Raven X-HSPA Sierra Wireless Cellular Modem
... technology of the Sierra Wireless AirLink products simplifies installation, operation and maintenance of any solution, and provides an always-on, alwaysaware intelligent connection for mission-critical applications. ...
... technology of the Sierra Wireless AirLink products simplifies installation, operation and maintenance of any solution, and provides an always-on, alwaysaware intelligent connection for mission-critical applications. ...
NetVanta 6330 Series - Walker and Associates
... standards-based, IP routing functionality supporting BGP, OSPF, and RIP routing protocols. Inherent Quality of Service (QoS) methods ensure appropriate classification and prioritization of Voice over IP (VoIP) traffic. Using AOS simplifies management and administration through a Command Line Interfa ...
... standards-based, IP routing functionality supporting BGP, OSPF, and RIP routing protocols. Inherent Quality of Service (QoS) methods ensure appropriate classification and prioritization of Voice over IP (VoIP) traffic. Using AOS simplifies management and administration through a Command Line Interfa ...
Plug-and-Play IP Security:
... have also established keys while coordinating, hence their work is not of much practical impact. However, their work does provide some of the concepts used and extended in our work, where we establish keys between arbitrary parties, without assuming any coordination between them in advance. Hence, o ...
... have also established keys while coordinating, hence their work is not of much practical impact. However, their work does provide some of the concepts used and extended in our work, where we establish keys between arbitrary parties, without assuming any coordination between them in advance. Hence, o ...
Routing Information Protocol
... • The UDP packets has a maximum sixe of 512 bytes. This leaves room for 25 prefixes. If there are more prefixes to advertise we must use multiple UDP datagrams • The diameter of a network that runs RIP cannot be larger than 15. • In large networks, RIP traffic can consume a substantial amount of the ...
... • The UDP packets has a maximum sixe of 512 bytes. This leaves room for 25 prefixes. If there are more prefixes to advertise we must use multiple UDP datagrams • The diameter of a network that runs RIP cannot be larger than 15. • In large networks, RIP traffic can consume a substantial amount of the ...
22-05-0007-47-0000 - IEEE 802 LAN/MAN Standards Committee
... WG believe to be requirements. However, they are only guidance, and, in the interest of not inhibiting the ability of proposers to be innovative, proposers are free to take exception to requirements whose intent they believe can be met by other approaches, as long as they provide detailed justificat ...
... WG believe to be requirements. However, they are only guidance, and, in the interest of not inhibiting the ability of proposers to be innovative, proposers are free to take exception to requirements whose intent they believe can be met by other approaches, as long as they provide detailed justificat ...
Network Defense
... DHCP server database showed that this IP was assigned to a computer with MAC address 00:00:48:5c:3a:6c. This MAC belonged to a network printer. The router’s ARP table showed that the IP address 192.168.1.65. was used by a computer with MAC 00:30:65:4b:2a:5c. (IP-spoofing) Although this MAC was not o ...
... DHCP server database showed that this IP was assigned to a computer with MAC address 00:00:48:5c:3a:6c. This MAC belonged to a network printer. The router’s ARP table showed that the IP address 192.168.1.65. was used by a computer with MAC 00:30:65:4b:2a:5c. (IP-spoofing) Although this MAC was not o ...
downloading
... 1. (Optional) Upgrade the system firmware to the latest version available for the switch type to be used for the lab. Your instructor will provide the IP address of the TFT server and the name of the image to be used. a. Connect to the console port of your assigned switch using the console cable pro ...
... 1. (Optional) Upgrade the system firmware to the latest version available for the switch type to be used for the lab. Your instructor will provide the IP address of the TFT server and the name of the image to be used. a. Connect to the console port of your assigned switch using the console cable pro ...
R-iCDN: an Approach Supporting Flexible Content Routing for ISP
... III. R-iCDN Framework IV. Performance Evaluation V. ...
... III. R-iCDN Framework IV. Performance Evaluation V. ...
$doc.title
... switches) at network attachment points, also known as network interfaces; network interfaces at switches are also sometimes called switch ports. The fundamental functions performed by switches are to multiplex and demultiplex data frames belonging to different device-to-device information transfer s ...
... switches) at network attachment points, also known as network interfaces; network interfaces at switches are also sometimes called switch ports. The fundamental functions performed by switches are to multiplex and demultiplex data frames belonging to different device-to-device information transfer s ...
VLSM
... mask, also known as the: network prefix, or prefix length (/8, /19, and so on). The network address is no longer determined by the class of the address. ISPs could now more efficiently allocate address space using any prefix length, starting with /8 and larger (/8, /9, /10, and so on). ISP ...
... mask, also known as the: network prefix, or prefix length (/8, /19, and so on). The network address is no longer determined by the class of the address. ISPs could now more efficiently allocate address space using any prefix length, starting with /8 and larger (/8, /9, /10, and so on). ISP ...
The ENOC When, Who, What?
... – Operational interface between EGEE and the networks involved in the infrastructures (mainly, but not limited to, NRENs): Support unit for grid users for all network related issues, Point of contact for a NOC to provide operational information (TT) and contact EGEE for operational issues, ...
... – Operational interface between EGEE and the networks involved in the infrastructures (mainly, but not limited to, NRENs): Support unit for grid users for all network related issues, Point of contact for a NOC to provide operational information (TT) and contact EGEE for operational issues, ...
Bridging
... Wireless Bridges An increasingly popular alternative for bridging remote LANs up to 50 miles are wireless bridges. It use spread spectrum radio transmission between LAN sites and are primarily limited to Ethernet networks at this time. New wireless bridges using the 2.41 GHz or 5.81GHz frequen ...
... Wireless Bridges An increasingly popular alternative for bridging remote LANs up to 50 miles are wireless bridges. It use spread spectrum radio transmission between LAN sites and are primarily limited to Ethernet networks at this time. New wireless bridges using the 2.41 GHz or 5.81GHz frequen ...
PERFORMANCE PREDICTION OF MESSAGE PASSING COMMUNICATION IN DISTRIBUTED MEMORY SYSTEMS
... sending a message to all processes in the group including itself. A gather operation is the reverse of broadcast. The root process now waits to receive a message from every process in the group. In a scatter operation, the message sent by the root process is split into n equal parts and each of the ...
... sending a message to all processes in the group including itself. A gather operation is the reverse of broadcast. The root process now waits to receive a message from every process in the group. In a scatter operation, the message sent by the root process is split into n equal parts and each of the ...
Meyers_CompTIA_4e_PPT_Ch04
... Connecting Ethernet Segments • When all ports on an existing hub have been used, add another hub or a bridge – Hubs can be connected using an uplink port or a crossover cable ...
... Connecting Ethernet Segments • When all ports on an existing hub have been used, add another hub or a bridge – Hubs can be connected using an uplink port or a crossover cable ...
The OSI Model
... a. Advertisement for N1 is done by R1 because it is the only attached router and therefore the designated router. b. Advertisement for N2 can be done by either R1, R2, or R3, depending on which one is chosen as the designated router. ...
... a. Advertisement for N1 is done by R1 because it is the only attached router and therefore the designated router. b. Advertisement for N2 can be done by either R1, R2, or R3, depending on which one is chosen as the designated router. ...
第十九讲
... o Since ICMP is sent using IP, it’s just the IP source address o And can use PTR record to find name of router ...
... o Since ICMP is sent using IP, it’s just the IP source address o And can use PTR record to find name of router ...
ppt
... • Server responds with SYNACK keeps state about TCP half-open connection • Eventually server memory is exhausted with this state ...
... • Server responds with SYNACK keeps state about TCP half-open connection • Eventually server memory is exhausted with this state ...
ROUTE10S03L05
... Task 1: Configure OSPF over LAN interfaces – What steps did you take to configure the OSPF routing protocol and advertise all of the specific IP subnets used in the network? – How can you change the configuration to prevent any network added to the router from being advertised? – How does this cha ...
... Task 1: Configure OSPF over LAN interfaces – What steps did you take to configure the OSPF routing protocol and advertise all of the specific IP subnets used in the network? – How can you change the configuration to prevent any network added to the router from being advertised? – How does this cha ...
Chapter 3: Internetworking
... single switch, large networks can be built by interconnecting a number of switches We can connect switches to each other and to hosts using pointto-point links, which typically means that we can build networks of large geographic scope Adding a new host to the network by connecting it to a switch do ...
... single switch, large networks can be built by interconnecting a number of switches We can connect switches to each other and to hosts using pointto-point links, which typically means that we can build networks of large geographic scope Adding a new host to the network by connecting it to a switch do ...
dccn-ARP - WordPress.com
... Echo request and echo reply are designed for diagnostic purposes. These are used for identification of network problems. The combination of both echo request and reply messages determines whether two systems can communicate with each other. ...
... Echo request and echo reply are designed for diagnostic purposes. These are used for identification of network problems. The combination of both echo request and reply messages determines whether two systems can communicate with each other. ...
Multi-layer Traffic Engineering in Data-centric Optical
... keeping the network optimal, while reactive ones only fix problems. Next, there are several aspects concerning the decision strategy. The number of considered alternatives has a great effect on the optimality of the resulting logical topology. A trade-off has to be made though between optimality and ...
... keeping the network optimal, while reactive ones only fix problems. Next, there are several aspects concerning the decision strategy. The number of considered alternatives has a great effect on the optimality of the resulting logical topology. A trade-off has to be made though between optimality and ...
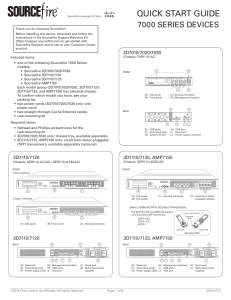
http://www.cisco.com/c/dam/en/us/td/docs/security/sourcefire/3d-system/53/quick-start-guides/QSG-3D7xxx-v53-3-20140311.pdf
... is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management network using an Ethernet cable, then connect the sensing interfaces to the network se ...
... is connected to your trusted management network and the various network segments you want to monitor. In a simple deployment scenario, you connect the management interface on your device to your trusted management network using an Ethernet cable, then connect the sensing interfaces to the network se ...
IOSR Journal of Electronics and Communication Engineering (IOSR-JECE)
... communication between different sub-networks concept of route redistribution is introduced [1]. In multihoming environment, if a link fails in the AS, it can still connect to the Internet via other connections. The reliability of the Internet depends upon the reaction time necessary for the underlyi ...
... communication between different sub-networks concept of route redistribution is introduced [1]. In multihoming environment, if a link fails in the AS, it can still connect to the Internet via other connections. The reliability of the Internet depends upon the reaction time necessary for the underlyi ...