Chapter5link
... Channel Partitioning protocols: FDMA FDMA: frequency division multiple access channel spectrum divided into frequency bands each station assigned fixed frequency band unused transmission time in frequency bands go idle example: 6-station LAN, 1,3,4 have pkt, frequency ...
... Channel Partitioning protocols: FDMA FDMA: frequency division multiple access channel spectrum divided into frequency bands each station assigned fixed frequency band unused transmission time in frequency bands go idle example: 6-station LAN, 1,3,4 have pkt, frequency ...
PCI Compliance - University of Nevada, Reno
... ensure third parties, with whom cardholder data is shared, are contractually required to adhere to the PCI-DSS requirements and to acknowledge they are responsible for the security of the cardholder data which they process. Controller’s Office – The Controller’s Office will verify that all employees ...
... ensure third parties, with whom cardholder data is shared, are contractually required to adhere to the PCI-DSS requirements and to acknowledge they are responsible for the security of the cardholder data which they process. Controller’s Office – The Controller’s Office will verify that all employees ...
User Manual - D-Link
... Large objects such as fish tanks, mirrors, file cabinets, metal doors and aluminum studs may also have a negative effect on range. 4. If you are using 2.4 GHz cordless phones, make sure that the 2.4 GHz phone base is as far away from your wireless device as possible. The base transmits a signal eve ...
... Large objects such as fish tanks, mirrors, file cabinets, metal doors and aluminum studs may also have a negative effect on range. 4. If you are using 2.4 GHz cordless phones, make sure that the 2.4 GHz phone base is as far away from your wireless device as possible. The base transmits a signal eve ...
9781133019862_PPT_ch02
... – Network addresses must be contiguous – When address aggregation occurs • CIDR address blocks work best when they come in sets that are greater than 1 and equal to some lowerorder bit pattern that corresponds to all 1s ...
... – Network addresses must be contiguous – When address aggregation occurs • CIDR address blocks work best when they come in sets that are greater than 1 and equal to some lowerorder bit pattern that corresponds to all 1s ...
Computer Security and Penetration Testing Chapter 17 Linux
... accounts are vulnerable to hacking attempts • Various networking services are available as part of some Linux operating systems; however, these services are highly vulnerable to unauthorized access • Weaknesses within some utilities in both Linux and UNIX-based operating systems allow hackers to bre ...
... accounts are vulnerable to hacking attempts • Various networking services are available as part of some Linux operating systems; however, these services are highly vulnerable to unauthorized access • Weaknesses within some utilities in both Linux and UNIX-based operating systems allow hackers to bre ...
Fallacies of Distributed Computing Explained
... administrator". You may be able to get away with this fallacy if you install your software on small, isolated LANs (for instance, a single person IT "group" with no WAN/Internet). However, for most enterprise systems the reality is much different. The IT group usually has different administrators, a ...
... administrator". You may be able to get away with this fallacy if you install your software on small, isolated LANs (for instance, a single person IT "group" with no WAN/Internet). However, for most enterprise systems the reality is much different. The IT group usually has different administrators, a ...
telecommunications system
... A local area network (LAN) connects two or more devices in a limited geographical region, usually within the same building, so that every device on the network can communicate with every other device. ...
... A local area network (LAN) connects two or more devices in a limited geographical region, usually within the same building, so that every device on the network can communicate with every other device. ...
PowerPoint 프레젠테이션 - Pohang University of
... Who gives the university the domain name “postech.ac.kr” Who assigns it the network prefix “141.223.0.0”? Who assigns port 80 as the default port for web servers? The functions associated with the assignment of numbers is referred to as Internet Assigned Number Authority (IANA). IANA used ...
... Who gives the university the domain name “postech.ac.kr” Who assigns it the network prefix “141.223.0.0”? Who assigns port 80 as the default port for web servers? The functions associated with the assignment of numbers is referred to as Internet Assigned Number Authority (IANA). IANA used ...
A Survey on Network Attacks
... An Intrusion Detection System (or IDS) generally detects unwanted manipulations to computer systems, mainly through the internet. There are many different types of IDS; some of them are described in next section. The manipulations may take the form of attacks by skilled malicious hackers, or script ...
... An Intrusion Detection System (or IDS) generally detects unwanted manipulations to computer systems, mainly through the internet. There are many different types of IDS; some of them are described in next section. The manipulations may take the form of attacks by skilled malicious hackers, or script ...
Develop a Global Network Strategy-SAMPLE - Info
... Attempting to contact local telecom providers, receive concrete information, and get your foreign facilities connected can be a lot like climbing a mountain. There’s always a little bit of uncertainty, and you probably have to take at least one or two leaps of faith without knowing how it will work ...
... Attempting to contact local telecom providers, receive concrete information, and get your foreign facilities connected can be a lot like climbing a mountain. There’s always a little bit of uncertainty, and you probably have to take at least one or two leaps of faith without knowing how it will work ...
Quality of Service in IP Networks
... Creates classes of service for traffic flows with different priorities • Aggregates large numbers of individual flows at the edge of the network into small numbers of aggregated flows through the core of the network • Flows are marked at network edge in the IPv4 ToS field (DS field). • Services appl ...
... Creates classes of service for traffic flows with different priorities • Aggregates large numbers of individual flows at the edge of the network into small numbers of aggregated flows through the core of the network • Flows are marked at network edge in the IPv4 ToS field (DS field). • Services appl ...
L09_TCP_IP - Interactive Computing Lab
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
... We’re making these slides freely available to all (faculty, students, readers). They’re in PowerPoint form so you can add, modify, and delete slides (including this one) and slide content to suit your needs. They obviously represent a lot of work on our part. In return for use, we only ask the follo ...
mobile ip - BWN-Lab
... it will send a broadcast registration to its home network called a direct broadcast. Every valid HA will respond and the MN uses the address of a valid HA to make a registration request. The HA and FA are similar to home and visiting databases – Upon a valid registration, the HA creates an entry ...
... it will send a broadcast registration to its home network called a direct broadcast. Every valid HA will respond and the MN uses the address of a valid HA to make a registration request. The HA and FA are similar to home and visiting databases – Upon a valid registration, the HA creates an entry ...
How medical device companies can safeguard
... (north-south) traffic and internal traffic between physical and virtual hosts with an IP address – for example, laptops, servers, printers, BYOD/personal smart-devices, and IoT devices – regardless of the operating system or application, including traffic between virtual workloads in the data center ...
... (north-south) traffic and internal traffic between physical and virtual hosts with an IP address – for example, laptops, servers, printers, BYOD/personal smart-devices, and IoT devices – regardless of the operating system or application, including traffic between virtual workloads in the data center ...
subscription services brief
... Our high-performance APs, incorporating the latest 802.11ac Wave 2 technology, are a perfect fit for customers of all sizes, including educational institutions, retail, hospitality, and healthcare providers. Completely plug-and-play, our APs are controlled and managed from the cloud and include a bu ...
... Our high-performance APs, incorporating the latest 802.11ac Wave 2 technology, are a perfect fit for customers of all sizes, including educational institutions, retail, hospitality, and healthcare providers. Completely plug-and-play, our APs are controlled and managed from the cloud and include a bu ...
.pdf
... built from such system components thus cannot know with any certainty what software has entered system components or what actions those components might take. The trustworthiness of an NIS encompasses correctness, reliability, security (conventionally including secrecy, confidentiality, integrity, a ...
... built from such system components thus cannot know with any certainty what software has entered system components or what actions those components might take. The trustworthiness of an NIS encompasses correctness, reliability, security (conventionally including secrecy, confidentiality, integrity, a ...
Transport Layer
... be used without IANA registration. The registration procedure is defined in [RFC4340], Section 19.9. The Dynamic and/or Private Ports are those from 49152 through 65535 http://www.iana.org/assignments/port-numbers ...
... be used without IANA registration. The registration procedure is defined in [RFC4340], Section 19.9. The Dynamic and/or Private Ports are those from 49152 through 65535 http://www.iana.org/assignments/port-numbers ...
an OpenSource Virtual Content Distribution Network (vCDN) Platform
... SDN is not a provisioning system or configuration management tool ...
... SDN is not a provisioning system or configuration management tool ...
Botnets: Infrastructure and Attacks
... Cause the bot to display its status Cause the bot to display system information Cause the bot to quit IRC and terminate itself Change the nickname of the bot Completely remove the bot from the system Display the bot version or ID Display the information about the bot Make the bot execute a .EXE file ...
... Cause the bot to display its status Cause the bot to display system information Cause the bot to quit IRC and terminate itself Change the nickname of the bot Completely remove the bot from the system Display the bot version or ID Display the information about the bot Make the bot execute a .EXE file ...
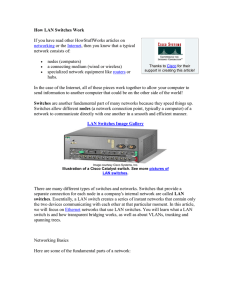
How LAN Switches Work
... segments in the broadcast domain, but a router will not. Think about our four-way intersection again: All of the traffic passed through the intersection no matter where it was going. Now imagine that this intersection is at an international border. To pass through the intersection, you must provide ...
... segments in the broadcast domain, but a router will not. Think about our four-way intersection again: All of the traffic passed through the intersection no matter where it was going. Now imagine that this intersection is at an international border. To pass through the intersection, you must provide ...
Document
... • Advice: use Cat 5, Cat 5e or Cat6 UTP (unshielded twisted pair) • Category 7 and higher marketing hype – Not official IEEE spec ...
... • Advice: use Cat 5, Cat 5e or Cat6 UTP (unshielded twisted pair) • Category 7 and higher marketing hype – Not official IEEE spec ...
Gladiator Startup 1.0
... Consists of all users that are eligible for service The most important property - size o infinite population - arrival rate does not depend on the number of users in the system o finite population - arrival rate depends on the number of users in the system o if the population is large relative t ...
... Consists of all users that are eligible for service The most important property - size o infinite population - arrival rate does not depend on the number of users in the system o finite population - arrival rate depends on the number of users in the system o if the population is large relative t ...