PDF
... was implemented in Cisco IOS releases 12.0(5)S and 12.0(7)T. The MSDP MIB describes managed objects that can be used to remotely monitor MSDP speakers using SNMP. The MSDP MIB module contains four scalar objects and three tables. The tables are the Requests table, the Peer Table, and the Source-Acti ...
... was implemented in Cisco IOS releases 12.0(5)S and 12.0(7)T. The MSDP MIB describes managed objects that can be used to remotely monitor MSDP speakers using SNMP. The MSDP MIB module contains four scalar objects and three tables. The tables are the Requests table, the Peer Table, and the Source-Acti ...
Slide 1
... Paragraph 3.4.1 of the Amended Annex requires that ATN shall either use International Organization for Standardization (ISO) communication standards for Open System Interconnection (ISO) or use the Internet Society (ISOC) communications standards for the Internet protocol Suite (IPS) ICAO circulat ...
... Paragraph 3.4.1 of the Amended Annex requires that ATN shall either use International Organization for Standardization (ISO) communication standards for Open System Interconnection (ISO) or use the Internet Society (ISOC) communications standards for the Internet protocol Suite (IPS) ICAO circulat ...
Understanding Simple Network Management Protocol
... Simple Network Management Protocol (SNMP), an application layer protocol, facilitates the exchange of management information among network devices, such as nodes, routers, and so on. As part of the TCP/IP protocol suite, SNMP enables administrators to remotely manage network performance, find and so ...
... Simple Network Management Protocol (SNMP), an application layer protocol, facilitates the exchange of management information among network devices, such as nodes, routers, and so on. As part of the TCP/IP protocol suite, SNMP enables administrators to remotely manage network performance, find and so ...
document
... effectively divide an OSPF domain into sub-domains. •A router in an area knows nothing detailed of topology outside of its own area. •Expressed in an Area ID of 32 bits, most often as decimal, but can be in dotted decimal like an IP address. •Area 0 must exist in all OSPF implementations and should ...
... effectively divide an OSPF domain into sub-domains. •A router in an area knows nothing detailed of topology outside of its own area. •Expressed in an Area ID of 32 bits, most often as decimal, but can be in dotted decimal like an IP address. •Area 0 must exist in all OSPF implementations and should ...
Trickle: A Userland Bandwidth Shaper for Unix-like Systems
... Furthermore, such users may not have administrative access to their operating system(s) or network infrastructure in order to apply traditional bandwidth shaping techniques. Some operating systems provide the ability to shape traffic of local origin (these are usually extensions to the router functi ...
... Furthermore, such users may not have administrative access to their operating system(s) or network infrastructure in order to apply traditional bandwidth shaping techniques. Some operating systems provide the ability to shape traffic of local origin (these are usually extensions to the router functi ...
VERTICAL HORIZON VH-2402-L3 FAST ETHERNET SWITCH
... 5. Develop a security scheme. Some subnets on the network need more security or should be isolated from the other subnets. IP or MAC filtering can be used. Also, one or more VLANs on the Layer 3 switch can be configured without an IP subnet – in which case, these VLANs will function as a layer 2 VLA ...
... 5. Develop a security scheme. Some subnets on the network need more security or should be isolated from the other subnets. IP or MAC filtering can be used. Also, one or more VLANs on the Layer 3 switch can be configured without an IP subnet – in which case, these VLANs will function as a layer 2 VLA ...
Sophos UTM Manager
... Get in control of all your Sophos gateway software and appliance installations worldwide instantly. Just install SUM, connect your Sophos gateway at SUM and you are done. SUM offers the same intuitive web-based GUI as known from all other Sophos products. Right from the start it helps you monitor th ...
... Get in control of all your Sophos gateway software and appliance installations worldwide instantly. Just install SUM, connect your Sophos gateway at SUM and you are done. SUM offers the same intuitive web-based GUI as known from all other Sophos products. Right from the start it helps you monitor th ...
Using RADIUS Protocol with Check Point Security
... Configuring SafeNet Authentication Service ......................................................................................................... 7 Synchronizing User Stores to SAS ................................................................................................................. 7 ...
... Configuring SafeNet Authentication Service ......................................................................................................... 7 Synchronizing User Stores to SAS ................................................................................................................. 7 ...
FS980M Datasheet
... Centralized Power with PoE+ ۼۼPoE+ provides centralized power connection to media, cameras, IP phones and wireless access points. ۼۼPoE+ reduces costs and offers greater flexibility with the capability to connect devices requiring more power (up to 30W), such as pan-tilt-zoom security cameras. ...
... Centralized Power with PoE+ ۼۼPoE+ provides centralized power connection to media, cameras, IP phones and wireless access points. ۼۼPoE+ reduces costs and offers greater flexibility with the capability to connect devices requiring more power (up to 30W), such as pan-tilt-zoom security cameras. ...
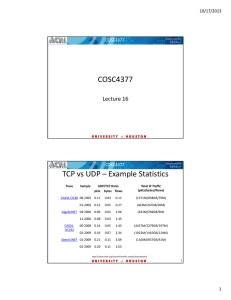
COSC4377 TCP vs UDP – Example Statistics
... growth ia coming from major ISPs within the U.S., as they roll out production IPv6 support to their end‐users, including Verizon Wireless, AT&T, and Comcast. This is on top of some ISPs in Europe and Asia that have had IPv6 deployed in production for a few years, as well as a long tail of thousan ...
... growth ia coming from major ISPs within the U.S., as they roll out production IPv6 support to their end‐users, including Verizon Wireless, AT&T, and Comcast. This is on top of some ISPs in Europe and Asia that have had IPv6 deployed in production for a few years, as well as a long tail of thousan ...
Performance Evaluation of Commodity iSCSI-based - ICS
... For instance, SCSI [7] and Fiber Channel [6] are among the most popular such interconnects and associated protocols. Although these approaches have been used and are still used extensively for building storage area networks, many problems have emerged due to changes in underlying technologies. First ...
... For instance, SCSI [7] and Fiber Channel [6] are among the most popular such interconnects and associated protocols. Although these approaches have been used and are still used extensively for building storage area networks, many problems have emerged due to changes in underlying technologies. First ...
Aalborg Universitet Adaptive Capacity Management in Bluetooth Networks Son, L.T.
... With the Internet and mobile wireless development, accelerated by high-speed and low cost VLSI device evolution, short range wireless communications have become more and more popular, especially Bluetooth. Bluetooth is a new short range radio technology that promises to be very convenient, low power ...
... With the Internet and mobile wireless development, accelerated by high-speed and low cost VLSI device evolution, short range wireless communications have become more and more popular, especially Bluetooth. Bluetooth is a new short range radio technology that promises to be very convenient, low power ...
IP Datagram - La Salle University
... Different physical networks have different MTUs. The MTU may also be set by the network administrator. If the source computer transmits packets that are too large for some network encountered on the way to its destination, then a router will break the packet into smaller packets (fragmenting). Ideal ...
... Different physical networks have different MTUs. The MTU may also be set by the network administrator. If the source computer transmits packets that are too large for some network encountered on the way to its destination, then a router will break the packet into smaller packets (fragmenting). Ideal ...
MPLS for Dummies
... • There are lot of IP people out there who still don’t like MPLS. • Many of the concepts are completely foreign to pure IP networks. • Many parts of MPLS smell like ATM, a technology which did a lot of things wrong as it was applied to the IP world. • Many aspects of MPLS could be called overly comp ...
... • There are lot of IP people out there who still don’t like MPLS. • Many of the concepts are completely foreign to pure IP networks. • Many parts of MPLS smell like ATM, a technology which did a lot of things wrong as it was applied to the IP world. • Many aspects of MPLS could be called overly comp ...
This chapter covers the following topics: • Characteristics of roaming
... With passive scanning, the client iterates through the channels slower than active scanning because it is listening for beacons that are sent out by APs at a set rate (usually 10 beacons per second). The client must dwell on each channel for a longer time duration to make sure it receives beacons fr ...
... With passive scanning, the client iterates through the channels slower than active scanning because it is listening for beacons that are sent out by APs at a set rate (usually 10 beacons per second). The client must dwell on each channel for a longer time duration to make sure it receives beacons fr ...
Impact of Delay in Voice over IP Services
... (b) Examine the packet size. Some systems are configured to use large voice packets or to pack multiple voice packets per IP packet. If this is the problem, use smaller packet sizes. ...
... (b) Examine the packet size. Some systems are configured to use large voice packets or to pack multiple voice packets per IP packet. If this is the problem, use smaller packet sizes. ...
Chapter 7
... The estimates di and vi are calculated for every received packet, although they are only used at the beginning of a talk spurt. For first packet in talk spurt, playout time is: ...
... The estimates di and vi are calculated for every received packet, although they are only used at the beginning of a talk spurt. For first packet in talk spurt, playout time is: ...
Chapter 3: Wireless Access Point Web Management
... The TPL-310AP 200Mbps Powerline AV Wireless N Access Point is an excellent solution that can be used to extend your network using your home or small office electrical wiring. In a home or small office building, use TPL-310AP adapters to link multiple locations without the need to run long Ethernet c ...
... The TPL-310AP 200Mbps Powerline AV Wireless N Access Point is an excellent solution that can be used to extend your network using your home or small office electrical wiring. In a home or small office building, use TPL-310AP adapters to link multiple locations without the need to run long Ethernet c ...
WR - Computer Science and Engineering
... • Distributed RAN architecture saves backhaul cost (less than half of the cost of existing architecture ) • Distributed RAN architecture supports 99.999% service-level availability compared to conventional network. In fact, full mesh is not required for realizing the 99.999% availability. Even parti ...
... • Distributed RAN architecture saves backhaul cost (less than half of the cost of existing architecture ) • Distributed RAN architecture supports 99.999% service-level availability compared to conventional network. In fact, full mesh is not required for realizing the 99.999% availability. Even parti ...
PDF
... attacks. They detect any network communication by the monitored host that violates the safety specification, whether it is the result of compromise by an outside attacker, misconfiguration, or even insider attacks. The trusted hardware platform and the attestation services protect against compromise ...
... attacks. They detect any network communication by the monitored host that violates the safety specification, whether it is the result of compromise by an outside attacker, misconfiguration, or even insider attacks. The trusted hardware platform and the attestation services protect against compromise ...
Campus LAN Reference Design
... Data Center, MAN/WAN, and Internet. Standard applications (web browsing and email), communication applications (unified communications, video conferencing) and other networking services (Wireless LANs, video surveillance, digital signage) all rely on the Campus LAN to function. All of these applicat ...
... Data Center, MAN/WAN, and Internet. Standard applications (web browsing and email), communication applications (unified communications, video conferencing) and other networking services (Wireless LANs, video surveillance, digital signage) all rely on the Campus LAN to function. All of these applicat ...
Motorola Outdoor System Planner
... supports user data applications, such as telemetry, web browsing, e-mail, video, and file synchronization. Application requirements enable the specification of throughput as part of the wireless network design. Initial understanding of the specific use cases and the applications that will be support ...
... supports user data applications, such as telemetry, web browsing, e-mail, video, and file synchronization. Application requirements enable the specification of throughput as part of the wireless network design. Initial understanding of the specific use cases and the applications that will be support ...
Understanding KaZaA
... process, a KaZaA-Lite ON first sends its query to the SN to which it is connected. We have learned from our measurement work that after receiving all the replies from its parent SN, the ON often disconnects and connects with a new SN, and resends the query to the new SN. During a specific search, th ...
... process, a KaZaA-Lite ON first sends its query to the SN to which it is connected. We have learned from our measurement work that after receiving all the replies from its parent SN, the ON often disconnects and connects with a new SN, and resends the query to the new SN. During a specific search, th ...
Serverless Network File Systems
... The recent introduction of switched local area networks such as ATM or Myrinet [Bode95] enables serverlessness by providing aggregate bandwidth that scales with the number of machines on the network. In contrast, shared media networks such as Ethernet or FDDI allow only one client or server to trans ...
... The recent introduction of switched local area networks such as ATM or Myrinet [Bode95] enables serverlessness by providing aggregate bandwidth that scales with the number of machines on the network. In contrast, shared media networks such as Ethernet or FDDI allow only one client or server to trans ...
Attack Detection and Defense Mechanisms
... The terms and conditions for using this software are described in the software license contained in the acknowledgment to your purchase order or, to the extent applicable, to any reseller agreement or end-user purchase agreement executed between you and Juniper Networks. By using this software, you ...
... The terms and conditions for using this software are described in the software license contained in the acknowledgment to your purchase order or, to the extent applicable, to any reseller agreement or end-user purchase agreement executed between you and Juniper Networks. By using this software, you ...