Chapter 11 Interior Routing Protocols
... —Link value may be inversely proportional to capacity, proportional to current load, or some combination —May differ in different two directions ...
... —Link value may be inversely proportional to capacity, proportional to current load, or some combination —May differ in different two directions ...
Optimized Link State Routing Protocol for Ad Hoc Networks
... Route immediately available Minimize flooding by using MPR ...
... Route immediately available Minimize flooding by using MPR ...
Mobile Agents - Departament d`Electrònica, Informàtica i Automàtica
... Modularity in the sense that such a mechanism can be activated or deactivated without disrupting the normal network operation and also in the sense that this mechanism can be deployed only in several sections of a network. ...
... Modularity in the sense that such a mechanism can be activated or deactivated without disrupting the normal network operation and also in the sense that this mechanism can be deployed only in several sections of a network. ...
Module 1: Allocating IP Addressing by using Dynamic Host
... Relay agent forwards the DHCPDISCOVER message to the DHCP server Server sends a DHCPOFFER message to the DHCP relay agent Relay agent broadcasts the DHCPOFFER packet Client1 broadcasts a DHCPREQUEST packet ...
... Relay agent forwards the DHCPDISCOVER message to the DHCP server Server sends a DHCPOFFER message to the DHCP relay agent Relay agent broadcasts the DHCPOFFER packet Client1 broadcasts a DHCPREQUEST packet ...
PCI DSS Compliance Reference Card
... PCI DSS Compliance Reference Card Payment Card Industry Data Security Standard (PCI DSS) v3.0 The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, Maste ...
... PCI DSS Compliance Reference Card Payment Card Industry Data Security Standard (PCI DSS) v3.0 The Payment Card Industry Data Security Standard (PCI DSS) is a proprietary information security standard for organizations that handle branded credit cards from the major card schemes including Visa, Maste ...
... which results that we cannot start another FTP connection. Similarly, the Skype connection uses most of the link resources and leaves only 1Kbit/s for the FTP. From the above observations, we can see that both Skype and MSN do not have implemented the congestion control mechanism, i.e., they are not ...
18. Principles of Network Routing
... • all the links to the routers in the region 5/17 • one or few links to node[s] in the neighbor regions • Multilevel hierarchy possible • Iterregion routing may be distributed or centralized • Hierarchy optimization (Kleinrock) for N-router network: • optimal # of levels L = lnN • required # of tabl ...
... • all the links to the routers in the region 5/17 • one or few links to node[s] in the neighbor regions • Multilevel hierarchy possible • Iterregion routing may be distributed or centralized • Hierarchy optimization (Kleinrock) for N-router network: • optimal # of levels L = lnN • required # of tabl ...
TCP operations
... unreliable internetwork. This reliability is provided by adding services on top of IP. IP is connectionless and does not guarantee delivery of packets. The reliability of TCP is achieved by retransmitting data, which has been sent but not acknowledged by receiver within given time. Thus sending TCP ...
... unreliable internetwork. This reliability is provided by adding services on top of IP. IP is connectionless and does not guarantee delivery of packets. The reliability of TCP is achieved by retransmitting data, which has been sent but not acknowledged by receiver within given time. Thus sending TCP ...
How to connect an Epson POS printer with
... Important : If you are assigning a permanent IP address to the Epson printer, it is advised that dip switch 8 on the interface module by switched to off once the address has been set. Configuring the Computer (all types) Installing the Device Drivers for Windows If provided with a driver disk from B ...
... Important : If you are assigning a permanent IP address to the Epson printer, it is advised that dip switch 8 on the interface module by switched to off once the address has been set. Configuring the Computer (all types) Installing the Device Drivers for Windows If provided with a driver disk from B ...
module10-rip
... • Periodic Updates: Updates to the routing tables are sent at the end of a certain time period. A typical value is 90 seconds. • Triggered Updates: If a metric changes on a link, a router immediately sends out an update without waiting for the end of the update period. • Full Routing Table Update: M ...
... • Periodic Updates: Updates to the routing tables are sent at the end of a certain time period. A typical value is 90 seconds. • Triggered Updates: If a metric changes on a link, a router immediately sends out an update without waiting for the end of the update period. • Full Routing Table Update: M ...
Chapter 10: Circuit Switching and Packet Switching Switching
... • Nodes may connect to other nodes only, or to stations and other nodes • Node to node links usually multiplexed • Network is usually partially connected — Some redundant connections are desirable for ...
... • Nodes may connect to other nodes only, or to stations and other nodes • Node to node links usually multiplexed • Network is usually partially connected — Some redundant connections are desirable for ...
Transport Layer
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
The evolutionary origins of modularity References
... We investigate an alternate hypothesis that has been suggested, but heretofore untested, which is that modularity evolves not because it conveys evolvability, but as a byproduct from selection to reduce connection costs in a network (figure 1) [9,16]. Such costs include manufacturing connections, ma ...
... We investigate an alternate hypothesis that has been suggested, but heretofore untested, which is that modularity evolves not because it conveys evolvability, but as a byproduct from selection to reduce connection costs in a network (figure 1) [9,16]. Such costs include manufacturing connections, ma ...
PRP - Seamless redundancy for Industrial Ethernet scheme
... coming from different lanes are ignored. - for supervision, each node keeps a table of all other nodes in the network, based on observation of the network. This allows to detect nodes absence and bus errors at the same time. IEC SC65C WG15 © 2011 HK 2010-11-21 ...
... coming from different lanes are ignored. - for supervision, each node keeps a table of all other nodes in the network, based on observation of the network. This allows to detect nodes absence and bus errors at the same time. IEC SC65C WG15 © 2011 HK 2010-11-21 ...
69 Kyung Hee University Router Link LSA 70 Kyung Hee University
... We refer to information about each route received from a neighbor as R, which has only two piece of information : R.dest and R.cost. The next hop is not included in the received record because it is the source address of the sender ...
... We refer to information about each route received from a neighbor as R, which has only two piece of information : R.dest and R.cost. The next hop is not included in the received record because it is the source address of the sender ...
Chapter11 (Unicast Routing Protocols)
... We refer to information about each route received from a neighbor as R, which has only two piece of information : R.dest and R.cost. The next hop is not included in the received record because it is the source address of the sender ...
... We refer to information about each route received from a neighbor as R, which has only two piece of information : R.dest and R.cost. The next hop is not included in the received record because it is the source address of the sender ...
2-7 The Mathematics Models and an Actual Proof Experiment
... on intended packets (created in part from data on attacks detected by IDS). If traffic matches this information, the router will send a UDP packet to the manager. This packet includes, among other data, information on which router is to be monitored next. Based on UDP packets sent from the series of ...
... on intended packets (created in part from data on attacks detected by IDS). If traffic matches this information, the router will send a UDP packet to the manager. This packet includes, among other data, information on which router is to be monitored next. Based on UDP packets sent from the series of ...
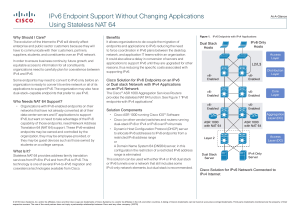
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
... © 2010 Cisco Systems, Inc. and/or its affiliates. Cisco and the Cisco Logo are trademarks of Cisco Systems, Inc. and/or its affiliates in the U.S. and other countries. A listing of Cisco's trademarks can be found at www.cisco.com/go/trademarks. Third-party trademarks mentioned are the property of th ...
ccna4-mod3-PPP
... Authentication, if used, takes place before the network layer protocol phase is entered. As part of this phase, LCP also allows for an optional link-quality determination test. – The link is tested to determine whether the link quality is good enough to bring up network layer protocols ...
... Authentication, if used, takes place before the network layer protocol phase is entered. As part of this phase, LCP also allows for an optional link-quality determination test. – The link is tested to determine whether the link quality is good enough to bring up network layer protocols ...
Implementation of Nested Virtual Laboratory System Jaakko Nurmi
... Service Provider Networks course in spring of 2015 liked the idea to have ...
... Service Provider Networks course in spring of 2015 liked the idea to have ...
Connectivity
... I.e. Multiplexing + indirection = virtualization We can “refer” to the virtual resource as if it were the physical resource. Pure magic ! Eg: ...
... I.e. Multiplexing + indirection = virtualization We can “refer” to the virtual resource as if it were the physical resource. Pure magic ! Eg: ...