How to contact Acknowledgements
... ♦ is a rare incident, but may be caused by data alternation or loss ♦ also caused by hackers to provoke unusual system behavior ♦ miss insertion and wrong delivery may cause serious problems, therefore some techniques use countermeasurements especially to avoid these problems • out−of−order delivery ...
... ♦ is a rare incident, but may be caused by data alternation or loss ♦ also caused by hackers to provoke unusual system behavior ♦ miss insertion and wrong delivery may cause serious problems, therefore some techniques use countermeasurements especially to avoid these problems • out−of−order delivery ...
Broadband Wireless Access WISP Cookbook June 2003
... the network and to various types of networks. Over time, we witnessed a wide range of situations experienced by our partners: from the management decision-making process to technical and logistic activities by different types of operators: cellular, data access, ISPs and local independent telcos. Un ...
... the network and to various types of networks. Over time, we witnessed a wide range of situations experienced by our partners: from the management decision-making process to technical and logistic activities by different types of operators: cellular, data access, ISPs and local independent telcos. Un ...
Lab Set Up
... Lab 6 – LAN switching LAN switching in Ethernet networks; forwarding of Ethernet frames between LAN switches/bridges; spanning tree protocol for loop free routing between interconnected LANs. Lab 7 - NAT and DHCP Setup of a private network; dynamic assignment of IP addresses with DHCP. Lab 8 – Domai ...
... Lab 6 – LAN switching LAN switching in Ethernet networks; forwarding of Ethernet frames between LAN switches/bridges; spanning tree protocol for loop free routing between interconnected LANs. Lab 7 - NAT and DHCP Setup of a private network; dynamic assignment of IP addresses with DHCP. Lab 8 – Domai ...
siskiyous.edu
... Gain experience with networking equipment Follow general guidelines for each device type Devices most disruptive and complex to add or ...
... Gain experience with networking equipment Follow general guidelines for each device type Devices most disruptive and complex to add or ...
Blueprint For Security Chapter 6
... detect when intruder creates, modifies, or deletes files Most HIDPSs work on the principle of configuration or change management Advantage over NIDPS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 3rd edition ...
... detect when intruder creates, modifies, or deletes files Most HIDPSs work on the principle of configuration or change management Advantage over NIDPS: can usually be installed so that it can access information encrypted when traveling over network Principles of Information Security, 3rd edition ...
Module 15: Network Structures A Distributed System
... ■ Clusters – a collection of semi-autonomous machines ...
... ■ Clusters – a collection of semi-autonomous machines ...
Networks
... Peer-to peer is not suited for networks with many computers. Peer-to-peer is easy to set up. Example: home ...
... Peer-to peer is not suited for networks with many computers. Peer-to-peer is easy to set up. Example: home ...
Chapter5b
... link-layer device: takes an active role store and forward Ethernet frames examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment ...
... link-layer device: takes an active role store and forward Ethernet frames examine incoming frame’s MAC address, selectively forward frame to one-or-more outgoing links when frame is to be forwarded on segment, uses CSMA/CD to access segment ...
Slide 1
... addresses, one each for the three interfaces: eth0, eth1, and eth1:1. For example, for host 101, those would be x.y.z.101 (x.y.z. represents the first three octets of VLabNet’s externally routable IPv4 addresses) for interface eth0 (an externally routable address), 10.10.10.101 for interface eth1 (n ...
... addresses, one each for the three interfaces: eth0, eth1, and eth1:1. For example, for host 101, those would be x.y.z.101 (x.y.z. represents the first three octets of VLabNet’s externally routable IPv4 addresses) for interface eth0 (an externally routable address), 10.10.10.101 for interface eth1 (n ...
Inglés
... RREP to a extremely big value. In our proposal we add a value of eight (as a result from many simulations of different scenarios for our case of study, as explained in the following paragraph) to the sequence number stored in the node’s table. If the sequence number in the RREP is greater than the on ...
... RREP to a extremely big value. In our proposal we add a value of eight (as a result from many simulations of different scenarios for our case of study, as explained in the following paragraph) to the sequence number stored in the node’s table. If the sequence number in the RREP is greater than the on ...
Wireless medical sensor network with ZigBee™
... plaster and is fixed at the chest. This sensor gives information about the movement of the patient. For example while the patient is sleeping, such a sensor counts how often the patient turned around a night or slept in dorsal or prone position. The three axis of movement are analyzed and only the r ...
... plaster and is fixed at the chest. This sensor gives information about the movement of the patient. For example while the patient is sleeping, such a sensor counts how often the patient turned around a night or slept in dorsal or prone position. The three axis of movement are analyzed and only the r ...
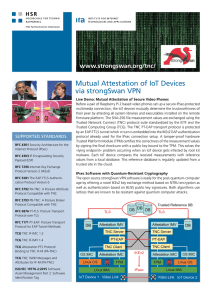
Mutual Attestation of IoT Devices via strongSwan VPN
... by signing the final checksum with a public key bound to the TPM. This solves the «lying endpoint» problem occurring when an IoT device gets infested by root kit malware. Each IoT device compares the received measurements with reference values from a local database. This reference database is regula ...
... by signing the final checksum with a public key bound to the TPM. This solves the «lying endpoint» problem occurring when an IoT device gets infested by root kit malware. Each IoT device compares the received measurements with reference values from a local database. This reference database is regula ...
Mesh Networks - Gordon College
... communication infrastructure between multiple individual wireless tranceivers that have Ethernet capabilities Can either be centralized for highly scalable applications, or can be decentralized ...
... communication infrastructure between multiple individual wireless tranceivers that have Ethernet capabilities Can either be centralized for highly scalable applications, or can be decentralized ...
待讨论问题 - IETF
... The 3GPP has considered some of the security aspects with respect to synchronization performance. The [3GPP.33.820] report lists the following: 1. it may be possible to leave some of the messages unprotected, but there might be security risks. Care should be taken in considering which messages are p ...
... The 3GPP has considered some of the security aspects with respect to synchronization performance. The [3GPP.33.820] report lists the following: 1. it may be possible to leave some of the messages unprotected, but there might be security risks. Care should be taken in considering which messages are p ...
Chord: A Distributed P2P Network
... • The responsible node for this object is the first one that comes after it in the ring ...
... • The responsible node for this object is the first one that comes after it in the ring ...
вбг ¤ вбг ¤ ¥ £ ¤ ¥ time, which represents the зй !" $# . Such one
... The problem of QoS routing for mobile Ad hoc networks is studied. Most routing protocols for the mobile Ad hoc networks (MANETs) [1], such as OLSR [2], AODV [3], DSR [4], are designed without explicitly considering QoS of the routes they generate. The number of hops is the most common criterion adop ...
... The problem of QoS routing for mobile Ad hoc networks is studied. Most routing protocols for the mobile Ad hoc networks (MANETs) [1], such as OLSR [2], AODV [3], DSR [4], are designed without explicitly considering QoS of the routes they generate. The number of hops is the most common criterion adop ...
Network
... stays strung out over the network, potentially blocking other messages (needs only buffer the piece of the packet that is sent between switches). CM-5 uses it, with each switch buffer being 4 bits per port. – Cut through routing lets the tail continue when head is blocked, compresses the whole messa ...
... stays strung out over the network, potentially blocking other messages (needs only buffer the piece of the packet that is sent between switches). CM-5 uses it, with each switch buffer being 4 bits per port. – Cut through routing lets the tail continue when head is blocked, compresses the whole messa ...
15-overlay
... Active Networks • Nodes (routers) receive packets: • Perform computation based on their internal state and control information carried in packet • Forward zero or more packets to end points depending on result of the computation ...
... Active Networks • Nodes (routers) receive packets: • Perform computation based on their internal state and control information carried in packet • Forward zero or more packets to end points depending on result of the computation ...
3G and 4G - Web Services Overview
... Predominantly voice- data as Converged data and VoIP add-on Wide area Cell based Hybrid – integration of Wireless Lan (WiFi), Blue ...
... Predominantly voice- data as Converged data and VoIP add-on Wide area Cell based Hybrid – integration of Wireless Lan (WiFi), Blue ...
Graph Theory – Some Definitions A mathematical representation of
... The neighborhood of a given node n is the set of its neighbors. The connectivity of n, denoted by kn, is the size of its neighborhood. The average number of neighbors indicates the average connectivity of a node in the network. A normalized version of this parameter is the network density. The densi ...
... The neighborhood of a given node n is the set of its neighbors. The connectivity of n, denoted by kn, is the size of its neighborhood. The average number of neighbors indicates the average connectivity of a node in the network. A normalized version of this parameter is the network density. The densi ...
ppt
... velocity from both of the physical layers Select a physical interface based on the measurement data from the physical layer Trigger a vertical handoff or a horizontal handoff Notify an impending handoff to the TCP layer so that the TCP receiver module sets its HO optional field ...
... velocity from both of the physical layers Select a physical interface based on the measurement data from the physical layer Trigger a vertical handoff or a horizontal handoff Notify an impending handoff to the TCP layer so that the TCP receiver module sets its HO optional field ...
Understanding and Testing Gigabit Ethernet Networks
... With the advent of gigabit data rates in the already popular Ethernet protocol, this technology is sure to experience phenomenal growth. This increase in data rate enables new, exciting applications for this mature, well-established technology. These applications now demand proper testing and charac ...
... With the advent of gigabit data rates in the already popular Ethernet protocol, this technology is sure to experience phenomenal growth. This increase in data rate enables new, exciting applications for this mature, well-established technology. These applications now demand proper testing and charac ...
WINDOWS NT SERVER 3.51
... NetBEUI • NetBIOS extended user interface • Standard user interface for LANs of 20 to 200 users • Non-routeable suitable for a single type of network • Purpose: – Communicate with other computers using NetBEUI ...
... NetBEUI • NetBIOS extended user interface • Standard user interface for LANs of 20 to 200 users • Non-routeable suitable for a single type of network • Purpose: – Communicate with other computers using NetBEUI ...
Samantha - SSI Robotics
... The ½” gear hub that is supplied in the TETRIX kit is the right size and is a good choice to use as a spacer for proper strain relief with the original Samantha. Experiment to find the best solution with the newer modules. ...
... The ½” gear hub that is supplied in the TETRIX kit is the right size and is a good choice to use as a spacer for proper strain relief with the original Samantha. Experiment to find the best solution with the newer modules. ...