SoNIC: Precise Realtime Software Access and Control of Wired Networks
... to higher layers of the network stack. Unfortunately, the physical and data link layers are usually implemented in hardware and not easily accessible to systems programmers. Further, systems programmers often treat these lower layers as a black box. Not to mention that commodity network interface ca ...
... to higher layers of the network stack. Unfortunately, the physical and data link layers are usually implemented in hardware and not easily accessible to systems programmers. Further, systems programmers often treat these lower layers as a black box. Not to mention that commodity network interface ca ...
Headlight Intensity Control Methods – A Review
... surrounding vehicles are more. The high beams emit very high intensity light and are operated when not much vehicles are present on the road. When the oncoming vehicles emit a very bright light on the opposite vehicle, the driver of this vehicle has to face the fluorescence for some amount of time w ...
... surrounding vehicles are more. The high beams emit very high intensity light and are operated when not much vehicles are present on the road. When the oncoming vehicles emit a very bright light on the opposite vehicle, the driver of this vehicle has to face the fluorescence for some amount of time w ...
Packet Reading for Network Emulation
... In promiscuous mode no hardware filtering is done and the card passes on all packets that it sees to the host kernel. The kernel is then free to filter and discard packets as it sees fit. This filtering is being performed in software, which is slower but more flexible. Promiscuous mode is generally ...
... In promiscuous mode no hardware filtering is done and the card passes on all packets that it sees to the host kernel. The kernel is then free to filter and discard packets as it sees fit. This filtering is being performed in software, which is slower but more flexible. Promiscuous mode is generally ...
Chapter 1 - Prof J. Noorul Ameen ME
... /* active open */ if ((s = socket(PF_INET, SOCK_STREAM, 0)) < 0) { perror("simplex-talk: socket"); ...
... /* active open */ if ((s = socket(PF_INET, SOCK_STREAM, 0)) < 0) { perror("simplex-talk: socket"); ...
Lecture-2.1 => Network Typologies
... 1. Transmitting network is not affected by high traffic or by adding more nodes, as only the nodes having tokens can transmit data. 2. Cheap to install and expand ...
... 1. Transmitting network is not affected by high traffic or by adding more nodes, as only the nodes having tokens can transmit data. 2. Cheap to install and expand ...
GI3112131218
... situation demands. In an ad hoc network, one of the major concerns is how to decrease the power usage or battery depletion level of each node among the network so that the overall lifetime of the network can be stretched as much as possible. So while the data packets are sent from source to destinat ...
... situation demands. In an ad hoc network, one of the major concerns is how to decrease the power usage or battery depletion level of each node among the network so that the overall lifetime of the network can be stretched as much as possible. So while the data packets are sent from source to destinat ...
ECE/CS 4984: Lecture 11
... TCP Problems with Wireless ● Packet loss in wireless networks typically due to… ■ Bit errors due to wireless channel impairments ■ Handoffs due to mobility ■ Possibly congestion, but not often ● As we’ve seen, TCP assumes packet loss is due to… ■ Congestion in the network ■ Packet reordering, but n ...
... TCP Problems with Wireless ● Packet loss in wireless networks typically due to… ■ Bit errors due to wireless channel impairments ■ Handoffs due to mobility ■ Possibly congestion, but not often ● As we’ve seen, TCP assumes packet loss is due to… ■ Congestion in the network ■ Packet reordering, but n ...
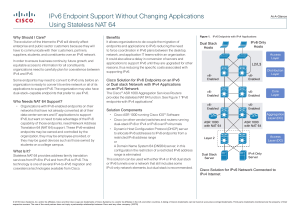
IPv6 Endpoint Support Without Changing Applications Using Stateless NAT 64
... Organizations with IPv6-enabled endpoints on their networks that have not already converted all of their data center servers and IT applications to support IPv6, but want or need to take advantage of the IPv6 capability of those endpoints, need Network Address Translation 64 (NAT 64) support. These ...
... Organizations with IPv6-enabled endpoints on their networks that have not already converted all of their data center servers and IT applications to support IPv6, but want or need to take advantage of the IPv6 capability of those endpoints, need Network Address Translation 64 (NAT 64) support. These ...
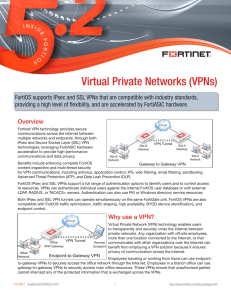
Virtual Private Networks (VPNs)
... by the network infrastructure and the VPN configuration can focus on high-level communication requirements, access control, security profiles, and endpoint control. Some networks, such as those available in public spaces, may block IPsec protocols, thereby preventing IPsec endpoints from accessing t ...
... by the network infrastructure and the VPN configuration can focus on high-level communication requirements, access control, security profiles, and endpoint control. Some networks, such as those available in public spaces, may block IPsec protocols, thereby preventing IPsec endpoints from accessing t ...
Centrality Measures
... Freeman’s Network Centrality • How do we calculate the value of centrality of the network – To check how much variaHon there is among the nodes (heterogeneity?) Max value of Degree Centrality in the ...
... Freeman’s Network Centrality • How do we calculate the value of centrality of the network – To check how much variaHon there is among the nodes (heterogeneity?) Max value of Degree Centrality in the ...
Effects on TCP of Routing Strategies in Satellite Constellations
... 2b, offer more regular repeating routing and delay patterns over time between terminals. Unlike the “polar star” constellations, rosette constellations can also offer two distinct sets of paths between terminals, depending on whether the terminals’ uplink and downlink communications have been alloca ...
... 2b, offer more regular repeating routing and delay patterns over time between terminals. Unlike the “polar star” constellations, rosette constellations can also offer two distinct sets of paths between terminals, depending on whether the terminals’ uplink and downlink communications have been alloca ...
Network Design and Management
... Congestion causes latency because switches and routers must store frames and packets while waiting to send them out again. ...
... Congestion causes latency because switches and routers must store frames and packets while waiting to send them out again. ...
Network Security
... protocols, based on the Internet security protocols IPsec and SSL/TLS. Network boundaries as security perimeters. Principles and limitations of firewalls and ...
... protocols, based on the Internet security protocols IPsec and SSL/TLS. Network boundaries as security perimeters. Principles and limitations of firewalls and ...
Survivability and Resilience Mechanisms in modern Optical Fibre Systems
... In the late 1980s we witnessed the first deployment of optical networks. Today we see the proliferation of data and storage networks. Standardisation of Synchronous Optical Network (SONET) and Synchronous Digital Hierarchy (SDH), as well as the high-speed optical interfaces on other devices, such as ...
... In the late 1980s we witnessed the first deployment of optical networks. Today we see the proliferation of data and storage networks. Standardisation of Synchronous Optical Network (SONET) and Synchronous Digital Hierarchy (SDH), as well as the high-speed optical interfaces on other devices, such as ...
PDF
... The first heuristic, when given an IP address, determines the length of the address mask associated with that address as follows: for masklen = 31 to 7 do a. assume network mask is of length masklen b. construct the ‘0’ and ‘255’ directed broadcast addresses for that address and masklen c. ping thes ...
... The first heuristic, when given an IP address, determines the length of the address mask associated with that address as follows: for masklen = 31 to 7 do a. assume network mask is of length masklen b. construct the ‘0’ and ‘255’ directed broadcast addresses for that address and masklen c. ping thes ...
IntelliServ™ Product Catalog
... and hole cleaning management can be addressed with high frequency and low latency data, enabling higher rates of penetration (ROP) to be achieved. ...
... and hole cleaning management can be addressed with high frequency and low latency data, enabling higher rates of penetration (ROP) to be achieved. ...
3. Centralized versus Distributed Mobility
... In centralized mobility management, the location information in terms of a mapping between the session identifier and the forwarding address is kept at a single mobility anchor, and packets destined to the session identifier are forwarded via this anchor. In other words, such mobility management sys ...
... In centralized mobility management, the location information in terms of a mapping between the session identifier and the forwarding address is kept at a single mobility anchor, and packets destined to the session identifier are forwarded via this anchor. In other words, such mobility management sys ...
Estimating Available Capacity of a Network Connection
... these previous work, as we account for the capacity lost due to cross traffic, in our estimates. The cprobe tool in [CaCr 96a] provides an available bandwidth measure, which accounts for cross traffic. They do so by sending a stream of packets, at a rate higher than the bottleneck bandwidth, and the ...
... these previous work, as we account for the capacity lost due to cross traffic, in our estimates. The cprobe tool in [CaCr 96a] provides an available bandwidth measure, which accounts for cross traffic. They do so by sending a stream of packets, at a rate higher than the bottleneck bandwidth, and the ...
Cisco Cluster Management Suite - Network
... • Provides comprehensive layout of all clustered devices: ...
... • Provides comprehensive layout of all clustered devices: ...
3/11
... Data link layer of the protocol stack is targeted Sniffer is a program that gathers traffic from local network & is useful for attackers for attackers to get all information as well as network administrators trying to trouble shoot problems An attacker can read data passing by a given machine in rea ...
... Data link layer of the protocol stack is targeted Sniffer is a program that gathers traffic from local network & is useful for attackers for attackers to get all information as well as network administrators trying to trouble shoot problems An attacker can read data passing by a given machine in rea ...
Guide to TCP/IP, Second Edition
... • Although these documents do not have the force of a Standard RFC, they do provide useful information that represents best approaches to designing, configuring, implementing, or maintaining TCP/IP-based networks and related services • For those reasons, BCPs are highly regarded and can be useful to ...
... • Although these documents do not have the force of a Standard RFC, they do provide useful information that represents best approaches to designing, configuring, implementing, or maintaining TCP/IP-based networks and related services • For those reasons, BCPs are highly regarded and can be useful to ...
license manager popcorn uninstall
... or grounding-type plug. A polarized plug has two blades with one wider than the other. A grounding- NOT OBSTRUCT THE VENTILATION VENTS. type plug has two blades and a third grounding prong. The wide blade or the third prong are provided for your safety. If the provided plug does not fit into your ou ...
... or grounding-type plug. A polarized plug has two blades with one wider than the other. A grounding- NOT OBSTRUCT THE VENTILATION VENTS. type plug has two blades and a third grounding prong. The wide blade or the third prong are provided for your safety. If the provided plug does not fit into your ou ...
Document
... • Other two routers are drop routers connected to client devices. • Two connections from the network port at the ingress service router to two drop ports, one in each of the drop routers. Client device sends 50% of the traffic on one of these drop interfaces and 50% on the other (it is attached to b ...
... • Other two routers are drop routers connected to client devices. • Two connections from the network port at the ingress service router to two drop ports, one in each of the drop routers. Client device sends 50% of the traffic on one of these drop interfaces and 50% on the other (it is attached to b ...
Internet
... ARP (Address Resolution Protocol) takes care of mapping between logical IP addresses and physical MAC addresses in a Local Area Network (LAN). PPP (Point-to-Point Protocol) or SLIP (Serial Line IP) is used for transport of IP traffic over modem connections between terminal and ISP’s Point of Presenc ...
... ARP (Address Resolution Protocol) takes care of mapping between logical IP addresses and physical MAC addresses in a Local Area Network (LAN). PPP (Point-to-Point Protocol) or SLIP (Serial Line IP) is used for transport of IP traffic over modem connections between terminal and ISP’s Point of Presenc ...