Developing a formal framework to measure the robustness of networks
... An overlay network is built on top of physical network. Nodes in the overlay can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network. Examples: • P2P overlay network run on top of the Intern ...
... An overlay network is built on top of physical network. Nodes in the overlay can be thought of as being connected by virtual or logical links, each of which corresponds to a path, perhaps through many physical links, in the underlying network. Examples: • P2P overlay network run on top of the Intern ...
Higher Computing – Unit 3
... The monitoring of individuals’ Internet and email use is a contentious issue. Many governments would like to have access to this sort of information. Many individuals would not like them to have this kind of access. With modern communications networks it is theoretically possible to trace the moveme ...
... The monitoring of individuals’ Internet and email use is a contentious issue. Many governments would like to have access to this sort of information. Many individuals would not like them to have this kind of access. With modern communications networks it is theoretically possible to trace the moveme ...
Chapter04
... • A 32-bit value that allows the recipient of IP packets to distinguish the network ID portion of the IP address from the host ID portion. ...
... • A 32-bit value that allows the recipient of IP packets to distinguish the network ID portion of the IP address from the host ID portion. ...
performance-analysis
... TCP session reset without completing 3-way handshake Two MAC addresses found for the same IP address UDP data to a closed port Unknown protocol (no HTTP/FTP/SMTP/SSH) detected (on port 80/21/25/22) Unusual ICMP options ...
... TCP session reset without completing 3-way handshake Two MAC addresses found for the same IP address UDP data to a closed port Unknown protocol (no HTTP/FTP/SMTP/SSH) detected (on port 80/21/25/22) Unusual ICMP options ...
Virtual Router VPN Architecture
... A virtual router (VR) is an emulation of a physical router at the software and hardware levels VRs have independent IP routing and forwarding tables and they are isolated from each other Two main functions ...
... A virtual router (VR) is an emulation of a physical router at the software and hardware levels VRs have independent IP routing and forwarding tables and they are isolated from each other Two main functions ...
Global Terabit Research Network
... 5154 terabit-meters/second; 384.22 Mb/s Better than any previous single/multiple IPv4 or IPv6 Concurrently with the production traffic ...
... 5154 terabit-meters/second; 384.22 Mb/s Better than any previous single/multiple IPv4 or IPv6 Concurrently with the production traffic ...
PPT - University of Cincinnati
... * Use index based on meta data called descriptive strings * In order to retrieve a piece from Freenet network, the user must first derive, or know a key which matches the file associated with the item. * This request is sent to the querying node’s neighbor, which forwards the request to its neighbor ...
... * Use index based on meta data called descriptive strings * In order to retrieve a piece from Freenet network, the user must first derive, or know a key which matches the file associated with the item. * This request is sent to the querying node’s neighbor, which forwards the request to its neighbor ...
Virtual Private Networking over MPDS
... As VPNs must encrypt and decrypt all packets, this can put a considerable load on the VPN server (and client), as well as on the corporate network and Internet connection. VPN servers are either hardware solutions (encrypting routers), firewall solutions (plug-in modules for firewalls), or software ...
... As VPNs must encrypt and decrypt all packets, this can put a considerable load on the VPN server (and client), as well as on the corporate network and Internet connection. VPN servers are either hardware solutions (encrypting routers), firewall solutions (plug-in modules for firewalls), or software ...
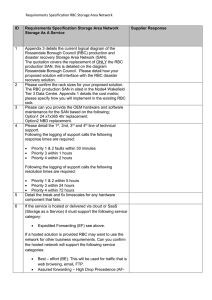
Appendix 2. Requirements Specification RBC Storage Area Network
... Please detail how you will provide effective change, configuration and release management. A detailed process has to be in place. An Internet based portal or website must be provided to the supplier’s service desk. This must include reporting tools for incident management, change management and perf ...
... Please detail how you will provide effective change, configuration and release management. A detailed process has to be in place. An Internet based portal or website must be provided to the supplier’s service desk. This must include reporting tools for incident management, change management and perf ...
GPRS
... Address of the VLR currently serving the MS IP address of the new SGSN where the buffered packets should be forwarded Authentication and ciphering parameters Current ciphering key Kc and the selected ciphering algorithm MS radio access capabilities and GPRS network access capabilities MNRG (Mobile S ...
... Address of the VLR currently serving the MS IP address of the new SGSN where the buffered packets should be forwarded Authentication and ciphering parameters Current ciphering key Kc and the selected ciphering algorithm MS radio access capabilities and GPRS network access capabilities MNRG (Mobile S ...
History and technical background
... CTO / DFID Internet Policy workshop, Jamaica, 22-26 April 2002 ...
... CTO / DFID Internet Policy workshop, Jamaica, 22-26 April 2002 ...
RIP/OSPF
... RIP Operation • Uses simple distance-vector routing • Partitions participants into – Active: advertises routes to other participants – Silent: only listen to routes. Do not advertise route tables ...
... RIP Operation • Uses simple distance-vector routing • Partitions participants into – Active: advertises routes to other participants – Silent: only listen to routes. Do not advertise route tables ...
bgp header
... • Routers/hosts with default routes rely on other routers to complete the picture. • In general routing information should be: – Consistent, I.e., if packet is sent off in one direction then another direction should not be more optimal – Complete, I.e., should be able to reach all destinations ...
... • Routers/hosts with default routes rely on other routers to complete the picture. • In general routing information should be: – Consistent, I.e., if packet is sent off in one direction then another direction should not be more optimal – Complete, I.e., should be able to reach all destinations ...
powerpoint lecture
... – Location outside the firewalls (or between firewalls) – More vulnerable to attack from outside – Separates services offered internally from those offered externally – Protected by router filters – Allows each server a particular service – Another firewall exists on the other side ...
... – Location outside the firewalls (or between firewalls) – More vulnerable to attack from outside – Separates services offered internally from those offered externally – Protected by router filters – Allows each server a particular service – Another firewall exists on the other side ...
Cooper Bussmann 945U-E Wireless Ethernet Modem & Device Server User Manual
... This device complies with Part 15.247 of the FCC Rules. Operation is subject to the following two conditions: • This device may not cause harmful interference, and • This device must accept any interference received, including interference that may cause undesired operation. This device must be op ...
... This device complies with Part 15.247 of the FCC Rules. Operation is subject to the following two conditions: • This device may not cause harmful interference, and • This device must accept any interference received, including interference that may cause undesired operation. This device must be op ...
Slides
... physically-connected interface (same network) 48 bit MAC address (for most LANs) burned in the adapter ROM ...
... physically-connected interface (same network) 48 bit MAC address (for most LANs) burned in the adapter ROM ...
Before You Begin: Assign Information Classification
... Current Challenges with Technology in Schools Network connections are needed throughout schools, but infrastructure cannot support needs ...
... Current Challenges with Technology in Schools Network connections are needed throughout schools, but infrastructure cannot support needs ...
VoCCN: Voice-over Content
... VoIP Signaling and Media paths result from a mismatch between the user’s goal and the network’s meaning of achieving it. Alice simply wants to talk to Bob but the network requires that the communication be addressed to the IP address of Bob’s phone. ...
... VoIP Signaling and Media paths result from a mismatch between the user’s goal and the network’s meaning of achieving it. Alice simply wants to talk to Bob but the network requires that the communication be addressed to the IP address of Bob’s phone. ...
Default Routes - University of Windsor
... between R1 and D? R1 will detect the change and look for ...
... between R1 and D? R1 will detect the change and look for ...
Measurement Based Routing Strategies on Overlay Architectures Tuna G ¨uven
... • Experiment done under Network Model-I under Sprint backbone topology ...
... • Experiment done under Network Model-I under Sprint backbone topology ...
TLC_Requirements_TI+AlcatelLucent
... – Embedded computing at lower level inside the network to make efficient, timely and secure the data processing ( filtering, aggregation and correlation mechanisms); Perform analysis and diagnosis useful for the infrastructure where MIT components are installed and for other infrastructures with whi ...
... – Embedded computing at lower level inside the network to make efficient, timely and secure the data processing ( filtering, aggregation and correlation mechanisms); Perform analysis and diagnosis useful for the infrastructure where MIT components are installed and for other infrastructures with whi ...
Wireless Communication Technologies in Healthcare Market - Global Industry Analysis and Forecast 2016 - 2022
... Ultra Wide Band (UWB) UWB is a radio technology that uses very low energy level for short range and high bandwidth communication over a large portion of the radio spectrum. Healthcare systems can be significantly improved with lower coast and higher quality of services by using ultra wide band techn ...
... Ultra Wide Band (UWB) UWB is a radio technology that uses very low energy level for short range and high bandwidth communication over a large portion of the radio spectrum. Healthcare systems can be significantly improved with lower coast and higher quality of services by using ultra wide band techn ...
Visual Mining of Multi-Modal Social Networks at Different Abstraction
... underlying matrix representation of the graph, this commercial product supports merging and decomposing of matrices as well as translation of multi-valued attributes into binary variables for statistical operations. Each node can have multiple attribute values assigned by the user. A very nice featu ...
... underlying matrix representation of the graph, this commercial product supports merging and decomposing of matrices as well as translation of multi-valued attributes into binary variables for statistical operations. Each node can have multiple attribute values assigned by the user. A very nice featu ...