Glossary of Networking Terms
... URL (Uniform Resource Locator) URL is an address that uniquely identifies a location on the Internet. . Generally, a URL specifies the connection protocol and a file name. The connection protocol can be telnet, ftp, gopher, etc., and for web pages, http is the usual protocol as in the fictitious URL ...
... URL (Uniform Resource Locator) URL is an address that uniquely identifies a location on the Internet. . Generally, a URL specifies the connection protocol and a file name. The connection protocol can be telnet, ftp, gopher, etc., and for web pages, http is the usual protocol as in the fictitious URL ...
3rd Edition: Chapter 4
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data ...
Pass4sure 920
... Study Material updated on regular basis. Questions, Answers and Study Guides are downloadable in PDF format. Audio Exams are downloadable in MP3 format. No authorization code required to open exam. ...
... Study Material updated on regular basis. Questions, Answers and Study Guides are downloadable in PDF format. Audio Exams are downloadable in MP3 format. No authorization code required to open exam. ...
What is Internet addressing
... messages one sends. In fact, for all programs that utilize the TCP/IP protocol, the sender IP address and destination IP address are required in order to establish communications and send data. Internet addresses are needed not only for unique enumeration of hosted interfaces, but also for routing p ...
... messages one sends. In fact, for all programs that utilize the TCP/IP protocol, the sender IP address and destination IP address are required in order to establish communications and send data. Internet addresses are needed not only for unique enumeration of hosted interfaces, but also for routing p ...
Linux+ Guide to Linux Certification
... A physical topology is the basic physical layout of a network; it does not specify devices, connectivity methods, or addresses on the network A bus topology consists of a single cable connecting all nodes on a network without intervening connectivity devices In a ring topology, each node is conn ...
... A physical topology is the basic physical layout of a network; it does not specify devices, connectivity methods, or addresses on the network A bus topology consists of a single cable connecting all nodes on a network without intervening connectivity devices In a ring topology, each node is conn ...
Merlin: A Language for Provisioning Network Resources
... including middlebox placement and bandwidth [22, 34, 54, 57], but they expose APIs that are either extremely simple (e.g., sequences of middleboxes) or not specified in detail. Overall, the challenges of managing real-world networks using existing SDN APIs remain unmet. This paper presents a new SDN ...
... including middlebox placement and bandwidth [22, 34, 54, 57], but they expose APIs that are either extremely simple (e.g., sequences of middleboxes) or not specified in detail. Overall, the challenges of managing real-world networks using existing SDN APIs remain unmet. This paper presents a new SDN ...
Presentation Title
... in the network. Inherent self-healing and load balancing capabilities ensure failsafe operations. ...
... in the network. Inherent self-healing and load balancing capabilities ensure failsafe operations. ...
Lecture 7
... Internet standards RFC: Request for comments IETF: Internet Engineering Task Force Introduction ...
... Internet standards RFC: Request for comments IETF: Internet Engineering Task Force Introduction ...
downloading
... U Up: The route is active. H Host: The route destination is a single host. G Gateway: Send anything for this destination on to this remote system, which will figure out from there where to send it. S Static: This route was configured manually, not automatically generated by the system. C Clone: Gene ...
... U Up: The route is active. H Host: The route destination is a single host. G Gateway: Send anything for this destination on to this remote system, which will figure out from there where to send it. S Static: This route was configured manually, not automatically generated by the system. C Clone: Gene ...
Paragon Boot Media Builder
... Before you launch Boot Media Builder please make sure you’ve got either Windows Automated Installation Kit (WAIK) or OEM Preinstallation Kit (OPK) installed in your system. Otherwise, you won’t be able to accomplish the operation. WAIK is a Microsoft’s proprietary tool and can be obtained from its D ...
... Before you launch Boot Media Builder please make sure you’ve got either Windows Automated Installation Kit (WAIK) or OEM Preinstallation Kit (OPK) installed in your system. Otherwise, you won’t be able to accomplish the operation. WAIK is a Microsoft’s proprietary tool and can be obtained from its D ...
Windows Server 2012 for Hosting Service Provider
... Lower-cost storage options Use of either storage area network (SAN) or direct attached storage (DAS) for pooled scenarios ...
... Lower-cost storage options Use of either storage area network (SAN) or direct attached storage (DAS) for pooled scenarios ...
4th Edition: Chapter 1
... Internet standards RFC: Request for comments IETF: Internet Engineering Task Force Introduction ...
... Internet standards RFC: Request for comments IETF: Internet Engineering Task Force Introduction ...
Technical Note TN # 85 Strong Motion Instrument Networks
... surveillance, common triggering and time synchronisation for the network is accomplished by GNC-CR, which as well displays the status of each sensor on-line. An optional Alarm Output can be defined in a way similar to selecting the event-recording trigger, thereby enabling the user to be informed im ...
... surveillance, common triggering and time synchronisation for the network is accomplished by GNC-CR, which as well displays the status of each sensor on-line. An optional Alarm Output can be defined in a way similar to selecting the event-recording trigger, thereby enabling the user to be informed im ...
Web Server Administration - Edinboro University of
... How do you connect to the Internet outside of school and what hardware and software is involved? From what you know so far what provides a better platform for web development, Linux or Windows? What is your reason? ...
... How do you connect to the Internet outside of school and what hardware and software is involved? From what you know so far what provides a better platform for web development, Linux or Windows? What is your reason? ...
Efficiently Discovering and Assessing
... The Ping Scan technique consists in sending ICMP echo request packets sequentially to every IP address on the network, relying on the response of each active device with an ICMP echo reply. The intrinsic problem is that blocking ICMP sweeps is rather easy, simply by not allowing ICMP echo requests i ...
... The Ping Scan technique consists in sending ICMP echo request packets sequentially to every IP address on the network, relying on the response of each active device with an ICMP echo reply. The intrinsic problem is that blocking ICMP sweeps is rather easy, simply by not allowing ICMP echo requests i ...
Slide 1
... • Intelligent routing of intrusion data throughout the network • Lightweight implementation ...
... • Intelligent routing of intrusion data throughout the network • Lightweight implementation ...
Chapter 1
... The attacker attempts to breach a web application. Common attacks of this type are SQL injection and Cross Site Scripting. ...
... The attacker attempts to breach a web application. Common attacks of this type are SQL injection and Cross Site Scripting. ...
Using NViz tool for Environmental Sensor Networks Anh-Vu Dinh-Duc , Non-member
... cannot verify with the change of application scenarios[1, 2]. Users have to modify and re-compile program or create new plug-in module for these tools if they want to use it in their applications. NetViewer[7], a universal visualization tool for WSN, has been introduced at GLOBECOM 2010. It allows u ...
... cannot verify with the change of application scenarios[1, 2]. Users have to modify and re-compile program or create new plug-in module for these tools if they want to use it in their applications. NetViewer[7], a universal visualization tool for WSN, has been introduced at GLOBECOM 2010. It allows u ...
COMMZOOM BROADBAND INTERNET SERVICE DISCLOSURES
... potential customer believes they have an unusual configuration, our customer service department will help determine if there is a compatibility problem. ...
... potential customer believes they have an unusual configuration, our customer service department will help determine if there is a compatibility problem. ...
Chapter 9
... • Each firewall generation can be implemented in several architectural configurations • Common architectural implementations – Packet filtering routers – Screened-host firewalls – Dual-homed host firewalls – Screened-subnet firewalls ...
... • Each firewall generation can be implemented in several architectural configurations • Common architectural implementations – Packet filtering routers – Screened-host firewalls – Dual-homed host firewalls – Screened-subnet firewalls ...
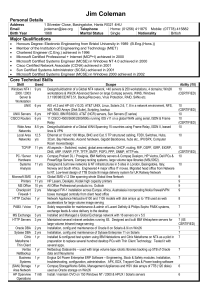
CV (Word) - OoCities
... run several large projects including Capacity Planning for 500 servers (UNIX and Windows), a "SWAT" team to analyse and fix an obscure and ongoing Windows Replication issue, and to design and write the test specification for CRM Performance testing. The Capacity Planning project involved managing a ...
... run several large projects including Capacity Planning for 500 servers (UNIX and Windows), a "SWAT" team to analyse and fix an obscure and ongoing Windows Replication issue, and to design and write the test specification for CRM Performance testing. The Capacity Planning project involved managing a ...
Internetworking
... – Echo: ping - send ICMP ECHO_REQUEST packets to network hosts – Redirect (from router to source host) – Destination unreachable (protocol, port, or host) – TTL exceeded (so datagrams don’t cycle forever) – Checksum failed – Reassembly failed – Cannot fragment ...
... – Echo: ping - send ICMP ECHO_REQUEST packets to network hosts – Redirect (from router to source host) – Destination unreachable (protocol, port, or host) – TTL exceeded (so datagrams don’t cycle forever) – Checksum failed – Reassembly failed – Cannot fragment ...
Securing Wireless Networks for HIPAA Compliance
... Information (PHI). Media Access Control (MAC) filtering is another method built into 802.11x devices; it works by blocking any traffic that is not originating from a wireless network card that has a trusted MAC address. This attempt at securing who can gain access to the wireless network can also be ...
... Information (PHI). Media Access Control (MAC) filtering is another method built into 802.11x devices; it works by blocking any traffic that is not originating from a wireless network card that has a trusted MAC address. This attempt at securing who can gain access to the wireless network can also be ...
Social Order and Network Security. Exploratory Research on TOR
... one. At the same time it is crucial to point out, that the new technology does not annihilate previous achievements, it rather adapts them, as the old one is still being used to fulfill the tasks for which the new one is either unsuitable or uneconomical (Bolter, 1990). And so, not only services, bu ...
... one. At the same time it is crucial to point out, that the new technology does not annihilate previous achievements, it rather adapts them, as the old one is still being used to fulfill the tasks for which the new one is either unsuitable or uneconomical (Bolter, 1990). And so, not only services, bu ...
Protecting IIoT Endpoints - Industrial Internet Consortium
... • One single (security) model for all locations • A single computer, even a device, can have several endpoints • Example Router: One LAN endpoint, one WAN endpoint • Frequently shared code/data between multiple endpoints • Endpoint and its communication are another model ...
... • One single (security) model for all locations • A single computer, even a device, can have several endpoints • Example Router: One LAN endpoint, one WAN endpoint • Frequently shared code/data between multiple endpoints • Endpoint and its communication are another model ...