u ...
... such as an array or a pointer in C Buffer overflow occurs when a program or process tries to store more data in a buffer than it was intended to hold Buffer overflows are exploited to change the flow of a program in execution Buffer overflows are by far the most commonly exploited bug on the linux/u ...
Insert Title Here
... Electrostatic discharge protection Could be injected by attacker to cause failures Diodes, Transient Voltage Suppressor devices (i.e. Semtech) ...
... Electrostatic discharge protection Could be injected by attacker to cause failures Diodes, Transient Voltage Suppressor devices (i.e. Semtech) ...
The word “computer” comes from word compute, which means to
... 1. Speed : It can calculated millions of calculation in seconds. 2. Accuracy : Computer results are highly accurate. 3. Memory : Computers have a large amount of memory to hold a very large amount of data or information. 4. Programmed Intelligence: They are programmed in such a way that they can per ...
... 1. Speed : It can calculated millions of calculation in seconds. 2. Accuracy : Computer results are highly accurate. 3. Memory : Computers have a large amount of memory to hold a very large amount of data or information. 4. Programmed Intelligence: They are programmed in such a way that they can per ...
This article from Compton`s Family Encyclopedia was contributed by
... Most CPU chips and microprocessors have four functional sections: (1) the arithmetic/logic unit, which performs arithmetic operations (such as addition and subtraction) and logic operations (such as testing a value to see if it is true or false); (2) temporary storage locations, called registers, w ...
... Most CPU chips and microprocessors have four functional sections: (1) the arithmetic/logic unit, which performs arithmetic operations (such as addition and subtraction) and logic operations (such as testing a value to see if it is true or false); (2) temporary storage locations, called registers, w ...
Review For Exam notes
... Characterized by technical expertise and dogged persistence, not just a bag of tools ...
... Characterized by technical expertise and dogged persistence, not just a bag of tools ...
What is Beta Testing? - KV Institute of Management and Information
... Organizations standards, processes, systems, and plans are adequate to enable the organization ...
... Organizations standards, processes, systems, and plans are adequate to enable the organization ...
Network Security Parameter Analysis Using Simulation Approach
... [1] Ajay Sharma, “Performance Evaluation of AODV under Blackhole attack in MANET using NS2 simulator”, International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), Volume 1, Issue 8, October 2012 ISSN: 2278 – 1323 | [2] Alper T. M_zrak, “Detecting Malicious Packet Losse ...
... [1] Ajay Sharma, “Performance Evaluation of AODV under Blackhole attack in MANET using NS2 simulator”, International Journal of Advanced Research in Computer Engineering & Technology (IJARCET), Volume 1, Issue 8, October 2012 ISSN: 2278 – 1323 | [2] Alper T. M_zrak, “Detecting Malicious Packet Losse ...
rethink network availability
... Malware-Infected Devices – the New Threat to Network Availability Cyberthreats have become increasingly sophisticated over time, with attackers perfecting the techniques used to attract victims and using multiple application types to maximize their financial gains or inflict damage on network avail ...
... Malware-Infected Devices – the New Threat to Network Availability Cyberthreats have become increasingly sophisticated over time, with attackers perfecting the techniques used to attract victims and using multiple application types to maximize their financial gains or inflict damage on network avail ...
ch 13 Information Security
... Does the firewall support filtering at the highest layers of the OSI model, not just at the DataModified Linkby:and ...
... Does the firewall support filtering at the highest layers of the OSI model, not just at the DataModified Linkby:and ...
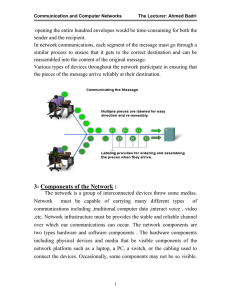
1-Introduction :
... Network Access Devices (Hubs, Bridges ,Switches, and wireless access points that call “Repeaters”) Internetworking Devices (Routers) Communication Servers and Modems Security Devices (Firewalls) The management of data as it flows through the network is also a role of the intermediary devices ...
... Network Access Devices (Hubs, Bridges ,Switches, and wireless access points that call “Repeaters”) Internetworking Devices (Routers) Communication Servers and Modems Security Devices (Firewalls) The management of data as it flows through the network is also a role of the intermediary devices ...
Social engineering
... developing the methods necessary to attack those targets successfully • Social engineering works because people are, for the most part, trusting and helpful • To counter social engineering, organizations must establish known security policies and conduct mandatory security training • Dumpster diving ...
... developing the methods necessary to attack those targets successfully • Social engineering works because people are, for the most part, trusting and helpful • To counter social engineering, organizations must establish known security policies and conduct mandatory security training • Dumpster diving ...
- Rajshahi University Alumni Association
... Overview of networking: Network architecture, planning and designing networks, Protocols, TCP/IP, IPv6, Agent. Ad hoc network architecture and protocols: Blue Tooth, IEEE802.11; Voice-over-IP, Combination of IP and ATM Technologies: Classical IP-over-ATM, LAN emulation. Concepts and principles of cl ...
... Overview of networking: Network architecture, planning and designing networks, Protocols, TCP/IP, IPv6, Agent. Ad hoc network architecture and protocols: Blue Tooth, IEEE802.11; Voice-over-IP, Combination of IP and ATM Technologies: Classical IP-over-ATM, LAN emulation. Concepts and principles of cl ...
Word Template
... useless to the Cybercriminal and protecting the organization from potential bot damage. ...
... useless to the Cybercriminal and protecting the organization from potential bot damage. ...