SECURITY METRICS FOR ENTERPRISE INFORMATION SYSTEMS Interdisciplinarity – New Approaches and Perspectives
... 2. Standardization - Drivers and Results Security performance measurement by using standardized metrics gained increasingly interest during the last years with the help of guidelines, code of practices and standards accepted widely over the world, and with the efforts of international organizations ...
... 2. Standardization - Drivers and Results Security performance measurement by using standardized metrics gained increasingly interest during the last years with the help of guidelines, code of practices and standards accepted widely over the world, and with the efforts of international organizations ...
20061205-hopi-summerhillsobieskijohnson
... • With all TSC partners • Leadership from Tom Lehman of ISI for inter-domain control plane development • Leadership from Jerry Sobieski of MAX for TSC program direction ...
... • With all TSC partners • Leadership from Tom Lehman of ISI for inter-domain control plane development • Leadership from Jerry Sobieski of MAX for TSC program direction ...
SCORE: A Scalable Architecture for Implementing Resource
... Connection flooding: attacker sends as much data as the victim can handle, preventing other from acess – E.g., ping of death, smurf, syn flooding, etc. Traffic redirection: routers forward packets to wrong address – Corrupted router, incorrect DNS entry, etc. ...
... Connection flooding: attacker sends as much data as the victim can handle, preventing other from acess – E.g., ping of death, smurf, syn flooding, etc. Traffic redirection: routers forward packets to wrong address – Corrupted router, incorrect DNS entry, etc. ...
What is data communication? - Information Systems
... – This difference is apparent in the network oriented protocols only. ...
... – This difference is apparent in the network oriented protocols only. ...
Circumvention Defense Network (CDN)
... externally-hosted non-web servers used by various circumvention tools to proxy or re-route users’ web requests. We then correlate and filter these IP addresses against those shared with known legitimate websites to eliminate false positives. The results are synchronized with your onpremises iPrism a ...
... externally-hosted non-web servers used by various circumvention tools to proxy or re-route users’ web requests. We then correlate and filter these IP addresses against those shared with known legitimate websites to eliminate false positives. The results are synchronized with your onpremises iPrism a ...
ppt - Northwestern Networks Group
... “Online advertising is a $20 billion industry that is growing rapidly… It has become an integral and inseparable part of the World Wide Web” ...
... “Online advertising is a $20 billion industry that is growing rapidly… It has become an integral and inseparable part of the World Wide Web” ...
Multiprotocol Label Switching
... information in packets (packet switching) comprises a number of interrelated protocols - MPLS protocol suite is used to ensure that all packets in a particular flow take the same route over a backbone deployed by many telecommunication companies and service providers delivers QoS required to support ...
... information in packets (packet switching) comprises a number of interrelated protocols - MPLS protocol suite is used to ensure that all packets in a particular flow take the same route over a backbone deployed by many telecommunication companies and service providers delivers QoS required to support ...
Redundant Network Architecture
... Basic premise is to modularly upgrade software features and/or components without having to reboot the router Support from vendors still growing, and not supported on all platforms Initial support is on high-end platforms that support ...
... Basic premise is to modularly upgrade software features and/or components without having to reboot the router Support from vendors still growing, and not supported on all platforms Initial support is on high-end platforms that support ...
Top-Down Network Design
... network/subnet field and which part is the host field – The network/subnet portion of the mask is all 1s in binary. – The host portion of the mask is all 0s in binary. – Convert the binary expression back to dotted-decimal notation for entering into configurations. ...
... network/subnet field and which part is the host field – The network/subnet portion of the mask is all 1s in binary. – The host portion of the mask is all 0s in binary. – Convert the binary expression back to dotted-decimal notation for entering into configurations. ...
File: IIB ACCEPTABLE USE POLICY for Internet/Online
... networks also allow students and staff to participate in valuable educational projects. Unfortunately, the great potential of computer networks is not always used in a positive and constructive way. The Internet, in particular, has been subject to some abuses because it is simply a system of interco ...
... networks also allow students and staff to participate in valuable educational projects. Unfortunately, the great potential of computer networks is not always used in a positive and constructive way. The Internet, in particular, has been subject to some abuses because it is simply a system of interco ...
SYNCHRONY®
... intelligence resources. ST products were designed for this role, so partitioning capability is inherent in the networking elements. Network management ‘communities’ build on the partition capability to control the resource within individual partitions. ...
... intelligence resources. ST products were designed for this role, so partitioning capability is inherent in the networking elements. Network management ‘communities’ build on the partition capability to control the resource within individual partitions. ...
No Slide Title
... protocol allowing clients behind NAT (or multiple NATs) to find out its public address, the type of NAT it is behind and the internet side port associated by the NAT with a particular local port. This information is used to set up UDP communication between two hosts that are both behind NAT routers. ...
... protocol allowing clients behind NAT (or multiple NATs) to find out its public address, the type of NAT it is behind and the internet side port associated by the NAT with a particular local port. This information is used to set up UDP communication between two hosts that are both behind NAT routers. ...
―A Brief View of Computer Network Topology
... In Mesh network problems are easier to diagnose and Privacy between computers is maintained as messages travel along dedicated path. Mesh is avoided to uses in some cases because it requires the amount of cabling required is high and a large number of I/O (input/output) ports are required. G. Hybrid ...
... In Mesh network problems are easier to diagnose and Privacy between computers is maintained as messages travel along dedicated path. Mesh is avoided to uses in some cases because it requires the amount of cabling required is high and a large number of I/O (input/output) ports are required. G. Hybrid ...
1 - Cisco Support Community
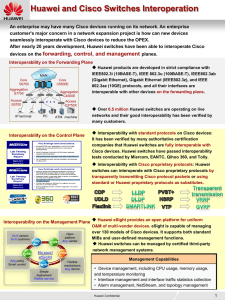
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
... Huawei &Cisco Interoperation Success Stories Turkey AveA's campus network project: Huawei S9700 interoperated with Cisco C6509E through OSPF and used BFD to speed up OSPF convergence. Huawei S5700 and Cisco 3560 ran VRRP to implement redundancy protection. S5700 and Cisco 2960/3560 ran standard MST ...
Neutral Net Neutrality
... What music do users want to zero rate? 66% of user preferences not in Music Freedom (November 2015) ...
... What music do users want to zero rate? 66% of user preferences not in Music Freedom (November 2015) ...
SLC 8000 Product Brief, Partners, A4
... of IT equipment from anywhere and at any time. Users can access the SLC 8000 device ports via Telnet/SSH, or a web browser-based console client without any proprietary software. Any IT asset that provides console or serial port management services can be managed remotely and locally with the same in ...
... of IT equipment from anywhere and at any time. Users can access the SLC 8000 device ports via Telnet/SSH, or a web browser-based console client without any proprietary software. Any IT asset that provides console or serial port management services can be managed remotely and locally with the same in ...
ELEN E6761 Fall `00
... Repeaters are used to connect multiple segments (up to 5); a repeater repeats the bits it hears on one interface to its other interfaces, ie a physical layer device only! ...
... Repeaters are used to connect multiple segments (up to 5); a repeater repeats the bits it hears on one interface to its other interfaces, ie a physical layer device only! ...
ccna1-ch10
... •Router uses path determination to decide to which port the packet must be sent toward its destination. Routing the packet. •Each router along the path is called Hop. ...
... •Router uses path determination to decide to which port the packet must be sent toward its destination. Routing the packet. •Each router along the path is called Hop. ...
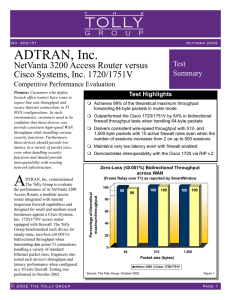
NetVanta 3200 Tolly Group Report
... Analysis User requirements for full linerate support are not limited to high-end connections on the LAN, but include WAN connections, as well. Remote connections via frame relay and Internet connectivity via PPP or frame relay continue to be in demand even with the growth of DSL and cable modem conn ...
... Analysis User requirements for full linerate support are not limited to high-end connections on the LAN, but include WAN connections, as well. Remote connections via frame relay and Internet connectivity via PPP or frame relay continue to be in demand even with the growth of DSL and cable modem conn ...
Network Research and Research Networks
... Home or corporate network has defense in depth Perimeter security (firewall) Intrusion management End system security ...
... Home or corporate network has defense in depth Perimeter security (firewall) Intrusion management End system security ...
Chap 6: Web Security - IUP Personal Websites
... • The 83 naming convention introduces a security vulnerability with some Web servers – Microsoft Internet Information Server 40 and other Web servers can inherit privileges from parent directories instead of the requested directory if the requested directory uses a long filename ...
... • The 83 naming convention introduces a security vulnerability with some Web servers – Microsoft Internet Information Server 40 and other Web servers can inherit privileges from parent directories instead of the requested directory if the requested directory uses a long filename ...
XML: Part - Houston Community College System
... • The 83 naming convention introduces a security vulnerability with some Web servers – Microsoft Internet Information Server 40 and other Web servers can inherit privileges from parent directories instead of the requested directory if the requested directory uses a long filename ...
... • The 83 naming convention introduces a security vulnerability with some Web servers – Microsoft Internet Information Server 40 and other Web servers can inherit privileges from parent directories instead of the requested directory if the requested directory uses a long filename ...
20061019-internet2intro
... bandwidths, for variable lengths of time • Capable of lightpath provisioning to the campus ...
... bandwidths, for variable lengths of time • Capable of lightpath provisioning to the campus ...
The Integration of Amateur Radio and 802.11
... come in through Amateur Radio and reach the TNC, then the gateway (Paclink Server) for transmission to the wireless clients. Transmission Control Protocol (TCP) at the Transport Layer TCP is the transport layer end to end protocol. TCP provides reliable, sequenced, and unduplicated delivery of bytes ...
... come in through Amateur Radio and reach the TNC, then the gateway (Paclink Server) for transmission to the wireless clients. Transmission Control Protocol (TCP) at the Transport Layer TCP is the transport layer end to end protocol. TCP provides reliable, sequenced, and unduplicated delivery of bytes ...