Internet Measurements - Computer Science & Engineering
... Study dynamics of scam hosting infrastructure ...
... Study dynamics of scam hosting infrastructure ...
How Fast Is the Internet - Faculty of Computer Science
... When an acknowledgement is received, congestion window is increased When a packet is lost (and retransmitted) congestion window is reduced Net transmission rate is WinSize / RTT ...
... When an acknowledgement is received, congestion window is increased When a packet is lost (and retransmitted) congestion window is reduced Net transmission rate is WinSize / RTT ...
What is a Network? - ITCK
... • A computer network or data network is a telecommunications network which allows computers to exchange data. • In computer networks, networked computing devices exchange data with each other using a data link. The connections between nodes are established using either cable media or wireless media. ...
... • A computer network or data network is a telecommunications network which allows computers to exchange data. • In computer networks, networked computing devices exchange data with each other using a data link. The connections between nodes are established using either cable media or wireless media. ...
pptx
... video Others in between, or with stronger requirements Biggest cause of delay variation: reliable delivery Today’s ...
... video Others in between, or with stronger requirements Biggest cause of delay variation: reliable delivery Today’s ...
Advantages and Disadvantages of Different Network Topologies
... A network topology refers to the way in which nodes in a network are connected to one another. The way in which they are connected defines how they communicate. Each kind of arrangement of network nodes has its own advantages and disadvantages. Here we tell you about the same. Network topologies des ...
... A network topology refers to the way in which nodes in a network are connected to one another. The way in which they are connected defines how they communicate. Each kind of arrangement of network nodes has its own advantages and disadvantages. Here we tell you about the same. Network topologies des ...
vocab-network-euro-15
... typically involve a mobile computer, a cell phone and a handheld computing device such as a PDA. ...
... typically involve a mobile computer, a cell phone and a handheld computing device such as a PDA. ...
IP, ATM, Wireless
... • Increases range and data speed possible • “Effective Radiated Power” = real power * gain of antenna ...
... • Increases range and data speed possible • “Effective Radiated Power” = real power * gain of antenna ...
fm fluidity
... With FLUIDITY you can now control train operations. Redundant setup, secure and continuous connection along with an unmatched average handoff time of 3 milliseconds give you the confidence you need to secure automatic train operations. Our radios create wireless networks for train and metro operator ...
... With FLUIDITY you can now control train operations. Redundant setup, secure and continuous connection along with an unmatched average handoff time of 3 milliseconds give you the confidence you need to secure automatic train operations. Our radios create wireless networks for train and metro operator ...
Bitcoin
... networks to find the degree distributions, and the evolution of the network with time. Analyzing the Hubs in the networks to find the Money mixers in the network. Analyzing the characteristics of the rich people in each network. Finding the percentage of users accessing the bitcoin network ano ...
... networks to find the degree distributions, and the evolution of the network with time. Analyzing the Hubs in the networks to find the Money mixers in the network. Analyzing the characteristics of the rich people in each network. Finding the percentage of users accessing the bitcoin network ano ...
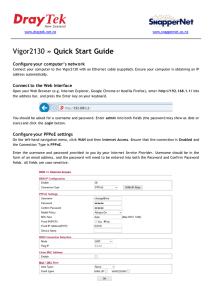
Vigor2130 » Quick Start Guide
... Configure your computer’s network Connect your computer to the Vigor2130 with an Ethernet cable (supplied). Ensure your computer is obtaining an IP address automatically. ...
... Configure your computer’s network Connect your computer to the Vigor2130 with an Ethernet cable (supplied). Ensure your computer is obtaining an IP address automatically. ...
Analysis of a Clock Synchronization Protocol for Wireless Sensor
... We claim that for a line network of size N, the guard time g should be at least N. We consider only networks with perfect clocks, in which clock drift is zero. ...
... We claim that for a line network of size N, the guard time g should be at least N. We consider only networks with perfect clocks, in which clock drift is zero. ...
Discovering Computers Fundamentals 3rd Edition
... Protocol) technology transmits data by breaking it up into small pieces, or packets ...
... Protocol) technology transmits data by breaking it up into small pieces, or packets ...
MET Connect Presentation
... • 3G Networks use Network Address Translation (NAT) so Public IP address isn’t usually possible • Some providers offer a custom APN which locks you to one provider • Dyn-DNS services to track a changing IP address are not scalable to many devices ...
... • 3G Networks use Network Address Translation (NAT) so Public IP address isn’t usually possible • Some providers offer a custom APN which locks you to one provider • Dyn-DNS services to track a changing IP address are not scalable to many devices ...
Cell tower solutions for tier 2 service providers
... tier 2 service providers The exploding growth of smartphones and other mobile data devices is driving huge increases in demand for wireless bandwidth. New 4G Long Term Evolution (LTE) services provide greater bandwidth for mobile devices and will compete with residential broadband services. The 4G L ...
... tier 2 service providers The exploding growth of smartphones and other mobile data devices is driving huge increases in demand for wireless bandwidth. New 4G Long Term Evolution (LTE) services provide greater bandwidth for mobile devices and will compete with residential broadband services. The 4G L ...
Mastering Windows Network Forensics and Investigation
... • Use only trusted and validated analysis tools • Request intimate details about target system ...
... • Use only trusted and validated analysis tools • Request intimate details about target system ...
basics
... Nothing is absolute in networks research 2. This applies for the first rule 3. There are no complicated concepts, just ...
... Nothing is absolute in networks research 2. This applies for the first rule 3. There are no complicated concepts, just ...
Chapter 15
... – Advantages of Internet-based EDI are the ability to use well-understood Internet technology, a preexisting, costless network to transmit business data, and convenience. – Disadvantages of using Internet-based EDI are data security and lack of consulting expertise in the implementation phase. ...
... – Advantages of Internet-based EDI are the ability to use well-understood Internet technology, a preexisting, costless network to transmit business data, and convenience. – Disadvantages of using Internet-based EDI are data security and lack of consulting expertise in the implementation phase. ...
INFO 2225 - Metropolitan Community College
... Research Terminal Emulation Client Software and Configure the SSH Client Secure Cisco IOS Image and Configure Files on R1 and R3’ Configure a Synchronized Time Source Using NTP Configure Automated Security Features Use the CCP Security Audit Tool on R1 to Identify Security Risk ...
... Research Terminal Emulation Client Software and Configure the SSH Client Secure Cisco IOS Image and Configure Files on R1 and R3’ Configure a Synchronized Time Source Using NTP Configure Automated Security Features Use the CCP Security Audit Tool on R1 to Identify Security Risk ...
Networked Systems
... Star topology – each node or host is connected to a central network hub or concentrator directly central network hub or concentrator – manages and controls all functions of the network o also acts as a repeated for the data flow popular because it is easy to install and wire no disruption in ...
... Star topology – each node or host is connected to a central network hub or concentrator directly central network hub or concentrator – manages and controls all functions of the network o also acts as a repeated for the data flow popular because it is easy to install and wire no disruption in ...
G-Lab Deep: Cross-layer Composition and
... allow composition of independent service and network functional blocks in one integrated framework based on the requirements and the network status. A modular solution with loose coupling is desirable to (a) achieve a clean separation of the needed functional blocks without strong entanglement of me ...
... allow composition of independent service and network functional blocks in one integrated framework based on the requirements and the network status. A modular solution with loose coupling is desirable to (a) achieve a clean separation of the needed functional blocks without strong entanglement of me ...
Chapter 6 slides, Computer Networking, 3rd edition
... access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTSs may still collide with each other (but they’re short) ...
... access of data frames: avoid collisions of long data frames sender first transmits small request-to-send (RTS) packets to BS using CSMA RTSs may still collide with each other (but they’re short) ...
Cancer site-specific multidisciplinary team
... CANCER SITE SPECIFIC AND SPECIALIST SERVICES LEAD CLINICIANS The Lead Clinicians will support the Network Advisory Groups and will be expected to work with the Network Chair, Lead Clinician and Directors to ensure: The continued development of the tumour site specific cancers clinical networks R ...
... CANCER SITE SPECIFIC AND SPECIALIST SERVICES LEAD CLINICIANS The Lead Clinicians will support the Network Advisory Groups and will be expected to work with the Network Chair, Lead Clinician and Directors to ensure: The continued development of the tumour site specific cancers clinical networks R ...
21-07-0102-00-0000-comments-to-lb1c
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
... This document has been prepared to assist the IEEE 802.21 Working Group. It is offered as a basis for discussion and is not binding on the contributing individual(s) or organization(s). The material in this document is subject to change in form and content after further study. The contributor(s) res ...
Framework Document Presentation
... Other networks, and upper layer functional entities (FEs) • Session admission, authentication and enforcement of policy are executed via the “Session and Policy” control functions • Value-added and enhanced services are hosted in servers in the “Applications and Service Capability” functions • Servi ...
... Other networks, and upper layer functional entities (FEs) • Session admission, authentication and enforcement of policy are executed via the “Session and Policy” control functions • Value-added and enhanced services are hosted in servers in the “Applications and Service Capability” functions • Servi ...
Network and Perimeter Security
... VPNs provide a secure option for communicating across a public network VPNS are used in two primary scenarios: Network access for remote clients Network access between sites VPN quarantine control provides an additional level of security by providing the ability to check the configuration of the VPN ...
... VPNs provide a secure option for communicating across a public network VPNS are used in two primary scenarios: Network access for remote clients Network access between sites VPN quarantine control provides an additional level of security by providing the ability to check the configuration of the VPN ...