Network Management Basics
... • Active attacks: masquerades (i.e., users pretending to be someone else, or • repeating, giving priority to or delaying message; (unauthorized access, viruses, Trojan horses, denial-of-service attacks). • Malfunctioning of resources. • Faulty or inappropriate behavior and incorrect response operati ...
... • Active attacks: masquerades (i.e., users pretending to be someone else, or • repeating, giving priority to or delaying message; (unauthorized access, viruses, Trojan horses, denial-of-service attacks). • Malfunctioning of resources. • Faulty or inappropriate behavior and incorrect response operati ...
Sentence Processing using a recurrent network
... and Verb are different classes except the “VERB-INTRAN”. Also, subclasses for NOUN are classified correctly, but some subclasses for VERB are mixed. This is related to the input example. 2. The network can recognize and predict the relative pronoun, “which”, but not “who” Why? Because the sentences ...
... and Verb are different classes except the “VERB-INTRAN”. Also, subclasses for NOUN are classified correctly, but some subclasses for VERB are mixed. This is related to the input example. 2. The network can recognize and predict the relative pronoun, “which”, but not “who” Why? Because the sentences ...
C06.InformationSecur.. - SIUE Computer Science
... Spam refers to unsolicited junk e-mail that makes up more than half of the amount of e-mail delivered. Concepts > Information Security > Internet Security > Spam ...
... Spam refers to unsolicited junk e-mail that makes up more than half of the amount of e-mail delivered. Concepts > Information Security > Internet Security > Spam ...
NAME: Computer Science 461 Midterm Exam March 30, 2009
... 4A. How many (datalink) networks are shown above? 4B. Just before the packet reaches bridge B1, what is its layer 2 destination? 4C. Just before the packet reaches bridge B2, what is its layer 2 source? 4D. Just after the packet leaves router R2, what is its layer 3 source? 4E. When H1 sends out an ...
... 4A. How many (datalink) networks are shown above? 4B. Just before the packet reaches bridge B1, what is its layer 2 destination? 4C. Just before the packet reaches bridge B2, what is its layer 2 source? 4D. Just after the packet leaves router R2, what is its layer 3 source? 4E. When H1 sends out an ...
Uw draadloze beveiligingscode
... What are three characteristics of CSMA/CD? (Choose three.) Devices can be configured with a higher transmission priority. A jam signal indicates that the collision has cleared and the media is not busy. A device listens and waits until the media is not busy before transmitting. The device with the e ...
... What are three characteristics of CSMA/CD? (Choose three.) Devices can be configured with a higher transmission priority. A jam signal indicates that the collision has cleared and the media is not busy. A device listens and waits until the media is not busy before transmitting. The device with the e ...
sockets
... Switch is a layer-2 device which is also used to connect all devices on a network so that they communicate with each other. However Switches for the first time do broadcast and afterwards it will do unicast data communication. Bridges work similar to Switches with the main difference in number of po ...
... Switch is a layer-2 device which is also used to connect all devices on a network so that they communicate with each other. However Switches for the first time do broadcast and afterwards it will do unicast data communication. Bridges work similar to Switches with the main difference in number of po ...
WP-U3: Content and Service Perspective
... • Two IP-based access networks with the similar infrastructure are presented. • More than one EN with the network sub-layer is located within one access network and they communicate with each other via signalling. • one AAA server within each network, which is located close to the ENs to help delive ...
... • Two IP-based access networks with the similar infrastructure are presented. • More than one EN with the network sub-layer is located within one access network and they communicate with each other via signalling. • one AAA server within each network, which is located close to the ENs to help delive ...
Network Coding for Large Scale Content Distribution
... – Typical content distribution solutions • CDN – Content Delivery Network • Placing dedicated equipment around the network • e.g. Akamai ...
... – Typical content distribution solutions • CDN – Content Delivery Network • Placing dedicated equipment around the network • e.g. Akamai ...
Babu Madhav Institute of Information Technology
... Write note on component of data communication Write advantages and uses of computer network. Write application area of Computer Network. How network is useful to a company? Describe the advantages and uses of network for people. Define Topology. Explain types of topology with its advantage and disad ...
... Write note on component of data communication Write advantages and uses of computer network. Write application area of Computer Network. How network is useful to a company? Describe the advantages and uses of network for people. Define Topology. Explain types of topology with its advantage and disad ...
Internetworking, or IP and Networking Basics
... – “connection oriented” – Management & control was centralized “New” ...
... – “connection oriented” – Management & control was centralized “New” ...
About the Presentations
... • Skills to acquire – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a netwo ...
... • Skills to acquire – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a netwo ...
About the Presentations - SUNYIT Computer Science
... • Skills to acquire – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a netwo ...
... • Skills to acquire – Installing, configuring, troubleshooting network server and client hardware and software – Understanding characteristics of transmission media – Understanding network design – Understanding network protocols – Understanding how users interact with network – Constructing a netwo ...
Chapter One
... – Traverse more than one LAN segment and more than one type of network through a router – Subnets • The individual networks joined together by routers in an internetwork ...
... – Traverse more than one LAN segment and more than one type of network through a router – Subnets • The individual networks joined together by routers in an internetwork ...
C08
... security is integrated and not an add-on, authentication of registration is included COA can be assigned via auto-configuration (DHCPv6 is one candidate), every node has address autoconfiguration no need for a separate FA, all routers perform router advertisement which can be used instead of the spe ...
... security is integrated and not an add-on, authentication of registration is included COA can be assigned via auto-configuration (DHCPv6 is one candidate), every node has address autoconfiguration no need for a separate FA, all routers perform router advertisement which can be used instead of the spe ...
A Guide to Windows 2000 Server
... Compatible with standard tools for analyzing network performance Parallel ability to use DHCP and WINS through a Windows 2000 server Ability for diverse networks and operating systems to communicate Compatible with Microsoft Windows Sockets ...
... Compatible with standard tools for analyzing network performance Parallel ability to use DHCP and WINS through a Windows 2000 server Ability for diverse networks and operating systems to communicate Compatible with Microsoft Windows Sockets ...
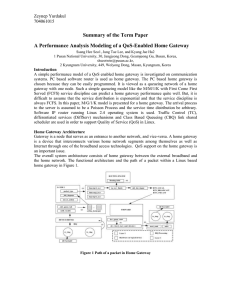
A performance analysis modeling of a QoS
... A simple performance model of a QoS enabled home gateway is investigated on communication systems. PC based software router is used as home gateway. The PC based home gateway is chosen because they can be easily programmed. It is viewed as a queueing network of a home gateway with one node. Such a s ...
... A simple performance model of a QoS enabled home gateway is investigated on communication systems. PC based software router is used as home gateway. The PC based home gateway is chosen because they can be easily programmed. It is viewed as a queueing network of a home gateway with one node. Such a s ...
OptiSwitch® 940 Series - MV Communications Co., Ltd.
... All RJ45 electrical interfaces enable remote copper-TDR cable diagnostics All SFP and XFP ports have SyncE support for mobile backhaul clock synchronization ...
... All RJ45 electrical interfaces enable remote copper-TDR cable diagnostics All SFP and XFP ports have SyncE support for mobile backhaul clock synchronization ...
Slide 1
... • The Demos require that you be logged in to the Virtual Technical College web site when you click on them to run. • To access and log in to the Virtual Technical College web site: – To access the site type www.vtc.com in the url window – Log in using the username: CIS 1140 or ATCStudent1 – Enter th ...
... • The Demos require that you be logged in to the Virtual Technical College web site when you click on them to run. • To access and log in to the Virtual Technical College web site: – To access the site type www.vtc.com in the url window – Log in using the username: CIS 1140 or ATCStudent1 – Enter th ...
Week 3 Topical Lecture
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
... If you use these slides (e.g., in a class) in substantially unaltered form, that you mention their source (after all, we’d like people to use our book!) If you post any slides in substantially unaltered form on a www site, that you note that they are adapted from (or perhaps identical to) our sl ...
Layers in OSI Model – Transport layer
... – Translation: the processes in two systems are usually exchanging information in the form of character strings, numbers, which should be changed to bit streams before being transmitted. It is responsible for interoperability between different encoding methods: sender-dependent format -> common form ...
... – Translation: the processes in two systems are usually exchanging information in the form of character strings, numbers, which should be changed to bit streams before being transmitted. It is responsible for interoperability between different encoding methods: sender-dependent format -> common form ...
3rd Edition: Chapter 1
... • Datagram network is not either connection-oriented or connectionless. • Internet provides both connection-oriented (TCP) and connectionless services (UDP) to apps. Introduction ...
... • Datagram network is not either connection-oriented or connectionless. • Internet provides both connection-oriented (TCP) and connectionless services (UDP) to apps. Introduction ...
Cobrador – Channeler brochure
... For more information about Cobrador and the Bouncer please visit us at www.cobrador.net or contact us at [email protected] ...
... For more information about Cobrador and the Bouncer please visit us at www.cobrador.net or contact us at [email protected] ...