IP Internet Protocol Based on notes from D. Hollinger Netprog 2002 TCP/IP
... A: It depends on the application. TCP provides a connection-oriented, reliable byte stream service (lots of overhead). ...
... A: It depends on the application. TCP provides a connection-oriented, reliable byte stream service (lots of overhead). ...
Designing an LTE Network Using EDX SignalPro
... The user also has the option of modifying the default Adaptive Modulation and Coding to C/(I+N) mapping for both uplink and downlink studies. The LTE E-UTRA standard defines 3 modulations (QPSK, 16QAM and 64QAM) with 15 different usable CQI levels (1-15) that determine the modulation and channel cod ...
... The user also has the option of modifying the default Adaptive Modulation and Coding to C/(I+N) mapping for both uplink and downlink studies. The LTE E-UTRA standard defines 3 modulations (QPSK, 16QAM and 64QAM) with 15 different usable CQI levels (1-15) that determine the modulation and channel cod ...
Bluetooth-an Enabler for Personal Area Networking Presentation
... often referred to as a personal area network (PAN). Access to the Internet via a (public)wireless LAN (WLAN) access point and/or via a third-generation (3G) cellular phone would enable the devices in the PAN to be constantly on-line. Bluetooth presents a number of technical challenges from a network ...
... often referred to as a personal area network (PAN). Access to the Internet via a (public)wireless LAN (WLAN) access point and/or via a third-generation (3G) cellular phone would enable the devices in the PAN to be constantly on-line. Bluetooth presents a number of technical challenges from a network ...
BBSM Services
... The server queries the network device's MIB to detect when the link status for the client's port becomes inactive. ...
... The server queries the network device's MIB to detect when the link status for the client's port becomes inactive. ...
PPT - CCSS
... Detection System (IDS) approaches ◦ IDS protects local hosts within its perimeter (LAN) ◦ An enumerator would identify both local as well as remote infections ...
... Detection System (IDS) approaches ◦ IDS protects local hosts within its perimeter (LAN) ◦ An enumerator would identify both local as well as remote infections ...
Chapter 1: A First Look at Windows 2000 Professional
... Internet Service Provider (ISP) – Provides a service or membership that allows you to access the information available on the Internet. Dialup Connection – A connecting device to a network via modem or a public telephone network. Dialup access acts just like a phone connection, except that the two c ...
... Internet Service Provider (ISP) – Provides a service or membership that allows you to access the information available on the Internet. Dialup Connection – A connecting device to a network via modem or a public telephone network. Dialup access acts just like a phone connection, except that the two c ...
WiMAX-3GPP Optimized Handover
... ND&S a big issue only for 802.11 networks – Not such a big issue for other networks operating primarily in licensed bands – Inter-RAT Neighbor Advertisements are good enough – Operators skeptical about dedicated IS server ...
... ND&S a big issue only for 802.11 networks – Not such a big issue for other networks operating primarily in licensed bands – Inter-RAT Neighbor Advertisements are good enough – Operators skeptical about dedicated IS server ...
... should have the adaptability and ability to measure the concentration of greenhouse gases with a minimum response time and a high precession [7]-[13]. In recent years, wireless sensor networks/actuators and data harvesting technology have played an important role in the area of environment monitorin ...
User Manual for NetSH Tool ns- W
... 10 Developed by WiNG, NITK, Surathkal, Mangalore, India. http://wing.nitk.ac.in ...
... 10 Developed by WiNG, NITK, Surathkal, Mangalore, India. http://wing.nitk.ac.in ...
Network Support for IP Traceback - David Wetherall
... attack. For example, an attack may consist of packets sent from many different slave machines, themselves under the control of a remote master machine. Such indirection may be achieved either explicitly (by compromising the individual slave hosts directly) or implicitly (by sending false requests to ...
... attack. For example, an attack may consist of packets sent from many different slave machines, themselves under the control of a remote master machine. Such indirection may be achieved either explicitly (by compromising the individual slave hosts directly) or implicitly (by sending false requests to ...
Online IP CIDR / VLSM Supernet Calculator
... Without CIDR, our routing table would need to maintain a seperate entry for each of the eight individual networks. As the eight example networks are contiguous, i.e. their address spaces follow numerically with no gaps, we can encapsulate all eight with a single CIDR route by simply changing the sub ...
... Without CIDR, our routing table would need to maintain a seperate entry for each of the eight individual networks. As the eight example networks are contiguous, i.e. their address spaces follow numerically with no gaps, we can encapsulate all eight with a single CIDR route by simply changing the sub ...
Live migration of processes maintaining multiple
... Maintain a massive amount of network connections (clients) Maintain connections with other in-cluster components How to migrate such processes? IEEE Cluster2010 ...
... Maintain a massive amount of network connections (clients) Maintain connections with other in-cluster components How to migrate such processes? IEEE Cluster2010 ...
Using Loss Pairs to Discover Network Properties
... 3. p1 and p2 traverse the same sequence of links and routers up to the point where one of them is dropped. In all of the estimations used in this paper we take In an active measurement setting, this is the natural choice. In a passive measurement setting, such as we consider here, increasing would s ...
... 3. p1 and p2 traverse the same sequence of links and routers up to the point where one of them is dropped. In all of the estimations used in this paper we take In an active measurement setting, this is the natural choice. In a passive measurement setting, such as we consider here, increasing would s ...
UMTS GSM
... IPv6 does contain QOS headers, which can be used with the correctly configured hardware All 3G devices could have a single IP address that would not need to change ...
... IPv6 does contain QOS headers, which can be used with the correctly configured hardware All 3G devices could have a single IP address that would not need to change ...
Ethernet Switches
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
... in shared mode, CSMA/CD is used; short distances between nodes to be efficient uses Star topology with hub, called here ''Buffered Distributor'‘ or switch at center Full-Duplex at 1 Gbps for point-to-point links Serves as a backbone for interconnecting multiple 10Mbps, 100 Mbps Ethernet LANs ...
Poland`s leading telco
... Some of the information included in this material contains forward-looking statements. Readers are cautioned that any such forward-looking statements are not guarantees of future performance and involve risks and uncertainties, and that actual results may differ materially from those in the forward- ...
... Some of the information included in this material contains forward-looking statements. Readers are cautioned that any such forward-looking statements are not guarantees of future performance and involve risks and uncertainties, and that actual results may differ materially from those in the forward- ...
Note
... (1) A local area network (LAN) is a computer network that is designed for a limited geographic area such as a building or a campus. (2) Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LANs today are also linked ...
... (1) A local area network (LAN) is a computer network that is designed for a limited geographic area such as a building or a campus. (2) Although a LAN can be used as an isolated network to connect computers in an organization for the sole purpose of sharing resources, most LANs today are also linked ...
OSI Reference Model
... transmitted on the network medium as bits. During decapsulation on the receiving host, the reverse occurs: • The frame is received from the physical medium. • The Data-Link layer processes its header, strips it off, and then hands it off to the Network layer. • The Network layer processes its header ...
... transmitted on the network medium as bits. During decapsulation on the receiving host, the reverse occurs: • The frame is received from the physical medium. • The Data-Link layer processes its header, strips it off, and then hands it off to the Network layer. • The Network layer processes its header ...
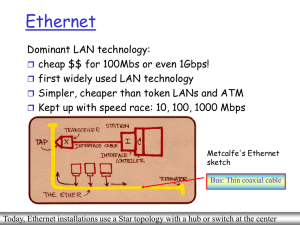
Ethernet
... For Router-on-a-stick configuration, _________________ Configure interfaces (__________ for Router-on-a-stick) ...
... For Router-on-a-stick configuration, _________________ Configure interfaces (__________ for Router-on-a-stick) ...
A Critical Analysis of Layer 2 Network Security in Virtualized
... Typically virtualized hosting environments will utilize either a bridged network interface or a virtualized switch such as Open vSwitch[31, 32] for Xen and KVM based environments, or the Cisco Nexus 1000V Series virtual switch for VMware vSphere environments[12]. These virtual switches are designed ...
... Typically virtualized hosting environments will utilize either a bridged network interface or a virtualized switch such as Open vSwitch[31, 32] for Xen and KVM based environments, or the Cisco Nexus 1000V Series virtual switch for VMware vSphere environments[12]. These virtual switches are designed ...
Network Reliability and Fault Tolerance
... circuit rerouting schemes can be broadly split into path-based and link- or node-based approaches. Prompted by the increasing reliance on high-speed communications and the requirement that these communications be robust to failures, backbone networks have generally adopted self-healing strategies to ...
... circuit rerouting schemes can be broadly split into path-based and link- or node-based approaches. Prompted by the increasing reliance on high-speed communications and the requirement that these communications be robust to failures, backbone networks have generally adopted self-healing strategies to ...
Australian Journal of Basic and Applied Sciences Reducing Overall
... with high speed. A single WiMAX Base Station (BS) may not enough to provide enough QoS in densely populated urban areas. So, to cover large area and to provide QoS, multiple overlapped BSs are used in WiMAX networks. The mobile station (MS) moving with high speed may goes out of coverage frequently. ...
... with high speed. A single WiMAX Base Station (BS) may not enough to provide enough QoS in densely populated urban areas. So, to cover large area and to provide QoS, multiple overlapped BSs are used in WiMAX networks. The mobile station (MS) moving with high speed may goes out of coverage frequently. ...
ZigBee Overview
... We can accommodate custom SENSOR(s) or custom Conditioning Circuitry in order to build what we call a Custom Module. Together with this custom module we also provide a driver supported in LabVIEW or C. ...
... We can accommodate custom SENSOR(s) or custom Conditioning Circuitry in order to build what we call a Custom Module. Together with this custom module we also provide a driver supported in LabVIEW or C. ...
pdf file
... millimeter sized sensors [3] (biomedical sensors, “smart home”, etc.). The special characteristics of an all-wireless network present several unique challenges. First, the lack of centralized control implies a high level of cooperation from the nodes. As individual nodes rely entirely on their own e ...
... millimeter sized sensors [3] (biomedical sensors, “smart home”, etc.). The special characteristics of an all-wireless network present several unique challenges. First, the lack of centralized control implies a high level of cooperation from the nodes. As individual nodes rely entirely on their own e ...