New Scheduling Algorithm for Providing Proportional Jitter in Differentiated Service Network
... is called Proportional Jitter Differentiated Service Model (PJD). This model is very simple and efficient for highspeed networks because it is not necessary to have proportional jitter scheduling algorithms at every routers. Relative Jitter Packet Scheduling algorithm [4], which produces proportiona ...
... is called Proportional Jitter Differentiated Service Model (PJD). This model is very simple and efficient for highspeed networks because it is not necessary to have proportional jitter scheduling algorithms at every routers. Relative Jitter Packet Scheduling algorithm [4], which produces proportiona ...
On the Effectiveness of Traffic Analysis Against
... anonymous traffic. On average, about 42% of the connections between victim Tor clients and entry nodes preserved the traffic fluctuations induced by the server. ...
... anonymous traffic. On average, about 42% of the connections between victim Tor clients and entry nodes preserved the traffic fluctuations induced by the server. ...
Deploying the Dell Force10 MXL into a Cisco Nexus Network
... Uplink configuration for the MXL will generally be done in one of two ways in a Cisco Nexus network environment: running PVST with discreet LAGs connected to separate top-of-rack switches as covered in Trunk Port Uplink Configuration with Per-VLAN Spanning Tree and running PVST with a single LAG con ...
... Uplink configuration for the MXL will generally be done in one of two ways in a Cisco Nexus network environment: running PVST with discreet LAGs connected to separate top-of-rack switches as covered in Trunk Port Uplink Configuration with Per-VLAN Spanning Tree and running PVST with a single LAG con ...
Presentation Title Size 30PT
... ** Student passes CCNA Discovery 4 or Exploration 4 final from the first attempt with 75% or higher they are eligible either the two or one exam offer, but not both 26 ...
... ** Student passes CCNA Discovery 4 or Exploration 4 final from the first attempt with 75% or higher they are eligible either the two or one exam offer, but not both 26 ...
PDF
... Tunneling encapsulates an AppleTalk packet inside the foreign protocol packet, which is then sent across the backbone to a destination router. The destination router then removes the encapsulation from the AppleTalk packet and, if necessary, routes the packet to a normal AppleTalk network. Because t ...
... Tunneling encapsulates an AppleTalk packet inside the foreign protocol packet, which is then sent across the backbone to a destination router. The destination router then removes the encapsulation from the AppleTalk packet and, if necessary, routes the packet to a normal AppleTalk network. Because t ...
The VPN Menu
... Don’t block traffic between clients: By default, the OpenVPN server isolates clients from each other. To change this behavior and allow traffic between different VPN clients, tick this option. Allow multiple connections from one account: Usually one client is allowed to connect from one location at ...
... Don’t block traffic between clients: By default, the OpenVPN server isolates clients from each other. To change this behavior and allow traffic between different VPN clients, tick this option. Allow multiple connections from one account: Usually one client is allowed to connect from one location at ...
Duplicate Address Detection in IPv6 Mobile Ad Hoc Network
... Routing: Distance Vector, Link State, and PIM-SM Transportation: TCP and UDP Traffic Sources: web, ftp, telnet, cbr, and stochastic Queuing Disciplines: drop-tail, RED, FQ, SFQ, and DRR QoS: InterServ and DiffServ Routing: Ad hoc routing and Mobile IP ...
... Routing: Distance Vector, Link State, and PIM-SM Transportation: TCP and UDP Traffic Sources: web, ftp, telnet, cbr, and stochastic Queuing Disciplines: drop-tail, RED, FQ, SFQ, and DRR QoS: InterServ and DiffServ Routing: Ad hoc routing and Mobile IP ...
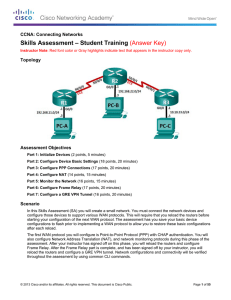
Skills Assessment – Student Training (Answer Key)
... In this Skills Assessment (SA) you will create a small network. You must connect the network devices and configure those devices to support various WAN protocols. This will require that you reload the routers before starting your configuration of the next WAN protocol. The assessment has you save yo ...
... In this Skills Assessment (SA) you will create a small network. You must connect the network devices and configure those devices to support various WAN protocols. This will require that you reload the routers before starting your configuration of the next WAN protocol. The assessment has you save yo ...
(PPT, 327KB)
... giving the minimum size of 20 bytes and maximum of 60 bytes, allowing for up to 40 bytes of options in the header. This field gets its name from the fact that it is also the offset from the start of the TCP segment to the actual data. https://store.theartofservice.com/the-transmission-control-protoc ...
... giving the minimum size of 20 bytes and maximum of 60 bytes, allowing for up to 40 bytes of options in the header. This field gets its name from the fact that it is also the offset from the start of the TCP segment to the actual data. https://store.theartofservice.com/the-transmission-control-protoc ...
Computer Networks and Internets By Douglas E Comer
... Transmitter indiciates start of next character by transmitting a zero o Receiver can detect transition as start of character o Extra zero called the start bit Transmitter must leave wire idle so receiver can detect transition marking beginning of next character o Transmitter sends a one after each c ...
... Transmitter indiciates start of next character by transmitting a zero o Receiver can detect transition as start of character o Extra zero called the start bit Transmitter must leave wire idle so receiver can detect transition marking beginning of next character o Transmitter sends a one after each c ...
CIS 175 Lecture Notes
... Transmitter indiciates start of next character by transmitting a zero o Receiver can detect transition as start of character o Extra zero called the start bit Transmitter must leave wire idle so receiver can detect transition marking beginning of next character o Transmitter sends a one after each c ...
... Transmitter indiciates start of next character by transmitting a zero o Receiver can detect transition as start of character o Extra zero called the start bit Transmitter must leave wire idle so receiver can detect transition marking beginning of next character o Transmitter sends a one after each c ...
UPnP Forum marketing overview
... Highly extensible – any data type, any transfer protocol, any combination of server, render, and control point Highly scalable – ultra low resource devices (cameras, EPF) up to high-end servers (PCs, media servers, Internet, broadcasts, PVR). * Out of band = not UPnP Constrained ...
... Highly extensible – any data type, any transfer protocol, any combination of server, render, and control point Highly scalable – ultra low resource devices (cameras, EPF) up to high-end servers (PCs, media servers, Internet, broadcasts, PVR). * Out of band = not UPnP Constrained ...
TTAS tandard - TTA표준화 위원회
... For Fixed-Mobile Convergence(FMC), some scenarios require seamless roaming between GSM/GPRS/3G mobile and WLAN networks. Both networks may independently be authenticated. To maintain the quality of the customer experience and due to the difference of networks, handovers to support service continuity ...
... For Fixed-Mobile Convergence(FMC), some scenarios require seamless roaming between GSM/GPRS/3G mobile and WLAN networks. Both networks may independently be authenticated. To maintain the quality of the customer experience and due to the difference of networks, handovers to support service continuity ...
Overview of Provider Backbone Bridging and Integration
... providers and integration with virtual private LAN service (VPLS) are discussed. Interoperability scenarios of PBB with VPLS are covered with emphasis on how the combined solution addresses existing challenges in VPLS. ...
... providers and integration with virtual private LAN service (VPLS) are discussed. Interoperability scenarios of PBB with VPLS are covered with emphasis on how the combined solution addresses existing challenges in VPLS. ...
IPv6: New Plumbing for the Internet
... • Operator support: BT, DT, Telia, NTT • Government support: Japan, Korea, European Union, Canada • Many vendors have IPv6 product road map • Support in current software releases ...
... • Operator support: BT, DT, Telia, NTT • Government support: Japan, Korea, European Union, Canada • Many vendors have IPv6 product road map • Support in current software releases ...
User Guide CUBE/MOVE | cordless IP camera | Indoor
... This instruction manual serves to familiarize you with the the mode of operation of this product. Therefore keep these instructions safe at all times, so that you can access them at any time. With the purchase of this product, you receive a two-year guarantee against defects when used properly. Plea ...
... This instruction manual serves to familiarize you with the the mode of operation of this product. Therefore keep these instructions safe at all times, so that you can access them at any time. With the purchase of this product, you receive a two-year guarantee against defects when used properly. Plea ...
Cisco PIX 535 Security Appliance
... partners, and remote offices worldwide using the full-featured VPN capabilities provided by the Cisco PIX 535 Security Appliance. Solutions range from standards-based site-to-site VPN leveraging the Internet Key Exchange (IKE) and IP security (IPsec) VPN standards, to the innovative Cisco Easy VPN c ...
... partners, and remote offices worldwide using the full-featured VPN capabilities provided by the Cisco PIX 535 Security Appliance. Solutions range from standards-based site-to-site VPN leveraging the Internet Key Exchange (IKE) and IP security (IPsec) VPN standards, to the innovative Cisco Easy VPN c ...
Introduction to VLANs
... Switches will flood unicast traffic out all ports if it does not have the destination MAC address in its source address table. This can be especially true for large flat networks where switches cannot contain all of the MAC addresses. – MAC address table can be 1,024 (or less) and more than 16,000 a ...
... Switches will flood unicast traffic out all ports if it does not have the destination MAC address in its source address table. This can be especially true for large flat networks where switches cannot contain all of the MAC addresses. – MAC address table can be 1,024 (or less) and more than 16,000 a ...
Tapestry: An Infrastructure for Fault-tolerant Wide-area
... approaches to providing object name service, consistency, location and routing. If we project current trends for growing numbers and complexities of overlay network services, we may be headed towards a future state of world computing infrastructure that collapses under its own weight. Already, many ...
... approaches to providing object name service, consistency, location and routing. If we project current trends for growing numbers and complexities of overlay network services, we may be headed towards a future state of world computing infrastructure that collapses under its own weight. Already, many ...