Delay-sensitive and multimedia communication in cognitive radio
... open research challenges for design of real-time CRSN transport protocols are explored. Finally, the paper is concluded in Section 5. 2. Real-time transport in cognitive radio sensor networks In order to realize real-time communication in CRSN, a reliable transport mechanism is imperative. Mainly tr ...
... open research challenges for design of real-time CRSN transport protocols are explored. Finally, the paper is concluded in Section 5. 2. Real-time transport in cognitive radio sensor networks In order to realize real-time communication in CRSN, a reliable transport mechanism is imperative. Mainly tr ...
Group Comm
... Less important CoAP group communications shall be authenticated by simply verifying that it originated from one of the group members (i.e. without explicitly identifying the source node). This is a weaker requirement (but simpler to implement) than REQ2. It shall also be possible to send unauthentic ...
... Less important CoAP group communications shall be authenticated by simply verifying that it originated from one of the group members (i.e. without explicitly identifying the source node). This is a weaker requirement (but simpler to implement) than REQ2. It shall also be possible to send unauthentic ...
Intro
... May include delivery by a broadband connection. For residential users, this type of service is often provided in conjunction with Video on Demand (VoD) and may be part of combined Internet services such as Web access and VoIP In businesses IPTV may be used to deliver television content over corporat ...
... May include delivery by a broadband connection. For residential users, this type of service is often provided in conjunction with Video on Demand (VoD) and may be part of combined Internet services such as Web access and VoIP In businesses IPTV may be used to deliver television content over corporat ...
Prolink Hurricane-9000P Manual
... SNR Margin: Amount of increased noise that can be tolerated while maintaining the designed BER (bit error rate). The SNR Margin is set by Central Office DSLAM. If the SNR Margin is increased, bit error rate performance will improve, but the data rate will decrease. Conversely, if the SNR Margin is d ...
... SNR Margin: Amount of increased noise that can be tolerated while maintaining the designed BER (bit error rate). The SNR Margin is set by Central Office DSLAM. If the SNR Margin is increased, bit error rate performance will improve, but the data rate will decrease. Conversely, if the SNR Margin is d ...
MPLS
... Each switch needs a table that contains the actions it is to perform when a given label arrives. The downstream end of a link needs to know what label values will be sent. This can be done by management action – directly equivalent to PVC’s in ATM. But this does not scale well. And there i ...
... Each switch needs a table that contains the actions it is to perform when a given label arrives. The downstream end of a link needs to know what label values will be sent. This can be done by management action – directly equivalent to PVC’s in ATM. But this does not scale well. And there i ...
Intrusion Detection Techniques for Mobile Wireless
... weaknesses in the systems due to design and programming errors, or various “socially engineered” penetration techniques. For example, even though they were first reported many years ago, exploitable “buffer overflow” security holes, which can lead to an unauthorized root shell, still exist in some r ...
... weaknesses in the systems due to design and programming errors, or various “socially engineered” penetration techniques. For example, even though they were first reported many years ago, exploitable “buffer overflow” security holes, which can lead to an unauthorized root shell, still exist in some r ...
(TAF) Migration towards NGN ITU/BDT Regional
... A large variety of country scenarios and transition strategies generate major differences in the economical results Planning to be performed per country and operator June 2005 ...
... A large variety of country scenarios and transition strategies generate major differences in the economical results Planning to be performed per country and operator June 2005 ...
Lecture 1: Course Introduction and Overview
... • Change is continuous and system designs should adapt – Not: look how stupid batch processing was – But: Made sense at the time ...
... • Change is continuous and system designs should adapt – Not: look how stupid batch processing was – But: Made sense at the time ...
A Hands-On Environment for Teaching Networks
... The Bad Need to modify clients Generally require major changes to datapath (e.g. PKI) Security dependent on path length Capability setup requires global rate-limiting infrastructure? SRUTI 2006 ...
... The Bad Need to modify clients Generally require major changes to datapath (e.g. PKI) Security dependent on path length Capability setup requires global rate-limiting infrastructure? SRUTI 2006 ...
ICMP - Febby Dian Anggraini
... way as any other data, they are subject to the same delivery failures This creates a scenario where error reports could generate more error reports, causing increased congestion on an already ailing network. For this reason, errors created by ICMP messages do not generate their own ICMP messages ...
... way as any other data, they are subject to the same delivery failures This creates a scenario where error reports could generate more error reports, causing increased congestion on an already ailing network. For this reason, errors created by ICMP messages do not generate their own ICMP messages ...
Flattened Butterfly Topology for On-Chip Networks
... its capacity [11], and directly influences the implementation costs, both in terms of on-chip resources and implementation complexity. In this paper, we explore the topology aspect of on-chip interconnection network and argue that highradix topologies such as the flattened butterfly are more costeff ...
... its capacity [11], and directly influences the implementation costs, both in terms of on-chip resources and implementation complexity. In this paper, we explore the topology aspect of on-chip interconnection network and argue that highradix topologies such as the flattened butterfly are more costeff ...
ppt
... 1. An identifier is hashed into a key 2. The key is sent to the local node 3. If data is not in local store, the request is forwarded to the best neighbor Repeat 3 with next best neighbor until data found, or request times out 4. If data is found, or hop-count reaches zero, return the data or error ...
... 1. An identifier is hashed into a key 2. The key is sent to the local node 3. If data is not in local store, the request is forwarded to the best neighbor Repeat 3 with next best neighbor until data found, or request times out 4. If data is found, or hop-count reaches zero, return the data or error ...
PowerPoint
... behaviour applied to a DS-compliant node to packets with same label (DS codepoint) • PHB Group: set of PHBs which can only meaningfully specified and implemented simultaneously (e.g. with common constraints on queue servicing and queue management). E.g. 4 PHB each associated to a different drop prio ...
... behaviour applied to a DS-compliant node to packets with same label (DS codepoint) • PHB Group: set of PHBs which can only meaningfully specified and implemented simultaneously (e.g. with common constraints on queue servicing and queue management). E.g. 4 PHB each associated to a different drop prio ...
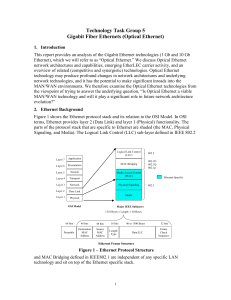
Gigabit Fiber Ethernets (Optical Ethernet)
... Ethernet (10/100/1000 Mbps) currently has a cost advantage that stems in large part from the volumes in production brought about by the use of this technology in the enterprise market. 10 GbE costs are not showing a significant cost advantage as yet, but this technology is very new and it has not ta ...
... Ethernet (10/100/1000 Mbps) currently has a cost advantage that stems in large part from the volumes in production brought about by the use of this technology in the enterprise market. 10 GbE costs are not showing a significant cost advantage as yet, but this technology is very new and it has not ta ...
Reviewing Traffic Classification - Sites personnels de TELECOM
... to perform Lawful Interception [6] of illegal or critical traffic, thus requiring them to know exactly the type of content transmitted over their networks. Traffic classification represents in fact the first step for activities such as anomaly detection for the identification of malicious use of net ...
... to perform Lawful Interception [6] of illegal or critical traffic, thus requiring them to know exactly the type of content transmitted over their networks. Traffic classification represents in fact the first step for activities such as anomaly detection for the identification of malicious use of net ...
Technical Report DSL Forum TR-059
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
... o Variable precedence arrangements – allowing some application’s traffic to take precedence over others. o Specific support for IP applications (e.g. IP-QoS and multicasting), o Support for new business models that can include more types of service providers, and o Support for these new service para ...
Performance Analysis of RIP and OSPF in Network Using
... At Peshawar location by using RIP protocol star topology is used as shown in figure. Two types of routers used access router and edge routers. Access routers directly attach with LAN network. LAN network send its outgoing traffic directly to access routers. Access routers attach with each other and ...
... At Peshawar location by using RIP protocol star topology is used as shown in figure. Two types of routers used access router and edge routers. Access routers directly attach with LAN network. LAN network send its outgoing traffic directly to access routers. Access routers attach with each other and ...
Chapter 10 Protocols for QoS Support
... domain with a node that is outside of the domain, either because it does not run MPLS, and/or because it is in a different domain. Note that if an LSR has a neighboring host that is not running MPLS, then that LSR is an MPLS edge node. ...
... domain with a node that is outside of the domain, either because it does not run MPLS, and/or because it is in a different domain. Note that if an LSR has a neighboring host that is not running MPLS, then that LSR is an MPLS edge node. ...
3rd Edition, Chapter 5
... sender generates packets every 20 msec during talk spurt. first packet received at time r ...
... sender generates packets every 20 msec during talk spurt. first packet received at time r ...
Microsoft Windows 2000? Router Configuration Guide
... guide, you can also configure the DHCP Relay Agent, configure IP multicast support, design and deploy network address translation, configure IPX packet filter, or design and deploy demand-dial routing. An additional routing benefit that will be discussed later is the configuration of IP packet filte ...
... guide, you can also configure the DHCP Relay Agent, configure IP multicast support, design and deploy network address translation, configure IPX packet filter, or design and deploy demand-dial routing. An additional routing benefit that will be discussed later is the configuration of IP packet filte ...
NETWORK LAN PLANNER
... computer networks may increase the organizational learning rate, which many authors declare as the only fundamental advantage in competition. Besides this major reason why any organization should not fail to have a computer network, there are other reasons as well: cost reduction by sharing hard- an ...
... computer networks may increase the organizational learning rate, which many authors declare as the only fundamental advantage in competition. Besides this major reason why any organization should not fail to have a computer network, there are other reasons as well: cost reduction by sharing hard- an ...
COPE
... This is best illustrated with an example. In Fig. 2, node B has 4 packets in its forwarding queue p 1 , p2 , p3 , and p4 . The table in Fig 2-a shows the next-hop of each of these packets. When the MAC signals to B to transmit, B picks packet p1 from the head of the queue to transmit it. Assume B kn ...
... This is best illustrated with an example. In Fig. 2, node B has 4 packets in its forwarding queue p 1 , p2 , p3 , and p4 . The table in Fig 2-a shows the next-hop of each of these packets. When the MAC signals to B to transmit, B picks packet p1 from the head of the queue to transmit it. Assume B kn ...
IPv6 Rationale and Features
... This processing at the application layer is called an application level gateway (ALG). Every NAT implementation includes a FTP ALG to enable this widely used protocol to traverse NATs. An ALG does not work if the application payload is encrypted or integrity protected by the application protocol or ...
... This processing at the application layer is called an application level gateway (ALG). Every NAT implementation includes a FTP ALG to enable this widely used protocol to traverse NATs. An ALG does not work if the application payload is encrypted or integrity protected by the application protocol or ...