* Your assessment is very important for improving the workof artificial intelligence, which forms the content of this project
Download Cindy - Anatomy of a Window
Survey
Document related concepts
Wake-on-LAN wikipedia , lookup
Asynchronous Transfer Mode wikipedia , lookup
Zero-configuration networking wikipedia , lookup
Cracking of wireless networks wikipedia , lookup
Piggybacking (Internet access) wikipedia , lookup
Computer network wikipedia , lookup
Distributed firewall wikipedia , lookup
Network tap wikipedia , lookup
List of wireless community networks by region wikipedia , lookup
Airborne Networking wikipedia , lookup
Deep packet inspection wikipedia , lookup
Internet protocol suite wikipedia , lookup
Recursive InterNetwork Architecture (RINA) wikipedia , lookup
Transcript
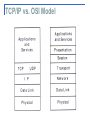
Data Transmission Basics for Digital Investigations Objectives Understand the OSI and TCP models Understand the basics of how data is transmitted on networks 2 OSI Model Standard was needed for companies to communicate with each other via their computer systems OSI model released in 1984 Created by the International Organization for Standardization (ISO) OSI model breaks down complexity of data communications into a simple layered approach 3 OSI Model (Cont.) Advantages of layered approach: Different hardware/software vendors have a standard to follow for designing products Collaboration between companies to develop network components is easier Changes in one layer are not carried over into other layers Network design is broken down into smaller, more manageable parts Problem resolution is easier because problems are usually confined to a single layer 4 OSI Model (Cont.) Layer 7: Application layer provides services to applications such as email or Internet browsers Allows access to network services that support applications Handles network access, flow control, and error recovery Layer 6: Presentation layer ensures the data formats from the application layer of one computer can be read by the application layer of another computer Converts all formats into a common uniform format Protocol conversion Encryption/decryption 5 OSI Model (Cont.) Layer 5: Session layer provides services to the presentation layer by creating a communication link between two hosts Establishes identification to exclude non-communicating hosts Establishes checkpoints Manages data transmit times and length Layer 4: Transport layer segments data and prepare these segments for transport across a network. Also reassembles those segments on the receiving side. Regulates flow control Uses acknowledgements Enables error handling 6 OSI Model (Cont.) Layer 3: Network layer functions (Connectivity and path selection between two hosts on a network) Logical addressing (IP addressing) Translating logical addresses to physical addressing Packet switching Routing 7 OSI Model (Cont.) Layer 2: Data link layer functions (physical addressing across a network) Conversion of packets into raw bits Error correction Flow control Layer 1: Physical layer functions (physical connectivity issue in a network) Defines hardware standards Transmits raw data over different mediums Defines protocols on how to transmit raw data over different mediums 8 OSI Model (Cont.) Data flow in the OSI model Protocols that function at each layer on Host A communicate with the corresponding layer on Host B Protocol data units (PDUs) are used to include header information on the packet being sent from host to host Each layer depends on the layer below it for services, and each layer above adds PDUs via encapsulation 9 OSI Reference Model END USER A END USER B Application Layer Application Layer Presentation Layer higher level protocols lower level protocols or network services Session Layer End user functions Presentation Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Data Link Layer Network functions Data Link Layer Physical Layer Physical Layer higher level protocols lower level protocols or network services PHYSICAL MEDIUM 10 TCP/IP Model Also called the Internet Protocol Suite Set the communications protocols for the Internet and other similar networks. TCP – Transmission Control Protocol IP – Internet Protocol De facto standard for communications Direct result of the Department of Defense efforts to require a protocol that could survive wartime situations and still communicate with other hosts via different communication mediums Has only four (five) layers as compared to seven layers of OSI model 11 TCP/IP vs. OSI Model TCP/IP Model (Cont.) How data transports in the network Switching networks Packet switching Circuit switching 13 Typical Scenario We have a source machine A We have a destination machine B A has some application specific data stored as a file. An example might be a web page stored as an html file on a web server. The user on machine B launches a web browser (Application layer) and types in the URL to the web page on machine A and hits GO! Typical Scenario cont. (APPLICATION LAYER) An http request (Application Layer) with URL is generated by the browser and sent down the stack to the Transport layer. (TCP LAYER) The transport layer “wraps” the application layer data with TCP headers. TCP header provides information for end-to-end service, such as end host port numbers, Sequence number and Acknowledgement Number for tracking and delivery confirmation. Typical Scenario cont. (IP LAYER) Once the Transport layer has added its headers, it transfers the growing set of data to the IP Layer. The Network layer wraps the TCP segment with IP headers. IP headers give the receiving counterpart information on source and destination IP addresses, next layer protocol, fragmentation information, etc. Typical Scenario cont. (DATA LINK LAYER) Once the IP Layer has added its headers, it transfers the still growing set of data to the Data Link layer. The Data Link Layer wraps the IP packet with frame header. The frame header is just more bytes of data that specifies source and destination physical MAC addresses of the current hop (the whole path may contain multiple hops). Run “tracert” in Windows. Typical Scenario cont. (PHYSICAL LAYER) A completed Frame ready to be placed on the wire and sent to its destination. The wire is the physical layer and it accommodates the physical transfer of the frame to its destination. Network Devices 21 Network Interface Card Network Interface Card Also known as NIC, network card or network adapter Works in OSI Layers 1 and 2 Has a unique MAC (Media Access Control) or physical address (12-digit hexadecimal) ipconfig/all in Windows Command Prompt Connects to other network devices, e.g. routers or switches, via network cables or wireless connections Network Cables Network Cables Category 5 cable CAT-5 twisted pair cables are mostly used for 100 mbps 4 pairs (8)of twisted wires are connected to the 8 pins of a RJ-45 plug Each pair of wires has specific functions, such as sending and receiving data signal Crossover cables are good for direct communication between two computers or same type of devices. Needs n(n-1)/2 cables for n computers (too many cables!) Network Hubs Network Hubs Work in Layer 1 (Physical Layer) Same as connecting all wires together Not capable of making use of MAC or IP addresses Broadcast every single bit onto all the links Have NO Media Access Control Can cause traffic conflicts from different computers; performance degrades when more computers are connected Not very fast speed, e.g. 10mbps ~ 100mbps Network Switches Network Switches Mainly work in Layer 2 (Data Link Layer) Do not look into traffic type or other details like routers do Make use of MAC addresses Have Media Access Control Not capable of making use of IP addresses Support high data rate, e.g. 100 mbps or 1 Gbps Good for high speed communications among computers in a LAN Routers Routers Also called Layer 3 switches Work in Layer 3 (Network Layer) Make use of IP addresses Decide a path in the networks for data Interconnect separate logical networks, often different types of networks Not as fast as switches, e.g., 100mbps Data Network Types Local Area Network A network configuration designed for a limited space or geographic area such as a series of offices in the same building Two common types of LANs are the campus area network (CAN) and the metropolitan area network (MAN) Wide Area Network A group of smaller LANs connected logically or physically WANs can combine other subnetworks such as intranets, extranets, and virtual private networks (VPNs) to provide enhanced network capabilities 32 Data Network Types cont. Internet Intranet The Internet is an interconnection of different-sized networks (LANs) around the world An intranet is a local or wide area network based on TCP/IP, but with firewalls that limit the network’s access to the Internet An intranet is more secure than the Internet because it has a restricted user community and local control Extranet An extranet is an intranet that allows select users outside of the firewalls to access the site 33 Firewalls Firewalls typically run monitoring software to detect and thwart external attacks on the site and protect the internal corporate network Firewalls are an essential device for network security Many of the architectures needed for security rely on one or more firewalls within an intelligent design 34 Firewalls cont. Application-Level Gateway Firewall Allows the network administrator to implement stricter security policies than packet-filtering routers can manage Requires special-purpose code (a proxy service) for each desired application The proxy code can be configured to support only acceptable features of an application Users are permitted access to the proxy services, but may not log in to the application-level gateway itself Application-level gateways allow information to flow between systems but do not allow the direct exchange of data 35 Firewalls cont. Benefits of Application-Level Gateways The network manager has complete control over each service and permitted services It has the ability to support strong user authentication and provide detailed logging information The filtering rules are much easier to configure and test 36 Firewalls cont. Limitations of Application-Level Gateways It requires either that users modify their behavior or that specialized software be installed on each system that accesses proxy services 37 Summary OSI model standardized the method of transmitting data on a network using a sevenlayer approach Application, presentation, session, transport, network, data link, and physical 38 Summary (Cont.) TCP/IP model consists of four layers: Application, transport, Internet, network interface De facto standard on the Internet Two address schemes are used to transmit data across networks Logical addressing Physical addressing 39