FiOS Gateway USER GUIDE - Frontier Communications
... You have an option of saving the Wi-Fi settings as an image on your device by clicking the Save as Picture button. After you click Save as Picture to save your Wi-Fi settings as an image, click Apply to save the Wi-Fi changes to your Gateway. Important: If you are on a Wi-Fi device when setting up y ...
... You have an option of saving the Wi-Fi settings as an image on your device by clicking the Save as Picture button. After you click Save as Picture to save your Wi-Fi settings as an image, click Apply to save the Wi-Fi changes to your Gateway. Important: If you are on a Wi-Fi device when setting up y ...
VROOM: Virtual ROuters On the Move
... piece of equipment to another without any discernible impact, i.e., without requiring the router to be reconfigured, without disturbing the IP-level topology, without causing downtime and without triggering reconvergence of protocols in the logical topology. Further, we would like to not only migrat ...
... piece of equipment to another without any discernible impact, i.e., without requiring the router to be reconfigured, without disturbing the IP-level topology, without causing downtime and without triggering reconvergence of protocols in the logical topology. Further, we would like to not only migrat ...
Layer 2 Data Link Frame
... 2. Check for IOS boot system commands in startup-config file (NVRAM) If boot system commands in startup-config a. Run boot system commands in order they appear in startup-config to locate the IOS b If boot system commands fail, use default fallback sequence to locate the IOS (Flash, TFTP, ROM) 3. Lo ...
... 2. Check for IOS boot system commands in startup-config file (NVRAM) If boot system commands in startup-config a. Run boot system commands in order they appear in startup-config to locate the IOS b If boot system commands fail, use default fallback sequence to locate the IOS (Flash, TFTP, ROM) 3. Lo ...
Management Information Systems 6/e
... connect to the Internet Usually several ports to build a network for home computers or printers and share Internet connection ...
... connect to the Internet Usually several ports to build a network for home computers or printers and share Internet connection ...
Trading Structure for Randomness in Wireless Opportunistic Routing
... from the destination (which could potentially have transmitted at the same time as nodes close to the destination due to spatial reuse), cannot, since they have to wait for the nodes close to the destination to finish transmitting. Hence the scheduler has the side effect of preventing a flow from ex ...
... from the destination (which could potentially have transmitted at the same time as nodes close to the destination due to spatial reuse), cannot, since they have to wait for the nodes close to the destination to finish transmitting. Hence the scheduler has the side effect of preventing a flow from ex ...
JXTA Overview - 123SeminarsOnly.com
... creation of peers, peer groups and security primitives. • Service Layer. The Service layer includes the services that are not completely necessary for P2P networking, but are often used to make some tasks easier. • Application Layer. Implementations of integrated applications: i P2P instant messagin ...
... creation of peers, peer groups and security primitives. • Service Layer. The Service layer includes the services that are not completely necessary for P2P networking, but are often used to make some tasks easier. • Application Layer. Implementations of integrated applications: i P2P instant messagin ...
Napster and Gnutella - Department of Computer Science and
... Gnutella is a distributed network. It does not have a central server. A Gnutella host joins the network by first contacting another Gnutella host. It then sends file search messages to its neighbors, and the neighbors forward the message to other neighbors. A TTL (Time to Live) field ensures that th ...
... Gnutella is a distributed network. It does not have a central server. A Gnutella host joins the network by first contacting another Gnutella host. It then sends file search messages to its neighbors, and the neighbors forward the message to other neighbors. A TTL (Time to Live) field ensures that th ...
Powerpoint
... based on information provided by other routers in the network • routers communicate topology to each other via different protocols • routers then compute one or more next hops for each destination - trying to calculate the most optimal path ...
... based on information provided by other routers in the network • routers communicate topology to each other via different protocols • routers then compute one or more next hops for each destination - trying to calculate the most optimal path ...
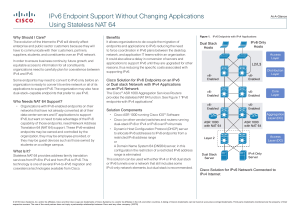
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
15. Interior Routing Protocols
... May also exist in hosts – If attached to single network with single router then not needed ...
... May also exist in hosts – If attached to single network with single router then not needed ...
18. Principles of Network Routing
... – applicable always when requisite set is available and the temporary status of the network does not deviate substantially from a steadystate ...
... – applicable always when requisite set is available and the temporary status of the network does not deviate substantially from a steadystate ...
Primitives for Active Internet Topology Mapping
... While dedicated platforms exist to perform topology measurements, e.g. [11, 19], these must balance induced measurement load against model fidelity. Unfortunately, in practice, such balancing results in multiple days worth of measurement to capture even an incomplete portion of the Internet. Employin ...
... While dedicated platforms exist to perform topology measurements, e.g. [11, 19], these must balance induced measurement load against model fidelity. Unfortunately, in practice, such balancing results in multiple days worth of measurement to capture even an incomplete portion of the Internet. Employin ...
SNMP Simple Network Management Protocol - CS-UCY
... • SNMPv2 was supposed to fix security problems, but effort derailed (The “c” in SNMPv2c stands for “community”). ...
... • SNMPv2 was supposed to fix security problems, but effort derailed (The “c” in SNMPv2c stands for “community”). ...
Study on a Fast OSPF Route Reconstruction Method Under Network
... to the DR. If the DR does not respond to 4 hello packets from a neighbor, a neighbor detects DR failure and all neighbors start to elect new DR among their own neighbors. The hello packet interval is 10 sec (Hello Interval, default value), hence it takes 40 sec (Router Dead Interval) for neighbors t ...
... to the DR. If the DR does not respond to 4 hello packets from a neighbor, a neighbor detects DR failure and all neighbors start to elect new DR among their own neighbors. The hello packet interval is 10 sec (Hello Interval, default value), hence it takes 40 sec (Router Dead Interval) for neighbors t ...
LevelOne WAP-6110 300Mbps Wireless PoE
... network via an RJ-45 interface, with LAN connectivity for both the Wireless Gateway and a co-located PC or other Ethernet-based device. ...
... network via an RJ-45 interface, with LAN connectivity for both the Wireless Gateway and a co-located PC or other Ethernet-based device. ...
PDF - Complete Book (2.8 MB)
... configuration that will be applied when the ASAv is launched. This initial configuration is placed into a text file named “day0-config” in a working directory you chose, and is manipulated into a day0.iso file that is mounted and read on first boot. At the minimum, the Day 0 configuration file must ...
... configuration that will be applied when the ASAv is launched. This initial configuration is placed into a text file named “day0-config” in a working directory you chose, and is manipulated into a day0.iso file that is mounted and read on first boot. At the minimum, the Day 0 configuration file must ...
plug and play server load balancing and global server load
... that can lead to optimal client-server response times [9]. Figure 3 illustrates the flows between the various network components that affect the GSLB decision process. ENABLING ANYCAST The Server Load Balancing Registration Protocol can be used to automate support for anycast technology. Since the ...
... that can lead to optimal client-server response times [9]. Figure 3 illustrates the flows between the various network components that affect the GSLB decision process. ENABLING ANYCAST The Server Load Balancing Registration Protocol can be used to automate support for anycast technology. Since the ...
Basic Network Security - Kenneth M. Chipps Ph.D. Home Page
... mapping of systems, services, or vulnerabilities • It is also known as information gathering, and, in most cases, it precedes another type of attack • Reconnaissance is similar to a thief casing a neighborhood for vulnerable homes to break into, such as an unoccupied residence, or one with easy-to-o ...
... mapping of systems, services, or vulnerabilities • It is also known as information gathering, and, in most cases, it precedes another type of attack • Reconnaissance is similar to a thief casing a neighborhood for vulnerable homes to break into, such as an unoccupied residence, or one with easy-to-o ...
Slide 1
... Frame size • Different networks use different sizes of frames • Many frames hold about 1500 bytes of data • The sending software breaks up large amounts of data into smaller chunks • The receiving station must then put the chunks back together in the proper order © 2012 The McGraw-Hill Companies, In ...
... Frame size • Different networks use different sizes of frames • Many frames hold about 1500 bytes of data • The sending software breaks up large amounts of data into smaller chunks • The receiving station must then put the chunks back together in the proper order © 2012 The McGraw-Hill Companies, In ...
router rip
... The first version of RIP is often called RIPv1 to distinguish it from RIP version 2 (RIPv2). However, both versions share many of the same features. When discussing features common to both versions, we will refer to RIP. When discussing features unique to each version, we will use RIPv1 and RIPv ...
... The first version of RIP is often called RIPv1 to distinguish it from RIP version 2 (RIPv2). However, both versions share many of the same features. When discussing features common to both versions, we will refer to RIP. When discussing features unique to each version, we will use RIPv1 and RIPv ...
Advanced Threat Protection For Dummies®, Blue Coat Systems
... Copyright © 2013 by John Wiley & Sons, Inc., Hoboken, New Jersey No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 1 ...
... Copyright © 2013 by John Wiley & Sons, Inc., Hoboken, New Jersey No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 1 ...
Document
... header. This simplifies and speeds up the routing process because most of the options do not need to be checked by routers. ...
... header. This simplifies and speeds up the routing process because most of the options do not need to be checked by routers. ...
An End-to-End Approach to Host Mobility Abstract {
... may be employed, such as manual assignment, the Dynamic Host Configuration Protocol (DHCP) [7], or an autoconfiguration protocol [34]. While IP addresses fundamentally denote a point of attachment in the Internet topology and say nothing about the identity of the host that may be connected to that a ...
... may be employed, such as manual assignment, the Dynamic Host Configuration Protocol (DHCP) [7], or an autoconfiguration protocol [34]. While IP addresses fundamentally denote a point of attachment in the Internet topology and say nothing about the identity of the host that may be connected to that a ...
A Performance Comparison of Multi-Hop Wireless Ad Hoc
... Each mobile node has a position and a velocity and moves around on a topography that is specified using either a digital elevation map or a flat grid. The position of a mobile node can be calculated as a function of time, and is used by the radio propagation model to calculate the propagation delay ...
... Each mobile node has a position and a velocity and moves around on a topography that is specified using either a digital elevation map or a flat grid. The position of a mobile node can be calculated as a function of time, and is used by the radio propagation model to calculate the propagation delay ...
Detecting Malicious SMB Activity Using Bro
... attacks using lateral movement techniques. There are documented examples that show the use of SMB in attacks that were not detected initially. In 2013, threat actors involved in the Ke3chang campaign infected computers on several European Ministries of Foreign Affairs (MFAs) networks and gathered ad ...
... attacks using lateral movement techniques. There are documented examples that show the use of SMB in attacks that were not detected initially. In 2013, threat actors involved in the Ke3chang campaign infected computers on several European Ministries of Foreign Affairs (MFAs) networks and gathered ad ...