TL1 History - ManageEngine
... CMIP, SNMP is a machine-to-machine language. SNMP as the name implies is based on simple get-set messaging. With this simplicity comes lack of sophisticated operations capabilities. SNMP dominates the IP domain and is popular in applications where the management process is simple. Management of ente ...
... CMIP, SNMP is a machine-to-machine language. SNMP as the name implies is based on simple get-set messaging. With this simplicity comes lack of sophisticated operations capabilities. SNMP dominates the IP domain and is popular in applications where the management process is simple. Management of ente ...
Microsoft.Realtests.70-642.v2014-05-06.by
... Your network contains an Active Directory domain named contoso.com. The domain contains two Active Directory sites named Site1 and Site2. You have a domain-based Distributed File System (DFS) namespace named \\contoso.com\public that has a single namespace server located in Site1. You install anoth ...
... Your network contains an Active Directory domain named contoso.com. The domain contains two Active Directory sites named Site1 and Site2. You have a domain-based Distributed File System (DFS) namespace named \\contoso.com\public that has a single namespace server located in Site1. You install anoth ...
0110/0111/0115 Access Point
... Resuscitation Begin resuscitation immediately if someone is injured and stops breathing. Any delay could result in death. To work on or near high voltage, you should be familiar with approved industrial first aid methods. Energized equipment Never work on energized equipment unless authorized by a r ...
... Resuscitation Begin resuscitation immediately if someone is injured and stops breathing. Any delay could result in death. To work on or near high voltage, you should be familiar with approved industrial first aid methods. Energized equipment Never work on energized equipment unless authorized by a r ...
XTM 2 and 5 Series
... • What it is: – Unique, real time spam blocking service for Firebox X and XTM appliances – Partnered with Commtouch, an industry leader in spam prevention and mitigation ...
... • What it is: – Unique, real time spam blocking service for Firebox X and XTM appliances – Partnered with Commtouch, an industry leader in spam prevention and mitigation ...
RoamAbout 802.11 Wireless Networking Guide
... Before calling Cabletron Systems, please have the following information ready: ...
... Before calling Cabletron Systems, please have the following information ready: ...
Cisco IP SLA`s
... Cisco router to server • Threshold notifications when end point is not available What is the availability of a Network File System (NFS) server used to store business critical data from a remote site ? ...
... Cisco router to server • Threshold notifications when end point is not available What is the availability of a Network File System (NFS) server used to store business critical data from a remote site ? ...
Cisco PIX Firewall Command Reference
... All customers, partners, and resellers who have a valid Cisco service contract have complete access to the technical support resources on the Cisco TAC website. Some services on the Cisco TAC website require a Cisco.com login ID and password. If you have a valid service contract but do not have a lo ...
... All customers, partners, and resellers who have a valid Cisco service contract have complete access to the technical support resources on the Cisco TAC website. Some services on the Cisco TAC website require a Cisco.com login ID and password. If you have a valid service contract but do not have a lo ...
Networking 101 An Introduction to Networking
... done by sharing parts of existing computer systems, such as their printer or hard drive. How this is done depends a lot on the operating system of the computer that will be doing the sharing. We will address these tasks in the context of Microsoft Windows. Specifically we will look at printer sharin ...
... done by sharing parts of existing computer systems, such as their printer or hard drive. How this is done depends a lot on the operating system of the computer that will be doing the sharing. We will address these tasks in the context of Microsoft Windows. Specifically we will look at printer sharin ...
Chapter 3
... the TCP layer which uses two types of messages: Error-Reporting and Query • Query uses one of four types of messages, including Echo Request and Reply. • Ping combines the Echo Request and Reply function of ICMP with UDP in an IP packet to validate whether a node is functioning ...
... the TCP layer which uses two types of messages: Error-Reporting and Query • Query uses one of four types of messages, including Echo Request and Reply. • Ping combines the Echo Request and Reply function of ICMP with UDP in an IP packet to validate whether a node is functioning ...
RFC 3261+ Session Initiation Protocol (SIP)
... It is also an application-layer control (signaling) protocol for creating, modifying and terminating sessions with one or more participants. These sessions include Internet multimedia conferences, Internet telephone calls and multimedia distribution. Members in a session can communicate via multicas ...
... It is also an application-layer control (signaling) protocol for creating, modifying and terminating sessions with one or more participants. These sessions include Internet multimedia conferences, Internet telephone calls and multimedia distribution. Members in a session can communicate via multicas ...
IPv6 Primer
... Protocol -- ::0:5EFE:w.x.y.z prefix) • 6to4 (Tunnel Brokers – 3ffe or 2001 prefix) • Automatic 6to4 (Dynamic Tunnels – 2002 prefix) • Teredo and Silkroad (6to4 tunnelling over UDP) • NAT/PT (Network Address Translation/Protocol ...
... Protocol -- ::0:5EFE:w.x.y.z prefix) • 6to4 (Tunnel Brokers – 3ffe or 2001 prefix) • Automatic 6to4 (Dynamic Tunnels – 2002 prefix) • Teredo and Silkroad (6to4 tunnelling over UDP) • NAT/PT (Network Address Translation/Protocol ...
A Software Development Kit to exploit RINA
... Unifies networking and distributed computing: the network is a distributed application that provides IPC • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) bet ...
... Unifies networking and distributed computing: the network is a distributed application that provides IPC • 3 There is a single type of layer with programmable functions, that repeats as many times as needed by the network designers • 4 All layers provide the same service: communication (flows) bet ...
Segment Routing and Path Computation Element
... (MPLS) labels or as one or more IPv6 addresses. Where MPLS is used, SR does not have a requirement for the Label Distribution Protocol (LDP) and/or Resource Reservation Protocol – Traffic Engineering (RSVP-TE) transport signaling control plane. No state is held in the network with the exception of t ...
... (MPLS) labels or as one or more IPv6 addresses. Where MPLS is used, SR does not have a requirement for the Label Distribution Protocol (LDP) and/or Resource Reservation Protocol – Traffic Engineering (RSVP-TE) transport signaling control plane. No state is held in the network with the exception of t ...
LevelOne
... This printer server provides an Ethernet network port (10/100Mbps Ethernet) and one print port for printer. This printer server supports IPX/SPX, NetBEUI, TCP/IP and AppleTalk protocols. It is the best network printing solutions for various common network operating systems such as Windows 98SE/ME/20 ...
... This printer server provides an Ethernet network port (10/100Mbps Ethernet) and one print port for printer. This printer server supports IPX/SPX, NetBEUI, TCP/IP and AppleTalk protocols. It is the best network printing solutions for various common network operating systems such as Windows 98SE/ME/20 ...
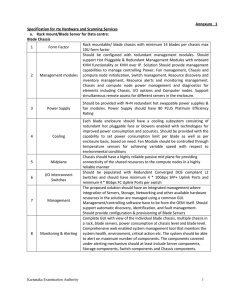
Annexure 1
... 1 client network and across all the controllers in the cluster. SAN: The backend SAN storage should be provided with dual controllers in Active-Active mode. Each controller should be with Single/Dual CPU 4-cores or above. The controller pair should not be more than 2U form factor. The controller pai ...
... 1 client network and across all the controllers in the cluster. SAN: The backend SAN storage should be provided with dual controllers in Active-Active mode. Each controller should be with Single/Dual CPU 4-cores or above. The controller pair should not be more than 2U form factor. The controller pai ...
LABEL SPACE REDUCTION IN GMPLS AND ALL-OPTICAL LABEL SWAPPING NETWORKS
... Burst Switching (OBS) as well) using All-Optical Label Swapping (AOLS) is closer to become a reality nowadays. With AOLS, OTN technologies will not only perform traffic switching completely optically at different granularity, but they will be capable of performing basic forwarding functions in the o ...
... Burst Switching (OBS) as well) using All-Optical Label Swapping (AOLS) is closer to become a reality nowadays. With AOLS, OTN technologies will not only perform traffic switching completely optically at different granularity, but they will be capable of performing basic forwarding functions in the o ...
Apuntes seguridad Redes Avanzadas 0708
... forwarded to gateways through tunnels. This allows any potential receiver in the Internet to create a dynamic tunnel to download multicast data streams. AMT is a transition strategy towards the full multicast-enabled Internet, a way to provide much more video content over the Internet in the near fu ...
... forwarded to gateways through tunnels. This allows any potential receiver in the Internet to create a dynamic tunnel to download multicast data streams. AMT is a transition strategy towards the full multicast-enabled Internet, a way to provide much more video content over the Internet in the near fu ...
Cisco IP SLA`s
... • Optimize IP business applications and services Voice over IP, Video, and VPN ...
... • Optimize IP business applications and services Voice over IP, Video, and VPN ...
Product Description
... Integrated networking application of the products ..................................... 125 ZXCTN’s application in mobile backhaul network ............................................. 125 ZXCTN’s application in Metro-E ....................................................................... 127 ...
... Integrated networking application of the products ..................................... 125 ZXCTN’s application in mobile backhaul network ............................................. 125 ZXCTN’s application in Metro-E ....................................................................... 127 ...
Single Packet IP Traceback in AS-level Partial Deployment Scenario
... away from the current AS). If the attack path cannot be reconstructed, it sends queries to its level-2 SPIE-deployed AS neighbors (2-hop away from the current AS), and so on. This process continues until the STM gets the origin of attack packet or it cannot trace anymore. The number of the levels to ...
... away from the current AS). If the attack path cannot be reconstructed, it sends queries to its level-2 SPIE-deployed AS neighbors (2-hop away from the current AS), and so on. This process continues until the STM gets the origin of attack packet or it cannot trace anymore. The number of the levels to ...
Chapter 2 Mobility Management for GPRS and UMTS
... the network to inform each other that the MS will not access the SGSN-based services. PS attach and detach are described in Section 2.5. Security procedures include authentication, user identity confidentiality (for example, P-TMSI reallocation and PTMSI signature) and ciphering. ...
... the network to inform each other that the MS will not access the SGSN-based services. PS attach and detach are described in Section 2.5. Security procedures include authentication, user identity confidentiality (for example, P-TMSI reallocation and PTMSI signature) and ciphering. ...
VESR90x Serial Server
... Connecting ESERV-1xT Serial Servers to Serial Devices ................................................................................... 8 Connecting the ESERV-11T......................................................................................................................................9 ...
... Connecting ESERV-1xT Serial Servers to Serial Devices ................................................................................... 8 Connecting the ESERV-11T......................................................................................................................................9 ...
6 Gaps between Legacy Networks and NGN
... Many of developing countries faced to improve their telecommunication infrastructures which are based on telephone service oriented, that is, PSTN/ISDN. Providing enhanced services such as Internet is one of the reasons but already passed life cycle of systems used in legacy networks, especially cir ...
... Many of developing countries faced to improve their telecommunication infrastructures which are based on telephone service oriented, that is, PSTN/ISDN. Providing enhanced services such as Internet is one of the reasons but already passed life cycle of systems used in legacy networks, especially cir ...
Document
... – Supporting route aggregation (summarization), also known as supernetting, where thousands of routes could be represented by a single route in the routing table. • Route aggregation also helps prevent route flapping on Internet routers using BGP. Flapping routes can be a serious concern with Intern ...
... – Supporting route aggregation (summarization), also known as supernetting, where thousands of routes could be represented by a single route in the routing table. • Route aggregation also helps prevent route flapping on Internet routers using BGP. Flapping routes can be a serious concern with Intern ...
DEPLOYMENT IPV6 OVER IPV4 NETWORK INFRASTRUCTURE Tien Dung Hoang
... 2.2 IPv6-addressing IPv6 addresses contains 128 bits, divides into 16 octets in binary number system or 8 groups in hexadecimal number system. Each octet has 4 hexadecimal, equal with 16 binary bits. When writing, each group of 4 octets (16 bits) is represented as unsigned integer which is written ...
... 2.2 IPv6-addressing IPv6 addresses contains 128 bits, divides into 16 octets in binary number system or 8 groups in hexadecimal number system. Each octet has 4 hexadecimal, equal with 16 binary bits. When writing, each group of 4 octets (16 bits) is represented as unsigned integer which is written ...