Read the position paper
... challenge. A more realistic alternative is wireless connections. Options in this direction include using a 5G macro access network for relay/ backhaul of small cells. Another would be to use a separate wireless system. ...
... challenge. A more realistic alternative is wireless connections. Options in this direction include using a 5G macro access network for relay/ backhaul of small cells. Another would be to use a separate wireless system. ...
Network Routing Algorithms
... • With Link State Routing the routers are aware of network topology and the spanning tree can be computed • With Distance Vector Routing reverse path forwarding is used. – When a router receives a packet for a multicast group for which it has no subscribers (hosts or other routers), the router sends ...
... • With Link State Routing the routers are aware of network topology and the spanning tree can be computed • With Distance Vector Routing reverse path forwarding is used. – When a router receives a packet for a multicast group for which it has no subscribers (hosts or other routers), the router sends ...
CSE 524: Lecture 8 - Tamkang University
... • Tunnels – IP-in-IP encapsulation – Poor interaction with firewalls, multi-path routers, etc. ...
... • Tunnels – IP-in-IP encapsulation – Poor interaction with firewalls, multi-path routers, etc. ...
Study of Transport Layer Protocol for InterPlaNetary Internet
... The LTP engines must necessarily retain transmission status and retransmission resources for all of the sessions that might be set up. These LTP transmission state information need to be maintained for quite a long time since a long time may pass before LTP can be assured of transmission success. Th ...
... The LTP engines must necessarily retain transmission status and retransmission resources for all of the sessions that might be set up. These LTP transmission state information need to be maintained for quite a long time since a long time may pass before LTP can be assured of transmission success. Th ...
Transport layer
... name server to translate the mnemonic name used by humans to IP address. Transport layer: An important task of the transport layer is to accept messages from the application layer and to ensure that the messages are properly formatted for transmission over the internet. ...
... name server to translate the mnemonic name used by humans to IP address. Transport layer: An important task of the transport layer is to accept messages from the application layer and to ensure that the messages are properly formatted for transmission over the internet. ...
IP over InfiniBand: Connected Mode
... Service ID of: 1:Protocol or FF:0:0:0:0:0:0 – Protocol indicates IPv4 or IPv6 – FF indicates both IPv4 and IPv6 packets will use this connection – Private Data includes the IP address that was resolved ...
... Service ID of: 1:Protocol or FF:0:0:0:0:0:0 – Protocol indicates IPv4 or IPv6 – FF indicates both IPv4 and IPv6 packets will use this connection – Private Data includes the IP address that was resolved ...
Quality of Service in the Internet QoS Parameters
... cyclically for determining which one is allowed to send. The scanning is made byte by byte of the queues; if a packet is completely scanned, it is sent. Weighted means that certain queues get larger portions of the scanning time than others. Router with five packets for line O A ...
... cyclically for determining which one is allowed to send. The scanning is made byte by byte of the queues; if a packet is completely scanned, it is sent. Weighted means that certain queues get larger portions of the scanning time than others. Router with five packets for line O A ...
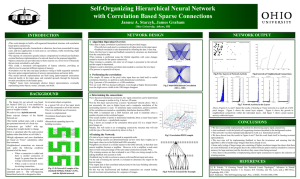
Self-Organizing Hierarchical Neural Network
... We have successfully implemented a method for determining sparse input connectivity. And combined it with the hybrid self-organizing structure described in the background section. The networks was then expanded and adjusted to work as a hierarchical network. We have shown from the results in Fig ...
... We have successfully implemented a method for determining sparse input connectivity. And combined it with the hybrid self-organizing structure described in the background section. The networks was then expanded and adjusted to work as a hierarchical network. We have shown from the results in Fig ...
Lecture 15: VOIP - Harding University
... • Voice providers are carrying more data than they are voice. ...
... • Voice providers are carrying more data than they are voice. ...
Lift-Net Brochure - Integrated Display Systems, Inc.
... • Multiple banks, even multiple buildings of different equipment on the same screen. All banks visible from any PC on the network. Telephone and LAN connection available. • Real-time display of opening, closing and dwell time. ...
... • Multiple banks, even multiple buildings of different equipment on the same screen. All banks visible from any PC on the network. Telephone and LAN connection available. • Real-time display of opening, closing and dwell time. ...
Overview - LIA - Laboratory of Advanced Research on Computer
... The consequence was e big effort that developed in two directions, initially antithetic: 1) The integration in the telephone switches of features providing communication capabilities also to IT equipment, besides the voice ones; 2) The birth of the data networks: LAN, IBM SNA, geographical packet ne ...
... The consequence was e big effort that developed in two directions, initially antithetic: 1) The integration in the telephone switches of features providing communication capabilities also to IT equipment, besides the voice ones; 2) The birth of the data networks: LAN, IBM SNA, geographical packet ne ...
ECE/CS 4984: Lecture 1
... ■ CDMA systems (many of today’s mobile wireless systems) are typically interference-constrained ...
... ■ CDMA systems (many of today’s mobile wireless systems) are typically interference-constrained ...
Final MCQ CS610
... A computer attached to a given network can only communicate with other computers attached to the same network. Is this a problem with multiple networks? True False The term self-identifying is used for Classful IP addresses because the class of the address can be computed from the address_______ ...
... A computer attached to a given network can only communicate with other computers attached to the same network. Is this a problem with multiple networks? True False The term self-identifying is used for Classful IP addresses because the class of the address can be computed from the address_______ ...
other transport layer protocols for ad hoc wireless networks
... network path Based on the feedback information received from the intermediate nodes, the TCP sender changes its state to the persist state, congestion control state, or the retransmit state. When an intermediate node finds that the network is partitioned, then the TCP sender state is changed to ...
... network path Based on the feedback information received from the intermediate nodes, the TCP sender changes its state to the persist state, congestion control state, or the retransmit state. When an intermediate node finds that the network is partitioned, then the TCP sender state is changed to ...
MULTOPS - The University of Texas at Dallas
... destination addresses matching such prefixes might defeat the attack, though it may also impose “collateral damage” by dropping legitimate packets. In attackeroriented mode, MULTOPS determines the addresses of attackers by looking for prefixes for which R(P ) is less than some threshold. Dropping pa ...
... destination addresses matching such prefixes might defeat the attack, though it may also impose “collateral damage” by dropping legitimate packets. In attackeroriented mode, MULTOPS determines the addresses of attackers by looking for prefixes for which R(P ) is less than some threshold. Dropping pa ...
LIFETIME WARRANTY WWW.COMNET.NET TECH SUPPORT
... Includes all of the security features of the Standard Security version, plus: Identity Management and Authentication Proxy Access (APA) NERC-CIP-5 defines the important requirement for network security protection of remote and unattended facilities. The capability of identifying the user and creatin ...
... Includes all of the security features of the Standard Security version, plus: Identity Management and Authentication Proxy Access (APA) NERC-CIP-5 defines the important requirement for network security protection of remote and unattended facilities. The capability of identifying the user and creatin ...
PPT Version
... • New applications and new network designs require accurate time and/or frequency • Accurate = ~50ppb frequency and 1-10us Time. • Transmitting time and/or frequency at these accuracies over a PSN – is a hard (but solvable) problem – is not addressed by any of the existing IETF WGs ...
... • New applications and new network designs require accurate time and/or frequency • Accurate = ~50ppb frequency and 1-10us Time. • Transmitting time and/or frequency at these accuracies over a PSN – is a hard (but solvable) problem – is not addressed by any of the existing IETF WGs ...
Our Brochure - Basic Commerce and Industries
... for Routing and Message throughput • SNMP monitoring & control capabilities • Turn-key solutions for easy drop-in operation in customer environments ...
... for Routing and Message throughput • SNMP monitoring & control capabilities • Turn-key solutions for easy drop-in operation in customer environments ...
Contact network structure and risk of infection
... We have identified a number of network centrality measures that may be useful predictors of individuals’ risk of infection during outbreaks of disease in naive populations. In the example investigated here, the degree centrality performed as well as, or better than, other measures. This has importan ...
... We have identified a number of network centrality measures that may be useful predictors of individuals’ risk of infection during outbreaks of disease in naive populations. In the example investigated here, the degree centrality performed as well as, or better than, other measures. This has importan ...
RF Handheld Testers Guarantee Traffic Stability Under
... return loss in the field. Return loss is a measure of the signal reflection characteristics of the cable and antenna system. In S-parameter terms, it is referred to as an S11 measurement. To make the measurement, the handheld CAT (e.g., the Agilent N9330B) uses a signal generator to generate a swept R ...
... return loss in the field. Return loss is a measure of the signal reflection characteristics of the cable and antenna system. In S-parameter terms, it is referred to as an S11 measurement. To make the measurement, the handheld CAT (e.g., the Agilent N9330B) uses a signal generator to generate a swept R ...