Percolation and Network Resilience
... to sink, but also by parallel flow paths through other parts of the system. Where the network jogs around large geographical obstacles, such as the Rocky Mountains in the West or the Great Lakes in the East, loop flows around the obstacle are set up that can drive as much as 1 GW of power in a cir ...
... to sink, but also by parallel flow paths through other parts of the system. Where the network jogs around large geographical obstacles, such as the Rocky Mountains in the West or the Great Lakes in the East, loop flows around the obstacle are set up that can drive as much as 1 GW of power in a cir ...
Mobile Communications
... (1-10 Mbit/s) many proprietary solutions, especially for higher bit-rates, standards take their time (e.g. IEEE 802.11) products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, ...
... (1-10 Mbit/s) many proprietary solutions, especially for higher bit-rates, standards take their time (e.g. IEEE 802.11) products have to follow many national restrictions if working wireless, it takes a vary long time to establish global solutions like, ...
9781423902454_PPT_ch02 - Advanced Computer Maintenance
... Objectives (cont’d.) • Understand how two network nodes communicate through the OSI model • Discuss the structure and purpose of data packets and frames • Describe the two types of addressing covered by the OSI model ...
... Objectives (cont’d.) • Understand how two network nodes communicate through the OSI model • Discuss the structure and purpose of data packets and frames • Describe the two types of addressing covered by the OSI model ...
Evolve IP - Defense in Depth
... government contractors, industrial espionage and much more. Best defenses: This is the most challenging risk. Security awareness training is important but is definitely not sufficient to solve this problem. Two defenses seem promising: (a) inoculation in which all users are sent periodic spear phish ...
... government contractors, industrial espionage and much more. Best defenses: This is the most challenging risk. Security awareness training is important but is definitely not sufficient to solve this problem. Two defenses seem promising: (a) inoculation in which all users are sent periodic spear phish ...
Snort - an network intrusion prevention and detection system
... malicious activity such as denial of service attacks, port scans or even attempts to crack into computers by monitoring network traffic. ...
... malicious activity such as denial of service attacks, port scans or even attempts to crack into computers by monitoring network traffic. ...
Inte Controlling E3/T3 Services over Incumbent Carrier`s
... is detected. For fault isolation, the device automatically detects a pattern in the E3 or T3 header coming from the network port for in-band indication to activate/deactivate a diagnostic loopback. The RADview standard SNMP application, running on the HP OpenView UNIX or PC platform, provides a user ...
... is detected. For fault isolation, the device automatically detects a pattern in the E3 or T3 header coming from the network port for in-band indication to activate/deactivate a diagnostic loopback. The RADview standard SNMP application, running on the HP OpenView UNIX or PC platform, provides a user ...
Document
... another and that also link pages to other objects, such as sound, video, or animation files • Hypertext Transfer Protocol (HTTP): Communications standard used to transfer pages on Web • Uniform resource locator (URL): Full address of web page, including protocol, domain name, directory path, and fil ...
... another and that also link pages to other objects, such as sound, video, or animation files • Hypertext Transfer Protocol (HTTP): Communications standard used to transfer pages on Web • Uniform resource locator (URL): Full address of web page, including protocol, domain name, directory path, and fil ...
Best Practices for Better Security
... Customizable content controls: Keep tabs on online activities. You can set limits on Internet access by time, day of week, type of activity or device. It also is possible to provide access to only the Web sites you identify while choosing content categories to block. Professional-grade firewall: Thi ...
... Customizable content controls: Keep tabs on online activities. You can set limits on Internet access by time, day of week, type of activity or device. It also is possible to provide access to only the Web sites you identify while choosing content categories to block. Professional-grade firewall: Thi ...
CIS 199 -- Internet Basics – Terminology
... back to the server when a new file is requested. Cookies are stored on the browser. ...
... back to the server when a new file is requested. Cookies are stored on the browser. ...
CIS 199 -- Internet Basics – Terminology
... back to the server when a new file is requested. Cookies are stored on the browser. ...
... back to the server when a new file is requested. Cookies are stored on the browser. ...
LAN Systems
... preconfigured fashion or switched connections. • Easily scalable by adding more ATM switches or devices. • Seamless integration of LANs and WANs. • Possible types of ATM LANs are: – Gateway to ATM WAN: • ATM switch acts as a router and traffic concentrator. – Backbone ATM switch: • Single ATM switch ...
... preconfigured fashion or switched connections. • Easily scalable by adding more ATM switches or devices. • Seamless integration of LANs and WANs. • Possible types of ATM LANs are: – Gateway to ATM WAN: • ATM switch acts as a router and traffic concentrator. – Backbone ATM switch: • Single ATM switch ...
Who uses the Internet
... by using computers, dial-up modems, or broadband network connections, and fax machines to perform work that formerly required a person to travel physically to work. – A person who telecommutes is a teleworker. ...
... by using computers, dial-up modems, or broadband network connections, and fax machines to perform work that formerly required a person to travel physically to work. – A person who telecommutes is a teleworker. ...
Planning and Configuring Routing and Switching
... 70-293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network ...
... 70-293: MCSE Guide to Planning a Microsoft Windows Server 2003 Network ...
Here is the Original File
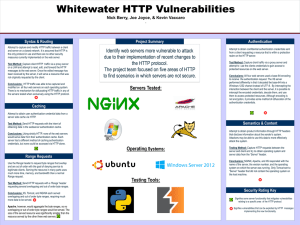
... and server on a closed network. It is assumed that HTTP is the only protocol in use and there are no other security measures currently implemented on the web server. Test Method: Capture client HTTP traffic via a proxy server on a LAN and attempt to read, edit, and forward the HTTP messages to the w ...
... and server on a closed network. It is assumed that HTTP is the only protocol in use and there are no other security measures currently implemented on the web server. Test Method: Capture client HTTP traffic via a proxy server on a LAN and attempt to read, edit, and forward the HTTP messages to the w ...
Dynamic Host Configuration Protocol
... Configure DHCP Options Local specific options (Windows, VoIP) - Options that apply to all clients in one scope only -Vendor-defined option classes - User-defined option classes - Reserved client options ...
... Configure DHCP Options Local specific options (Windows, VoIP) - Options that apply to all clients in one scope only -Vendor-defined option classes - User-defined option classes - Reserved client options ...
ppt - UTK-EECS
... Simplex Stop-and-Wait Protocol Assumptions Both the transmitting and receiving network layers are always ready Infinite buffer space is available The communication channel between the data link layers never damages or loses frames Data are transmitted in one direction only Processing time can be ig ...
... Simplex Stop-and-Wait Protocol Assumptions Both the transmitting and receiving network layers are always ready Infinite buffer space is available The communication channel between the data link layers never damages or loses frames Data are transmitted in one direction only Processing time can be ig ...
NetworkConcepts
... three PCs connected together to share resources. It can also connect hundreds of computers of different kinds • The connection can be made either by cables, infrared links, or small wireless devices Modern Computer and Information Technology (HKCEE) Core Module Section B Computer Systems and Network ...
... three PCs connected together to share resources. It can also connect hundreds of computers of different kinds • The connection can be made either by cables, infrared links, or small wireless devices Modern Computer and Information Technology (HKCEE) Core Module Section B Computer Systems and Network ...
What Is P2P…
... record of a file name matching key. If so, send a RESP message back to the node identified by return-pid; if not, propagate the query to all known peers with a decreased ttl (time-to-live) value, unless ttl ...
... record of a file name matching key. If so, send a RESP message back to the node identified by return-pid; if not, propagate the query to all known peers with a decreased ttl (time-to-live) value, unless ttl ...
Chapter 3. QoS Mechanisms
... provides the finest granularity and supports perflow QoS service. Limitations: • OK at the EDGE, but NOT Suitable to CORE • Problems when passing firewalls using NAT ...
... provides the finest granularity and supports perflow QoS service. Limitations: • OK at the EDGE, but NOT Suitable to CORE • Problems when passing firewalls using NAT ...