Networking Components and Devices
... switches are often interconnected to create larger networks. Despite their similarity in appearance and their identical physical connections to computers, switches offer significant operational advantages over hubs. As discussed earlier in the chapter, a hub forwards data to all ports, regardless of ...
... switches are often interconnected to create larger networks. Despite their similarity in appearance and their identical physical connections to computers, switches offer significant operational advantages over hubs. As discussed earlier in the chapter, a hub forwards data to all ports, regardless of ...
ICMP (Internet Control Message Protocol)
... The default gateway has two configurable bits in its Router Advertisement (RA) available for this purpose: • O bit — When this bit is set, the client can use DHCPv6 to retrieve other configuration parameters (for example, TFTP server address or DNS server address) but not the client's IP address. • ...
... The default gateway has two configurable bits in its Router Advertisement (RA) available for this purpose: • O bit — When this bit is set, the client can use DHCPv6 to retrieve other configuration parameters (for example, TFTP server address or DNS server address) but not the client's IP address. • ...
Chapter 6 slides, Computer Networking, 3rd edition
... (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
... (aka “cell”) in infrastructure mode contains: wireless hosts access point (AP): base station ad hoc mode: hosts only ...
Is the Boston subway a small-world network?
... Although the initial small-world concept came from social networks, having a mathematical characterization makes it tempting to apply the same concept to any network representative of a complex system. This grand plan clashes with the fact that the mathematical formalism of Ref. [2] su=ers from seve ...
... Although the initial small-world concept came from social networks, having a mathematical characterization makes it tempting to apply the same concept to any network representative of a complex system. This grand plan clashes with the fact that the mathematical formalism of Ref. [2] su=ers from seve ...
ConnectX®-3 Pro VPI Adapters for Open Compute
... tenants, each with its own isolated network domain over a shared network infrastructure. To achieve maximum efficiency, data center operators create overlay networks that carry traffic from individual Virtual Machines (VMs) in encapsulated formats such as NVGRE and VXLAN over a logical “tunnel,” the ...
... tenants, each with its own isolated network domain over a shared network infrastructure. To achieve maximum efficiency, data center operators create overlay networks that carry traffic from individual Virtual Machines (VMs) in encapsulated formats such as NVGRE and VXLAN over a logical “tunnel,” the ...
Case Study: Prestigious hospital. Outdated network.
... exchanged, storing months of information. • Cisco StealthWatch adds threat intelligence through analytics to NetFlow data to accelerate response. The Cisco StealthWatch solution can analyze network audit trails, identify anomalous activity, and zero in on the root causes of attacks. With the soluti ...
... exchanged, storing months of information. • Cisco StealthWatch adds threat intelligence through analytics to NetFlow data to accelerate response. The Cisco StealthWatch solution can analyze network audit trails, identify anomalous activity, and zero in on the root causes of attacks. With the soluti ...
Optimized Multi-Layer Transport
... All-Native: 100G/200G centralized packet switching plus 40G TDM switching ...
... All-Native: 100G/200G centralized packet switching plus 40G TDM switching ...
Role of Ethernet in Optical Networks
... This presentation contains forward-looking statements that involve substantial risks and uncertainties, including but not limited to, statements relating to goals, plans, objectives and future events. All statements, other than statements of historical facts, included in this presentation regarding ...
... This presentation contains forward-looking statements that involve substantial risks and uncertainties, including but not limited to, statements relating to goals, plans, objectives and future events. All statements, other than statements of historical facts, included in this presentation regarding ...
Healthcare Monitoring System Using Wireless Sensor Network
... any sentient organism, the smart environment relies first urrent health care systems are structured and and foremost on sensory data from the real world. Sensory data comes from multiple sensors of different optimized for reacting to crisis and managing illness are modalities in distributed location ...
... any sentient organism, the smart environment relies first urrent health care systems are structured and and foremost on sensory data from the real world. Sensory data comes from multiple sensors of different optimized for reacting to crisis and managing illness are modalities in distributed location ...
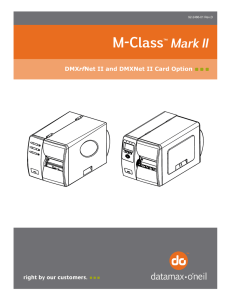
DMXrfNet II and DMXNet II Card Option
... backplate of the wireless card or on the Network Report, it is listed as “MACR”. From Windows , you may now “View Wireless Networks”. From the list of available wireless networks select the printer’s SSID (printers MAC Address) that you wish to connect to and then click on the Connect button. If you ...
... backplate of the wireless card or on the Network Report, it is listed as “MACR”. From Windows , you may now “View Wireless Networks”. From the list of available wireless networks select the printer’s SSID (printers MAC Address) that you wish to connect to and then click on the Connect button. If you ...
2001 Midterm Solutions
... The most obvious answer is to put a flag in the header of the IPv4 packet that a IPv4 router will ignore and that an IPv6 router will take to mean that an IPv6 packet is included. The key point is that you can not modify the IPv6 header in such a way that it will confuse and IPv4 router. One solutio ...
... The most obvious answer is to put a flag in the header of the IPv4 packet that a IPv4 router will ignore and that an IPv6 router will take to mean that an IPv6 packet is included. The key point is that you can not modify the IPv6 header in such a way that it will confuse and IPv4 router. One solutio ...
Flow control
... • Receiver checks for five consecutive 1s – if next bit = 0, it is removed – if next two bits are 10, then flag is detected – If next two bits are 11, then frame has errors ...
... • Receiver checks for five consecutive 1s – if next bit = 0, it is removed – if next two bits are 10, then flag is detected – If next two bits are 11, then frame has errors ...
CS 447/557 Computer Forensics
... – Did not specify email contents just e-mail logs • Harder to obtain warrants for email contents ...
... – Did not specify email contents just e-mail logs • Harder to obtain warrants for email contents ...
Technical Overview of the Leaf Patient Monitoring
... The Leaf Patient Monitoring System uses a propriety wireless local area network (WLAN) to relay messages between the Patient Sensors and the computer running the Mesh Network Server Software. The WLAN is comprised of many Relay Antennas that are plugged into available power outlets within the facili ...
... The Leaf Patient Monitoring System uses a propriety wireless local area network (WLAN) to relay messages between the Patient Sensors and the computer running the Mesh Network Server Software. The WLAN is comprised of many Relay Antennas that are plugged into available power outlets within the facili ...
Flexible, Managed SDH Multiplexers
... networks unifying data and telephony in order to revolutionise the way people work, ...
... networks unifying data and telephony in order to revolutionise the way people work, ...
Ch. 7 - OSI Data Link Layer
... • If a device is MOVED from one subnet to another…layer 2 address is the same. Will need to change the layer 3 address for the device to ...
... • If a device is MOVED from one subnet to another…layer 2 address is the same. Will need to change the layer 3 address for the device to ...
www.siskiyous.edu
... delivered error-free are called _____ protocols. • Answer: connectionless Network+ Guide to Networks, 5th Edition ...
... delivered error-free are called _____ protocols. • Answer: connectionless Network+ Guide to Networks, 5th Edition ...
Slides - The University of Texas at Dallas
... • All active plugins stored on code servers are digitally signed by their developers • Code servers are well-known network nodes that authenticate active plugins when sending them to ANN • ANNs have the capability to check the plugin’s sources and developer before installing and running active plugi ...
... • All active plugins stored on code servers are digitally signed by their developers • Code servers are well-known network nodes that authenticate active plugins when sending them to ANN • ANNs have the capability to check the plugin’s sources and developer before installing and running active plugi ...
PPT
... Benes networks • Any permutation has a conflict free route – Useful property – Offline computation is difficult ...
... Benes networks • Any permutation has a conflict free route – Useful property – Offline computation is difficult ...
Cindy - Anatomy of a Window
... security policies than packet-filtering routers can manage Requires special-purpose code (a proxy service) for each desired application The proxy code can be configured to support only acceptable features of an application Users are permitted access to the proxy services, but may not log in to the a ...
... security policies than packet-filtering routers can manage Requires special-purpose code (a proxy service) for each desired application The proxy code can be configured to support only acceptable features of an application Users are permitted access to the proxy services, but may not log in to the a ...
ppt
... address X and source port P, to the internal host only if the internal host had previously sent a packet to IP address X and port P. • Symmetric NAT – A symmetric NAT is a NAT where all requests from the same internal IP address and port to a specific destination IP address and port are mapped to th ...
... address X and source port P, to the internal host only if the internal host had previously sent a packet to IP address X and port P. • Symmetric NAT – A symmetric NAT is a NAT where all requests from the same internal IP address and port to a specific destination IP address and port are mapped to th ...