Review for Quiz-1 - Georgia Institute of Technology
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data “6to4 Translation” ...
... Priority: identify priority among datagrams in flow Flow Label: identify datagrams in same “flow.” (concept of“flow” not well defined). Next header: identify upper layer protocol for data “6to4 Translation” ...
Attacks to the IDS
... Gateway Intrusion Detection System – A network intrusion detection system which acts as a network gateway – Designed to stop malicious traffic and generate alerts on suspicious traffic – An “ideal” gateway IDS is able to stop all ...
... Gateway Intrusion Detection System – A network intrusion detection system which acts as a network gateway – Designed to stop malicious traffic and generate alerts on suspicious traffic – An “ideal” gateway IDS is able to stop all ...
Document
... It is relatively easy for a hacker to send a faked deauthenitcaiton or disaasoication frame to a wireless client, and to terminate its connection to the Wireless Access Point (WAP). Making it worse, a hacker could flood a wireless client with deauthentication or disassociatation frames. During the a ...
... It is relatively easy for a hacker to send a faked deauthenitcaiton or disaasoication frame to a wireless client, and to terminate its connection to the Wireless Access Point (WAP). Making it worse, a hacker could flood a wireless client with deauthentication or disassociatation frames. During the a ...
Overlay networks
... For the equivalent amount of multicast traffic, the sender needs much less processing power and bandwidth ...
... For the equivalent amount of multicast traffic, the sender needs much less processing power and bandwidth ...
EE 122: Computer Networks
... Security Implications of ICMP? • Attacker can cause host to accept an ICMP if the excerpt looks correct (assuming the host checks) – Must guess recent IP packet header & 8B of payload – All that really matters is source/destination addresses and ports ...
... Security Implications of ICMP? • Attacker can cause host to accept an ICMP if the excerpt looks correct (assuming the host checks) – Must guess recent IP packet header & 8B of payload – All that really matters is source/destination addresses and ports ...
module 3 Cyberpatriot Powerpoint
... – Transmission Control Protocol (TCP) – User Datagram Protocol (UDP) – Internet Control Message Protocol (ICMP) – Hypertext Transfer Protocol (HTTP) ...
... – Transmission Control Protocol (TCP) – User Datagram Protocol (UDP) – Internet Control Message Protocol (ICMP) – Hypertext Transfer Protocol (HTTP) ...
Document
... Link state algorithms • All the nodes know the state of the network • Some time to propagate changes • E.g. OSPF (Open Short Path First) ...
... Link state algorithms • All the nodes know the state of the network • Some time to propagate changes • E.g. OSPF (Open Short Path First) ...
Encrypting Wireless Data with VPN Techniques
... application that provides an authenticated, cryptographically secure TCP/IP tunnel between two computers. • SSH2 has the following features: – Public and private key authentication or the client’s username/password. – Public and private key data signing – Private key passphrase association – Data en ...
... application that provides an authenticated, cryptographically secure TCP/IP tunnel between two computers. • SSH2 has the following features: – Public and private key authentication or the client’s username/password. – Public and private key data signing – Private key passphrase association – Data en ...
02_TCPIP
... Note that both TCP and UDP are responsible only for sending data. They do not attempt to make any sense of the data itself--that is the responsibility of the next layer up Files are not responsible for the format or meaning of the data written to them--that’s the responsibility of the applications t ...
... Note that both TCP and UDP are responsible only for sending data. They do not attempt to make any sense of the data itself--that is the responsibility of the next layer up Files are not responsible for the format or meaning of the data written to them--that’s the responsibility of the applications t ...
Introduction to IP Routing
... Link State Routing Protocols Each link, the connected nodes and the metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
... Link State Routing Protocols Each link, the connected nodes and the metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
The Emerging Optical Control Plane
... The various abstraction mechanisms allow for a trade-off between information loss and scalability. Increased information loss helps to achieve scalability, but it can make certain functions more difficult, such as diversity or end-to-end latency calculation. On one end of the spectrum, “no abstract ...
... The various abstraction mechanisms allow for a trade-off between information loss and scalability. Increased information loss helps to achieve scalability, but it can make certain functions more difficult, such as diversity or end-to-end latency calculation. On one end of the spectrum, “no abstract ...
Introduction to IP Routing
... Link State Routing Protocols Each link, the connected nodes and the metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
... Link State Routing Protocols Each link, the connected nodes and the metric is flooded to all routers Each link up/down status change is incrementally flooded Each router re-computes the routing table in parallel using the common link state database OSPF is the main protocol in use today ...
IP: Datagram and Addressing
... LENGTH: gives length of option as it appears in IP datagram INTERNET ADDRESS: denotes the area reserved for internet addresses. This region is initially empty. Each router along the datagram path enters its address on the list POINTER: points to next available internet address slot in the option. Wh ...
... LENGTH: gives length of option as it appears in IP datagram INTERNET ADDRESS: denotes the area reserved for internet addresses. This region is initially empty. Each router along the datagram path enters its address on the list POINTER: points to next available internet address slot in the option. Wh ...
Methods of Attack
... Ping of death: a packet that is greater in size than the maximum allowed by IP (65,535 bytes) is sent to a device. This can cause the receiving system to crash. ...
... Ping of death: a packet that is greater in size than the maximum allowed by IP (65,535 bytes) is sent to a device. This can cause the receiving system to crash. ...
Mechanism for transitioning into and out of VBD mode
... 1 Gateways that only support Voice and Voice Band Data mode as per v.VBD This section describes the transitioning mechanism for an implementation that only supports VBD as per v.VBD and Voice, but does not support any relay mechanisms such as RFC2833, T.38 or V.150.1, nor VBD as per V.150.1. This me ...
... 1 Gateways that only support Voice and Voice Band Data mode as per v.VBD This section describes the transitioning mechanism for an implementation that only supports VBD as per v.VBD and Voice, but does not support any relay mechanisms such as RFC2833, T.38 or V.150.1, nor VBD as per V.150.1. This me ...
Smart Community - Support
... The information in this document may contain predictive statements including, without limitation, statements regarding the future financial and operating results, future product portfolio, new technology, etc. There are a number of factors that could cause actual results and developments to differ m ...
... The information in this document may contain predictive statements including, without limitation, statements regarding the future financial and operating results, future product portfolio, new technology, etc. There are a number of factors that could cause actual results and developments to differ m ...
Chapter 8 - Columbia CS
... This chapter is primarily based on the work of Alon’s group http://www.weizmann.ac.il/mcb/UriAlon/ The seminal publication: S Shen-Orr, R Milo, S Mangan & U Alon, ”Network motifs in the transcriptional regulation network of Escherichia coli.” Nature Genetics, 31:64-68 (2002). Pdf. ...
... This chapter is primarily based on the work of Alon’s group http://www.weizmann.ac.il/mcb/UriAlon/ The seminal publication: S Shen-Orr, R Milo, S Mangan & U Alon, ”Network motifs in the transcriptional regulation network of Escherichia coli.” Nature Genetics, 31:64-68 (2002). Pdf. ...
FAR: A Fault-avoidance Routing Method for Data Center Networks
... New Network architectures—MatrixDCN A MatrixDCN network can support 36,864 hosts using 3,840 48port switches ...
... New Network architectures—MatrixDCN A MatrixDCN network can support 36,864 hosts using 3,840 48port switches ...
Difficulties in Simulating the Internet
... the intended model. It is generally easier to verify the correctness of a mathematical analysis than it is to verify the correctness of the software implementation of an extensive and complex underlying model. For these reasons, Internet simulations are most useful as a tool for building understandi ...
... the intended model. It is generally easier to verify the correctness of a mathematical analysis than it is to verify the correctness of the software implementation of an extensive and complex underlying model. For these reasons, Internet simulations are most useful as a tool for building understandi ...
Topology Patterns of a Community Network: Guifi.net
... growing without major problems. Regarding the usage of Guifi.net, a few numbers of nodes, namely proxies, act as a gateway to give Internet, usually web only, access to the community network users. Without access to one of these proxies, Guifi.net users can still exploit the benefits of connectivity ...
... growing without major problems. Regarding the usage of Guifi.net, a few numbers of nodes, namely proxies, act as a gateway to give Internet, usually web only, access to the community network users. Without access to one of these proxies, Guifi.net users can still exploit the benefits of connectivity ...
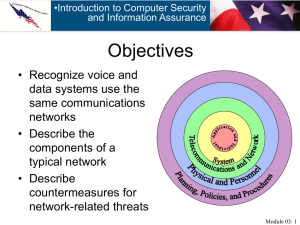
Chapter 6 Telecommunications and Networks
... networks are set up, how devices communicate, how problems are identified and corrected, and how components are connected. – Token ring protocols send an electronic signal that can carry both a message and an address around the ring quickly. ...
... networks are set up, how devices communicate, how problems are identified and corrected, and how components are connected. – Token ring protocols send an electronic signal that can carry both a message and an address around the ring quickly. ...
ArrowSpan_102407
... nodes on the mesh network via Mesh Manager unit. Once the Mesh Manager is updated with the new firmware: the new, updated firmware will propagate to every node on the mesh network. ...
... nodes on the mesh network via Mesh Manager unit. Once the Mesh Manager is updated with the new firmware: the new, updated firmware will propagate to every node on the mesh network. ...