I2RS Requirements
... Multiple Applications across 2G to LTE, various network architectures, different service carriers make MBB configuration more arduous Traditional configuration and diagnoses mechanisms base on device-level management tools and manual processing are illsuited to meet the requirements of today‘s s ...
... Multiple Applications across 2G to LTE, various network architectures, different service carriers make MBB configuration more arduous Traditional configuration and diagnoses mechanisms base on device-level management tools and manual processing are illsuited to meet the requirements of today‘s s ...
Evaluating Design Approaches For Smart Building Systems
... interconnectivity between two or more networks is a challenging task. This is mainly due to the fact that different protocols, systems and implementations do not always operate in harmony. An obvious move towards the amalgamation of the isolated WSN is to adapt multiple and diverse sensor networks t ...
... interconnectivity between two or more networks is a challenging task. This is mainly due to the fact that different protocols, systems and implementations do not always operate in harmony. An obvious move towards the amalgamation of the isolated WSN is to adapt multiple and diverse sensor networks t ...
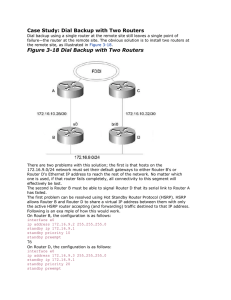
Case Study: Dial Backup with Two Routers
... When a host on the 172.16.9.0/24 network attempts to transmit a packet to a destination that is off the local segment, it will ARP for its default gateway's physical address, and the HSRP active router will answer with the virtual address. The host will then send all off-segment traffic to the virtu ...
... When a host on the 172.16.9.0/24 network attempts to transmit a packet to a destination that is off the local segment, it will ARP for its default gateway's physical address, and the HSRP active router will answer with the virtual address. The host will then send all off-segment traffic to the virtu ...
Streaming media Using VLC
... The addresses from 239.0.0.0 to 239.255.255.255 are called Limited Scope Addresses or Administratively Scoped Addresses. These are defined in RFC 2365 to be constrained to a local group or organisation. Routers are typically configured with filters to prevent multicast traffic in this address range ...
... The addresses from 239.0.0.0 to 239.255.255.255 are called Limited Scope Addresses or Administratively Scoped Addresses. These are defined in RFC 2365 to be constrained to a local group or organisation. Routers are typically configured with filters to prevent multicast traffic in this address range ...
Link asymmetry - GIST Networked Computing Systems Laboratory
... Passive scheme : collect accurate and stable link-quality information from a large volume of existing data traffic. ...
... Passive scheme : collect accurate and stable link-quality information from a large volume of existing data traffic. ...
Transport Control Protocol (TCP) & Applications
... Domain Name System specifies the name syntax and the rules for delegation authority over names. It provides: • hierarchical domain based naming scheme • distributed database implemented in a hierarchy of many name servers primarily for mapping host names to IP addresses • the Internet is divided int ...
... Domain Name System specifies the name syntax and the rules for delegation authority over names. It provides: • hierarchical domain based naming scheme • distributed database implemented in a hierarchy of many name servers primarily for mapping host names to IP addresses • the Internet is divided int ...
Chapter 2: Networking Standards and the OSI Model
... Objectives (cont’d.) • Understand how two network nodes communicate through the OSI model • Discuss the structure and purpose of data packets and frames • Describe the two types of addressing covered by the OSI model ...
... Objectives (cont’d.) • Understand how two network nodes communicate through the OSI model • Discuss the structure and purpose of data packets and frames • Describe the two types of addressing covered by the OSI model ...
PGTP: Power Aware Game Transport Protocol for Multi
... packet instead of a byte. The reliable packet is placed on a timer to be sent repeatedly until an acknowledgement arrives or if the maximum number of retries has been exceed. While the packet waits for acknowledgement, the send queue is scanned for data to be sent. Data requiring the reliable delive ...
... packet instead of a byte. The reliable packet is placed on a timer to be sent repeatedly until an acknowledgement arrives or if the maximum number of retries has been exceed. While the packet waits for acknowledgement, the send queue is scanned for data to be sent. Data requiring the reliable delive ...
TCP/IP Protocol Suite
... • Host X begins by encapsulating the IP packet into a data link frame (in this case Ethernet) with RTA’s Ethernet 0 interface’s MAC address as the data link destination address. • How does Host X know to forward to packet to RTA and not directly to Host Y? How does Host X know or get RTA’s Ethernet ...
... • Host X begins by encapsulating the IP packet into a data link frame (in this case Ethernet) with RTA’s Ethernet 0 interface’s MAC address as the data link destination address. • How does Host X know to forward to packet to RTA and not directly to Host Y? How does Host X know or get RTA’s Ethernet ...
TCP/IP and Other Transports for High
... preamble provides all the nodes on the network a signal against which to synchronize. Start Frame delimiter, which marks the start of a frame. The start frame delimiter is 8 bits long with the pattern10101011 Media Access Control (MAC) Address Every Ethernet network card has, built into its hardware ...
... preamble provides all the nodes on the network a signal against which to synchronize. Start Frame delimiter, which marks the start of a frame. The start frame delimiter is 8 bits long with the pattern10101011 Media Access Control (MAC) Address Every Ethernet network card has, built into its hardware ...
MAC Protocols
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
Chapter I: Introduction
... implicitly by its time slot or frequency assignment. In packet switching, identity of data must be explicitly specified by a header. Circuit switching must be connection-oriented. Packet switching can be connectionless (datagram), or connection-oriented (virtual circuit). Modern computer communi ...
... implicitly by its time slot or frequency assignment. In packet switching, identity of data must be explicitly specified by a header. Circuit switching must be connection-oriented. Packet switching can be connectionless (datagram), or connection-oriented (virtual circuit). Modern computer communi ...
Permissions
... and install themselves when users click files. A macro is a small program, usually written in VBA (Visual Basic for Applications). Macro viruses spread when users click files in which the macro virus resides. Macro viruses may also delete files, etc. on an ...
... and install themselves when users click files. A macro is a small program, usually written in VBA (Visual Basic for Applications). Macro viruses spread when users click files in which the macro virus resides. Macro viruses may also delete files, etc. on an ...
A046060105
... The use of Wi-Fi enabled android phones as IP phones, and their communication within a local wireless LAN is discussed in this paper. This proposed model is a form of telecommunication that allows exchange of data and voice via Wi-Fi network. The phones, which are Wi-Fi enabled and have android oper ...
... The use of Wi-Fi enabled android phones as IP phones, and their communication within a local wireless LAN is discussed in this paper. This proposed model is a form of telecommunication that allows exchange of data and voice via Wi-Fi network. The phones, which are Wi-Fi enabled and have android oper ...
www.cs.hofstra.edu
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
... 1. Try default passwords used with standard accounts shipped with the system 2. Exhaustive try of all short passwords 3. Try words in system’s dictionary or list of likely passwords (hacker bulletin boards) 4. Collect information about users (full names, names of spouses and children, pictures and b ...
MAC Protocols
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
... point-to-point PPP for dial-up access point-to-point link between Ethernet switch and host broadcast (shared wire or medium) traditional Ethernet upstream HFC 802.11 wireless LAN ...
Network Servers - Wright State University
... Network File System • A network file system is a design for storing files on one or more hard disks on the servers on the network – File system refers to the file storage structure on an individual server, whereas network file system refers to how file storage is structured across all servers in th ...
... Network File System • A network file system is a design for storing files on one or more hard disks on the servers on the network – File system refers to the file storage structure on an individual server, whereas network file system refers to how file storage is structured across all servers in th ...
lect25 - Computer and Information Sciences
... With high error rate, the elapsed time simply increased but the transmissions were completed The traffic was bursty and with distributed routing, the network behavior was unpredictable because congested routers could drop additional incoming packets ...
... With high error rate, the elapsed time simply increased but the transmissions were completed The traffic was bursty and with distributed routing, the network behavior was unpredictable because congested routers could drop additional incoming packets ...
Internet and Mobile Services
... GPRS can be utilized for services such as WAP access, SMS and MMS, but also for Internet communication services such as email and web access ...
... GPRS can be utilized for services such as WAP access, SMS and MMS, but also for Internet communication services such as email and web access ...
Computers Are Your Future Chapter 7: Networks: Communicating and Sharing Resources Twelfth Edition
... • Expansion board or adapter that provides a connection between the computer and the network • Notebook computers usually support both wired and wireless ...
... • Expansion board or adapter that provides a connection between the computer and the network • Notebook computers usually support both wired and wireless ...