Introduction to Computer Systems IESL
... Servers (also called hosts or host computers) Clients Circuits Clients and Servers typically work together in clientserver networks. Networks without servers are called peer-to-peer networks. Routers are specialized devices responsible for moving information between networks, are also a common netwo ...
... Servers (also called hosts or host computers) Clients Circuits Clients and Servers typically work together in clientserver networks. Networks without servers are called peer-to-peer networks. Routers are specialized devices responsible for moving information between networks, are also a common netwo ...
Exam 70-681
... You work as the network administrator at ABC Company.com. The network consists of a single Active Directory domain named ABC Company.com. The network consists of two subnets connected by a router. SubnetA contains all ABC Company.com servers. SubnetB contains all ABC Company.com client computers. Al ...
... You work as the network administrator at ABC Company.com. The network consists of a single Active Directory domain named ABC Company.com. The network consists of two subnets connected by a router. SubnetA contains all ABC Company.com servers. SubnetB contains all ABC Company.com client computers. Al ...
KSWAN Presentation - Karnataka State Wide Area Network
... Username and Password should be given by the department for Dial-up connection ...
... Username and Password should be given by the department for Dial-up connection ...
Slide 1
... • A packet arriving at an input port travels along the horizontal bus attached to the input port until it intersects with the vertical bus leading to the desired output port. • If the vertical bus leading to the output port is free, the packet is transferred to the output port. If the vertical bus i ...
... • A packet arriving at an input port travels along the horizontal bus attached to the input port until it intersects with the vertical bus leading to the desired output port. • If the vertical bus leading to the output port is free, the packet is transferred to the output port. If the vertical bus i ...
infosys.richmond.cc.nc.us
... level and contains only the hashed passwords Security+ Guide to Network Security Fundamentals, Third Edition ...
... level and contains only the hashed passwords Security+ Guide to Network Security Fundamentals, Third Edition ...
Advanced Intelligent Network for Wireless Communications
... 2) Service Control Point The Service Control Point (SCP) is the brain of the AIN. The SCP invokes service logic programs. The common channel signalling network allows the SCP to fully interconnect with AIN switching systems via a signalling transport (STP). The switch (SSP) will consult the SCP at v ...
... 2) Service Control Point The Service Control Point (SCP) is the brain of the AIN. The SCP invokes service logic programs. The common channel signalling network allows the SCP to fully interconnect with AIN switching systems via a signalling transport (STP). The switch (SSP) will consult the SCP at v ...
cos 413 day 19
... Performing Live Acquisitions • Live acquisitions are especially useful when you’re dealing with active network intrusions or attacks • Live acquisitions done before taking a system offline are also becoming a necessity ...
... Performing Live Acquisitions • Live acquisitions are especially useful when you’re dealing with active network intrusions or attacks • Live acquisitions done before taking a system offline are also becoming a necessity ...
Security+ Guide to Network Security Fundamentals, Third Edition
... level and contains only the hashed passwords Security+ Guide to Network Security Fundamentals, Third Edition ...
... level and contains only the hashed passwords Security+ Guide to Network Security Fundamentals, Third Edition ...
Active Directory & DNS Setup Abstract
... For example, an organization that has an external domain name of contoso.com might use the internal domain name corp.contoso.com. You can use your internal domain as a parent for additional child domains that you create to manage divisions within your company, in cases where you are deploying an Act ...
... For example, an organization that has an external domain name of contoso.com might use the internal domain name corp.contoso.com. You can use your internal domain as a parent for additional child domains that you create to manage divisions within your company, in cases where you are deploying an Act ...
Blueprint For Security Chapter 6
... detect when intruder creates, modifies, or deletes files Most HIDPSs work on the principle of configuration or change management Advantage over NIDPS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 3rd edition ...
... detect when intruder creates, modifies, or deletes files Most HIDPSs work on the principle of configuration or change management Advantage over NIDPS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 3rd edition ...
PDF
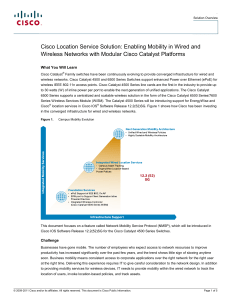
... lobby of an office building can have different policies from a phone in a conference room or in an employee’s office. Today the policies are statically administered based on an endpoint’s MAC address and not based on the location of the endpoint itself. Knowing the location of a wired entity provide ...
... lobby of an office building can have different policies from a phone in a conference room or in an employee’s office. Today the policies are statically administered based on an endpoint’s MAC address and not based on the location of the endpoint itself. Knowing the location of a wired entity provide ...
Updated November 2011 - OneSource Wireless Internet
... networks used in transmission. Latency is typically measured in milliseconds, and generally has no significant impact on typical everyday Internet usage. As latency varies based on any number of factors, most importantly the distance between a customer's computer and the ultimate Internet destinatio ...
... networks used in transmission. Latency is typically measured in milliseconds, and generally has no significant impact on typical everyday Internet usage. As latency varies based on any number of factors, most importantly the distance between a customer's computer and the ultimate Internet destinatio ...
Moodle-5 - Willingdon College, Sangli
... difference is the connector used. Apple Local Talk connector generally must be soldered during installation, a process that requires some practice and skill on the part the installer. Capacity : The capacity of STP cable is 500 Mbps. Although few implementations exceed 155 Mbps with 100 meter cable ...
... difference is the connector used. Apple Local Talk connector generally must be soldered during installation, a process that requires some practice and skill on the part the installer. Capacity : The capacity of STP cable is 500 Mbps. Although few implementations exceed 155 Mbps with 100 meter cable ...
Analysis of NAT-Based Internet Connectivity for Multi
... Analysis of NAT-Based Internet Connectivity for Multi-Homed On-Demand Ad Hoc Networks Engelstad, P.E. and Egeland, G. University of Oslo (UniK) / Telenor R&D, 1331 Fornebu, Norway ...
... Analysis of NAT-Based Internet Connectivity for Multi-Homed On-Demand Ad Hoc Networks Engelstad, P.E. and Egeland, G. University of Oslo (UniK) / Telenor R&D, 1331 Fornebu, Norway ...
Presentation 04 - Tufts Wireless Laboratory
... • Based on the collective information, nRTEDBs actively control a WSN to extract important data directly relevant to an event of interest. In this way, they considerably enhance the overall timeliness, security, and efficiency. • Extend and integrate cutting-edge real-time data service techniques as ...
... • Based on the collective information, nRTEDBs actively control a WSN to extract important data directly relevant to an event of interest. In this way, they considerably enhance the overall timeliness, security, and efficiency. • Extend and integrate cutting-edge real-time data service techniques as ...
CSE 302-Mobile Computing Challenges
... • The potential of decoupled and disconnected operation, location-dependent computation and communication, and powerful portable computing devices gives rise to opportunities for new patterns of distributed computation that require a revised view of distributed systems. • However, factors such as we ...
... • The potential of decoupled and disconnected operation, location-dependent computation and communication, and powerful portable computing devices gives rise to opportunities for new patterns of distributed computation that require a revised view of distributed systems. • However, factors such as we ...
110520159259936663_network__monitoring_system_-new
... managed services. The manager responsibility is to monitor the agents. The agents are software that manage all the network devices and send the details report about the managed objects to the manager. The agent should manage each network device based on the feedback received from the manager. It is ...
... managed services. The manager responsibility is to monitor the agents. The agents are software that manage all the network devices and send the details report about the managed objects to the manager. The agent should manage each network device based on the feedback received from the manager. It is ...
1-network
... – IP address is a unique address on a network assigned to a device – If the packet is meant for a device on the local host IP gets the MAC address for the device and sends it directly to the host – For a remote packet it first looks up the routing table for an explicit route to the network. – If an ...
... – IP address is a unique address on a network assigned to a device – If the packet is meant for a device on the local host IP gets the MAC address for the device and sends it directly to the host – For a remote packet it first looks up the routing table for an explicit route to the network. – If an ...
Media Communication
... other via voice, video and/or other data over the Internet - Conference initiation, start, join, leave, end, control, etc. - Sending audio/video data from one-to-many (multicast) - Sharing other conference data (data conferencing) among all participants - Synchronization and network delay, jitter, p ...
... other via voice, video and/or other data over the Internet - Conference initiation, start, join, leave, end, control, etc. - Sending audio/video data from one-to-many (multicast) - Sharing other conference data (data conferencing) among all participants - Synchronization and network delay, jitter, p ...
Introduction to Computer Networks
... • Preamble: 7 bytes with the pattern 10101010 followed by one byte with the pattern 10101011 (SFD - start frame delimiter) • Address: 6 bytes, received by all adapters, but dropped if address does not match • Type: indicates the higher layer protocol, mostly IP • CRC: checked at receiver, if error i ...
... • Preamble: 7 bytes with the pattern 10101010 followed by one byte with the pattern 10101011 (SFD - start frame delimiter) • Address: 6 bytes, received by all adapters, but dropped if address does not match • Type: indicates the higher layer protocol, mostly IP • CRC: checked at receiver, if error i ...
COMP211_Topic6_Link
... connectionless: no handshaking between sending and receiving NICs unreliable: receiving NIC doesnt send acks or nacks to sending NIC data in dropped frames recovered only if initial sender uses higher layer rdt (e.g., TCP), otherwise ...
... connectionless: no handshaking between sending and receiving NICs unreliable: receiving NIC doesnt send acks or nacks to sending NIC data in dropped frames recovered only if initial sender uses higher layer rdt (e.g., TCP), otherwise ...
PowerPoint
... the IP header, using the six most significant bits of the IPv4 “type of service” (TOS) octet The edge router may also perform traffic conditioning (e.g., selective dropping of packets) on incoming flows ...
... the IP header, using the six most significant bits of the IPv4 “type of service” (TOS) octet The edge router may also perform traffic conditioning (e.g., selective dropping of packets) on incoming flows ...