ITE PC v4.0 Chapter 1
... Network security tools can be used to audit the network. By monitoring the network, an administrator can assess what type of information an attacker would be able to gather. For example, by attacking and flooding the CAM table of a switch, an administrator learn which switch ports are vulnerable ...
... Network security tools can be used to audit the network. By monitoring the network, an administrator can assess what type of information an attacker would be able to gather. For example, by attacking and flooding the CAM table of a switch, an administrator learn which switch ports are vulnerable ...
ITE PC v4.0 Chapter 1
... Network security tools can be used to audit the network. By monitoring the network, an administrator can assess what type of information an attacker would be able to gather. For example, by attacking and flooding the CAM table of a switch, an administrator learn which switch ports are vulnerable ...
... Network security tools can be used to audit the network. By monitoring the network, an administrator can assess what type of information an attacker would be able to gather. For example, by attacking and flooding the CAM table of a switch, an administrator learn which switch ports are vulnerable ...
Computer Science Illuminated, 3rd Edition
... True or False? An Internet service provider (ISP) is a company that provides other companies or individuals with access to the Internet. ...
... True or False? An Internet service provider (ISP) is a company that provides other companies or individuals with access to the Internet. ...
Tapestry: A Resilient Global-scale Overlay for Service - IC
... Internet developers are constantly proposing new and visionary distributed applications. These new applications have a variety of requirements for availability, durability, and performance. One technique for achieving these properties is to adapt to failures or changes in load through migration and ...
... Internet developers are constantly proposing new and visionary distributed applications. These new applications have a variety of requirements for availability, durability, and performance. One technique for achieving these properties is to adapt to failures or changes in load through migration and ...
DMXrfNet II and DMXNet II Card Option
... The Print Server makes IP requests at power-up, so before making a network connection to the printer consider how your IP addressing needs to be assigned. The IP addressing of the Internal Ethernet Print Server can be configured in one of two ways: Using a static IP Address or Using IP Discovery (DH ...
... The Print Server makes IP requests at power-up, so before making a network connection to the printer consider how your IP addressing needs to be assigned. The IP addressing of the Internal Ethernet Print Server can be configured in one of two ways: Using a static IP Address or Using IP Discovery (DH ...
Shall we apply paging technologies to proxy mobile IPv6?
... – which typically operates in a limited capacity • maintaining binding information has a strong influence on the limited resource. ...
... – which typically operates in a limited capacity • maintaining binding information has a strong influence on the limited resource. ...
Network Set-up and Operation for LC-XB100/XB200 (English)
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate ...
... This equipment has been tested and found to comply with the limits for a Class B digital device, pursuant to part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses and can radiate ...
PowerPoint Presentation - requirements for delivering MPLS
... – Last IETF, Yakov asked a question about the scalability of CTE LSPs ...
... – Last IETF, Yakov asked a question about the scalability of CTE LSPs ...
Machine-to-Machine (M2M) Gateway: Trusted and Connected
... • Security: Trusted boot platform and integrated security engine have single pass encryption/ message authentication for common security protocols (e.g., IPsec, SSL, etc.). Trust architecture platform helps protect against software intrusion and software cloning by incorporating advanced end-to-end ...
... • Security: Trusted boot platform and integrated security engine have single pass encryption/ message authentication for common security protocols (e.g., IPsec, SSL, etc.). Trust architecture platform helps protect against software intrusion and software cloning by incorporating advanced end-to-end ...
Routing - La Salle University
... the number of nodes increases, issues of scalability arise. For a network to “scale” ...
... the number of nodes increases, issues of scalability arise. For a network to “scale” ...
Fingerprinting Encrypted Tunnel Endpoints Vafa Dario Izadinia U
... are IPSec and SSL VPNs. IPSec VPN tunnels are established at Layer 3 of the OSI stack [32, 3] whereas SSL VPNs are referred to as Application-Layer or Layer 7 VPNs [92, 119]. When deploying VPN tunnels, the endpoints of which are frequently placed behind firewalls, effectively bypassing them; being ...
... are IPSec and SSL VPNs. IPSec VPN tunnels are established at Layer 3 of the OSI stack [32, 3] whereas SSL VPNs are referred to as Application-Layer or Layer 7 VPNs [92, 119]. When deploying VPN tunnels, the endpoints of which are frequently placed behind firewalls, effectively bypassing them; being ...
An Efficient Diffusion Load Balancing Algorithm in Distributed System
... no information is collected for the load transfer but the receiver may be far away from the sender and this may cause performance degradation due to the transfer cost. To overcome this problem, immediate neighbor state policy has been proposed which states that the receiver and sender would be adjac ...
... no information is collected for the load transfer but the receiver may be far away from the sender and this may cause performance degradation due to the transfer cost. To overcome this problem, immediate neighbor state policy has been proposed which states that the receiver and sender would be adjac ...
Scheduler
... QoS (Quality of Service) mechanisms are becoming increasingly popular in current networks. This is mainly due to the varied type of applications (such as voice, video, real-time streaming data) concurrently using the network. These applications typically require different levels of performance in te ...
... QoS (Quality of Service) mechanisms are becoming increasingly popular in current networks. This is mainly due to the varied type of applications (such as voice, video, real-time streaming data) concurrently using the network. These applications typically require different levels of performance in te ...
Jakab_Bratislava_KE_Zilina_Roadshow_2008
... – Project of training of computer network administrators (more than 3000) / Ministry of Education – Project of training of IT professionals – networking, Java, SAP, etc. (more than 160 participants) / Ministry of Labor ...
... – Project of training of computer network administrators (more than 3000) / Ministry of Education – Project of training of IT professionals – networking, Java, SAP, etc. (more than 160 participants) / Ministry of Labor ...
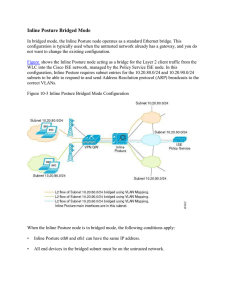
15360608-Inline Posture Bridged Mode
... traffic from entering the network by filtering source and destination IP addresses, transport protocols, and other variables, using the RADIUS protocol. After you create DACLs as named permission objects, add them to authorization profiles, which you then specify as the result of an authorization po ...
... traffic from entering the network by filtering source and destination IP addresses, transport protocols, and other variables, using the RADIUS protocol. After you create DACLs as named permission objects, add them to authorization profiles, which you then specify as the result of an authorization po ...
Título do Projeto
... changes since its inception. It presents issues difficult to solve, because of the barrier to deploy new features, the hardness to understand its behavior and dynamics, and complexity to identify and correct faults. The deployment on Internet architecture is a tough task, because the need to deploy ...
... changes since its inception. It presents issues difficult to solve, because of the barrier to deploy new features, the hardness to understand its behavior and dynamics, and complexity to identify and correct faults. The deployment on Internet architecture is a tough task, because the need to deploy ...
2| 1. Windows 2000 Active Directory
... global catalog servers in other domains. (2) The global catalog stores a full replica of all object attributes in the directory for its host domain. (3) The global catalog stores a partial replica of all object attributes contained in the directory for every domain in the forest. (4) The partial rep ...
... global catalog servers in other domains. (2) The global catalog stores a full replica of all object attributes in the directory for its host domain. (3) The global catalog stores a partial replica of all object attributes contained in the directory for every domain in the forest. (4) The partial rep ...
Network and Service Discovery in Distributed Environments
... a) employing converters b) employing photonic switches ...
... a) employing converters b) employing photonic switches ...
networkfundamental
... internal network over a shared infrastructure using dedicated connections. They allow access only to the employees of the enterprise. – Extranet VPNs – link business partners to the hq of the network over a shared infrastructure using dedicated connections. They allow access to users outside the ent ...
... internal network over a shared infrastructure using dedicated connections. They allow access only to the employees of the enterprise. – Extranet VPNs – link business partners to the hq of the network over a shared infrastructure using dedicated connections. They allow access to users outside the ent ...
18-MidIIRev_1 - Computer Science Division
... Reliable, in-order, and at most once delivery Messages can be of arbitrary length Provides multiplexing/demultiplexing to IP Provides congestion control and avoidance ...
... Reliable, in-order, and at most once delivery Messages can be of arbitrary length Provides multiplexing/demultiplexing to IP Provides congestion control and avoidance ...
6781_MPLS_Lecture2 - Computer Science and Engineering
... • Specifies how frequently the committed rate should be given to CRLSP ...
... • Specifies how frequently the committed rate should be given to CRLSP ...
client-side buffering and playout delay
... • grab video frame, add RTP headers, create UDP segments, send segments to UDP socket • include seq numbers and time stamps • client RTP provided for you ...
... • grab video frame, add RTP headers, create UDP segments, send segments to UDP socket • include seq numbers and time stamps • client RTP provided for you ...
DFL-600 User`s Guide for FW 2.11 and 2.30
... The DMZ port is used to allow computers and devices connected to this port to have more direct access to the Internet. This is useful for certain applications that may conflict with the firewall and Network Address Translation (NAT) features of the DFL-600. Computers and devices connected to the DM ...
... The DMZ port is used to allow computers and devices connected to this port to have more direct access to the Internet. This is useful for certain applications that may conflict with the firewall and Network Address Translation (NAT) features of the DFL-600. Computers and devices connected to the DM ...