Administration Guide - SUSE Linux Enterprise Desktop 12 SP2
... system. This part introduces a few of them. System ...
... system. This part introduces a few of them. System ...
The Ultimate Computer Acronyms Archive
... «I'm sitting in a coffee shop in Milford, NH. In the booth next to me are two men, a father and a son. Over coffee, the father is asking his son about modems, and the son is holding forth pretty well on the subject of fax compatibility, UART requirements, and so on. But he's little out of date: The ...
... «I'm sitting in a coffee shop in Milford, NH. In the booth next to me are two men, a father and a son. Over coffee, the father is asking his son about modems, and the son is holding forth pretty well on the subject of fax compatibility, UART requirements, and so on. But he's little out of date: The ...
The Gartner Glossary - SUNY Center for Professional Development
... for wireless local-area networks (WLANs). Various specifications cover WLAN transmission speeds from one megabit per second (Mbps) to 54 Mbps. There are three main physical-layer standards — see 802.11a, 802.11b and 802.11g. 802.11a An Institute of Electrical and Electronics Engineers standard for t ...
... for wireless local-area networks (WLANs). Various specifications cover WLAN transmission speeds from one megabit per second (Mbps) to 54 Mbps. There are three main physical-layer standards — see 802.11a, 802.11b and 802.11g. 802.11a An Institute of Electrical and Electronics Engineers standard for t ...
21-06-0664-00-0000-QoS_considerations_in_NIHO_v3
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
TR-0024-3GPP_Rel13_IWK-V2_0_1 - FTP
... © 2016, oneM2M Partners Type 1 (ARIB, ATIS, CCSA, ETSI, TIA, TSDSI, TTA, TTC). ...
... © 2016, oneM2M Partners Type 1 (ARIB, ATIS, CCSA, ETSI, TIA, TSDSI, TTA, TTC). ...
(Backup) MDR
... there exists a bidirectional neighbor that does not satisfy condition (a) or (b). If a Backup MDR receives a new LSA, it waits BackupWaitInterval seconds, and then floods the LSA back out the receiving interface if there exists a bidirectional neighbor that does not satisfy condition (a) or (b). An ...
... there exists a bidirectional neighbor that does not satisfy condition (a) or (b). If a Backup MDR receives a new LSA, it waits BackupWaitInterval seconds, and then floods the LSA back out the receiving interface if there exists a bidirectional neighbor that does not satisfy condition (a) or (b). An ...
6 – Transport Layer
... • Need to find the situations and improve the protocols Examples: • Broadcast storm: one broadcast triggers another • Synchronization: a building of computers all contact the DHCP server together after a power failure • Tiny packets: some situations can cause TCP to send many small packets instead o ...
... • Need to find the situations and improve the protocols Examples: • Broadcast storm: one broadcast triggers another • Synchronization: a building of computers all contact the DHCP server together after a power failure • Tiny packets: some situations can cause TCP to send many small packets instead o ...
D3.2 Traffic Models
... Internet usage is evolving, from the traditional WWW usage (i.e. downloading web pages), to tripleplay usage where households may have all their communication services (telephony, data, TV) through their broadband access connection. The challenge is to design IP access networks so that they can deli ...
... Internet usage is evolving, from the traditional WWW usage (i.e. downloading web pages), to tripleplay usage where households may have all their communication services (telephony, data, TV) through their broadband access connection. The challenge is to design IP access networks so that they can deli ...
XBee® 865/868LP RF Modules
... XBee modules are designed to be self sufficient and have minimal sensitivity to nearby processors, crystals or other PCB components. As with all PCB designs, Power and Ground traces should be thicker than signal traces and able to comfortably support the maximum current specifications. A recommended ...
... XBee modules are designed to be self sufficient and have minimal sensitivity to nearby processors, crystals or other PCB components. As with all PCB designs, Power and Ground traces should be thicker than signal traces and able to comfortably support the maximum current specifications. A recommended ...
csci5211: Computer Networks and Data Communications
... – Members do not know delay to each other when they join – Members probe each other to learn network related information – Overlay must self-improve as more information available ...
... – Members do not know delay to each other when they join – Members probe each other to learn network related information – Overlay must self-improve as more information available ...
Overview of Scalable Networks
... At a minimum the algorithm must specify: – A procedure for passing reachability information about networks to other routers. – A procedure for receiving reachability information from other routers. – A procedure for determining optimal routes based on the reachability information it has and for reco ...
... At a minimum the algorithm must specify: – A procedure for passing reachability information about networks to other routers. – A procedure for receiving reachability information from other routers. – A procedure for determining optimal routes based on the reachability information it has and for reco ...
ITE PC v4.0 Chapter 1
... Interfaces and Ports Network communications depend on end user device interfaces, networking device interfaces, and the cables that connect them Types of network media include twisted-pair copper cables, fiberoptic cables, coaxial cables, or wireless Different types of network media have diffe ...
... Interfaces and Ports Network communications depend on end user device interfaces, networking device interfaces, and the cables that connect them Types of network media include twisted-pair copper cables, fiberoptic cables, coaxial cables, or wireless Different types of network media have diffe ...
Design and Implementation of a Routing Control Platform Matthew Caesar Donald Caldwell
... The RCP’s IGP Viewer monitors the IGP topology and provides this information to the RCS. The IGP Viewer establishes IGP adjacencies to receive the IGP’s linkstate advertisements (LSAs). To ensure that the IGP Viewer never routes data packets, the links between the IGP Viewer and the routers should b ...
... The RCP’s IGP Viewer monitors the IGP topology and provides this information to the RCS. The IGP Viewer establishes IGP adjacencies to receive the IGP’s linkstate advertisements (LSAs). To ensure that the IGP Viewer never routes data packets, the links between the IGP Viewer and the routers should b ...
A Close Examination of Performance and Power Characteristics of
... 24], we design a new mobile network measurement tool for Android devices, called 4GTest [2], with higher accuracy and improved user experience. As a new feature, 4GTest allows users to switch among different network types, i.e., 3G, WiFi and LTE. We also improve the network measurement methodology l ...
... 24], we design a new mobile network measurement tool for Android devices, called 4GTest [2], with higher accuracy and improved user experience. As a new feature, 4GTest allows users to switch among different network types, i.e., 3G, WiFi and LTE. We also improve the network measurement methodology l ...
Design and Implementation of a Routing Control Platform Matthew Caesar Donald Caldwell
... The RCP’s IGP Viewer monitors the IGP topology and provides this information to the RCS. The IGP Viewer establishes IGP adjacencies to receive the IGP’s linkstate advertisements (LSAs). To ensure that the IGP Viewer never routes data packets, the links between the IGP Viewer and the routers should b ...
... The RCP’s IGP Viewer monitors the IGP topology and provides this information to the RCS. The IGP Viewer establishes IGP adjacencies to receive the IGP’s linkstate advertisements (LSAs). To ensure that the IGP Viewer never routes data packets, the links between the IGP Viewer and the routers should b ...
MAC address
... =2">edit]Address details
... =2">edit]Address details

PDF
... With Cisco Resource Pool Manager (RPM), telephone companies and Internet service providers (ISPs) can share dial resources for wholesale and retail dial network services in a single network access server (NAS) or across multiple NAS stacks. Call management and call discrimination can be configured t ...
... With Cisco Resource Pool Manager (RPM), telephone companies and Internet service providers (ISPs) can share dial resources for wholesale and retail dial network services in a single network access server (NAS) or across multiple NAS stacks. Call management and call discrimination can be configured t ...
What is Cisco SDM? - College of DuPage
... web-based device-management tool designed for configuring LAN, WAN, and security features on Cisco IOS software-based routers. –It provides easy-to-use smart wizards, –automates router security management, –assists through comprehensive online help. ...
... web-based device-management tool designed for configuring LAN, WAN, and security features on Cisco IOS software-based routers. –It provides easy-to-use smart wizards, –automates router security management, –assists through comprehensive online help. ...
Network Loss Inference with Second Order Statistics
... throughout the measurement period. • T.2 No route fluttering: There is no pair of paths Pi and Pi′ that share two links ej and ej ′ without also sharing all the links located in between ej and ej ′ . That is, the two paths never meet at one link, diverge, and meet again further away at another link. ...
... throughout the measurement period. • T.2 No route fluttering: There is no pair of paths Pi and Pi′ that share two links ej and ej ′ without also sharing all the links located in between ej and ej ′ . That is, the two paths never meet at one link, diverge, and meet again further away at another link. ...
ExperimenTor: A Testbed for Safe and Realistic Tor Experimentation Kevin Bauer
... these experiments offer valuable insight into the proposed selection technique, they do not analyze the behavior of the proposed algorithm when many or all Tor clients use various configurations of tunable selection. Similarly, Tang and Goldberg [35] evaluate their proposed circuit scheduling algori ...
... these experiments offer valuable insight into the proposed selection technique, they do not analyze the behavior of the proposed algorithm when many or all Tor clients use various configurations of tunable selection. Similarly, Tang and Goldberg [35] evaluate their proposed circuit scheduling algori ...
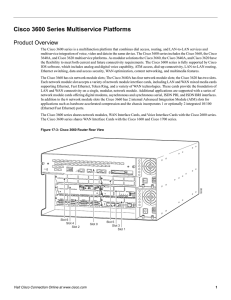
Cisco 3600 Series Multiservice Platforms
... Many corporate environments require support for a mixture of ISDN PRI, ISDN BRI, asynchronous serial, and synchronous serial connections. The Cisco 3600 series is ideal for this scenario. It allows migration between interfaces or simultaneous support of several technologies. ...
... Many corporate environments require support for a mixture of ISDN PRI, ISDN BRI, asynchronous serial, and synchronous serial connections. The Cisco 3600 series is ideal for this scenario. It allows migration between interfaces or simultaneous support of several technologies. ...
Ch 11-OSPF
... OSPF in Multiaccess Networks Criteria for getting elected DR/BDR 1. DR: Router with the highest OSPF interface priority. 2. BDR: Router with the second highest OSPF interface priority. 3. If OSPF interface priorities are equal, the highest router ID is used to break the tie. ...
... OSPF in Multiaccess Networks Criteria for getting elected DR/BDR 1. DR: Router with the highest OSPF interface priority. 2. BDR: Router with the second highest OSPF interface priority. 3. If OSPF interface priorities are equal, the highest router ID is used to break the tie. ...