... Wireless adapter cards used on laptop and desktop systems support the same protocols as Ethernet adapter cards, allowing wireless users to use the same applications as those used on a wired network. People use WLAN technology for many different purposes: Mobility - productivity increases when people ...
File - Information Technology Security
... others to read, such as birthdays, where they live, and their employment history. Attackers may steal this data and use it for malicious purposes. Users are generally trusting. Attackers often join a social networking site and pretend to be part of the network of users. After several days or weeks, ...
... others to read, such as birthdays, where they live, and their employment history. Attackers may steal this data and use it for malicious purposes. Users are generally trusting. Attackers often join a social networking site and pretend to be part of the network of users. After several days or weeks, ...
Chap4-NetworkLayer - Home
... • A site must have only one single connection to the global Internet through a router that runs the NAT software (i.e. NAT-enabled router). • The private network uses private addresses. The router uses one private address and one global address. – the private network is transparent to the rest of th ...
... • A site must have only one single connection to the global Internet through a router that runs the NAT software (i.e. NAT-enabled router). • The private network uses private addresses. The router uses one private address and one global address. – the private network is transparent to the rest of th ...
Metrics for Degree of Reordering in Packet Sequences
... sequences using frequencies of displacement values and reorder density function (RD) its normalized form. Displacement depends on the number of positions in the sequence a packet got delayed. Reorder density can also be viewed as the occupancy distribution of a hypothetical buffer at the receiver en ...
... sequences using frequencies of displacement values and reorder density function (RD) its normalized form. Displacement depends on the number of positions in the sequence a packet got delayed. Reorder density can also be viewed as the occupancy distribution of a hypothetical buffer at the receiver en ...
Maintenance ST - Common Criteria
... Asynchronous Transfer Mode (ATM) is a standardized digital data Asynchronous Transfer transmission technology. ATM is a cell-based switching technique Mode that uses asynchronous time division multiplexing. Border Gateway Protocol The Border Gateway Protocol (BGP) is the core routing protocol of the ...
... Asynchronous Transfer Mode (ATM) is a standardized digital data Asynchronous Transfer transmission technology. ATM is a cell-based switching technique Mode that uses asynchronous time division multiplexing. Border Gateway Protocol The Border Gateway Protocol (BGP) is the core routing protocol of the ...
An Introduction to SSH Secure Shell
... between the local and the remote hosts are encrypted, protecting the dat a sent between these machines. Secure shell provides s everal security improvements over the telnet, ftp and rlogin protocols. In particular, passwords are never sent over the network in a clear text format as t hey are when us ...
... between the local and the remote hosts are encrypted, protecting the dat a sent between these machines. Secure shell provides s everal security improvements over the telnet, ftp and rlogin protocols. In particular, passwords are never sent over the network in a clear text format as t hey are when us ...
chap2v3sem3 - Virtual Access
... RouterA(config)# router ospf 1 RouterA(config-router)# network 172.16.4.0 0.0.1.255 area 1 RouterA(config)# router ospf 10 RouterA(config-router)# network 172.16.4.0 0.0.0.255 area 0 RouterA(config-router)# network 172.16.5.0 0.0.0.255 area 0 RouterA(config)# router ospf 10 RouterA(config-router)# a ...
... RouterA(config)# router ospf 1 RouterA(config-router)# network 172.16.4.0 0.0.1.255 area 1 RouterA(config)# router ospf 10 RouterA(config-router)# network 172.16.4.0 0.0.0.255 area 0 RouterA(config-router)# network 172.16.5.0 0.0.0.255 area 0 RouterA(config)# router ospf 10 RouterA(config-router)# a ...
RIP V1
... RIP routes (routes for networks within the RIP routing domain) from "external" RIP routes, which may have been imported from an EGP or another IGP • Routers supporting protocols other than RIP should be configurable to allow the Route Tag to be configured for routes imported from different sources • ...
... RIP routes (routes for networks within the RIP routing domain) from "external" RIP routes, which may have been imported from an EGP or another IGP • Routers supporting protocols other than RIP should be configurable to allow the Route Tag to be configured for routes imported from different sources • ...
Computer Networks - Network Optiminization Research Group
... • All interior gateway protocol has to do is to move packets as efficiently as possible without worrying about politics. • Exterior gateway protocol routers have to worry about politics. – No transit traffic through certain ASes. – Traffic starting or ending at IBM should not transit Microsoft. ...
... • All interior gateway protocol has to do is to move packets as efficiently as possible without worrying about politics. • Exterior gateway protocol routers have to worry about politics. – No transit traffic through certain ASes. – Traffic starting or ending at IBM should not transit Microsoft. ...
Misbehaving TCP Receivers Can Cause Internet-Wide Congestion Collapse Rob Sherwood Bobby Bhattacharjee
... Two significant components of transport protocols are the flow and congestion control algorithms. These algorithms, by necessity, rely on remote feedback to determine the rate at which packets should be sent. This feedback can come directly from the network [18, 11] or, more typically, from end host ...
... Two significant components of transport protocols are the flow and congestion control algorithms. These algorithms, by necessity, rely on remote feedback to determine the rate at which packets should be sent. This feedback can come directly from the network [18, 11] or, more typically, from end host ...
Computer Networks(Routing and IPv6).
... • All interior gateway protocol has to do is to move packets as efficiently as possible without worrying about politics. • Exterior gateway protocol routers have to worry about politics. – No transit traffic through certain ASes. – Traffic starting or ending at IBM should not transit Microsoft. ...
... • All interior gateway protocol has to do is to move packets as efficiently as possible without worrying about politics. • Exterior gateway protocol routers have to worry about politics. – No transit traffic through certain ASes. – Traffic starting or ending at IBM should not transit Microsoft. ...
Resource-Freeing Attacks: Improve Your Cloud Performance (at Your Neighbor’s Expense)
... resources for their application by interfering with other customers’ use of them. A clear-cut example would be a malicious customer crashing co-resident VMs, but this requires knowledge of an exploitable vulnerability and would be easily detectable. We are interested in whether there exist more subt ...
... resources for their application by interfering with other customers’ use of them. A clear-cut example would be a malicious customer crashing co-resident VMs, but this requires knowledge of an exploitable vulnerability and would be easily detectable. We are interested in whether there exist more subt ...
Securing Wireless Systems
... accounts. During this time, wardialing became very popular. Programs like ToneLoc and Scan were popular. Hackers of the time would call ranges of phone numbers looking for systems with modems tied to them. Administrators fought back by limiting the hours that modems were on, started using callback s ...
... accounts. During this time, wardialing became very popular. Programs like ToneLoc and Scan were popular. Hackers of the time would call ranges of phone numbers looking for systems with modems tied to them. Administrators fought back by limiting the hours that modems were on, started using callback s ...
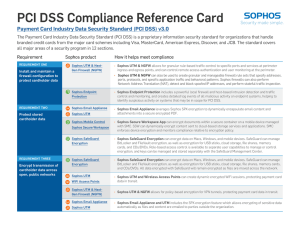
PCI DSS Compliance Reference Card
... ÌÌ Sophos Endpoint Protection includes a powerful local firewall and host-based intrusion detection and traffic control and monitoring, and creates detailed log events of all malicious activity on endpoint systems, helping to identify suspicious activity on systems that may be in scope for PCI DSS. ...
... ÌÌ Sophos Endpoint Protection includes a powerful local firewall and host-based intrusion detection and traffic control and monitoring, and creates detailed log events of all malicious activity on endpoint systems, helping to identify suspicious activity on systems that may be in scope for PCI DSS. ...
Underground Sensor Networks: Research Challenges
... Still most of the work are on “best effort” services. Strict delay guarantees is a difficult problem !! MMSPEED takes a probabilistic approach… more research needed !!! IFA’2007 ...
... Still most of the work are on “best effort” services. Strict delay guarantees is a difficult problem !! MMSPEED takes a probabilistic approach… more research needed !!! IFA’2007 ...
Computer networks CEN-330
... and received among network entities, and actions taken on msg transmission, receipt a human protocol and a computer network protocol: Hi ...
... and received among network entities, and actions taken on msg transmission, receipt a human protocol and a computer network protocol: Hi ...
Week_Nine
... • Larger address space: IPv6 addresses are 128 bits, compared to IPv4’s 32 bits. This larger addressing space allows more support for addressing hierarchy levels, a much greater number of addressable nodes, and simpler auto configuration of addresses. • Globally unique IP addresses: Every node can h ...
... • Larger address space: IPv6 addresses are 128 bits, compared to IPv4’s 32 bits. This larger addressing space allows more support for addressing hierarchy levels, a much greater number of addressable nodes, and simpler auto configuration of addresses. • Globally unique IP addresses: Every node can h ...
Systems and methods for forwarding data units in a communications
... In another implementation consistent with the principles of the invention, a method for transmitting data units from a ...
... In another implementation consistent with the principles of the invention, a method for transmitting data units from a ...
Week_Nine
... • Larger address space: IPv6 addresses are 128 bits, compared to IPv4’s 32 bits. This larger addressing space allows more support for addressing hierarchy levels, a much greater number of addressable nodes, and simpler auto configuration of addresses. • Globally unique IP addresses: Every node can h ...
... • Larger address space: IPv6 addresses are 128 bits, compared to IPv4’s 32 bits. This larger addressing space allows more support for addressing hierarchy levels, a much greater number of addressable nodes, and simpler auto configuration of addresses. • Globally unique IP addresses: Every node can h ...
DYNAMIC MANAGEMENT AND RESTORATION OF VIRTUAL PATHS IN BROADBAND NETWORKS
... for performing resource reservation, such as Asynchronous Transfer Mode (ATM) or MultiProtocol Label Switching (MPLS). Logical networks can be established by using Virtual Paths (VP) in ATM or Label Switched Paths (LSP) in MPLS, which we call generically Logical Paths (LP). The network users then us ...
... for performing resource reservation, such as Asynchronous Transfer Mode (ATM) or MultiProtocol Label Switching (MPLS). Logical networks can be established by using Virtual Paths (VP) in ATM or Label Switched Paths (LSP) in MPLS, which we call generically Logical Paths (LP). The network users then us ...
2011-02-3.presentation
... In this attack, a L2 attacker will be able to attain a full topology image of each one of the L1 areas. Similarly to the previous attack, the attacker will establish a virtual link with the PDIS of another L1 area in the network, causing it to believe that the attacker is a partitioned part of its a ...
... In this attack, a L2 attacker will be able to attain a full topology image of each one of the L1 areas. Similarly to the previous attack, the attacker will establish a virtual link with the PDIS of another L1 area in the network, causing it to believe that the attacker is a partitioned part of its a ...
Routing Protocol vs. Routed Protocol
... • Using the SPF tree, each router can independently determine the shortest path to every network. Distance vector routing protocols do not have a topological map of the network. • Routers implementing a distance vector routing protocol only have a list of networks, which includes the cost (distance) ...
... • Using the SPF tree, each router can independently determine the shortest path to every network. Distance vector routing protocols do not have a topological map of the network. • Routers implementing a distance vector routing protocol only have a list of networks, which includes the cost (distance) ...
Module 1. Introduction to Active Directory in Windows 2000
... Active Directory is organized into sections that permit storage for a very large number of objects. As a result, Active Directory can expand as an organization grows, so that an organization that has a single server with a few hundred objects can grow to having thousands of servers and millions of o ...
... Active Directory is organized into sections that permit storage for a very large number of objects. As a result, Active Directory can expand as an organization grows, so that an organization that has a single server with a few hundred objects can grow to having thousands of servers and millions of o ...
Pi: A Path Identification Mechanism to Defend against DDoS attacks
... then forced to drop incoming packets indiscriminately, and thus legitimate users experience service degradation or failure. – Server Memory Attack: In this attack, the attacker takes advantage of ambiguities in protocols to deplete the victim server’s memory. Ambiguities can range from the reservati ...
... then forced to drop incoming packets indiscriminately, and thus legitimate users experience service degradation or failure. – Server Memory Attack: In this attack, the attacker takes advantage of ambiguities in protocols to deplete the victim server’s memory. Ambiguities can range from the reservati ...
Catalyst 3560E-12D AR Messaging deck
... Cisco Network Assistant for centralized management of smaller networks CiscoWorks LAN Management Solution for larger branch networks Ease-of-use features; i.e., Cisco Smartports and Express Setup Auto QoS wizard ...
... Cisco Network Assistant for centralized management of smaller networks CiscoWorks LAN Management Solution for larger branch networks Ease-of-use features; i.e., Cisco Smartports and Express Setup Auto QoS wizard ...