ppt
... Wireless means communication without the use of wires other than antenna, which is the source of producing wireless waves. It is just uses the ether and the ground as place of wires. Radio exactly the same meaning which is the wireless transmission of signals, by modulation of electromagnetic waves ...
... Wireless means communication without the use of wires other than antenna, which is the source of producing wireless waves. It is just uses the ether and the ground as place of wires. Radio exactly the same meaning which is the wireless transmission of signals, by modulation of electromagnetic waves ...
PPT - Pages
... Sends (B7, B7, 0) Receives (B1, B1, 0) from B1 Sends (B7, B1, 1) “up” and “right” Receives (B5, B5, 0) - ignored Receives (B5, B1, 1) – suboptimal Continues forwarding the B1 messages forever to the “right” ...
... Sends (B7, B7, 0) Receives (B1, B1, 0) from B1 Sends (B7, B1, 1) “up” and “right” Receives (B5, B5, 0) - ignored Receives (B5, B1, 1) – suboptimal Continues forwarding the B1 messages forever to the “right” ...
Document
... the HIT Lab connected to the internet. They can communicate with computers globally. ...
... the HIT Lab connected to the internet. They can communicate with computers globally. ...
Games and the Impossibility of Realizable Ideal Functionality
... Denial-of-Service: cost related evaluation ...
... Denial-of-Service: cost related evaluation ...
INET01 - BNRG - University of California, Berkeley
... • Special about mobile wireless? – Exploitation of location and mobility – Resource constrained nature of wireless environment ...
... • Special about mobile wireless? – Exploitation of location and mobility – Resource constrained nature of wireless environment ...
Networking Concepts An Introduction to
... network or LAN. We will also briefly discuss routing as it pertains to sending traffic from a LAN out to the internet. Generally, packets on a LAN are transmitted using a technology called ethernet. While there are multiple ways to physically interconnect ethernet-capable devices, the format of ethe ...
... network or LAN. We will also briefly discuss routing as it pertains to sending traffic from a LAN out to the internet. Generally, packets on a LAN are transmitted using a technology called ethernet. While there are multiple ways to physically interconnect ethernet-capable devices, the format of ethe ...
IEEE 802.11 architecture
... its “cell”. The channel is selected from the set that is allowed in the ...
... its “cell”. The channel is selected from the set that is allowed in the ...
70-687 8.1 Lecture Slides Lesson 10
... network, you can use the Forget this network option if you are currently in range or the netsh wlan delete profile name=”” command if the network is no longer
within range of your computer.
• Adhoc mode is used when you configure a wireless network
adapter to bypass a WAP and connect d ...
... network, you can use the Forget this network option if you are currently in range or the netsh wlan delete profile name=”
eligible services list (esl) glossary - Universal Service Administrative
... The following Glossary contains a list of common terms that relate to the eligibility of products and services that applicants may request in the E-rate program. This Glossary should NOT be used by applicants to determine the eligibility of a service or product or to determine the E-rate category of ...
... The following Glossary contains a list of common terms that relate to the eligibility of products and services that applicants may request in the E-rate program. This Glossary should NOT be used by applicants to determine the eligibility of a service or product or to determine the E-rate category of ...
Wireless Network Elements[edit source | editbeta]
... save time from physical installation, and also creates mobility for devices connected to the network.[10] Wireless networks are simple and require as few as one single wireless access point connected directly to the Internet via a router.[8] ...
... save time from physical installation, and also creates mobility for devices connected to the network.[10] Wireless networks are simple and require as few as one single wireless access point connected directly to the Internet via a router.[8] ...
Six Degrees of Separation - Olympus High Mathematics
... and Randomness. Princeton University Press. ISBN 0-691-00541-9 Watts, D.J. (2004). Six Degrees: the science of a connected age. W.W. Norton ...
... and Randomness. Princeton University Press. ISBN 0-691-00541-9 Watts, D.J. (2004). Six Degrees: the science of a connected age. W.W. Norton ...
How to Prevent Unauthorized Access to Laser Beam Printers and
... a network without having to operate the machine directly. Users can access the Remote UI's portal page from a computer screen by entering the device's IP address into a Web browser. For information about how to use Remote UI, please see the user manual provided with the machine. ...
... a network without having to operate the machine directly. Users can access the Remote UI's portal page from a computer screen by entering the device's IP address into a Web browser. For information about how to use Remote UI, please see the user manual provided with the machine. ...
Lecture 3: Data Link Layer Security
... – E.g. giving them its own IP as default router – Result in all the traffic passing through the attacker’s computer ...
... – E.g. giving them its own IP as default router – Result in all the traffic passing through the attacker’s computer ...
network
... The transport layer takes the message from the application layer, packages them with additional tags (50+bytes including sequence #, …) into packets of a size compatible with the beneath network layer, and hands over to the network layer. The network layer will properly forward these packets to the ...
... The transport layer takes the message from the application layer, packages them with additional tags (50+bytes including sequence #, …) into packets of a size compatible with the beneath network layer, and hands over to the network layer. The network layer will properly forward these packets to the ...
CH06
... After reading this chapter, the reader should be able to: Understand the rationale for the existence of networks. Distinguish between the three types of networks: LANs, MANs, and WANs. Understand the OSI model and TCP/IP. List different connecting devices and the OSI layers in which each device oper ...
... After reading this chapter, the reader should be able to: Understand the rationale for the existence of networks. Distinguish between the three types of networks: LANs, MANs, and WANs. Understand the OSI model and TCP/IP. List different connecting devices and the OSI layers in which each device oper ...
E-Business - Computer Science and Information Systems Technical
... Describe four (4) services that are part of the TCP/IP protocol suite that would probably be implemented within a network centre to manage: • naming within legacy systems • automated issuing of IP Addresses • name to IP Address translation • private IP addressing ...
... Describe four (4) services that are part of the TCP/IP protocol suite that would probably be implemented within a network centre to manage: • naming within legacy systems • automated issuing of IP Addresses • name to IP Address translation • private IP addressing ...
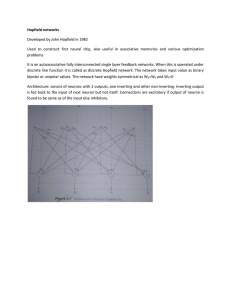
Hopfield networks
... Developed by John Hopfield in 1982 Used to construct first neural chip, also useful in associative memories and various optimization problems It is an autoassociative fully interconnected single layer feedback networks. When this is operated under discrete line function it is called as discrete Hopf ...
... Developed by John Hopfield in 1982 Used to construct first neural chip, also useful in associative memories and various optimization problems It is an autoassociative fully interconnected single layer feedback networks. When this is operated under discrete line function it is called as discrete Hopf ...
Module Title: Code: Level: Credits:
... 1. Have a good understanding of the OSI Reference Model and in particular have a good knowledge of Layers 1-3. 2. Analyze the requirements for a given organizational structure and select the most appropriate networking architecture and technologies; 3. Have a basic knowledge of the use of cryptograp ...
... 1. Have a good understanding of the OSI Reference Model and in particular have a good knowledge of Layers 1-3. 2. Analyze the requirements for a given organizational structure and select the most appropriate networking architecture and technologies; 3. Have a basic knowledge of the use of cryptograp ...
cis620-2
... IP Routing The Internet and other TCP/IP networks are connected by routers, which are devices that pass IP packets from one network to another. It is impractical to maintain addresses for all computers on an IP network with which the local computer communicates. Instead, a default gateway (ro ...
... IP Routing The Internet and other TCP/IP networks are connected by routers, which are devices that pass IP packets from one network to another. It is impractical to maintain addresses for all computers on an IP network with which the local computer communicates. Instead, a default gateway (ro ...
Basic Networking Concepts
... -Provides also 65,536 different ports. -Hence, every machine has two sets of 65,536 ports: one for TCP and the other for UDP. -Connectionless protocol, without any error detection facility. -Provides only support for data transmission from one end to the other, without any further verification. -The ...
... -Provides also 65,536 different ports. -Hence, every machine has two sets of 65,536 ports: one for TCP and the other for UDP. -Connectionless protocol, without any error detection facility. -Provides only support for data transmission from one end to the other, without any further verification. -The ...
Security Risks - Bannerman High School
... • Trojans are programs that pretend to be something like a game, a small application, a tool for maintaining your computer. • Once you run the Trojan program it will ...
... • Trojans are programs that pretend to be something like a game, a small application, a tool for maintaining your computer. • Once you run the Trojan program it will ...
A Scalable, Commodity Data Center Network Architecture
... FAT Tree based Solution • Connect end-host together using a fat tree topology – Infrastructure consist of cheap devices • Each port supports same speed as endhost ...
... FAT Tree based Solution • Connect end-host together using a fat tree topology – Infrastructure consist of cheap devices • Each port supports same speed as endhost ...
Chan
... Background Limitations of past systems o Highly susceptible to disconnection o Limited scalability Approach Use directional antenna arrays and electronic beamforming to: o Increase communication range without driving up power o Reduce interference and enable spatial frequency reuse ...
... Background Limitations of past systems o Highly susceptible to disconnection o Limited scalability Approach Use directional antenna arrays and electronic beamforming to: o Increase communication range without driving up power o Reduce interference and enable spatial frequency reuse ...
ppt
... the connection to be able to route back to that host/port. TCP source port field replaced with index into NAT box translation table which holds internal IP address and port number. Spring 2004 ...
... the connection to be able to route back to that host/port. TCP source port field replaced with index into NAT box translation table which holds internal IP address and port number. Spring 2004 ...








![Wireless Network Elements[edit source | editbeta]](http://s1.studyres.com/store/data/004984970_1-755673b30cfbd69af14b55cbbc12e8e5-300x300.png)