Approaches to Low Energy Networking
... Mobile access is becoming dominant access technology Any where, any time, any service Mobile is least energy efficient ~25 W/user @ 10 Mb/s PON is most efficient ...
... Mobile access is becoming dominant access technology Any where, any time, any service Mobile is least energy efficient ~25 W/user @ 10 Mb/s PON is most efficient ...
Internetwork Operation
... • Used by Routing Information Protocol (RIP) • Requires transmission of lots of information by each router — Distance vector to all neighbors — Contains estimated path cost to all networks in configuration — Changes take long time to propagate ...
... • Used by Routing Information Protocol (RIP) • Requires transmission of lots of information by each router — Distance vector to all neighbors — Contains estimated path cost to all networks in configuration — Changes take long time to propagate ...
Document
... Step 5: Configure NAT services on either router from the host PC or laptop to the mail server Step 6: Produce output validating NAT operations on the simulated network. a. Use the show ip nat statistics, show access-lists, and show ip nat translations commands to gather information about NAT’s opera ...
... Step 5: Configure NAT services on either router from the host PC or laptop to the mail server Step 6: Produce output validating NAT operations on the simulated network. a. Use the show ip nat statistics, show access-lists, and show ip nat translations commands to gather information about NAT’s opera ...
Lecture26 - The University of Texas at Dallas
... random IPs Establishes connection when it receives a discovery response packet Two hosts exchange list of peers Connects to those peers Runs a web server to publish /kx.exe, which is the Sinit binary Random IP scan generates a lot of ICMP 3 ...
... random IPs Establishes connection when it receives a discovery response packet Two hosts exchange list of peers Connects to those peers Runs a web server to publish /kx.exe, which is the Sinit binary Random IP scan generates a lot of ICMP 3 ...
Addressing the Network – IPv4
... Identify the historic method for assigning addresses and the issues associated with the method ...
... Identify the historic method for assigning addresses and the issues associated with the method ...
The Advanced Penetration Testing Boot Camp
... • Organizations of all sizes are finding that today’s mobile and collaborative workforce needs access to information inside and outside the office, along with the ability to share data with co-workers and partners. • Users are routinely using and sharing data without giving thought to confidentialit ...
... • Organizations of all sizes are finding that today’s mobile and collaborative workforce needs access to information inside and outside the office, along with the ability to share data with co-workers and partners. • Users are routinely using and sharing data without giving thought to confidentialit ...
4 Threats and Vulnerabilities Compared to Wired LANs
... transceiver used to generate interference, so the attacker has limited time before the transceiver is found. In the other hand the wireless LANs are not so vulnerable than the wired LANs to the other kind of denial of service attacks. For example the fixed LAN node can be isolated from the network b ...
... transceiver used to generate interference, so the attacker has limited time before the transceiver is found. In the other hand the wireless LANs are not so vulnerable than the wired LANs to the other kind of denial of service attacks. For example the fixed LAN node can be isolated from the network b ...
The Internet
... - IP - is responsible for moving packet of data from node to node. IP forwards each packet based on a four byte destination address (the IP number). - TCP - is responsible for verifying the correct delivery of data from client to server. Data can be lost in the intermediate network. TCP adds support ...
... - IP - is responsible for moving packet of data from node to node. IP forwards each packet based on a four byte destination address (the IP number). - TCP - is responsible for verifying the correct delivery of data from client to server. Data can be lost in the intermediate network. TCP adds support ...
TCP/IP protokolu kopa
... The Internet Society (ISOC). A group of volunteers who manages the standards of TCP/IP The Internet Architecture Board (IAB) is the technical advisory group of ISOC, and responsible for setting standards, publishing RFCs and overseeing the Internet Standards process. RFCs. A document written by anyo ...
... The Internet Society (ISOC). A group of volunteers who manages the standards of TCP/IP The Internet Architecture Board (IAB) is the technical advisory group of ISOC, and responsible for setting standards, publishing RFCs and overseeing the Internet Standards process. RFCs. A document written by anyo ...
acknowledgement
... The server calls the socket which creates an endpoint for the communications. The client also does the same by calling socket. The server then calls bind() to attach an unique IP address and a port number to which it is going to be listening for various clients. Then the server goes to accept stage ...
... The server calls the socket which creates an endpoint for the communications. The client also does the same by calling socket. The server then calls bind() to attach an unique IP address and a port number to which it is going to be listening for various clients. Then the server goes to accept stage ...
AGENDA
... THANK YOU… For more information: Visit Motorola Solutions and Zebra Technologies at Code Zone ...
... THANK YOU… For more information: Visit Motorola Solutions and Zebra Technologies at Code Zone ...
Web Server Administration
... Ports - The port number in a message helps identify individual connections between two addresses (like an phone extension) The combination of an address and port uniquely identifies a connection The inside address and port can be mapped to an outside address and port by the NAT ...
... Ports - The port number in a message helps identify individual connections between two addresses (like an phone extension) The combination of an address and port uniquely identifies a connection The inside address and port can be mapped to an outside address and port by the NAT ...
class15
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
... A: ICANN: Internet Corporation for Assigned Names and Numbers allocates addresses manages DNS assigns domain names, resolves disputes ...
3.1 Introduction to ARP
... 3.4 ARP Related Issues • ARP requests contain the device's IP/physical address pair, so the destination host and other hosts on the physical network can note them in their tables. • ARP cache to reduce ARP broadcast (high cost because all hosts need to process). Entries in the cache can be updated. ...
... 3.4 ARP Related Issues • ARP requests contain the device's IP/physical address pair, so the destination host and other hosts on the physical network can note them in their tables. • ARP cache to reduce ARP broadcast (high cost because all hosts need to process). Entries in the cache can be updated. ...
here
... Preferably has enough CPU, memory, and BW Preferably not behind firewall or NAT There are default supernodes Do signaling directly with other SNs Sometimes perform signaling and data transfer for SCs ...
... Preferably has enough CPU, memory, and BW Preferably not behind firewall or NAT There are default supernodes Do signaling directly with other SNs Sometimes perform signaling and data transfer for SCs ...
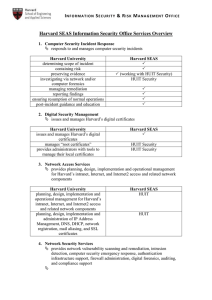
Harvard SEAS Information Security Office Services Overview
... attacks or network Denial of Service attack establishes configuration baseline and monitors infrastructure resources aggregates security event log data from infrastructure resources ...
... attacks or network Denial of Service attack establishes configuration baseline and monitors infrastructure resources aggregates security event log data from infrastructure resources ...
Lec02c-Interconnection Networks Part 2
... • Let s be the binary representation of the source and d be that of the destination processor. • The data traverses the link to the first switching node. If the most significant bits of s and d are the same, then the data is routed in pass-through mode by the switch else, it switches to crossover. • ...
... • Let s be the binary representation of the source and d be that of the destination processor. • The data traverses the link to the first switching node. If the most significant bits of s and d are the same, then the data is routed in pass-through mode by the switch else, it switches to crossover. • ...
CMSC 414 Computer (and Network) Security
... sessions (e.g., http traffic) – User does not need to be involved – The OS does not have to change, but applications do if they want to communicate securely – If TCP accepts a packet which is rejected by SSL, then TCP will reject the “correct” packet (detecting a replay) when it arrives! • SSL must ...
... sessions (e.g., http traffic) – User does not need to be involved – The OS does not have to change, but applications do if they want to communicate securely – If TCP accepts a packet which is rejected by SSL, then TCP will reject the “correct” packet (detecting a replay) when it arrives! • SSL must ...