DESIGN AND IMPLEMENTATION OF A WIRELESS ZIGBEE MESH NETWORK
... low-cost and low-power. For the XBee RF module, it does not need too much power and it can provide a reliable way to communicate between two or more devices. It interfaces to a host device through a logic-level asynchronous serial port. Through its serial port, the module can communicate with any lo ...
... low-cost and low-power. For the XBee RF module, it does not need too much power and it can provide a reliable way to communicate between two or more devices. It interfaces to a host device through a logic-level asynchronous serial port. Through its serial port, the module can communicate with any lo ...
Chapter 6 slides, Computer Networking, 3rd edition
... - Replace a single high power base station with several lower power base stations, each covering a smaller geographical area, a ‘cell’. - Each of the base stations is allocated a number of channels (portion of the overall system channels) 6: Wireless and Mobile Networks ...
... - Replace a single high power base station with several lower power base stations, each covering a smaller geographical area, a ‘cell’. - Each of the base stations is allocated a number of channels (portion of the overall system channels) 6: Wireless and Mobile Networks ...
C4 CMTS
... ▪ Impact: The affected voice line is disabled. Look for Voice Line Protection State Change logs to determine which line is in the fault condition. ▪ Action: Run the line card diagnostics on the NIU. If the NIU fails diagnostics, disconnect the house wiring from the NIU and proceed as follows: ▪ If t ...
... ▪ Impact: The affected voice line is disabled. Look for Voice Line Protection State Change logs to determine which line is in the fault condition. ▪ Action: Run the line card diagnostics on the NIU. If the NIU fails diagnostics, disconnect the house wiring from the NIU and proceed as follows: ▪ If t ...
DHCP - Personal Web Pages
... Configuration processes enters its final phase Acknowledgement phase involves sending a DHCPACK packet to the ...
... Configuration processes enters its final phase Acknowledgement phase involves sending a DHCPACK packet to the ...
Hardware Firewall
... purchase Internet Security/Firewall software licenses for 10 to 50 copies, and that too on an annual subscription basis, it will cost a lot of money and deployment could also be an issue. The users will have better control over the environment. If the user is not tech savvy and if they choose to ina ...
... purchase Internet Security/Firewall software licenses for 10 to 50 copies, and that too on an annual subscription basis, it will cost a lot of money and deployment could also be an issue. The users will have better control over the environment. If the user is not tech savvy and if they choose to ina ...
in Word DOC
... purchase Internet Security/Firewall software licenses for 10 to 50 copies, and that too on an annual subscription basis, it will cost a lot of money and deployment could also be an issue. The users will have better control over the environment. If the user is not tech savvy and if they choose to ina ...
... purchase Internet Security/Firewall software licenses for 10 to 50 copies, and that too on an annual subscription basis, it will cost a lot of money and deployment could also be an issue. The users will have better control over the environment. If the user is not tech savvy and if they choose to ina ...
Security Scheme Implementation in Mobile Information
... mobile-phone SMS encryption system" by Qun Ding is the recent work done on mobile security [11]. The author made a contribution to improve the present RSA algorithm. He proposed a security scheme consisting of the following aspects: Using FPGA to implement RSA algorithm Transmitting short messag ...
... mobile-phone SMS encryption system" by Qun Ding is the recent work done on mobile security [11]. The author made a contribution to improve the present RSA algorithm. He proposed a security scheme consisting of the following aspects: Using FPGA to implement RSA algorithm Transmitting short messag ...
Network Properties, Scalability and Requirements For Parallel Processing
... Contention: Several packets trying to use the same link/node at same time. – May be caused by limited available buffering. – Possible resolutions/prevention: • Drop one or more packets (once contention occurs). i.e to resolve contention • Increased buffer space. i.e. Dynamic • Use an alternative rou ...
... Contention: Several packets trying to use the same link/node at same time. – May be caused by limited available buffering. – Possible resolutions/prevention: • Drop one or more packets (once contention occurs). i.e to resolve contention • Increased buffer space. i.e. Dynamic • Use an alternative rou ...
Transitioning to IPv6
... DHCPv6 and DNS > Supports stateful configuration with DHCPv6 > Node has option to solicit an address via DHCP server when a router is not found > DHCPv6 is similar to DHCPv4 > DHCPv6 uses multicast for messaging > New record type to accommodate IPv6 addressing in DNS ...
... DHCPv6 and DNS > Supports stateful configuration with DHCPv6 > Node has option to solicit an address via DHCP server when a router is not found > DHCPv6 is similar to DHCPv4 > DHCPv6 uses multicast for messaging > New record type to accommodate IPv6 addressing in DNS ...
PPT - Globus Toolkit
... • Bulk data transfer has become one of the key requirements in many Grid applications • GridFTP has been widely deployed for high-speed data transport services • These services normally require reliable data transfer resulting in TCP as the preferred common base protocol • Unfortunately TCP performs ...
... • Bulk data transfer has become one of the key requirements in many Grid applications • GridFTP has been widely deployed for high-speed data transport services • These services normally require reliable data transfer resulting in TCP as the preferred common base protocol • Unfortunately TCP performs ...
Madhuri Velugotla-ZigBee_Final. ppt
... ZigBee is the set of specs built around the IEEE 802.15.4 wireless protocol. The name "ZigBee" is derived from the erratic zigzag patterns many bees make between flowers when collecting pollen. This is evocative of the invisible webs of connections existing in a fully wireless environment. The stand ...
... ZigBee is the set of specs built around the IEEE 802.15.4 wireless protocol. The name "ZigBee" is derived from the erratic zigzag patterns many bees make between flowers when collecting pollen. This is evocative of the invisible webs of connections existing in a fully wireless environment. The stand ...
gofileroom performance whitepaper
... backbone). Since many ‘hops’ are necessary to reach the destination website potential for delays may occur. This delay is called latency and may impact performance. Latency is a measure of the delay for a packet to travel from a source (your workstation) to a destination (web server). The higher the ...
... backbone). Since many ‘hops’ are necessary to reach the destination website potential for delays may occur. This delay is called latency and may impact performance. Latency is a measure of the delay for a packet to travel from a source (your workstation) to a destination (web server). The higher the ...
TCP Proxy
... – The shorter the DelayACK timer, the faster the connection reaches steady state – The shorter the DelayACK timer, the higher the probability to send an ACK without necessity – 50ms timer seems to be the best tradeoff between fast connection setup and low probability of unnecesarily sending ACKs in ...
... – The shorter the DelayACK timer, the faster the connection reaches steady state – The shorter the DelayACK timer, the higher the probability to send an ACK without necessity – 50ms timer seems to be the best tradeoff between fast connection setup and low probability of unnecesarily sending ACKs in ...
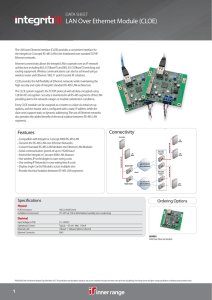
LAN Over Ethernet Module (CLOE)
... The LAN over Ethernet Interface (CLOE) provides a convenient interface for the Integriti (or Concept) RS-485 LAN to be distributed over standard TCP/IP Ethernet networks. Ethernet connectivity allows the Integriti LAN to operate over an IP network architecture including 802.3i (10baseT) and 802.3U ( ...
... The LAN over Ethernet Interface (CLOE) provides a convenient interface for the Integriti (or Concept) RS-485 LAN to be distributed over standard TCP/IP Ethernet networks. Ethernet connectivity allows the Integriti LAN to operate over an IP network architecture including 802.3i (10baseT) and 802.3U ( ...
Chapter 08.ppt
... Corporation computers (now Compaq) • Has evolved over the years to a peer network • DNA Structured Model – Has eight layers – Many hardware platforms need to communicate ...
... Corporation computers (now Compaq) • Has evolved over the years to a peer network • DNA Structured Model – Has eight layers – Many hardware platforms need to communicate ...
Red Team Instrumentation
... – Forces attackers to reach all machines at once – Networks work together to defeat exploitation attempts including reverse engineering attacks, viruses, and rootkits ...
... – Forces attackers to reach all machines at once – Networks work together to defeat exploitation attempts including reverse engineering attacks, viruses, and rootkits ...
Li-Fi-based IoT4bdg - Denny Darlis
... physical objects or "things" embedded with electronics, software, sensors, and network connectivity, which enables these objects to collect and exchange data.[1] ...
... physical objects or "things" embedded with electronics, software, sensors, and network connectivity, which enables these objects to collect and exchange data.[1] ...
public network
... • Once VPN configured, the company's sites can only communicate with one another – they are cut off from the rest of the NW. ...
... • Once VPN configured, the company's sites can only communicate with one another – they are cut off from the rest of the NW. ...
FiOS Quantum Gateway
... information about your device, including the default settings for the Gateway’s wireless network name (ESSID), wireless password (WPA2 key), local URL for accessing the Gateway’s administrative pages, and Gateway administrator password. The label also contains a QR code that you can scan with your s ...
... information about your device, including the default settings for the Gateway’s wireless network name (ESSID), wireless password (WPA2 key), local URL for accessing the Gateway’s administrative pages, and Gateway administrator password. The label also contains a QR code that you can scan with your s ...
UltraLight - Internet2
... • Packet switched: Many applications can effectively utilize the existing, cost effective networks provided by shared packet switched infrastructure. A subset of applications require more stringent guarantees than a best-effort network can provide, and so we are planning to utilize MPLS as an interm ...
... • Packet switched: Many applications can effectively utilize the existing, cost effective networks provided by shared packet switched infrastructure. A subset of applications require more stringent guarantees than a best-effort network can provide, and so we are planning to utilize MPLS as an interm ...
module02-review
... • The complexity of the communication task is reduced by using multiple protocol layers: • Each protocol is implemented independently • Each protocol is responsible for a specific subtask • Protocols are grouped in a hierarchy • A structured set of protocols is called a communications architecture o ...
... • The complexity of the communication task is reduced by using multiple protocol layers: • Each protocol is implemented independently • Each protocol is responsible for a specific subtask • Protocols are grouped in a hierarchy • A structured set of protocols is called a communications architecture o ...
Document
... • The Infected node (K, or I) reports the discovered suspicious neighbors (J, or F) to the M‐server, and forwards the checksum to the reported suspicious neighbors (J, or F). ...
... • The Infected node (K, or I) reports the discovered suspicious neighbors (J, or F) to the M‐server, and forwards the checksum to the reported suspicious neighbors (J, or F). ...